What is an Operating System?
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
UNIX Software Tools
... an email system) the software on the local host is the client and the software on the remote host is the server. In a X-Windows system this is reversed. The X-Windows server is on your local machine. It provides the following services: keyboard input, mouse, procedures for drawing on the screen, ...
... an email system) the software on the local host is the client and the software on the remote host is the server. In a X-Windows system this is reversed. The X-Windows server is on your local machine. It provides the following services: keyboard input, mouse, procedures for drawing on the screen, ...
Module 4: Processes
... should be brought into the ready queue Short-term scheduler (or CPU scheduler) – selects which process ...
... should be brought into the ready queue Short-term scheduler (or CPU scheduler) – selects which process ...
1. design principle
... the same. First they make computer hardware easier to use. Second the operating systems shares the resources among the different users and effectively manage them. The design of operating system is becoming more modular. The operating systems have evolved in a great way from the earliest Simple batc ...
... the same. First they make computer hardware easier to use. Second the operating systems shares the resources among the different users and effectively manage them. The design of operating system is becoming more modular. The operating systems have evolved in a great way from the earliest Simple batc ...
Rapid Response to the Advanced Persistent Threat (APT)
... ZoneFox takes a radically different approach to the software-agent model. The agent installed on each system performs no analysis or preventative actions on the endpoint but instead simply gathers and sends data for alerting or investigation. This ‘dumb agent’ approach has significant advantages as ...
... ZoneFox takes a radically different approach to the software-agent model. The agent installed on each system performs no analysis or preventative actions on the endpoint but instead simply gathers and sends data for alerting or investigation. This ‘dumb agent’ approach has significant advantages as ...
operating system (2a) - BackBenchersCafe.com
... FCFS, SJF, Round Robin (quantum=1). What is turnaround time and waiting time of each process for each of the above scheduling algorithms? 6. (a) What is virtual memory. Explain it with its advantages and disadvantages.(10) (b) Discuss with example about the FIFO page replacement algorithm. 7. Descri ...
... FCFS, SJF, Round Robin (quantum=1). What is turnaround time and waiting time of each process for each of the above scheduling algorithms? 6. (a) What is virtual memory. Explain it with its advantages and disadvantages.(10) (b) Discuss with example about the FIFO page replacement algorithm. 7. Descri ...
Intrusion Detection and Prevention
... Windows malware just loves this folder! Look for any folders or files with a different date modified timestamp. ...
... Windows malware just loves this folder! Look for any folders or files with a different date modified timestamp. ...
Chap 1: Introduction
... Provides high reliability. Asymmetric clustering: one server runs the application while other servers standby. Symmetric clustering: all N hosts are running the application. ...
... Provides high reliability. Asymmetric clustering: one server runs the application while other servers standby. Symmetric clustering: all N hosts are running the application. ...
Syllabus - Jordan University of Science and Technology
... Class lectures, lecture notes, and quizzes are designed to achieve the course objectives. You should read the assigned chapters before class, and participate in class and do whatever it takes for you to grasp this material. Also, ask any question related to O.S. You are responsible for all material ...
... Class lectures, lecture notes, and quizzes are designed to achieve the course objectives. You should read the assigned chapters before class, and participate in class and do whatever it takes for you to grasp this material. Also, ask any question related to O.S. You are responsible for all material ...
The Multikernel: A new OS architecture for scalable
... – Adapting the OS to run on hardware with new performance characteristics will not require extensive changes to the code base – Isolate the distributed communication algorithms from hardware implementation details – Enable late binding of both the protocol implementation & message transport ...
... – Adapting the OS to run on hardware with new performance characteristics will not require extensive changes to the code base – Isolate the distributed communication algorithms from hardware implementation details – Enable late binding of both the protocol implementation & message transport ...
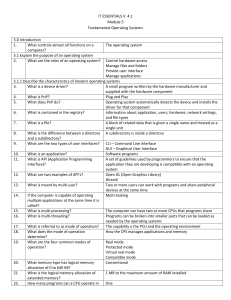
IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems 5
... A real-mode application runs within a protected-mode operating system Creates the environment of an earlier operating system for applications that are not compatible with the current operating system This allows an application to be run even if the user does not have the required administrative priv ...
... A real-mode application runs within a protected-mode operating system Creates the environment of an earlier operating system for applications that are not compatible with the current operating system This allows an application to be run even if the user does not have the required administrative priv ...
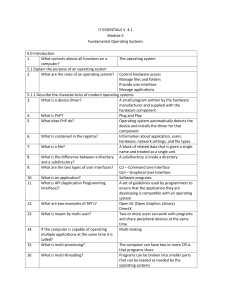
IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems
... A real-mode application runs within a protected-mode operating system Creates the environment of an earlier operating system for applications that are not compatible with the current operating system This allows an application to be run even if the user does not have the required administrative priv ...
... A real-mode application runs within a protected-mode operating system Creates the environment of an earlier operating system for applications that are not compatible with the current operating system This allows an application to be run even if the user does not have the required administrative priv ...
I/O Systems
... • Get: return next character of input stream • Put: append character to output stream • Close: release exclusive access ...
... • Get: return next character of input stream • Put: append character to output stream • Close: release exclusive access ...
Chapter 11 Outline
... The transport method encrypts only the data portion of a packet, thus enabling an outsider to see the source and destination IP addresses. This protects the data being transmitted. Protection of the data portion of a packet is referred to as content protection. ...
... The transport method encrypts only the data portion of a packet, thus enabling an outsider to see the source and destination IP addresses. This protects the data being transmitted. Protection of the data portion of a packet is referred to as content protection. ...
Real-Time Georgia…….
... Too many single points of network & system failure Inadequate data back-up & storage procedures Often there is no real communicated security policy Networks open to Cyber Attacks and Cyber Crime Small skill base of specialist IT security personnel ...
... Too many single points of network & system failure Inadequate data back-up & storage procedures Often there is no real communicated security policy Networks open to Cyber Attacks and Cyber Crime Small skill base of specialist IT security personnel ...
Chapter 1: Introduction What is an Operating System?
... in memory and on disk (the CPU is allocated to a job only if the job is in memory). ■ A job swapped in and out of memory to the disk. ■ On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control state ...
... in memory and on disk (the CPU is allocated to a job only if the job is in memory). ■ A job swapped in and out of memory to the disk. ■ On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control state ...
pdf-1 - IFSC-USP
... in memory and on disk (the CPU is allocated to a job only if the job is in memory). ■ A job swapped in and out of memory to the disk. ■ On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control state ...
... in memory and on disk (the CPU is allocated to a job only if the job is in memory). ■ A job swapped in and out of memory to the disk. ■ On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control state ...
Abstract View of System Components
... in memory and on disk (the CPU is allocated to a job only if the job is in memory). A job swapped in and out of memory to the disk. On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control state ...
... in memory and on disk (the CPU is allocated to a job only if the job is in memory). A job swapped in and out of memory to the disk. On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control state ...
Course Overview - Cyber Security Lab
... Need for Security Today’s businesses rely on extensive information communication with public networks and systems for survival and profitability. In the modern business environment, regardless of the business type, all data resident on a computer system is both valuable and vulnerable. Business is c ...
... Need for Security Today’s businesses rely on extensive information communication with public networks and systems for survival and profitability. In the modern business environment, regardless of the business type, all data resident on a computer system is both valuable and vulnerable. Business is c ...
What is an Operating System?
... The CPU is multiplexed among several jobs that are kept in memory and on disk (the CPU is allocated to a job only if the job is in memory). A job swapped in and out of memory to the disk. On-line communication between the user and the system is provided; when the operating system finishes the execut ...
... The CPU is multiplexed among several jobs that are kept in memory and on disk (the CPU is allocated to a job only if the job is in memory). A job swapped in and out of memory to the disk. On-line communication between the user and the system is provided; when the operating system finishes the execut ...
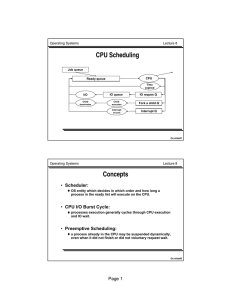
Page 1 • Scheduler: • CPU I/O Burst Cycle: • Preemptive Scheduling:
... OS entity which decides in which order and how long a process in the ready list will execute on the CPU. ...
... OS entity which decides in which order and how long a process in the ready list will execute on the CPU. ...
Federal Systems Level Guidance for Securing
... As most of us know, routers are the traffic cops of computer networks. Routers direct and control data flowing across networks and the Internet. Network administrators and security officers work in conjunction to secure network perimeters. They use routers to control network access, ward-off attacks ...
... As most of us know, routers are the traffic cops of computer networks. Routers direct and control data flowing across networks and the Internet. Network administrators and security officers work in conjunction to secure network perimeters. They use routers to control network access, ward-off attacks ...