* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download SG 17 is
Cyberwarfare wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Unix security wikipedia , lookup
Distributed firewall wikipedia , lookup
Wireless security wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Mobile security wikipedia , lookup
Airport security wikipedia , lookup
Security printing wikipedia , lookup
Information security wikipedia , lookup
International cybercrime wikipedia , lookup
Computer security wikipedia , lookup
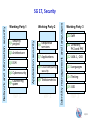
ITU-T Study Group 17 Security An overview for newcomers Arkadiy Kremer August 2012 Contents Importance of telecommunication/ICT security standardization ITU Plenipotentiary Conference (PP-10) actions on ICT security World Telecommunications Standardization Assembly (WTSA-08) mandate for Study Group 17 Study Group 17 overview Security Coordination Future meetings Useful references 2/51 Importance of telecommunication/ICT security standardization (1/4) National laws are oftentimes inadequate to protect against attacks. They are insufficient from the timing perspective (i.e. laws cannot keep up with the pace of technological change), and, since attacks are often transnational, national laws may well be inapplicable anyway. What this means is that the defenses must be largely technical, procedural and administrative; i.e. those that can be addressed in standards. The development of standards in an open forum that comprises international specialists from a wide variety of environments and backgrounds provides the best possible opportunity to ensure relevant, complete and effective standards. SG 17 provides the environment in which such standards can be, and are being, developed. 3/51 Importance of telecommunication/ICT security standardization (2/4) The primary challenges are the time it takes to develop a standard (compared to the speed of technological change and the emergence of new threats) and the shortage of skilled and available resources. We must work quickly to respond to the rapidly-evolving technical and threat environment but we must also ensure that the standards we produce are given sufficient consideration and review to ensure that they are complete and effective. We must recognize and respect the differences in developing countries respective environments: their telecom infrastructures may be at different levels of development from those of the developed countries; their ability to participate in, and contribute directly to the security standards work may be limited by economic and other considerations; and their needs and priorities may be quite different. 4/51 Importance of telecommunication/ICT security standardization (3/4) ITU-T can help the developing countries by fostering awareness of the work we are doing (and why we are doing it), by encouraging participation in the work particularly via the electronic communication facilities now being used (e.g. web based meetings and teleconferencing), and, most particularly, by encouraging the members from the developing countries to articulate their concerns and priorities regarding the telecommunication/ICT security. The members from the developed nations should not confuse their own needs with those of the developing countries, nor should they make assumptions about what the needs and priorities of the developing countries may be. 5/51 Importance of telecommunication/ICT security standardization (4/4) For on-going credibility, we need performance measures that provide some indication of the effectiveness of our standards. In the past there has been too much focus on quantity (i.e. how many standards are produced) than on the quality and effectiveness of the work. Going forward, we really need to know which standards are being used (and which are not being used), how widely they are used, and how effective they are. This is not going to be easy to determine but it would do much more to the ITU-T’s credibility if it could demonstrate the value and effectiveness of standards that have been developed rather than simply saying “we produced X number of standards”. The number of standards produced is irrelevant: what counts is the impact they have. 6/51 Importance of telecommunication/ICT security standardization ITU Plenipotentiary Conference (PP-10) actions on ICT security World Telecommunications Standardization Assembly (WTSA-08) mandate for Study Group 17 Study Group 17 overview Security Coordination Future meetings Useful references 7/51 ITU Plenipotentiary Conference 2010 Strengthened the role of ITU in telecommunication/ICT security: Strengthening the role of ITU in building confidence and security in the use of information and communication technologies (Res. 130) The use of telecommunications/information and communication technologies for monitoring and management in emergency and disaster situations for early warning, prevention, mitigation and relief (Res. 136). ITU's role with regard to international public policy issues relating to the risk of illicit use of information and communication technologies (Res. 174) ITU role in organizing the work on technical aspects of telecommunication networks to support the Internet (Res. 178) ITU's role in child online protection (Res. 179) Definitions and terminology relating to building confidence and security in the use of information and communication technologies (Res. 181) 8/51 Importance of telecommunication/ICT security standardization ITU Plenipotentiary Conference (PP-10) actions on telecommunication/ICT security World Telecommunications Standardization Assembly (WTSA-08) mandate for Study Group 17 Study Group 17 overview Security Coordination Future meetings Useful references 9/51 SG 17 mandate established by World Telecommunication Standardization Assembly (WTSA-08) WTSA-08 decided the following for Study Group 17: Title: Security Responsible for: studies relating to security including cybersecurity, countering spam and identity management. Also responsible for the application of open system communications including directory and object identifiers, and for technical languages, the method for their usage and other issues related to the software aspects of telecommunication systems. Lead Study Group for: – Telecommunication security – Identity management – Languages and description techniques Responsible for specific E, F, X and Z series Recommendations Responsible for 15 Questions Chairman: Arkadiy Kremer Vice chairmen: Jianyong Chen, Mohamed M.K. Elhaj, Antonio Guimaraes, Patrick Mwesigwa, Koji Nakao, Heung Youl Youm 10/51 Importance of telecommunication/ICT security standardization ITU Plenipotentiary Conference (PP-10) actions on telecommunication/ICT security World Telecommunications Standardization Assembly (WTSA-08) mandate for Study Group 17 Study Group 17 overview Security Coordination Future meetings Useful references 11/51 Study Group 17 Overview Primary focus is to build confidence and security in the use of Information and Communication Technologies (ICTs) Meets twice a year. Last meeting had 178 participants from 28 Member States, 18 Sector Members and 5 Associates. As of 1 June 2012, SG 17 is responsible for 290 approved Recommendations, 12 approved Supplements and 3 approved Implementer’s Guides in the E, F, X and Z series. Large program of work: • 8 new work items added to work program in 2012 • 17 Recommendations, 14 Corrigenda , 1 Supplement and 1 Appendix approved or entered approval process in 2012 • 127 new or revised Recommendations and other texts are under development for approval September 2012 or later Work organized into 3 Working Parties with 15 Questions 8 Correspondence groups See SG 17 web page for more information http://itu.int/ITU-T/studygroups/com17 12/51 Security Q1 project Q2 Architecture Q3 ISM Q4 Cybersecurity Countering Q5 spam WP 1 Working Party 2 Ubiquitous Q6 services Q7 Applications Q8 Cloud computing security Q9 Telebiometrics WP 2 Identity management and languages Working Party 1 Application security Network and information security SG 17, Security Working Party 3 Q10 IdM Q11 Directory, PKI and PMI Q12 ASN.1, OID Q13 Languages Q14 Testing Q15 OSI WP 3 13/51 Study Group 17 is the Lead Study Group on: ● Telecommunication security ● Identity management (IdM) ● Languages and description techniques A study group may be designated by WTSA or TSAG as the lead study group for ITU-T studies forming a defined programme of work involving a number of study groups. This lead study group is responsible for the study of the appropriate core Questions. In addition, in consultation with the relevant study groups and in collaboration, where appropriate, with other standards bodies, the lead study group has the responsibility to define and maintain the overall framework and to coordinate, assign (recognizing the mandates of the study groups) and prioritize the studies to be carried out by the study groups, and to ensure the preparation of consistent, complete and timely Recommendations. * Extracted from WTSA-08 Resolution 1 14/51 SG 17 is “Parent” for Joint Coordination Activities (JCAs) on: ● Identity management ● Child online protection ● Conformance & interoperability testing A joint coordination activity (JCA) is a tool for management of the work programme of ITU-T when there is a need to address a broad subject covering the area of competence of more than one study group. A JCA may help to coordinate the planned work effort in terms of subject matter, time-frames for meetings, collocated meetings where necessary and publication goals including, where appropriate, release planning of the resulting Recommendations. The establishment of a JCA aims mainly at improving coordination and planning. The work itself will continue to be conducted by the relevant study groups and the results are subject to the normal approval processes within each study group. A JCA may identify technical and strategic issues within the scope of its coordination role, but will not perform technical studies nor write Recommendations. A JCA may also address coordination of activities with recognized standards development organizations (SDOs) and forums, including periodic discussion of work plans and schedules of deliverables. The study groups take JCA suggestions into consideration as they carry out their work. * Extracted from Recommendation ITU-T A.1 15/51 Working Party 1/17 Network and information security Chairman: Koji Nakao Q1/17 Telecommunications systems security project Q2/17 Security architecture and framework Q3/17 Telecommunications information security management Q4/17 Cybersecurity Q5/17 Countering spam by technical means 16/51 Question 1/17 Telecommunications systems security project Security Coordination • Coordinate security matters within SG 17, with ITU-T SGs, ITU-D and externally with other SDOs • Maintain reference information on LSG security webpage ICT Security Standards Roadmap • Searchable database of approved ICT security standards from ITU-T, ISO/IEC, ETSI and others Security Compendium • Catalogue of approved security-related Recommendations and security definitions extracted from approved Recommendations ITU-T Security Manual • 4th edition published in 4Q/2009; 5th edition to be published 2012 Bridging the standardization gap 17/51 Question 1/17 (cnt’d) Telecommunications systems security project Security standardization strategy – Define a top-down approach to complement the contribution-driven work • to ensure the continued relevance of security standards by keeping them current with rapidly-developing technologies and operators’ trends (in e-commerce, e-payments, e-banking, telemedicine, fraud-monitoring, fraud-management, fraud identification, digital identity, infrastructure creation, billing systems, IPTV, Video-on-demand, grid network computing, ubiquitous networks, etc.) • to follow-up on considerable attention recently given to trust between network providers and communication infrastructure vendors, in particular for communication hardware and software security, issues of how trust can be established and/or enhanced would need to be considered Rapporteur: Antonio Guimaraes 18/51 Question 2/17 Security Architecture and Framework Responsible for general security architecture and framework for telecommunication systems 2 Recommendations and 2 Supplements approved in this study period Recommendations currently under study include: • X.1037, Architectural systems for security controls for preventing fraudulent activities in public carrier networks • X.gsiiso, Guidelines on security of the individual information service for operators • X.hns, Heterarchic for secure distributed services networks • X.ipv6-secguide, Technical guideline on deploying IPv6 • X.ncns-1, National IP-based Public Networks Security Center for Developing Countries • X.vissec, Security of digital broadcasting and multimedia video information systems (VIS Security) Relationships with ISO/IEC JTC 1 SCs 27 and 37, IEC TC 25, ISO TC 12, IETF, ATIS, ETSI, 3GPP, 3GPP2 Rapporteur: Patrick Mwesigwa 19/51 Question 3/17 Telecommunications information security management Responsible for information security management - X.1051, etc. 4 Recommendations approved in this study period Recommendations in TAP approval process For approval • X.1054 (X.isgf), Information technology - Security techniques - Governance of information security (w/SC 27) Developing specific guidelines including: For approval • X.gpim, Guideline for management of personally identifiable information for telecommunication org. • X.mgv6, Security management guideline for implementation of IPv6 environment • X.sgsm, Security management guidelines for small and medium-sized telecommunication organizations • Supplement - Information security management users’ guide for Recommendation ITU-T X.1051 • Handbook: Handbook on information security incident management for developing countries Close collaboration with ISO/IEC JTC 1/SC 27 Rapporteur: Miho Naganuma 20/51 Question 4/17 Cybersecurity Cybersecurity by design no longer possible; a new paradigm: • know your weaknesses minimize the vulnerabilities • know your attacks share the heuristics within trust communities Current work program (27 Recommendations under development) X.1500 suite: Cybersecurity Information Exchange (CYBEX) – nonprescriptive, extensible, complementary techniques for the new paradigm • • • • • • Weakness, vulnerability and state Event, incident, and heuristics Information exchange policy Identification, discovery, and query Identity assurance Exchange protocols Non-CYBEX deliverables include compendiums and guidelines for • • • • • SIP server protection Abnormal traffic detection Botnet mitigation Attack source attribution (including traceback) Trusted standards availability • Extensive relationships with many external bodies 21/51 Question 4/17 (cnt’d) Cybersecurity 8 Recommendations and 3 Supplements approved in this study period Recommendations in TAP approval process For approval For approval For approval For approval For approval For approval For approval For approval For approval • • • • • • • • • X.1527 (X.xccdf), Extensible configuration checklist description format X.1528 (X.cpe), Common platform enumeration X.1528.1 (X.cpe.1), Common platform enumeration naming X.1528.2 (X.cpe.2), Common platform enumeration name matching X.1528.3 (X.cpe.3), Common platform enumeration dictionary X.1528.4 (X.cpe.4), Common platform enumeration applicability language X.1541, Incident object description exchange format X.1580 (X.rid), Real-time inter-network defense X.1581 (X.ridt), Transport of real-time inter-network defense messages 22/51 Question 4/17 (cnt’d) Cybersecurity Recommendations currently under study include: For determ. For determ. For determ. For determ. For determ. For determ. • • • • • • • • • • • • • • • • • • X.1303rev, Common alerting protocol (CAP 1.2) X.abnot, Abnormal traffic detection and control guideline for telecommunication network X.bots, Centralized framework for botnet detection and response X.capec, Common attack pattern enumeration and classification X.cce, Common configuration enumeration X.cee, Common event expression X.csi, Guidelines for cybersecurity index X.csmc, Continuous security monitoring using CYBEX techniques X.cvrf, Common vulnerability reporting format X.cwss, Common weakness scoring system X.cybex-beep, A BEEP profile for cybersecurity information exchange techniques X.cybex-tp, Transport protocols supporting cybersecurity information exchange X.eipwa, Guideline on techniques for preventing web-based attacks X.maec, Malware attribute enumeration and classification X.oval, Open vulnerability and assessment language X.sip-cyber, Security guidelines for countering cyber attacks in SIP-based services X.sisnego, Framework of security information sharing negotiation X.trm, Overview of traceback mechanisms Rapporteur: Anthony Rutkowski 23/51 Question 5/17 Countering spam by technical means Lead group in ITU-T on countering spam by technical means in support of WTSA-08 Resolution 52 (Countering and combating spam) 3 Recommendations and 7 Supplements approved in this study period 2 draft texts under development (see structure in next slide): For approval • X.ticvs, Technologies involved in countering voice spam in telecommunication organizations • Supplement to X.1243 (X.ics), Functions and interfaces for countering email spam using botnet information Effective cooperation with ITU-D, IETF, ISO/IEC JTC 1, 3GPP, OECD, MAAWG , ENISA and other organizations Rapporteur: Hongwei Luo 24/51 Question 5/17 (cnt’d) Countering spam by technical means Technical strategies on countering spam (X.1231) Technologies involved in countering email spam (X.1240) Overall aspects of countering spam in IP-based multimedia applications (X.1244) Overall aspects of countering mobile messaging spam (Supplement 12 to Recommendation ITU-T X.1240) Technical framework for countering email spam (X.1241) Framework for countering IP multimedia spam (X.1245) Short message service (SMS) spam filtering system based on user-specified rules (X.1242) Framework based on real-time blocking list (RBL) for countering VoIP spam (Supplement 11 to Recommendation ITU-T X.1245) Interactive gateway system for countering spam (X.1243) A practical reference model for countering email spam using botnet information (Supplement x to ITU-T X.1243, X.ics) Technologies involved in countering voice spam in telecommunication organizations (X.ticvs) Supplement on countering spam and associated threats (Supplement 6 to Recommendation ITU-T X.1240) 25/51 Working Party 2/17 Application Security Chairman: Heung Youl Youm Q6/17 Security aspects of ubiquitous telecommunication services Q7/17 Secure application services Q8/17 Cloud computing security Q9/17 Telebiometrics 26/51 Question 6/17 Security aspects of ubiquitous telecommunication services Responsible for multicast security, home network security, mobile security, Networked ID security, IPTV security, and ubiquitous sensor network security 11 Recommendations approved in this study period. Recommendations currently under study include: For consent For consent For consent For consent X.iptvsec-6, Framework for the downloadable service and content protection system in the mobile IPTV environment X.iptvsec-8, Virtual machine-based security platform for renewable IPTV service and content protection (SCP) X.msec-6, Security aspects of smartphones X.msec-7, Guidelines on the management of infected terminals in mobile networks X.msec-8, Secure application distribution framework for communication devices X.sgsec-1, Security functional architecture for smart grid services using telecommunication network X.unsec-1, Security requirements and framework of ubiquitous networking X.usnsec-3, Security requirements for wireless sensor network routing Close relationship with JCA-IPTV and ISO/IEC JTC 1/SC 6/WG 7 Rapporteur: Jonghyun Baek 27/51 Question 7/17 Secure application services Responsible for Web security, security protocols, peer-to-peer security 1 Recommendation approved in this study period Recommendations currently under study include: X.1141 Amd.1, Security Assertion Markup Language (SAML) 2.0 – Amendment 1: Errata For consent X.1142 Amd.1, eXtensible Access Control Markup Language (XACML 2.0) – Amendment 1: Errata X.p2p-3, Security requirements and mechanisms of peer-to-peer based telecommunication network X.p2p-4, Use of service providers' user authentication infrastructure to implement PKI for peerFor consent to-peer networks For consent X.sap-4, The general framework of combined authentication on multiple identity service provider environment X.sap-5, Guideline on anonymous authentication for e-commerce service X.sap-6, Non-repudiation framework based on a one time password X.sap-7, The requirements of fraud detection and response service for sensitive Information Communication Technology applications For consent X.websec-4, Threats and security requirements for enhanced web based telecommunication service X.websec-5, Security architecture and operations for web mashup services For consent X.xacml3, eXtensible Access Control Markup Language (XACML) 3.0 For consent Relationships include: OASIS, OMA, W3C, ISO/IEC JTC 1/SC 27, Kantara Initiative Rapporteur: Jae Hoon Nah 28/51 Question 8/17 Cloud computing security • Recommendations currently under study include: – Security aspects of cloud computing For determ. - X.ccsec, Security requirements and architecture for cloud computing - X.goscc, Guideline of operational security for cloud computing – Security aspects of service oriented architecture - X.fsspvn, Framework of the secure service platform for virtual network - X.sfcsc, Security functional requirements for Software as a Service (SaaS) application environment Working closely with ITU-T SG 13, JCA-Cloud, ISO/IEC JTC 1/SCs 27 and 38, and Cloud Security Alliance on cloud computing Rapporteur: Liang Wei 29/51 Question 9/17 Telebiometrics Current focus: • Security requirements and guidelines for applications of telebiometrics • Requirements for evaluating security, conformance and interoperability with privacy protection techniques for applications of telebiometrics • Requirements for telebiometric applications in a high functionality network • Requirements for telebiometric multi-factor authentication techniques based on biometric data protection and biometric encryption • Requirements for appropriate generic protocols providing safety, security, privacy protection, and consent “for manipulating biometric data” in applications of telebiometrics, e.g., e-health, telemedicine 11 Recommendations approved in this study period. 30/51 Question 9/17 (cnt’d) Telebiometrics Recommendations under development: • X.bhsm, Telebiometric authentication framework using biometric hardware • X.tam, Guideline to technical and operational countermeasurers for telebiometric applications using mobile devices • X.tif, Integrated framework for telebiometric data protection • X.th-series, e-Health and world-wide telemedicines For determ. For determ. • • • • • X.th2, Telebiometrics related to physics X.th3, Telebiometrics related to chemistry X.th4, Telebiometrics related to biology X.th5, Telebiometrics related to culturology X.th6, Telebiometrics related to psychology Close working relationship with ISO/IEC JTC 1/SCs 17, 27 and 37, ISO TCs 12, 68 and 215, IEC TC 25, IETF, IEEE Rapporteur: Hale Kim 31/51 Working Party 3/17 Identity management and languages Chairman: Jianyong Chen Q10/17 Identity management architecture and mechanisms Q11/17 Directory services, Directory systems, and public-key/attribute certificates Q12/17 ASN.1, Object Identifiers (OIDs) and associated registration Q13/17 Formal languages and telecommunication software Q14/17 Testing languages, methodologies and framework Q15/17 Open Systems Interconnection (OSI) 32/51 Question 10/17 Identity Management (IdM) Identity Management (IdM) • • • • • Key focus • • • • IdM is a security enabler by providing trust in the identity of both parties to an e-transaction IdM also provides network operators an opportunity to increase revenues by offering advanced identity-based services The focus of ITU-T’s IdM work is on global trust and interoperability of diverse IdM capabilities in telecommunication. Work is focused on leveraging and bridging existing solutions This Question is dedicated to the vision setting and the coordination and organization of the entire range of IdM activities within ITU-T Adoption of interoperable federated identity frameworks that use a variety of authentication methods with well understood security and privacy Encourage the use of authentication methods resistant to known and projected threats Provide a general trust model for making trust-based authentication decisions between two or more parties Ensure security of online transactions with focus on end-to-end identification and authentication of the participants and components involved in conducting the transaction, including people, devices, and services 7 Recommendations and 1 Supplement approved in this study period. 33/51 Question 10/17 (cnt’d) Identity Management (IdM) Recommendations in TAP approval process For approval X.1254 (X.eaa), Information technology — Security techniques — Entity authentication assurance framework (w/SC 27) Recommendations under development: For determ. For determ. For determ. X.atag, Attribute aggregation framework X.authi, Guideline to implement the authentication integration of the network layer and the service layer. X.discovery, Discovery of identity management information X.giim, Mechanisms to support interoperability across different IdM services X.idmcc, Requirement of IdM in cloud computing X.mob-id, Baseline capabilities and mechanisms of identity management for mobile applications and environment X.oitf, Open identity trust framework Engagement • JCA-IdM • Related standardization bodies: ISO/IEC JTC 1 SCs 6, 27 and 37; IETF; ATIS; ETSI/TISPAN; OASIS; Kantara Initiative; OMA; NIST; 3GPP; 3GPP2; Eclipse; OpenID Foundation; OIX etc. Rapporteur: Abbie Barbir 34/51 Question 11/17 Directory services, Directory systems, and Public-key/attribute certificates Three Directory Projects: • ITU-T X.500 Series of Recommendations | ISO/IEC 9594 - all parts – The Directory • ITU-T E.115 - Computerized directory assistance • ITU-T F.5xx - Directory Service - Support of tag-based identification services X.500 series is a specification for a highly secure, versatile and distributed directory The X.500 series is under continuous enhancement • • • • Password policy Support of RFID Interworking with LDAP Support for Identity Management X.500 work is collaborative with ISO/IEC JTC 1/SC 6/WG 8 35/51 Question 11/17 (cnt’d) Directory services, Directory systems, and Public-key/attribute certificates ITU-T X.509 on public-key/attribute certificates is the cornerstone for security: • Base specification for public-key certificates and for attribute certificates • Has a versatile extension feature allowing additions of new fields to certificates • Basic architecture for revocation • Base specification for Public-Key Infrastructure (PKI) • Base specifications for Privilege Management Infrastructure (PMI) ITU-T X.509 is used in many different areas: • Basis for eGovernment, eBusiness, etc. all over the world • Used for IPsec, cloud computing, and many other areas • Is the base specification for many other groups (PKIX in IETF, ESI in ETSI, CA Browser Forum, etc.) Rapporteur: Erik Andersen 36/51 Question 11/17 (cnt’d) Directory services, Directory systems, and Public-key/attribute certificates 11 Recommendations and many Corrigenda approved in this study period. Recommendations under development: For consent For consent • • For consent • • For consent • For consent • For consent • For consent • For consent • For consent • For consent F.5xx, Directory Service - Support of Tag-based Identification Services X.500rev, Information technology – Open Systems Interconnection –The Directory: Overview of concepts, models and services X.501rev, Information technology – Open Systems Interconnection –The Directory – Models X.509rev, Information technology – Open Systems Interconnection –The Directory – Publickey and attribute certificate frameworks X.511rev, Information technology – Open Systems Interconnection –The Directory – Abstract Service Definition X.518rev, Information technology – Open Systems Interconnection –The Directory – Procedures for Distributed Operations X.519rev, Information technology – Open Systems Interconnection –The Directory – Protocols X.520rev, Information technology – Open Systems Interconnection –The Directory – Selected Attribute Types X.521rev, Information technology – Open Systems Interconnection –The Directory – Selected object classes X.525rev, Information technology – Open Systems Interconnection –The Directory – Replication 37/51 Question 12/17 Abstract Syntax Notation One (ASN.1), Object Identifiers (OIDs) and associated registration Developing and maintaining the heavily used Abstract Syntax Notation One (ASN.1) and Object Identifier (OID) specifications Recommendations are in the X.680 (ASN.1), X.690 ( ASN.1 Encoding Rules), X.660/X.670 (OID Registration), and X.890 (Generic Applications, such as Fast Infoset, Fast Web services, etc) series 13 Recommendations and several Corrigenda approved in this study period Recommendations under development: For consent X.667 Cor.1, Information technology – Procedures for the operation of Object Identifier Registration Authorities: Generation of Universally Unique Identifiers (UUIDS) and their use in object identifiers – Technical Corrigendum 1 Giving advice on the management of OID Registration Authorities, particularly within developing countries, through the ASN.1 and OID Project Leader Olivier Dubuisson Approving new top arcs of the Object Identifier tree as necessary Promoting use of OID resolution system by other groups such as SG 16 Repository of OID allocations and a database of ASN.1 modules Promoting the term “description and encoding of structured data” as what ASN.1 is actually about ASN.1 Packed Encoding Rules reduces the bandwidth required for communication thus conserving energy (e.g., compared with XML) Work is collaborative with ISO/IEC JTC 1/SC 6/WG 9 Former Rapporteur: John Larmouth 38/51 Question 13/17 Formal languages and telecommunication software Languages and methods for requirements, specification implementation, and Open Distributed Processing (ODP) Recommendations for: ODP (X.900 series in collaboration with JTC 1/SC 7/WG 19) Specification and Description Language (Z.100 series) Message Sequence Chart (Z.120 series) User Requirements Notation (Z.150 series) Framework and profiles for Unified Modeling Language, as well as use of languages (Z.110, Z.111, Z.400, Z.450). These techniques enable high quality Recommendations to be written from which formal tests can be derived, and products to be cost effectively developed. Relationship with SDL Forum Society Rapporteur: Rick Reed 39/51 Question 13/17 Formal languages and telecommunication software 17 Recommendations, 1 Implementers Guide approved in this study period. Recommendations under development: For consent For consent For consent For approval X.906rev, Open distributed processing – Use of UML for ODP system specification X.911rev, Open distributed processing – Reference model – Enterprise language Z.104 Amd.1, Data and action language in SDL-2010: Amendment 1 Annex C – Language Binding Z.151rev, User requirements notation (URN) – Language definition Z.uml-urn-grl, Unified modeling language (UML) profile for URN GRL Z.Sup1, Supplement 1 to Z-series Recommendations – ITU-T Z.100series – Supplement on methodology on the use of description techniques 40/51 Question 14/17 Testing languages, methodologies and framework Interoperability and conformance testing languages, methodologies and framework Responsible for Testing and Test Control Notation version 3 (TTCN-3) Recommendations: Z.161, Z.161.1, Z.162, Z.163, Z.164, Z.165, Z.165.1, Z.166, Z.167, Z.168, Z.169, Z.170 Also responsible for conformance testing methodology and framework for protocol Recommendations: X.290, X.291, X.292, X.293, X.294, X.295, X.296, X.Sup4 and X.Sup5 Provides support for WTSA-08 Resolution 78 on conformance and interoperability testing 12 Recommendations approved in this study period. Close liaisons with ETSI, SG 11, JCA-CIT Rapporteur: Dieter Hogrefe 41/51 Question 15/17 Open Systems Interconnection (OSI) Ongoing maintenance of the OSI X-series Recommendations and the OSI Implementer’s Guide: • • • • • • • • • OSI Architecture Message Handling Transaction Processing Commitment, Concurrency and Recovery (CCR) Remote Operations Reliable Transfer Quality of Service Upper layers – Application, Presentation, and Session Lower Layers – Transport, Network, Data Link, and Physical 109 approved Recommendations (from former study periods) Work is carried out in collaboration with ISO/IEC JTC 1 42/51 Importance of telecommunication/ICT security standardization ITU Plenipotentiary Conference (PP-10) actions on telecommunication/ICT security World Telecommunications Standardization Assembly (WTSA-08) mandate for Study Group 17 Study Group 17 overview Security Coordination Future meetings Useful references 43/51 Security Coordination Security activities in other ITU-T Study Groups ITU-T SG 2 Operation aspects & TMN – Q3 International Emergency Preference Scheme , ETS/TDR – Q5 Network and service operations and maintenance procedures , E.408 – Q11 TMN security, TMN PKI ITU-T SG 9 Integrated broadband cable and TV – Q3 Conditional access, copy protection, HDLC privacy, – Q7, Q8 DOCSIS privacy/security – Q9 IPCablecom 2 (IMS w. security), MediaHomeNet security gateway, DRM, ITU-T SG 11 Signaling Protocols – Q7 EAP-AKA for NGN ITU-T SG 13 Future network – Q16 Security and identity management for NGN – Q17 Deep packet inspection – Q26, Q27, Q28 Cloud computing ITU-T SG 15 Optical Transport & Access – Q9 Reliability, availability, Ethernet/MPLS protection switching ITU-T SG 16 Multimedia – Secure VoIP and multimedia security (H.233, H.234, H.235, H.323, JPEG2000) 44/51 Coordination with other bodies • SAG-S Study Group 17 • ETSI security workshops • ITU security workshops ITU-D, ITU-R, xyz… 45/51 SG 17 collaborative work with ISO/IEC JTC 1 Existing relationships having collaborative (joint) projects: JTC 1 SG 17 Question Subject SC 6/WG 7 Q6/17 Ubiquitous networking SC 6/WG 8 Q11/17 Directory SC 6/WG 9 Q12/17 ASN.1, OIDs, and Registration Authorities SC 7/WG 19 Q13/17 Open Distributed Processing (ODP) SC 27/WG 1 Q3/17 Information Security Management System (ISMS) SC 27/WG 3 Q2/17 Security architecture SC 27/WG 5 Q10/17 Identity Management (IdM) SC 37 Q9/17 Telebiometrics Note – In addition to collaborative work, extensive communications and liaison relationships exist with the following JTC 1 SCs: 6, 7, 17, 22, 27, 31, 37 and 38 on a wide range of topics. All SG 17 Questions are involved. 46/51 SG 17 collaborative work with ISO/IEC JTC 1 (cnt’d) Guide for ITU-T and ISO/IEC JTC 1 Cooperation • http://itu.int/rec/T-REC-A.23-201002-I!AnnA Listing of common text and technically aligned Recommendations | International Standards • http://itu.int/oth/T0A0D000011 Mapping between ISO/IEC International Standards and ITU-T Recommendations • http://itu.int/oth/T0A0D000012 Relationships of SG 17 Questions with JTC 1 SCs that categorizes the nature of relationships as: – joint work (e.g., common texts or twin texts) – technical collaboration by liaison mechanism – informational liaison • http://itu.int/en/ITU-T/studygroups/com17/Pages/relationships.aspx 47/51 Importance of telecommunication/ICT security standardization ITU Plenipotentiary Conference (PP-10) actions on telecommunication/ICT security World Telecommunications Standardization Assembly (WTSA-08) mandate for Study Group 17 Study Group 17 overview Security Coordination Future meetings Useful references 48/51 Study Group 17 Meetings This meeting (final meeting in 2008-2012 study period ): Wednesday, 29 August – Friday, 7 September 2012 (10 days), Geneva, Switzerland Next study period (2013-2016) starts following WTSA-12; for 2013 and 2014, Study Group 17 meetings have been scheduled for: 17 – 26 April 2013 (8 days), Geneva, Switzerland 15 – 24 January 2014 (8 days), Geneva, Switzerland 17 – 26 September 2014 (8 days), Geneva, Switzerland 49/51 Importance of telecommunication/ICT security standardization ITU Plenipotentiary Conference (PP-10) actions on telecommunication/ICT security World Telecommunications Standardization Assembly (WTSA-08) mandate for Study Group 17 Study Group 17 overview Security Coordination Future meetings Useful references 50/51 Reference links Webpage for ITU-T Study Group 17 • http://itu.int/ITU-T/studygroups/com17 Webpage on ICT security standard roadmap • http://itu.int/ITU-T/studygroups/com17/ict Webpage on ICT cybersecurity organizations • http://itu.int/ITU-T/studygroups/com17/nfvo Webpage for JCA on Identity management • http://www.itu.int/en/ITU-T/jca/idm/Pages/default.aspx Webpage for JCA on Conformance and interoperability testing • http://itu.int/en/ITU-T/jca/idm Webpage on lead study group on telecommunication security • http://itu.int/en/ITU-T/studygroups/com17/Pages/telesecurity.aspx Webpage on lead study group on identity management • http://itu.int/en/ITU-T/studygroups/com17/Pages/idm.aspx Webpage on lead study group on languages and description techniques • http://itu.int/en/ITU-T/studygroups/com17/Pages/ldt.aspx Webpage for security workshop on Addressing security challenges on a global scale 51/51 • http://itu.int/ITU-T/worksem/security/201012