Chapter 4 (b) - Jhasudan.com.np
... UNIX provides users with powerful tools and utilities. Some of these tools are simple commands that can be used to carry out specific tasks. Other tools and utilities are really small programmable languages that may be used to build scripts to ...
... UNIX provides users with powerful tools and utilities. Some of these tools are simple commands that can be used to carry out specific tasks. Other tools and utilities are really small programmable languages that may be used to build scripts to ...
CS3161 Operating System Principles
... higher-level language program (called run-time support routine) such as the ‘C’ language run-time system library. Example : A getchar function in ‘C’ program is complied by the language compiler into a call to a run-time support routine that issues the necessary read system calls, check for errors a ...
... higher-level language program (called run-time support routine) such as the ‘C’ language run-time system library. Example : A getchar function in ‘C’ program is complied by the language compiler into a call to a run-time support routine that issues the necessary read system calls, check for errors a ...
FreeBSD for the Linux user
... FTP install directories, floppy images, and ISO images for CDROMs with one command. • “make release” is used by many large companies to produce special versions of FreeBSD with special patches or additional software installed by default. • It is also the well documented way in which the release engi ...
... FTP install directories, floppy images, and ISO images for CDROMs with one command. • “make release” is used by many large companies to produce special versions of FreeBSD with special patches or additional software installed by default. • It is also the well documented way in which the release engi ...
System Management
... • The network manager allows a network admin to monitor the use of individual computers and shared hardware, and ensure software license agreement ...
... • The network manager allows a network admin to monitor the use of individual computers and shared hardware, and ensure software license agreement ...
No Slide Title - ECE Users Pages
... user of a computer and the computer hardware. • Operating system goals: – Execute user programs and make solving user problems easier. – Make the computer system convenient to use. • Use the computer hardware in an efficient manner. • Make it easy to write programs by handling common tasks like text ...
... user of a computer and the computer hardware. • Operating system goals: – Execute user programs and make solving user problems easier. – Make the computer system convenient to use. • Use the computer hardware in an efficient manner. • Make it easy to write programs by handling common tasks like text ...
CYREN WebSecurity for Enterprise
... Modern Cloud-based Web Security for the Latest Cyber Threats – With CYREN WebSecurity you have one cloud-based solution for every user, wherever they are and whatever devices they use. CYREN WebSecurity provides consistent real-time cyber intelligence on active online threats. Best-of-Breed Web Filt ...
... Modern Cloud-based Web Security for the Latest Cyber Threats – With CYREN WebSecurity you have one cloud-based solution for every user, wherever they are and whatever devices they use. CYREN WebSecurity provides consistent real-time cyber intelligence on active online threats. Best-of-Breed Web Filt ...
Chapter 21 - Linux Operating System
... once the system call has completed and control is about to be returned to user mode 2. The second technique applies to critical sections that occur in an interrupt service routines – By using the processor’s interrupt control hardware to disable interrupts during a critical section, the kernel guara ...
... once the system call has completed and control is about to be returned to user mode 2. The second technique applies to critical sections that occur in an interrupt service routines – By using the processor’s interrupt control hardware to disable interrupts during a critical section, the kernel guara ...
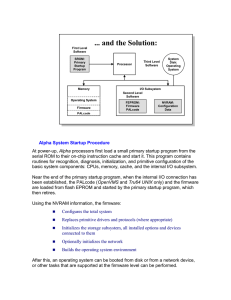
Alpha System Startup Procedure
... PALcode for OpenVMS and PALcode for Tru64 UNIX also reside on the flash EPROMs. The operating system specific PALcode is loaded and executed depending on the value of the os_type environment variable. Configuration data, called environment variables, are stored in nonvoltile RAM. Most of these varia ...
... PALcode for OpenVMS and PALcode for Tru64 UNIX also reside on the flash EPROMs. The operating system specific PALcode is loaded and executed depending on the value of the os_type environment variable. Configuration data, called environment variables, are stored in nonvoltile RAM. Most of these varia ...
Network Security (Daliah Stephan).
... – Viruses - Infect files; propagate by executing infected program - Payloads may be destructive – Illegal content: pornography, sexual or racial harassment – Spam (unsolicited commercial e-mail) ...
... – Viruses - Infect files; propagate by executing infected program - Payloads may be destructive – Illegal content: pornography, sexual or racial harassment – Spam (unsolicited commercial e-mail) ...
Lecture3-os-support
... • A middleware layer directly interacts with the OS • Example: a peer-to-peer file system implemented over a distributed hash table ...
... • A middleware layer directly interacts with the OS • Example: a peer-to-peer file system implemented over a distributed hash table ...
Introduction - London South Bank University
... are hidden from users • Users and applications can interact with a DS in a consistent and uniform way • Ds should also be easy to extend or scale • To support heterogeneous computers and networks while offering a single system view, DS is often organized in certain layers called middleware ...
... are hidden from users • Users and applications can interact with a DS in a consistent and uniform way • Ds should also be easy to extend or scale • To support heterogeneous computers and networks while offering a single system view, DS is often organized in certain layers called middleware ...
SG 17 is
... The establishment of a JCA aims mainly at improving coordination and planning. The work itself will continue to be conducted by the relevant study groups and the results are subject to the normal approval processes within each study group. A JCA may identify technical and strategic issues within t ...
... The establishment of a JCA aims mainly at improving coordination and planning. The work itself will continue to be conducted by the relevant study groups and the results are subject to the normal approval processes within each study group. A JCA may identify technical and strategic issues within t ...
Operating System Overview
... • Total control possible so OS must say “Mine, all mine” (Daffy Duck) ...
... • Total control possible so OS must say “Mine, all mine” (Daffy Duck) ...
Operating-System Structures
... them, search them, list file Information, permission management. ...
... them, search them, list file Information, permission management. ...
Oracle9i Security
... environments by defining the protocol for interaction between provisioning service components and agents representing provisioned services. ...
... environments by defining the protocol for interaction between provisioning service components and agents representing provisioned services. ...
The Difference Between Compliance and Cyber Security
... as Data Diodes. Some think the data diode is the silver bullet in cyber security. A data diode can enhance security in the appropriate environment; however, just adding a data diode to your network does not provide 100 percent protection for the network. A data diode cannot protect from an insider t ...
... as Data Diodes. Some think the data diode is the silver bullet in cyber security. A data diode can enhance security in the appropriate environment; however, just adding a data diode to your network does not provide 100 percent protection for the network. A data diode cannot protect from an insider t ...
Certified Penetration Testing Specialist
... vulnerability consultants. Mile2 trainers keep abreast of their expertise by practicing what they teach because we believe that an equal emphasis on theoretical and real world experience is essential for effective knowledge transfer to you, the student. The CPTS presents information on the latest vu ...
... vulnerability consultants. Mile2 trainers keep abreast of their expertise by practicing what they teach because we believe that an equal emphasis on theoretical and real world experience is essential for effective knowledge transfer to you, the student. The CPTS presents information on the latest vu ...
Windows - Part I
... How windows executes code The Windows operating system uses two modes to maintain operating system efficiency and integrity: user mode and kernel mode. The architecture of 80386 and higher processors defines four privilege levels, called rings, to protect system code and data from being overwritte ...
... How windows executes code The Windows operating system uses two modes to maintain operating system efficiency and integrity: user mode and kernel mode. The architecture of 80386 and higher processors defines four privilege levels, called rings, to protect system code and data from being overwritte ...
Chapter 1: Field Guide to Identifying Computers in the Wild
... • Operating System Functions • Capabilities and Limitations of an OS • Common OS Problems and Their ...
... • Operating System Functions • Capabilities and Limitations of an OS • Common OS Problems and Their ...
What is an Operating System? ¯ Three views of an operating system
... System View: The OS manages the hardware resources of a computer system. ¯ The execution environment provided by the OS includes a variety of abstract ¯ Resources include processors, memory, disks and other storage devices, entities that can be manipulated by a running program. Examples: ...
... System View: The OS manages the hardware resources of a computer system. ¯ The execution environment provided by the OS includes a variety of abstract ¯ Resources include processors, memory, disks and other storage devices, entities that can be manipulated by a running program. Examples: ...
Isolating Operating System Components with Intel SGX
... all software level attacks as well as physical attacks. In addition to the user password, we use a second authentication factor for deriving the encryption key which is stored sealed and bound to the platform. Thus, stealing the hard drive and sniffing the user password is insufficient for an attack ...
... all software level attacks as well as physical attacks. In addition to the user password, we use a second authentication factor for deriving the encryption key which is stored sealed and bound to the platform. Thus, stealing the hard drive and sniffing the user password is insufficient for an attack ...
CH09-CompSec2e - MCST-CS
... Bastion Hosts system identified as a critical strong point in the network’s ...
... Bastion Hosts system identified as a critical strong point in the network’s ...
Chapter 5 - Operating System Installation
... • Desktop Installations – Networked Client Systems • Systems that rely on network-based servers for critical applications/services are typically referred to as networked client systems, or “thin clients.” – These machines usually contain a copy of the OS, but very little other software gets installe ...
... • Desktop Installations – Networked Client Systems • Systems that rely on network-based servers for critical applications/services are typically referred to as networked client systems, or “thin clients.” – These machines usually contain a copy of the OS, but very little other software gets installe ...
ppt
... Naming and Protections domains are at language level. Not at virtual memory system level Name space management occurs at language level Protection domains: set of names or program symbols, that can be referenced by code with access to that domain Domains can be intersecting or disjoint enabling appl ...
... Naming and Protections domains are at language level. Not at virtual memory system level Name space management occurs at language level Protection domains: set of names or program symbols, that can be referenced by code with access to that domain Domains can be intersecting or disjoint enabling appl ...