Accessing Wireless Networks Safely Brochure
... schedule for our Digital Self Defense workshops, access security tools and software, or find out more ways to protect yourself. ...
... schedule for our Digital Self Defense workshops, access security tools and software, or find out more ways to protect yourself. ...
Real Time Operating Systems for IEC 61508 Mike Medoff
... so has tremendous advantages when going through a certification. First off, it allows you to identify non-safety critical tasks that do not need to be developed with the same level of rigor in terms of process and on-line diagnostics. This can greatly simplify the effort involved in the certificati ...
... so has tremendous advantages when going through a certification. First off, it allows you to identify non-safety critical tasks that do not need to be developed with the same level of rigor in terms of process and on-line diagnostics. This can greatly simplify the effort involved in the certificati ...
Five Business Takeaways from Gartner`s “Web
... Unlike traditional firewalls, NGFWs are able to recognize what applications are communicating on your network. NGFW vendors call this “application awareness,” which is the source of the confusion. Application awareness is irrelevant for preventing attacks on your web applications—exactly the thing a ...
... Unlike traditional firewalls, NGFWs are able to recognize what applications are communicating on your network. NGFW vendors call this “application awareness,” which is the source of the confusion. Application awareness is irrelevant for preventing attacks on your web applications—exactly the thing a ...
Common Endpoint Locator Pools (CELP)
... to know know that that different different locators locators refer refer to to same same endpoint? endpoint? Suggestion: Suggestion: That’s That’s what what domain domain names names or or URIs URIs are are for… for… ...
... to know know that that different different locators locators refer refer to to same same endpoint? endpoint? Suggestion: Suggestion: That’s That’s what what domain domain names names or or URIs URIs are are for… for… ...
Module 3: Operating-System Structures
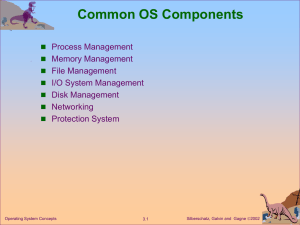
... memory, files, and I/O devices, to accomplish its task. The operating system is responsible for. Process creation and deletion. Process suspension and resumption. Mechanisms for synchronization and communication ...
... memory, files, and I/O devices, to accomplish its task. The operating system is responsible for. Process creation and deletion. Process suspension and resumption. Mechanisms for synchronization and communication ...
Linux Help Session
... To logically organize sets of user accounts To allow users to share files within their group or groups Every user is assigned to at least one group The file /etc/group contains a one-line entry for each group on the system ...
... To logically organize sets of user accounts To allow users to share files within their group or groups Every user is assigned to at least one group The file /etc/group contains a one-line entry for each group on the system ...
William Stallings, Cryptography and Network Security 3/e
... the internal network is invisible to the Internet. Similarly, the inside router advertises only the existence of the screened subnet to the internal network; therefore, the systems on the inside network cannot construct direct routes to the Internet. ...
... the internal network is invisible to the Internet. Similarly, the inside router advertises only the existence of the screened subnet to the internal network; therefore, the systems on the inside network cannot construct direct routes to the Internet. ...
Figure 5.01
... Utilization of Multiprocessor Architectures Threads may be running in parallel on different processors ...
... Utilization of Multiprocessor Architectures Threads may be running in parallel on different processors ...
Windows, Linux and Mac Operating system Booting Process: a
... where hardware configuration and detection has been perform, by looking and listen the errors and diagnosis reports e.g. Error codes, beeps codes, numeric codes. Will take care of identifying the Master boot record for the initializing the booting process. Step02: Now BIOS will look for the Booting ...
... where hardware configuration and detection has been perform, by looking and listen the errors and diagnosis reports e.g. Error codes, beeps codes, numeric codes. Will take care of identifying the Master boot record for the initializing the booting process. Step02: Now BIOS will look for the Booting ...
ch1
... Each processor runs and identical copy of the operating system Many processes can run at once without performance ...
... Each processor runs and identical copy of the operating system Many processes can run at once without performance ...
MODULE NAME: INFORMATION TECHNOLOGY 2
... of most networks. It is a very fast computer with a large amount of RAM and storage space, along with a fast network interface card. The network operating system software resides on this computer, along with any software applications and data files that need to be shared. ...
... of most networks. It is a very fast computer with a large amount of RAM and storage space, along with a fast network interface card. The network operating system software resides on this computer, along with any software applications and data files that need to be shared. ...
What is an Operating System?
... When the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard ...
... When the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard ...
Principles of Operating Systems
... • Resource allocation among users, applications • Isolation of different users, applications from each other • Communication between users, applications ...
... • Resource allocation among users, applications • Isolation of different users, applications from each other • Communication between users, applications ...
hw1_wet
... kernel/syscall_tags.c that you will have to create and add to the kernel. Update the makefile in that directory to compile your new file too. (Tip: add it to obj-y). 2. Update sched.h (constant + new fields definition) 3. Update entry.S (add new system call number) 4. Make any necessary changes in t ...
... kernel/syscall_tags.c that you will have to create and add to the kernel. Update the makefile in that directory to compile your new file too. (Tip: add it to obj-y). 2. Update sched.h (constant + new fields definition) 3. Update entry.S (add new system call number) 4. Make any necessary changes in t ...
What is an Operating System?
... When the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard ...
... When the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard ...
Computer Networks - Home - KSU Faculty Member websites
... Network operating systems (NOSs) distribute their functions over a number of networked computers. It adds functions that allow users to access shared resources concurrently. ...
... Network operating systems (NOSs) distribute their functions over a number of networked computers. It adds functions that allow users to access shared resources concurrently. ...
Lecture3-os-support
... • This way you get protection • And no need for hardware protection domains – everything can run in a single address space • Singularity: an OS from Microsoft implemented these concepts • ... End digression CMPT 401 © A. Fedorova ...
... • This way you get protection • And no need for hardware protection domains – everything can run in a single address space • Singularity: an OS from Microsoft implemented these concepts • ... End digression CMPT 401 © A. Fedorova ...
this module - NCIRL Course Builder
... Teaching & Learning will take place via a combination of methods including lectures, tutorials and practical work. Lectures will include in class discussion, problems solving exercises and feedback sessions. Practical sessions/tutorials will comprise of practical work and individual self-directed le ...
... Teaching & Learning will take place via a combination of methods including lectures, tutorials and practical work. Lectures will include in class discussion, problems solving exercises and feedback sessions. Practical sessions/tutorials will comprise of practical work and individual self-directed le ...
Exploration CCNA4 - Collin College Faculty Website Directory
... process within the organization. Users and system administrators who bypass the standard processes for account and access requests can lead to legal action against the organization. • Acquisition security assessment policy - Defines the responsibilities regarding corporate acquisitions and defines t ...
... process within the organization. Users and system administrators who bypass the standard processes for account and access requests can lead to legal action against the organization. • Acquisition security assessment policy - Defines the responsibilities regarding corporate acquisitions and defines t ...
ppt
... • Rate monotonic: equivalent to any static algorithm • Earliest deadline first: equiv. to any dynamic alg. ...
... • Rate monotonic: equivalent to any static algorithm • Earliest deadline first: equiv. to any dynamic alg. ...
Chapter 7 Operating Systems and Utility Programs
... Popular, free, multitasking UNIX-type operating system Open-source software — code is available to public Both a stand-alone and a network operating system e ...
... Popular, free, multitasking UNIX-type operating system Open-source software — code is available to public Both a stand-alone and a network operating system e ...
Introduction CS 239 Security for Networks and System
... • Includes mandatory access control – Using Bell-La Padula model – Each subject and object is assigned a security level • Requires both hierarchical and nonhierarchical access controls CS 236 Online ...
... • Includes mandatory access control – Using Bell-La Padula model – Each subject and object is assigned a security level • Requires both hierarchical and nonhierarchical access controls CS 236 Online ...
CS350-01-intro - dforeman.cs.bingh
... allow multiple users on 1 computer allow programs to interact with each other maximize memory and CPU utilization reduce the need for device handling allow programs' parts to be shared make the system more usable (friendlier?) make system faster ...
... allow multiple users on 1 computer allow programs to interact with each other maximize memory and CPU utilization reduce the need for device handling allow programs' parts to be shared make the system more usable (friendlier?) make system faster ...