* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download RFPWoodgroveBankJBHickmanmODFQ03
Computer security wikipedia , lookup
Computer network wikipedia , lookup
Server Message Block wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Wireless security wikipedia , lookup
Microsoft Security Essentials wikipedia , lookup
Distributed firewall wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Remote Desktop Services wikipedia , lookup
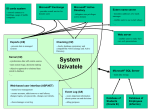
WOODGROVE BANK Proposal To Re-Design The Woodgrove Bank Network Blake Hickman 3/2/2012 Contents: 1. 2. 3. 4. 5. Executive Overview Network Infrastructure Design Security Business Continuity Plan Network Map Proposal To Re-Design The Woodgrove Bank Network 1. Executive Overview Over the last few years, Woodgrove Bank has suffered from a number of issues including: hacker attacks, security issues involving missing security patches, outdated virus protection, missing patches and updates to the operating systems throughout the network. Woodgrove Bank is also in need of upgrading its’ business continuity plan to respond to these and other issues. This has caused serious down time for Woodgrove Bank and its clients. Due to the new overhaul of the entire Woodgrove Bank network and addition of the new sites in North America, Woodgrove Bank will deploy a new network infrastructure compliant with security requirements which will secure all new and existing contracts with their clients. The new design that I propose will improve security throughout the entire network as well as individually at each site. It will have protection from hackers attacks by upgrading all servers and computers to the latest and most secure operating systems: Windows Server 2008 R2 and Windows 7 Service Pack 1. Monitoring applications will be installed to help detect and deter attacks. Network configuration settings will be enhanced which will help combat against unauthorized access to the network and data. Security patches as well as updates to the operating systems will be updated regularly. Virus protection will be updated and automated to insure the maximum protection available. Remote Access to the network will be secure and limited to only those computers that meet Woodgrove Bank’s access/security policy. Incorporating secure authentication by Smart Card is a top priority. Performance will increase due to new hardware and software configurations. Woodgrove Bank and their clients will have minimal downtime and maximum availability for vital software and data. Backups and a 1 Proposal To Re-Design The Woodgrove Bank Network detailed business continuity plan will be in place to handle internal and external threats, prevention of and recovery from those threats, and plans for continued operations from disruption from natural or man-made hazards. The network design proposed here will save Woodgrove Bank thousands of dollars because of the new room for future network growth, a more secure network, a minimal downtime strategy, centralized and minimal administration structure, and the many other benefits of my plan. This network layout is simple and cost effective, yet exceeds industry standards. Using my proposal and the newest technology on today’s market will insure Woodgrove Bank’s future in a highly competitive world. 2. Network Infrastructure Design Hardware Each individual sites network infrastructure will consist of a star topology, CAT 5e networking cables, gigabit network switches, and two new HP Hyper-V enabled servers for redundancy (Microsoft). Microsoft Hyper-V Server 2008 R2 is a platform that allows you to use one physical server to run multiple virtual sessions consolidating the workload. It improves the server utilization, decreases costs, and has a small footprint and little overhead (Microsoft). All servers will have RAID 10 (RAID 1+0) on each logical drive (the OS has a dedicated drive) (Microsoft Support, 2006). The operating system will be Windows Server 2008 R2 Enterprise Edition 64bit (which has licensing for 4 virtual machines per OS installation) on each physical server. All virtual servers will run Windows Server 2008 R2 Standard or Windows Server 2008 Core. Windows 7 Professional Service Pack 1 will be used for all Woodgrove Bank desktops and laptops. 2 Proposal To Re-Design The Woodgrove Bank Network Main Server Services Snapshot Server 1 – Hyper-V - Windows Server 2008 R2 Enterprise Edition 64bit 1. 2. 3. 4. VM – Primary DC, DNS, DHCP - Windows Server 2008 R2 Standard VM – Print & File Services - Windows Server 2008 R2 Standard VM – RRAS, NAP, WSUS, Antivirus - Windows Server 2008 R2 Standard VM – Active Directory Certificate Services* - Windows Server 2008 R2 Standard *Only on the Main Branch in NYC & turned off when not in use. (This VM server will host the Enterprise Certification Authority) Server 2 – Hyper-V - Windows Server 2008 R2 Enterprise Ed 64bit 1. VM – Backup DC, DNS, DHCP - Windows Server 2008 R2 Standard 2. VM – Backup Print & File Services - Windows Server 2008 R2 Standard 3. VM – Windows Server Backup & Symantec Backup- Windows Server 2008 Core Server Configuration For just the NYC site – Summary: Two host servers with seven VM sessions. 3 Proposal To Re-Design The Woodgrove Bank Network Server Configuration For all other sites – Summary: Two host servers with three VM sessions on each (total of six VM sessions). Deployment Strategy All servers will be initially built and configured at their respected sites; excluding the new branch locations. In North America, Toronto will be the testing and distribution center for its new branch locations: Vancouver and Calgary; and New York City will be the testing and distribution center for Seattle and its new branch locations: Redmond, Bellevue, Tacoma, and Spokane. Once the initial build-out is completed for the newly added branches the servers will be sent to their respected locations (additional configurations will be done after the new servers are in place). Once the servers are online, a few test desktops will be added to the new network. Once testing is complete, each required site Admin team will use Windows Deployment Services to push out 4 Proposal To Re-Design The Woodgrove Bank Network unattended installations of Windows 7 to each desktop/laptop not already running that version of the OS (Microsoft TechNet). The local site network Admin and management can make the call if any desktops and/or laptop need to be replace in order to run the new OS. Active Directory Active Directory Domain Services (AD DS) will be used on Woodgrove Bank’s network. Replication will be enabled on all Domain Controllers (DC) at each site. Due to the company’s size and physical locations, the existing forest model can be used in the new design. The trust configuration can be a two-way relationship. The major organizational units within the Woodgrove Bank domain would be modeled after the location of the sites (ie. NYC, London, Tokyo, etc.). Each geographical container has another container for every division within the company (ie. Servers, Desktops, IT, Executives, Managers, Staff, etc.). Separate Group Policies can be added to each OU and delegation of administrating the OU can be given to the acting Admin at each location (Microsoft TechNet). Physical Location North America Network Region NYC – Main Regional Branch Miami – Secondary Site Branch Toronto – Secondary Site Branch Canada’s new branch locations connected to Toronto Vancouver – Remote Site Branch Calgary – Remote Site Branch Newly acquired regional bank in Washington State Seattle – Secondary Site Branch Redmond – Remote Site Branch Bellevue – Remote Site Branch Tacoma – Remote Site Branch Spokane – Remote Site Branch 5 Proposal To Re-Design The Woodgrove Bank Network Europe Network Region London – Main Regional Branch Paris – Secondary Site Branch Lisbon – Secondary Site Branch Asia Network Region Tokyo – Main Regional Branch Beijing – Secondary Site Branch DHCP Woodgrove Bank will need to install two DHCP servers at each Site. Each site will have its own scope (see Scope layout). Each site’s DHCP scope will be split between the two DHCP servers. This configuration will provide fault tolerance and improve DHCP performance on this subnet (Davis, 2008). DHCP will be split between the primary DHCP server on the local subnet and the secondary DHCP server on the network using the 80/20 rule. This rule will exclude 20% of the addresses on the primary DHCP server, and 80% of the addresses on the backup DHCP server (Microsoft TechNet). Each site will mirror this DHCP setup (80/20 rule). The primary DHCP server will have a majority of the IP addresses and the backup DHCP server will have the remaining 20%. I have decided to incorporate super subnetting for some sites for more IP address on the same network (some sites need more than 254 addresses within the network).The Main and Secondary Site Branch has super subnetting for consistency and growth. In each scope, DHCP will have Exclusions and Reservations defined for the following network objects: Routers & Servers & Switches, Etc – Exclusions (static assignment) Secure Computers/Laptop – Reservations (DHCP) Public Computers/Laptop – Reservations (DHCP) Printers, and other devices – Reservations (DHCP) 6 Proposal To Re-Design The Woodgrove Bank Network IP scheme Each Region and site has a huge private IP scope for updates and expansion. A class B IPv4 network scheme: REGION North America SUBNET RANGE 172.16.x.x – 172.20.x.x Europe 172.21.x.x – 172.25.x.x Asia 172.26.x.x – 172.30.x.x Lab/Testing 172.31.x.x North America Region Scopes: Site NYC Site NYC SUBNET RANGE 172.16.0.1 – 172.16.255.254 SUBNET MASK 255.255.0.0 Miami 172.17.0.1 – 172.17.255.254 255.255.0.0 Toronto 172.18.0.1 – 172.18.253.254 255.255.0.0 Vancouver 172.18.254.1 – 172.18.254.254 255.255.255.0 Calgary 172.18.255.1 – 172.18.255.254 255.255.255.0 Seattle 172.19.0.1 – 172.19.251.254 Redmond 172.19.252.1 – 172.19.252.254 255.255.255.0 Bellevue 172.19.253.1 – 172.19.253.254 255.255.255.0 Tacoma 172.19.254.1 – 172.19.254.254 255.255.255.0 Spokane 172.19.255.1 – 172.19.255.254 255.255.255.0 Network Object Routers & Servers 255.255.0.0 SUBNET RANGE 172.16.0.1 – 172.16.0.254 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.16.1.1 – 172.16.99.254 255.255.0.0 Public Computers/Laptop 172.16.100.1 – 172.16.199.254 255.255.0.0 Printers, & devices 172.16.200.1 – 172.16.255.254 255.255.0.0 Site Miami Site Toronto Network Object Routers & Servers SUBNET RANGE 172.17.0.1 – 172.17.0.254 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.17.1.1 – 172.17.99.254 255.255.0.0 Public Computers/Laptop 172.17.100.1 – 172.17.199.254 255.255.0.0 Printers, & devices 172.17.200.1 – 172.17.255.254 255.255.0.0 Network Object Routers & Servers SUBNET RANGE 172.18.0.1 – 172.18.0.254 SUBNET MASK 255.255.255.0 7 Proposal To Re-Design The Woodgrove Bank Network Site Vancouver Site Calgary Site Seattle Site Redmond Site Bellevue Site Tacoma Secure Computers/Laptop 172.18.1.1 – 172.18.99.254 255.255.0.0 Public Computers/Laptop 172.18.100.1 – 172.18.199.254 255.255.0.0 Printers, & devices 172.18.200.1 – 172.18.253.254 255.255.0.0 Network Object Routers & Servers SUBNET RANGE 172.18.254.1 – 172.18.254.49 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.18.254.50 – 172.18.254.99 255.255.255.0 Public Computers/Laptop 172.18.254.100 – 172.18.254.149 255.255.255.0 Printers, & devices 172.18.254.150 – 172.18.254.254 255.255.255.0 SUBNET RANGE 172.18.255.1 – 172.18.255.49 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.18.255.50 – 172.18.255.99 255.255.255.0 Public Computers/Laptop 172.18.255.100 – 172.18.255.149 255.255.255.0 Printers, & devices 172.18.255.150 – 172.18.255.254 255.255.255.0 SUBNET RANGE 172.19.0.1 – 172.19.0.254 SUBNET MASK 255.255.255.0 Network Object Routers & Servers Network Object Routers & Servers Secure Computers/Laptop 172.19.1.1 – 172.19.99.254 255.255.0.0 Public Computers/Laptop 172.19.100.1 – 172.19.199.254 255.255.0.0 Printers, & devices 172.19.200.1 – 172.19.251.254 255.255.0.0 Network Object Routers & Servers SUBNET RANGE 172.19.252.1 – 172.19.252.49 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.19.252.50 – 172.19.252.99 255.255.255.0 Public Computers/Laptop 172.19.252.100 – 172.19.252.149 255.255.255.0 Printers, & devices 172.19.252.150 – 172.19.252.254 255.255.255.0 SUBNET RANGE 172.19.253.1 – 172.19.253.49 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.19.253.50 – 172.19.253.99 255.255.255.0 Public Computers/Laptop 172.19.253.100 – 172.19.253.149 255.255.255.0 Printers, & devices 172.19.253.150 – 172.19.253.254 255.255.255.0 SUBNET RANGE 172.19.254.1 – 172.19.254.49 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.19.254.50 – 172.19.254.99 255.255.255.0 Public Computers/Laptop 172.19.254.100 – 172.19.254.149 255.255.255.0 Printers, & devices 172.19.254.150 – 172.19.254.254 255.255.255.0 Network Object Routers & Servers Network Object Routers & Servers 8 Proposal To Re-Design The Woodgrove Bank Network Site Spokane Network Object Routers & Servers SUBNET RANGE 172.19.255.1 – 172.19.255.49 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.19.255.50 – 172.19.255.99 255.255.255.0 Public Computers/Laptop 172.19.255.100 – 172.19.255.149 255.255.255.0 Printers, & devices 172.19.255.150 – 172.19.255.254 255.255.255.0 Europe Region Scopes: Site London Site Paris Site Lisbon Site London SUBNET RANGE 172.21.0.1 – 172.21.255.254 SUBNET MASK 255.255.0.0 Paris 172.22.0.1 – 172.22.255.254 255.255.0.0 Lisbon 172.23.0.1 – 172.23.253.254 255.255.0.0 Network Object Routers & Servers SUBNET RANGE 172.21.0.1 – 172.21.0.254 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.21.1 – 172.21.99.254 255.255.0.0 Public Computers/Laptop 172.21.100.1 – 172.21.199.254 255.255.0.0 Printers, & devices 172.21.200.1 – 172.21.255.254 255.255.0.0 Network Object Routers & Servers SUBNET RANGE 172.22.0.1 – 172.22.0.254 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.22.1.1 – 172.22.99.254 255.255.0.0 Public Computers/Laptop 172.22.100.1 – 172.22.199.254 255.255.0.0 Printers, & devices 172.22.200.1 – 172.22.255.254 255.255.0.0 Network Object Routers & Servers SUBNET RANGE 172.23.0.1 – 172.23.0.254 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.23.1.1 – 172.23.99.254 255.255.0.0 Public Computers/Laptop 172.23.100.1 – 172.23.199.254 255.255.0.0 Printers, & devices 172.23.200.1 – 172.23.255.254 255.255.0.0 Asia Region Scopes: Site Tokyo Beijing Site Tokyo SUBNET RANGE 172.26.0.1 – 172.26.255.254 SUBNET MASK 255.255.0.0 172.27.0.1 – 172.27.255.254 255.255.0.0 Network Object Routers & Servers SUBNET RANGE 172.26.0.1 – 172.26.0.254 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.26.1.1 – 172.26.99.254 255.255.0.0 Public Computers/Laptop 172.26.100.1 – 172.26.199.254 255.255.0.0 9 Proposal To Re-Design The Woodgrove Bank Network Site Beijing Printers, & devices 172.26.200.1 – 172.26.255.254 Network Object Routers & Servers SUBNET RANGE 172.27.0.1 – 172.27.0.254 255.255.0.0 SUBNET MASK 255.255.255.0 Secure Computers/Laptop 172.27.1.1 – 172.27.99.254 255.255.0.0 Public Computers/Laptop 172.27.100.1 – 172.27.199.254 255.255.0.0 Printers, & devices 172.27.200.1 – 172.27.255.254 255.255.0.0 DNS It is essential that the design of the DNS namespace be created with Active Directory in mind and that the namespace that exists on the Internet does not conflict with Woodgrove Bank’s internal namespace (Microsoft Support, 2011). All DNS namespaces for Woodgrove Bank, both external and internal, are being re-created as follows: External namespace: WoodgroveBank.com Internal namespace: North America Network Region internal.nyc.na.woodgrovebank.com internal. miami.na.woodgrovebank.com internal. toronto.na.woodgrovebank.com internal. vancouver.na.woodgrovebank.com internal. calgary.na.woodgrovebank.com internal. seattle.na.woodgrovebank.com internal. redmond.na.woodgrovebank.com internal. bellevue.na.woodgrovebank.com internal. tacoma.na.woodgrovebank.com internal. spokane.na.woodgrovebank.com Europe Network Region internal. london.eur.woodgrovebank.com internal. paris.eur.woodgrovebank.com internal. lisbon.eur.woodgrovebank.com Asia Network Region internal. tokyo.asia.woodgrovebank.com internal. Beijing.asia.woodgrovebank.com 10 Proposal To Re-Design The Woodgrove Bank Network Each site will have internal and external DNS servers in addition to backup DNS servers. The external DNS will be configured to use the ISP’s DNS servers. Active Directory-integrated zone will be used to hold zone data in Active Directory. This will provide writeable copies of the zone data, fault tolerance, and security. Secure Dynamic DNS (DDNS) is only supported on Active Directory-integrated zones (Microsoft TechNet). With secure DDNS, only domain members can register DNS records, and only the same computer can modify those records. By increasing the number of servers that have a copy of the zone database, you improve DNS performance. Each site will be subdivided into child zones and site administrators will be delegated their part of the domain name space (Microsoft TechNet). Multiple DNS servers at each site will provide redundancy in case a server fails. Wireless At each site there will be two wireless networks using an infrastructure topology. Having wireless networks will provide flexibility, productivity and scalability. It allows people to move around and provide capabilities which traditional wired network infrastructures cannot do. Users will be able to access resources in hard to reach places. You can easily add hosts without increasing administrative efforts. There will be one public wireless network for guests and another wireless network secure and private for company use. The private network will use 802.1x as an enforcement point for both wired and wireless clients (See Security Policy for more information on 802.1x). The enforcement point will be configured as a RADIUS client to the NAP server. On an 802.1x switch, VLANs will be defined to create compliant and non-compliant networks. Client computers are assigned to the appropriate VLAN based 11 Proposal To Re-Design The Woodgrove Bank Network on health compliance. In the Network Policies on the NAP server, identify the VLAN that corresponds to the compliant and non-compliant networks (guests will be sent to the non-compliant network and will not have access to the private network). As an additional security measure, the Service Set Identifier (SSID) will be hidden. RRAS For remote access to the network, Woodgrove Bank will be using Routing and Remote Access (RRAS). Routing and Remote Access in Windows Server 2008 has enhanced security and manageability (Microsoft TechNet). With a Server Manager for managing, SSTP tunneling protocol, VPN enforcement for Network Access Protection, and a new cryptographic support, communication will be secure and meet the requirements for VPN security (Microsoft TechNet). This is part of the Network Policy and Access Services (NPAS) role which will provides services for configuring network access for LAN and remote clients throughout the network. Network Policy Server (NPS) will employ a RADIUS server and health policies used with Network Access Protection (NAP). Network Policy and Access Services will use Health Registration Authority (HRA) to enforceme NAP security, Remote Access Service to provide Virtual Private Networking (VPN) in conjunction with RRAS, Routing will provide Network Address Translation (NAT) (Microsoft). Network Access Protection (NAP) allows system health requirements enforcement for connecting clients. It allows administrators to regulate network access and communication based on a computer's compliance with health requirement policies. NAP gives you the ability to restrict access for non-compliant computers as well as to 12 Proposal To Re-Design The Woodgrove Bank Network provide access to updates or health update resources to allow computers to become compliant. Secure Socket Tunneling Protocol (SSTP) which uses HTTP over SSL to establish the VPN connection will also be used. This will allow easier access through firewalls and maintain a secure VPN connection. WSUS A Windows Server Update Services (WSUS) will be installed at each location to allow a centralized point for updating software at that site. Having a WSUS server installed will keep all computer operating systems updated and compliant. Employing a WSUS service gives Woodgrove Bank the ability to control which updates computers can receive, enforce the application of updates throughout the network, and significantly reduce the traffic on the WAN by receiving updates from local WSUS servers rather than using Internet links to receive updates (Sanders, 2008). The WSUS server at each site will be synchronized using a parent-child relationship. Since each region is fairly independent from the other regions, Woodgrove Bank will have a parent-child relationship within each region. New York City, London, and Tokyo will each host a parent WSUS server. From these parent WSUS servers, the approval lists and/or updates will synchronize between all child servers. At the other locations a downstream child WSUS server will be configured to point back to the parent WSUS server in their region. The WSUS service will be configured as replica mode so that both updates and approvals are synchronized to child servers. This will allow for centralized administration (Sanders, 2008). The exception to this are the Remote Site Branches: Vancouver, Calgary, 13 Proposal To Re-Design The Woodgrove Bank Network Redmond, Bellevue, Tacoma, and Spokane. These will still have access to the MS updates approval list but will download updates from the Microsoft Update Center. File Servers Each site will have a File server. Using the File Server role service adds the Share and Storage Management console where you can manage the shared folders that are available to network users, offline file settings on folders that allow for synchronization of files in shared folders when the user disconnects and reconnects to the shared folder, and disk partitions, volumes, and drive letters assigned to volumes. File Server Resource Manager (FSRM) will also be used to help manage folders and files on the file server. Using quotas, Woodgrove Bank can monitor or limit the disk space used by files within a folder. Using file screening, they can monitor or control the file types that can be saved in a folder. The reporting tools in FSRM will easily gather statistics about files. Adding the Distributed File System (DFS) service will provide a way to store copies of shared folders on multiple servers. Using DFS provides fault tolerance of shared folders by creating multiple copies, and improves shared folder access by placing copies (replicas) of shared folders on servers that are closer to the users. Separate DFS services will be on each region keeping them relatively independent from the other regions. Print Server Each site will also have the Print Server role service installed. This will allow for printer permissions which will control the actions that users can perform on a printer. Printer permissions apply to both local and shared printers. In this network re-build we 14 Proposal To Re-Design The Woodgrove Bank Network will be adding new network printers to each location. They will be listed in Active Directory and deploy with Group Policy. With the Print Server role Woodgrove Bank can use multiple printer objects for a single physical print device to customize access to the printer based on job roles. When configured, this will give priority to managers and executives. Printer pooling will also be employed to provide load balancing between the printers. 3. Security Policy Windows Server 2008 offers many tools for securing Woodgrove Bank’s servers. Windows’ Security Configuration Wizard, Security Templates snap-in, and Security Configuration and Analysis snap-in are some of those tools that Woodgrove Bank will be using. Security Configuration Wizard will be used to create and apply server security policy and keep Woodgrove Bank’s computers secure by checking for vulnerabilities. Security Templates will be used to automatically restrict some privileges or local policies for the network and allow for custom security policy to be built. Security Policy can be applied by using Group Policy objects. Security Configuration and Analysis will be used to ensure a sufficient level of security on each computer and analyze and configure local computer security (Microsoft TechNet). Auditing will be enabled in the local security policy or the Group Policy as needed. 802.1x authentication for both wired and wireless networks will use smart card devices to authenticate wireless clients. In order to provide secure authentication, 802.1x authentication will require a RADIUS server to centralize user account and authentication information. A centralized database for user authentication is required to allow wireless 15 Proposal To Re-Design The Woodgrove Bank Network clients to roam between cells but authenticate using the same account information. At a minimum, the RADIUS server must have a server certificate. To support mutual authentication, each client must also have a certificate. Certificates Certificates and encryption will be used to ensure security throughout the network. Using existing certificates or after obtaining a certification from a reputable vender, Woodgrove Bank will incorporate an Enterprise Certification Authority (CA). An additional virtual machine will be built on the NYC server and configured as the root CA. Afterwards it will be shut down and only reactivated when needed for additional security (Zacker, 2009). Each other site will each have subordinate enterprise CA issued from the parent CA in New York City. 4. Business Continuity Plan Backup and Recovery Backups would consist of a combination of Symantec backups to tape and local Windows Server Backups. All virtual sessions will be backed up to tape every Saturday using Symantec (each site has its own dedicated backup server and software) and those tapes will then be stored off site at a secure location (Symantec). However, copies of each VM session will be stored locally in addition to the copies on tape. Local Windows Server Backups will be done weekly as well (Microsoft TechNet). This will insure that all data and system states are recoverable. 16 Proposal To Re-Design The Woodgrove Bank Network Disaster Recovery Since all the servers are built on virtualization, rebuilding the infrastructure would be as simple as restoring the latest backups of each VM session to new servers. 5. Network Map 17 Proposal To Re-Design The Woodgrove Bank Network Bibliography Davis, D. (2008, 9 8). How to Install and Configure Windows Server 2008 DHCP Server. Retrieved 12 11, 2011, from WindowsNetworking.com: http://www.windowsnetworking.com/articles_tutorials/How-to-Install-ConfigureWindows-Server-2008-DHCP-Server.html Microsoft. (n.d.). Hyper-V Features. Retrieved 12 11, 2011, from Microsoft: http://www.microsoft.com/en-us/server-cloud/windows-server/hyper-vfeatures.aspx Microsoft Support. (2006, 11 1). Overview of Redundant Arrays of Inexpensive Disks (RAID). Retrieved 12 11, 2011, from Microsoft Support: http://support.microsoft.com/kb/100110 Microsoft Support. (2011, 9 11). DNS Namespace Planning. Retrieved 12 11, 2011, from Microsoft Support: http://support.microsoft.com/kb/254680 Microsoft TechNet. (n.d.). 80/20 Rule. Retrieved 12 11, 2011, from Microsoft TechNet: http://technet.microsoft.com/en-us/library/cc958936.aspx Microsoft TechNet. (n.d.). Active Directory Structure and Storage Technologies. Retrieved 12 11, 2011, from Microsoft TechNet: http://technet.microsoft.com/enus/library/cc759186(WS.10).aspx Microsoft TechNet. (n.d.). How DNS Support for Active Directory Works. Retrieved 12 11, 2011, from Microsoft TechNet: http://technet.microsoft.com/enus/library/cc759550(WS.10).aspx Microsoft TechNet. (n.d.). Namespace planning for DNS. Retrieved 11 12, 2011, from Microsoft TechNet: http://technet.microsoft.com/enus/library/cc759036(WS.10).aspx Microsoft TechNet. (n.d.). p-by-Step Guide for Windows Server 2008. Retrieved 12 11, 2011, from Microsoft TechNet: http://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&ved=0 CGkQFjAA&url=http%3A%2F%2Ftechnet.microsoft.com%2Fenus%2Flibrary%2Fcc770266(v%3Dws.10).aspx&ei=LzLlTqX0CYqU2wXS9qC6 BA&usg=AFQjCNHfEi3WRXjOQ5or1w8ZYhqSM9uWTg&sig2=wZA6QqWOwGyNs9HHHAYhw Microsoft TechNet. (n.d.). Routing and Remote Access. Retrieved 12 11, 2011, from Microsoft TechNet: http://technet.microsoft.com/en-us/network/bb545655 Microsoft TechNet. (n.d.). Server Security Policy Management in Windows Server 2008. Retrieved 12 11, 2011, from Microsoft TechNet: http://technet.microsoft.com/enus/library/cc754373(WS.10).aspx Microsoft TechNet. (n.d.). What's New in Routing and Remote Access in Windows Server 2008. Retrieved 12 11, 2011, from Microsoft TechNet: http://technet.microsoft.com/en-us/library/cc730711(WS.10).aspx Microsoft TechNet. (n.d.). Windows Deployment Services. Retrieved 12 11, 2011, from Microsoft TechNet: http://technet.microsoft.com/enus/library/cc772106(WS.10).aspx Sanders, C. (2008, 5 6). Deploying Microsoft Windows Server Update Services. Retrieved 12 11, 2011, from WindowsNetworking.com: http://www.windowsnetworking.com/articles_tutorials/deploying-microsoftwindows-server-update-services.html 18 Proposal To Re-Design The Woodgrove Bank Network Symantec.com. (n.d.). Virtual Machine Protection with Symantec NetBackup 7. Retrieved 12 11, 2011, from Symantec.com: http://eval.symantec.com/mktginfo/enterprise/white_papers/bsolution_overview_data_protection_vm_prot_with_sym_nbu7_WP_21003628.en -us.pdf Zacker, C. (2009). Windows Server 2008 Administrator. In C. Zacker, Windows Server 2008 Administrator (pp. 350-351). Hoboken: John Wiley & Sons. 19