Operating Systems I: Chapter 1
... The OS is a program that acts as an intermediary between the application programs and the hardware resources – All communication requires hardware resources, thus the OS is also an intermediary between users and applications The purpose of any OS is to provide an environment in which: – users can (c ...
... The OS is a program that acts as an intermediary between the application programs and the hardware resources – All communication requires hardware resources, thus the OS is also an intermediary between users and applications The purpose of any OS is to provide an environment in which: – users can (c ...
$doc.title
... administrators have full access, HR managers have less permission than the administrators, and data entry operators have no access to resources. Which of the following access control models is implemented in the organization? A. Role-based access control (RBAC) B. Network-based access control (NBAC) ...
... administrators have full access, HR managers have less permission than the administrators, and data entry operators have no access to resources. Which of the following access control models is implemented in the organization? A. Role-based access control (RBAC) B. Network-based access control (NBAC) ...
Virtualization
... issues when it comes to virtualization. Certain privilegedmode instructions do not trap, and can return different results based upon the mode. For example, the x86 STR instruction retrieves the security state, but the value returned is based upon the particular requester's privilege level. This is p ...
... issues when it comes to virtualization. Certain privilegedmode instructions do not trap, and can return different results based upon the mode. For example, the x86 STR instruction retrieves the security state, but the value returned is based upon the particular requester's privilege level. This is p ...
Chapter 1: Introduction
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs Concurrency by multiplexing the CPUs among the processes / threads ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs Concurrency by multiplexing the CPUs among the processes / threads ...
An operating system - Bilkent University Computer Engineering
... Clustered Systems • Like multiprocessor systems, but multiple systems working together – Usually sharing storage via a storage-area network (SAN) – Provides a high-availability service which survives failures • Asymmetric clustering has one machine in hot-standby mode • Symmetric clustering has mul ...
... Clustered Systems • Like multiprocessor systems, but multiple systems working together – Usually sharing storage via a storage-area network (SAN) – Provides a high-availability service which survives failures • Asymmetric clustering has one machine in hot-standby mode • Symmetric clustering has mul ...
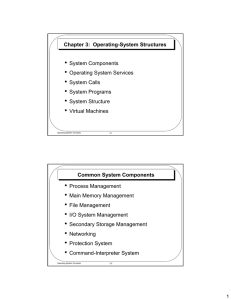
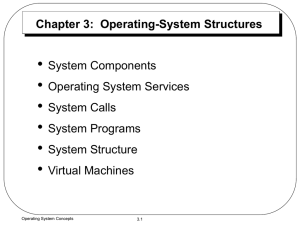
Chapter 3: Operating-System Structures • System Components
... compiled, it must be loaded into memory to be executed. The system may provide loaders, linkage editors and debuggers. – Communications: Programs provide mechanism for creating virtual connections among processes, users, and computer systems, such as sending messages and transferring files. Operatin ...
... compiled, it must be loaded into memory to be executed. The system may provide loaders, linkage editors and debuggers. – Communications: Programs provide mechanism for creating virtual connections among processes, users, and computer systems, such as sending messages and transferring files. Operatin ...
The Essence of UNIX and Linux
... Linux and UNIX • Linux is a UNIX-like operating system – Not written from the traditional UNIX code – Kernel created to look and act like UNIX • Enhancements include the POSIX standards • Linus Torvalds released it free of charge in 1991 ...
... Linux and UNIX • Linux is a UNIX-like operating system – Not written from the traditional UNIX code – Kernel created to look and act like UNIX • Enhancements include the POSIX standards • Linus Torvalds released it free of charge in 1991 ...
ppt
... expensive on the scale of a remote procedure call. A server maintains a stock of idle server processes to avoid procedure creation. Each packet contains a process ID for both source and destination. Ethernet driver checks process ID of packet and forwards to correct process ...
... expensive on the scale of a remote procedure call. A server maintains a stock of idle server processes to avoid procedure creation. Each packet contains a process ID for both source and destination. Ethernet driver checks process ID of packet and forwards to correct process ...
chapter4
... • System software deals with the physical complexities of computer hardware. It consists of four kinds of programs: operating systems, utilities, device drivers, and language translators. • System software tells the computer – how to interpret data and instructions; – how to communicate with periphe ...
... • System software deals with the physical complexities of computer hardware. It consists of four kinds of programs: operating systems, utilities, device drivers, and language translators. • System software tells the computer – how to interpret data and instructions; – how to communicate with periphe ...
Data and Applications Security - The University of Texas at Dallas
... Other forms of attacks, such as distributed denial of service attacks, sometimes rely on B.O.A. B.O.A. exploit the memory organization of the traditional activation stack model to overwrite the return address stored on the stack. This memory organization can be slightly changed so as to prevent buff ...
... Other forms of attacks, such as distributed denial of service attacks, sometimes rely on B.O.A. B.O.A. exploit the memory organization of the traditional activation stack model to overwrite the return address stored on the stack. This memory organization can be slightly changed so as to prevent buff ...
Security+ Guide to Network Security Fundamentals, Fourth Edition
... Security+ Guide to Network Security Fundamentals, Fourth Edition ...
... Security+ Guide to Network Security Fundamentals, Fourth Edition ...
AUSI-13- (Software)
... • OS is controlled by the kernel. • What is a kernel? – Kernel is the supervisor program that manage the memory and devices – Kernel is loaded into the memory from the hard disk (or other storage) during booting until computer is turned off – It is known as memory resident (because it resides in mem ...
... • OS is controlled by the kernel. • What is a kernel? – Kernel is the supervisor program that manage the memory and devices – Kernel is loaded into the memory from the hard disk (or other storage) during booting until computer is turned off – It is known as memory resident (because it resides in mem ...
Module 3: Operating
... compiled, it must be loaded into memory to be executed. The system may provide loaders, linkage editors and debuggers. – Communications: Programs provide mechanism for creating virtual connections among processes, users, and computer systems, such as sending messages and transferring files. Operatin ...
... compiled, it must be loaded into memory to be executed. The system may provide loaders, linkage editors and debuggers. – Communications: Programs provide mechanism for creating virtual connections among processes, users, and computer systems, such as sending messages and transferring files. Operatin ...
2. Operating System Structure
... Example: The UNIX command to delete a file rm file.txt searches for a file rm, loads it into memory, and executes it with the parameter file.txt. ∎ Addition of new commands is easy. The interpreter program is small and does not have to be changed. November 2016 ...
... Example: The UNIX command to delete a file rm file.txt searches for a file rm, loads it into memory, and executes it with the parameter file.txt. ∎ Addition of new commands is easy. The interpreter program is small and does not have to be changed. November 2016 ...
ppt
... by Linus Torvalds, with the major design goal of UNIX compatibility, released as open source Its history has been one of collaboration by many users from all around the world, corresponding almost exclusively over the Internet It has been designed to run efficiently and reliably on ...
... by Linus Torvalds, with the major design goal of UNIX compatibility, released as open source Its history has been one of collaboration by many users from all around the world, corresponding almost exclusively over the Internet It has been designed to run efficiently and reliably on ...
9. Application/Kernel Interface
... ... but it is still too high level for many OS interactions E.g., it does not specify file systems, network interfaces or power management C applications deal with portability with I I I ...
... ... but it is still too high level for many OS interactions E.g., it does not specify file systems, network interfaces or power management C applications deal with portability with I I I ...
Network Flow Analysis in Information Security Strategy
... This material has been approved for public release and unlimited distribution except as restricted below. This material may be reproduced in its entirety, without modification, and freely distributed in written or electronic form without requesting formal permission. Permission is required for any o ...
... This material has been approved for public release and unlimited distribution except as restricted below. This material may be reproduced in its entirety, without modification, and freely distributed in written or electronic form without requesting formal permission. Permission is required for any o ...
Social engineering - Information Systems
... Understand information privacy, accuracy, property, and accessibility Understand types of computer crime Understand the terms virus, worm, Trojan horse, and logic or time bomb ...
... Understand information privacy, accuracy, property, and accessibility Understand types of computer crime Understand the terms virus, worm, Trojan horse, and logic or time bomb ...
Chapter 19: Security
... – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter its behavior – May contain m ...
... – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter its behavior – May contain m ...
Chapter 19: Security - Murray State University
... – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter its behavior – May contain m ...
... – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter its behavior – May contain m ...
Chapter 19: Security
... – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter its behavior – May contain m ...
... – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter its behavior – May contain m ...
Guide to Firewalls and Network Security with Intrusion Detection and
... Reduce time and make the job easier for the security administrator Reduce chance of configuration errors that might result if the same changes were made manually for each firewall on the network ...
... Reduce time and make the job easier for the security administrator Reduce chance of configuration errors that might result if the same changes were made manually for each firewall on the network ...
GSI Credential Management with MyProxy
... – Confidentiality: Solution using proxy encryption techniques whereby the plaintext is not exposed at list server; instead, list server simply transforms encrypted messages – Integrity and authentication: Solution using digital signatures where certificate validation is provided by list server – Ant ...
... – Confidentiality: Solution using proxy encryption techniques whereby the plaintext is not exposed at list server; instead, list server simply transforms encrypted messages – Integrity and authentication: Solution using digital signatures where certificate validation is provided by list server – Ant ...
A Hypervisor Based Security Testbed Dan Duchamp and Greg DeAngelis
... For this step, we use a modified version of Emulab’s “Netbuild” client in which nodes, links between them, and link properties are specified visually. A significant difference, however, is that our experiment configuration is compiled into XML and the XML is then loaded into the database. The reason ...
... For this step, we use a modified version of Emulab’s “Netbuild” client in which nodes, links between them, and link properties are specified visually. A significant difference, however, is that our experiment configuration is compiled into XML and the XML is then loaded into the database. The reason ...
2. Operating System Models
... With all the processor-specific code is isolated into the microkernel, changes needed to run on a new processor are fewer and grouped logically together. It makes possible for running an operating system on more than one processor. With increasingly complex monolithic systems, its extension becomes ...
... With all the processor-specific code is isolated into the microkernel, changes needed to run on a new processor are fewer and grouped logically together. It makes possible for running an operating system on more than one processor. With increasingly complex monolithic systems, its extension becomes ...