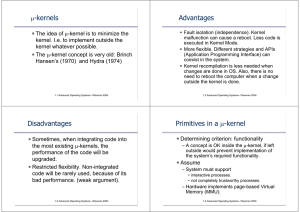
μ-kernels Advantages Disadvantages Primitives in a μ
... L4 – Was developed in GMD (Germany's national Research Center for Information Technology). It was implemented on x86 platforms. It has only 12Kbytes of code and implements just 7 system calls. Very common in use as a platform for the Linux operating system. – Some newer versions for MIPS and Alpha p ...
... L4 – Was developed in GMD (Germany's national Research Center for Information Technology). It was implemented on x86 platforms. It has only 12Kbytes of code and implements just 7 system calls. Very common in use as a platform for the Linux operating system. – Some newer versions for MIPS and Alpha p ...
MS Dos
... MS-DOS was a renamed form of 86-DOS– owned by Seattle Computer Products, written by Tim Paterson. Development of 86-DOS took only six weeks, as it was basically a clone of Digital Research's CP/M (for 8080/Z80 processors), ported to run on 8086 processors and with two notable differences compared to ...
... MS-DOS was a renamed form of 86-DOS– owned by Seattle Computer Products, written by Tim Paterson. Development of 86-DOS took only six weeks, as it was basically a clone of Digital Research's CP/M (for 8080/Z80 processors), ported to run on 8086 processors and with two notable differences compared to ...
Design of Hybrid Kernel and the Performance Improvement of
... affect the real-time characteristics of operating system, and then given an assessment method to evaluate the real-time character of operating system. Real-time systems are specific application systems in general, because specific characteristics could ensure their real-time characters on a certain ...
... affect the real-time characteristics of operating system, and then given an assessment method to evaluate the real-time character of operating system. Real-time systems are specific application systems in general, because specific characteristics could ensure their real-time characters on a certain ...
Design and implementation - CEUR
... Along with already mentioned advantages, the proposed design of the heterogeneous multi-kernel provides a number of the unique features, that can't be produced by the modern operating systems. The first advantage is native portability and supporting of heterogeneous computer systems that seems to be ...
... Along with already mentioned advantages, the proposed design of the heterogeneous multi-kernel provides a number of the unique features, that can't be produced by the modern operating systems. The first advantage is native portability and supporting of heterogeneous computer systems that seems to be ...
Introduction
... – Tires: Continental recalled Ford SUV tires in 2002 due to wire and vibration problems. – Software: Manufacturer not liable for security flaws. ...
... – Tires: Continental recalled Ford SUV tires in 2002 due to wire and vibration problems. – Software: Manufacturer not liable for security flaws. ...
Course Intro
... importance with the advancements made in computer organization and programming systems. This course is devoted to a structured survey of OS concepts and practices. Similarly, certain prominent OS will as well be introduced. Special emphasis will be assigned to Unix/Linux. Participant of the course w ...
... importance with the advancements made in computer organization and programming systems. This course is devoted to a structured survey of OS concepts and practices. Similarly, certain prominent OS will as well be introduced. Special emphasis will be assigned to Unix/Linux. Participant of the course w ...
Korea Univ Real-Time Systems
... Due to concerns such as cost and size, embedded devices usually have much less RAM and secondary storage than desktop computers, and are likely to use flash memory instead of a hard drive Since embedded devices are used for specific purposes rather than general purposes, developers optimize thei ...
... Due to concerns such as cost and size, embedded devices usually have much less RAM and secondary storage than desktop computers, and are likely to use flash memory instead of a hard drive Since embedded devices are used for specific purposes rather than general purposes, developers optimize thei ...
Computers: Understanding Technology, 3e
... Server Operating Systems Windows – Windows 2000 Server – Datacenter Server can support up to 23 processors and 64 gigabytes of data – Windows 2003 Server – Standard Edition intended for small- to medium-sized business; Datacenter Edition supports multiple servers – Windows Longhorn Server – has Win ...
... Server Operating Systems Windows – Windows 2000 Server – Datacenter Server can support up to 23 processors and 64 gigabytes of data – Windows 2003 Server – Standard Edition intended for small- to medium-sized business; Datacenter Edition supports multiple servers – Windows Longhorn Server – has Win ...
OWASP`s Ten Most Critical Web Application Security Vulnerabilities
... Be extremely careful storing keys, certs, and passwords Rethink whether you need to store the information Don’t store user passwords – use a hash like SHA-256 ...
... Be extremely careful storing keys, certs, and passwords Rethink whether you need to store the information Don’t store user passwords – use a hash like SHA-256 ...
The Architecture of a Reliable Operating System,
... Before we continue with the discussion of the components of MINIX 3, we give some examples to illustrate how our multiserver operating system actually works. Fig. 4 also shows some typical IPC interactions initiated by user processes. Although the POSIX operating system interface is implemented by m ...
... Before we continue with the discussion of the components of MINIX 3, we give some examples to illustrate how our multiserver operating system actually works. Fig. 4 also shows some typical IPC interactions initiated by user processes. Although the POSIX operating system interface is implemented by m ...
Physician Office Staff Security Access Form Office Staff Information
... I understand that the HCA affiliated facility or business entity (the “Company”) at which I have privileges or for which I work, volunteer or provide services manages health information as part of its mission to treat patients. Further, I understand that the Company has a legal and ethical responsib ...
... I understand that the HCA affiliated facility or business entity (the “Company”) at which I have privileges or for which I work, volunteer or provide services manages health information as part of its mission to treat patients. Further, I understand that the Company has a legal and ethical responsib ...
Module 3: Operating
... Additional functions exist not for helping the user, but rather for ensuring efficient system operation. • Resource allocation – allocating resources to multiple users or multiple jobs running at the same time. • Accounting – keep track of and record which users use how much and what kinds of comput ...
... Additional functions exist not for helping the user, but rather for ensuring efficient system operation. • Resource allocation – allocating resources to multiple users or multiple jobs running at the same time. • Accounting – keep track of and record which users use how much and what kinds of comput ...
OWASP_Flyer_Sep06
... OWASP WebScarab Project - a tool for performing all types of security testing on web applications and web services ...
... OWASP WebScarab Project - a tool for performing all types of security testing on web applications and web services ...
security in the post-Internet era
... design tradeoff examples • defense-in-depth conjecture (for N layers) – Security: MTTE (exploit) N**2 – Functionality: MTTI (innovation) N**2 – Supportability: MTTR (repair) N**2 ...
... design tradeoff examples • defense-in-depth conjecture (for N layers) – Security: MTTE (exploit) N**2 – Functionality: MTTI (innovation) N**2 – Supportability: MTTR (repair) N**2 ...
What is an Operating System?
... Protection and Security Protection – any mechanism for controlling access of processes or ...
... Protection and Security Protection – any mechanism for controlling access of processes or ...
Chapter 1: OS overview
... Protection and Security Protection – any mechanism for controlling access of processes or ...
... Protection and Security Protection – any mechanism for controlling access of processes or ...
CS5460: Operating Systems
... 7. Lots and lots of computers per person – Embedded systems » Cars commonly have 50+ processors » Cars, airplanes, factories run a huge amount of software – Mobile computing » PCs exceed the needs of many current computer users » Rise of smart phones and tablets – Cloud computing » Virtuali ...
... 7. Lots and lots of computers per person – Embedded systems » Cars commonly have 50+ processors » Cars, airplanes, factories run a huge amount of software – Mobile computing » PCs exceed the needs of many current computer users » Rise of smart phones and tablets – Cloud computing » Virtuali ...
Module 7: Process Synchronization
... ■ Uses spinlocks on multiprocessor systems. Threads holding spinlocks ...
... ■ Uses spinlocks on multiprocessor systems. Threads holding spinlocks ...
Circumvention Defense Network (CDN)
... Peer-to-Peer, Mixed Cascade, Onion Routing and LocalHost as well as other evasive circumvention tools designed to bypass Internet access controls. These tools are distributed in a variety of ways including through professional organizations, whose users can include younger professionals, students or ...
... Peer-to-Peer, Mixed Cascade, Onion Routing and LocalHost as well as other evasive circumvention tools designed to bypass Internet access controls. These tools are distributed in a variety of ways including through professional organizations, whose users can include younger professionals, students or ...
PPT
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
Security considerations for M2M - IEEE 802 LAN/MAN Standards
... attacks against the core network. They may also include changing the device’s authorized physical location in an unauthorized fashion or attacks on the radio access network, using a rogue device. ...
... attacks against the core network. They may also include changing the device’s authorized physical location in an unauthorized fashion or attacks on the radio access network, using a rogue device. ...
Information Security Policy
... committed to protecting the employees, partners and the company from illegal or damaging actions by individuals, either knowingly or unknowingly. The company will maintain an approved list of technologies and devices and personnel with access to such devices as detailed in Appendix B ...
... committed to protecting the employees, partners and the company from illegal or damaging actions by individuals, either knowingly or unknowingly. The company will maintain an approved list of technologies and devices and personnel with access to such devices as detailed in Appendix B ...