Virtualized Broadband Network Gateway
... The vBNG has been designoptimized for Linux 64-bit operating systems (CentOS, Red hat Enterprise Linux, and Ubuntu), in combination with the KWM/QEMU hypervisor. The vBNG can optionally be deployed using the Red Hat® OpenStack® Platform or RDO project distribution. ...
... The vBNG has been designoptimized for Linux 64-bit operating systems (CentOS, Red hat Enterprise Linux, and Ubuntu), in combination with the KWM/QEMU hypervisor. The vBNG can optionally be deployed using the Red Hat® OpenStack® Platform or RDO project distribution. ...
Chapter 1: Introduction
... Many processes can run at once without performance deterioration true parallelism vs pseudo parallelism of a multitasking system on a uniprocessor. Most modern operating systems support SMP ...
... Many processes can run at once without performance deterioration true parallelism vs pseudo parallelism of a multitasking system on a uniprocessor. Most modern operating systems support SMP ...
Proceedings of HotOS IX: The 9th Workshop on USENIX Association
... Bershad et al. [3] used feedback from special hardware to dynamically avoid conflict misses in large direct-mapped caches by reassigning the conflicting virtual memory pages. In the AppLeS [2] project, an application-level scheduler is used to adaptively and dynamically schedule individual applicatio ...
... Bershad et al. [3] used feedback from special hardware to dynamically avoid conflict misses in large direct-mapped caches by reassigning the conflicting virtual memory pages. In the AppLeS [2] project, an application-level scheduler is used to adaptively and dynamically schedule individual applicatio ...
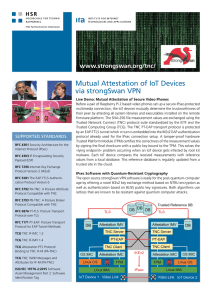
Mutual Attestation of IoT Devices via strongSwan VPN
... Live Demo: Mutual Attestation of Secure Video Phones Before a pair of Raspberry Pi 2 based video phones set up a secure IPsec-protected multimedia connection, the IoT devices mutually determine the trustworthiness of their peer by attesting all system libraries and executables installed on the remot ...
... Live Demo: Mutual Attestation of Secure Video Phones Before a pair of Raspberry Pi 2 based video phones set up a secure IPsec-protected multimedia connection, the IoT devices mutually determine the trustworthiness of their peer by attesting all system libraries and executables installed on the remot ...
16MCA24 - PESIT South
... In particular, the course will consider inherent functionality and processing of program execution . The emphasis of the course will be placed on understanding how the various elements that underlie operating system interact and provides services for execution of application software. 3. COURSE OBJE ...
... In particular, the course will consider inherent functionality and processing of program execution . The emphasis of the course will be placed on understanding how the various elements that underlie operating system interact and provides services for execution of application software. 3. COURSE OBJE ...
Faithful Virtualization on a Real
... Faithful virtualization is to construct a virtual machine that allows most of the guest code to execute directly on the CPU. When guest code cannot be executed, emulation is used for these specific parts. The basic technique for faithful virtualization is called trap and emulate. The guest code is e ...
... Faithful virtualization is to construct a virtual machine that allows most of the guest code to execute directly on the CPU. When guest code cannot be executed, emulation is used for these specific parts. The basic technique for faithful virtualization is called trap and emulate. The guest code is e ...
PowerPoint
... kernel-protected communication channel. Communication is accomplished by sending messages to ports; messages are queued at the destination port if no thread is immediately ready to receive them. Ports are protected by kernel-managed capabilities, or port rights; a task must have a port right to send ...
... kernel-protected communication channel. Communication is accomplished by sending messages to ports; messages are queued at the destination port if no thread is immediately ready to receive them. Ports are protected by kernel-managed capabilities, or port rights; a task must have a port right to send ...
Xen and the Art of Virtualisation
... – CPU: typical VMMs perform trap-and-emulate whereby the guest operating system executes in a lower processor privilege level/ring, and the access to privileged state or the execution of privileged instructions is captured and simulated by the VMM. Because Xen requires porting and utilizes paravirtu ...
... – CPU: typical VMMs perform trap-and-emulate whereby the guest operating system executes in a lower processor privilege level/ring, and the access to privileged state or the execution of privileged instructions is captured and simulated by the VMM. Because Xen requires porting and utilizes paravirtu ...
00-course description
... Email Communication: Anonymous emails will be ignored. When you send an email, you should use your PNU account and make sure to put “OS 340D " in the subject line and identify yourself with your group code and Student ID in the email message (body). Late submissions of any course material is not all ...
... Email Communication: Anonymous emails will be ignored. When you send an email, you should use your PNU account and make sure to put “OS 340D " in the subject line and identify yourself with your group code and Student ID in the email message (body). Late submissions of any course material is not all ...
00-course description - pnu-cs-os
... Email Communication: Anonymous emails will be ignored. When you send an email, you should use your PNU account and make sure to put “OS 340D " in the subject line and identify yourself with your group code and Student ID in the email message (body). Late submissions of any course material is not all ...
... Email Communication: Anonymous emails will be ignored. When you send an email, you should use your PNU account and make sure to put “OS 340D " in the subject line and identify yourself with your group code and Student ID in the email message (body). Late submissions of any course material is not all ...
Phishing and whaling – Don`t get hooked!
... the attackers often gather information about their targets to increase their probability of success. With the advent of social media, as well as other information on the internet there is often a wealth of information that can be easily obtained to assist attackers learn about, and even convincingly ...
... the attackers often gather information about their targets to increase their probability of success. With the advent of social media, as well as other information on the internet there is often a wealth of information that can be easily obtained to assist attackers learn about, and even convincingly ...
ppt
... Most OS’s can run many applications with acceptable performance. Other OS’s can run a few applications with excellent performance. It’s difficult or impossible to find OS’s that can do both (but it would be nice). ...
... Most OS’s can run many applications with acceptable performance. Other OS’s can run a few applications with excellent performance. It’s difficult or impossible to find OS’s that can do both (but it would be nice). ...
CCNPv5 Module 5 Lesson 1
... SNMP asks agents embedded in network devices for information or tells the agents to do something. ...
... SNMP asks agents embedded in network devices for information or tells the agents to do something. ...
6 - University of South Florida St. Petersburg
... Most organizations with Internet connection have a router serving as interface to Internet Many of these routers can be configured to reject packets that organization does not allow into network Drawbacks include a lack of auditing and strong authentication ...
... Most organizations with Internet connection have a router serving as interface to Internet Many of these routers can be configured to reject packets that organization does not allow into network Drawbacks include a lack of auditing and strong authentication ...
UNIX Operating System
... A journaling file system keeps track of the changes that will be made in a journal (usually a circular log in a dedicated area of the file system) before committing them to the main file system. In the event of a system crash or power failure, such file systems are quicker to bring back online and l ...
... A journaling file system keeps track of the changes that will be made in a journal (usually a circular log in a dedicated area of the file system) before committing them to the main file system. In the event of a system crash or power failure, such file systems are quicker to bring back online and l ...
Designing a future Internet: Architecture and requirements
... Identity itself should be rich and heterogeneous ...
... Identity itself should be rich and heterogeneous ...
Chapter 1: Introduction What is an Operating System?
... in memory and on disk (the CPU is allocated to a job only if the job is in memory). A job swapped in and out of memory to the disk. On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control state ...
... in memory and on disk (the CPU is allocated to a job only if the job is in memory). A job swapped in and out of memory to the disk. On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control state ...
Chapter 14 Virtual Machines Operating Systems:
... The operating system in the virtual machine, Linux or Microsoft Windows, has specialized paravirtualization support as part of the kernel, as well as specific paravirtualization drivers that allow the OS and hypervisor to work together more efficiently with the overhead of the hypervisor translation ...
... The operating system in the virtual machine, Linux or Microsoft Windows, has specialized paravirtualization support as part of the kernel, as well as specific paravirtualization drivers that allow the OS and hypervisor to work together more efficiently with the overhead of the hypervisor translation ...
Chp. 8 - Cisco Networking Academy
... Telnet servers –the Secure Shell (SSH) protocol allows for authentication and encryption of a remote management connection FTP servers - FTP can use SSL to securely exchange authentication and data. Some versions of FTP can also use SSH. File servers - In most cases, file server protocols do not off ...
... Telnet servers –the Secure Shell (SSH) protocol allows for authentication and encryption of a remote management connection FTP servers - FTP can use SSL to securely exchange authentication and data. Some versions of FTP can also use SSH. File servers - In most cases, file server protocols do not off ...
Messenger-Based Operating Systems - (CUI)
... is distributed and used. Messengers can, for instance, pool their money, or accumulate it, or obtain resources when prices are low (low demand) and sell it when demand is high. Such a currency mechanism does of course not solve the (global) allocation problem, but it provides the instrument to imple ...
... is distributed and used. Messengers can, for instance, pool their money, or accumulate it, or obtain resources when prices are low (low demand) and sell it when demand is high. Such a currency mechanism does of course not solve the (global) allocation problem, but it provides the instrument to imple ...
Linux Kernel—File Systems
... A mounted filesystem descriptor contains information common to filesystem types, pointers for functions provided by physical filesystem kernel code, and private data maintained by the physical filesystem code An inode descriptor contains pointers to functions that can be used to act on any file An o ...
... A mounted filesystem descriptor contains information common to filesystem types, pointers for functions provided by physical filesystem kernel code, and private data maintained by the physical filesystem code An inode descriptor contains pointers to functions that can be used to act on any file An o ...
9781435420168_PPT_CH01
... Computer can be subject of attack or object of attack; two types of attacks: direct and indirect Information security not an absolute: a process, not a goal; should balance reasonable access and availability while protecting against threats Information security performs four functions: – Prote ...
... Computer can be subject of attack or object of attack; two types of attacks: direct and indirect Information security not an absolute: a process, not a goal; should balance reasonable access and availability while protecting against threats Information security performs four functions: – Prote ...
PPT - Defcon
... • Overwrite the first seven bytes of SwapContext with a jump to our Detour function • The EDI register points to the KTHREAD of the thread to be scheduled to run • Our Detour function follows the KTHREAD to the EPROCESS block and determines if it is still appropriately linked in the list of active p ...
... • Overwrite the first seven bytes of SwapContext with a jump to our Detour function • The EDI register points to the KTHREAD of the thread to be scheduled to run • Our Detour function follows the KTHREAD to the EPROCESS block and determines if it is still appropriately linked in the list of active p ...