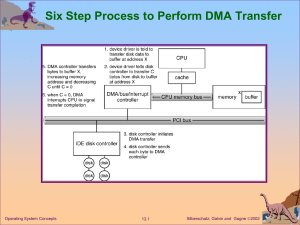
Background: Operating Systems
... – Web server: if files in disk cache, I/O wait spent mostly blocked on write to network – Networked file system client: could compile first part of file while fetching second part ...
... – Web server: if files in disk cache, I/O wait spent mostly blocked on write to network – Networked file system client: could compile first part of file while fetching second part ...
Playing it Safe: Document Destruction Best Practices - Shred-it
... It means a department or companywide commitment to shredding all documents on a regular basis. Standardising document destruction procedures will allow your organisation to align its rules and regulations with its information security goals and needs. A shred-all policy is a way to make sure there a ...
... It means a department or companywide commitment to shredding all documents on a regular basis. Standardising document destruction procedures will allow your organisation to align its rules and regulations with its information security goals and needs. A shred-all policy is a way to make sure there a ...
2012 Bond Planning Technology Project Update
... improved data analysis capabilities Significant investment in Computer & Devices Additional investment in educational technology innovation ...
... improved data analysis capabilities Significant investment in Computer & Devices Additional investment in educational technology innovation ...
A Brief Introduction To Virtualization Technologies
... the virtual machine simulates multiple instances of much (but not all) of an underlying hardware environment, particularly address spaces. ...
... the virtual machine simulates multiple instances of much (but not all) of an underlying hardware environment, particularly address spaces. ...
Incident Response and Honeypots
... Kill attacker’s processes and/or accounts. Block attacker’s network access to system. Patch and repair what you think was changed, ...
... Kill attacker’s processes and/or accounts. Block attacker’s network access to system. Patch and repair what you think was changed, ...
I/O Systems 2.
... If device can serve only one request at a time i.e., Printing Device reservation - provides exclusive access to a ...
... If device can serve only one request at a time i.e., Printing Device reservation - provides exclusive access to a ...
No Slide Title
... once the system call has completed and control is about to be returned to user mode 2. The second technique applies to critical sections that occur in an interrupt service routines – By using the processor’s interrupt control hardware to disable interrupts during a critical section, the kernel guara ...
... once the system call has completed and control is about to be returned to user mode 2. The second technique applies to critical sections that occur in an interrupt service routines – By using the processor’s interrupt control hardware to disable interrupts during a critical section, the kernel guara ...
Ceng 334 - Operating Systems
... • The scheduler allocates time based on execution priority, taking into account factors such as whether the thread belongs to a foreground or background process and how long it has been since the thread was last run • Win32 and DOS apps are preemptively multitasked. • Win16 apps are cooperatively mu ...
... • The scheduler allocates time based on execution priority, taking into account factors such as whether the thread belongs to a foreground or background process and how long it has been since the thread was last run • Win32 and DOS apps are preemptively multitasked. • Win16 apps are cooperatively mu ...
here - Help Net Security
... process, procedures, and tools that assure data can be stored reliability and retrieved by those authorised users procedures should additionally include services and utilities to log intrusion attempts and attacks aimed to penetrate security measures ...
... process, procedures, and tools that assure data can be stored reliability and retrieved by those authorised users procedures should additionally include services and utilities to log intrusion attempts and attacks aimed to penetrate security measures ...
The Linux System 21.2 Silberschatz, Galvin and Gagne ©2009
... once the system call has completed and control is about to be returned to user mode 2. The second technique applies to critical sections that occur in an interrupt service routines – By using the processor’s interrupt control hardware to disable interrupts during a critical section, the kernel guara ...
... once the system call has completed and control is about to be returned to user mode 2. The second technique applies to critical sections that occur in an interrupt service routines – By using the processor’s interrupt control hardware to disable interrupts during a critical section, the kernel guara ...
New Hardware Components for NGSCB
... These new problems have created the need for a trustworthy computing platform. Users want computers that are easy to use and that protect them from malicious programs that can damage their computers or access their personal information. Because they use their computers to process and store more and ...
... These new problems have created the need for a trustworthy computing platform. Users want computers that are easy to use and that protect them from malicious programs that can damage their computers or access their personal information. Because they use their computers to process and store more and ...
A Primer on Computer Security
... ID virus by its actions rather than structure of infected program Not driven by signature or heuristic Small set of actions ...
... ID virus by its actions rather than structure of infected program Not driven by signature or heuristic Small set of actions ...
J - The Brad Blog
... the phrase "clear error messages" being returned from Hart's products in general. - Compuware was unable to modify the MBB vote storage cards trying to use the Windows file system. The report suggests that this cannot be done, and it cannot, but this gives the impression that such information is hi ...
... the phrase "clear error messages" being returned from Hart's products in general. - Compuware was unable to modify the MBB vote storage cards trying to use the Windows file system. The report suggests that this cannot be done, and it cannot, but this gives the impression that such information is hi ...
Chapter 5 ppt下载
... More on Operating Systems • OS often called software environment or platform • Operating systems commonly used by individuals ...
... More on Operating Systems • OS often called software environment or platform • Operating systems commonly used by individuals ...
Computer Network and Infrastructure
... these processors share same main memory and I/O facilities All processors can perform the same functions Distributed operating systems provides the illusion of a single main memory and single secondary memory space used for distributed file system ...
... these processors share same main memory and I/O facilities All processors can perform the same functions Distributed operating systems provides the illusion of a single main memory and single secondary memory space used for distributed file system ...
Cybersecurity for Critical Control Systems in the Power Industry
... industrial control system. Stuxnet confirmed that industrial control systems are vulnerable and can be exploited, leading to significant damage. ...
... industrial control system. Stuxnet confirmed that industrial control systems are vulnerable and can be exploited, leading to significant damage. ...
An IPSec-based Host Architecture for Secure
... • In today’s Internet the need for efficient and secure multicast communication is growing. • Most works on designing secure multicast mechanisms concentrate on the global architecture and design of group control ...
... • In today’s Internet the need for efficient and secure multicast communication is growing. • Most works on designing secure multicast mechanisms concentrate on the global architecture and design of group control ...
OS Services #1 File
... Certain systems allow system calls to be made directly from a higher level language program, in which case the calls normally resemble predefined function or subroutine calls. As an example of how system calls are used, consider writing a simple program to read data from one file and to copy them to ...
... Certain systems allow system calls to be made directly from a higher level language program, in which case the calls normally resemble predefined function or subroutine calls. As an example of how system calls are used, consider writing a simple program to read data from one file and to copy them to ...
Multitasking (Time sharing)
... Finally, running multiple jobs concurrently requires that their ability to affect one another be limited in all phases of the operating system, including process ...
... Finally, running multiple jobs concurrently requires that their ability to affect one another be limited in all phases of the operating system, including process ...
Anonymous - ACG 6415
... In its early form, the concept had been adopted by a decentralized online community acting anonymously in a synchronized manner, usually in the direction of a loosely group-chosen goal, but the primary focus was to entertain them. Began in 2008 as a decentralized network of individuals, and beca ...
... In its early form, the concept had been adopted by a decentralized online community acting anonymously in a synchronized manner, usually in the direction of a loosely group-chosen goal, but the primary focus was to entertain them. Began in 2008 as a decentralized network of individuals, and beca ...
Chapter 1 Computer Basics
... • System software deals with the physical complexities of computer hardware. It consists of four kinds of programs: operating systems, utilities, device drivers, and language translators. • System software tells the computer – how to interpret data and instructions; – how to communicate with periphe ...
... • System software deals with the physical complexities of computer hardware. It consists of four kinds of programs: operating systems, utilities, device drivers, and language translators. • System software tells the computer – how to interpret data and instructions; – how to communicate with periphe ...
System software - Information Technology
... that describes a desired service (A) • Uses send function to pass the message to a trusted operating system process • The send function checks the message, switches the processor in protected mode and then delivers the message to the process that implements the target function • Meanwhile, the user ...
... that describes a desired service (A) • Uses send function to pass the message to a trusted operating system process • The send function checks the message, switches the processor in protected mode and then delivers the message to the process that implements the target function • Meanwhile, the user ...
SECURITY METRICS FOR ENTERPRISE INFORMATION SYSTEMS Interdisciplinarity – New Approaches and Perspectives
... vulnerabilities in a consistent fashion while at the same time allowing for personalization within each user environment. As CVSS matures, these metrics may expand or adjust making it even more accurate, flexible and representative of modern vulnerabilities and their risks. ...
... vulnerabilities in a consistent fashion while at the same time allowing for personalization within each user environment. As CVSS matures, these metrics may expand or adjust making it even more accurate, flexible and representative of modern vulnerabilities and their risks. ...