Distributed Operating Systems
... middleware layer at top of NOS implementing general-purpose services to provide distribution transparency ...
... middleware layer at top of NOS implementing general-purpose services to provide distribution transparency ...
Introduction to Operating Systems - Computer Science
... ◦ system software, which operates the computer hardware. ◦ A virtual machine shell, which provided a logical representation of the underlying physical computer hardware. ◦ An intermediary between a user of a computer and the computer hardware. ◦ A set of system and application and utility software t ...
... ◦ system software, which operates the computer hardware. ◦ A virtual machine shell, which provided a logical representation of the underlying physical computer hardware. ◦ An intermediary between a user of a computer and the computer hardware. ◦ A set of system and application and utility software t ...
Operating Systems
... Compaction refers to the mechanism of shuffling the memory portions such that all the free portions of the memory can be aligned (or merged) together in a single large block. OS to overcome the problem of fragmentation, either internal or external, performs this mechanism, frequently. Compaction is ...
... Compaction refers to the mechanism of shuffling the memory portions such that all the free portions of the memory can be aligned (or merged) together in a single large block. OS to overcome the problem of fragmentation, either internal or external, performs this mechanism, frequently. Compaction is ...
Threads and Virtualization - The University of Alabama in
... • Example 1: (Send Client code to Server) – Server manages a huge database. If a client application needs to perform many database operations, it may be better to ship part of the client application to the server and send only the results across the network. • Example 2: (Send Server code to Client) ...
... • Example 1: (Send Client code to Server) – Server manages a huge database. If a client application needs to perform many database operations, it may be better to ship part of the client application to the server and send only the results across the network. • Example 2: (Send Server code to Client) ...
Chapter 8
... • They provide logically distinct environments that can be individually controlled and managed. They can be stopped and started independent on each other. – Subsystems can have special purposes, such as controlling I/O or virtual machines. Others partition large application systems to make them more ...
... • They provide logically distinct environments that can be individually controlled and managed. They can be stopped and started independent on each other. – Subsystems can have special purposes, such as controlling I/O or virtual machines. Others partition large application systems to make them more ...
Chapter 9
... • They provide logically distinct environments that can be individually controlled and managed. They can be stopped and started independent on each other. – Subsystems can have special purposes, such as controlling I/O or virtual machines. Others partition large application systems to make them more ...
... • They provide logically distinct environments that can be individually controlled and managed. They can be stopped and started independent on each other. – Subsystems can have special purposes, such as controlling I/O or virtual machines. Others partition large application systems to make them more ...
Slides - TAMU Computer Science Faculty Pages
... Attack on Availability • Destroy hardware (cutting fiber) or software • Modify software in a subtle way (alias commands) • Corrupt packets in transit ...
... Attack on Availability • Destroy hardware (cutting fiber) or software • Modify software in a subtle way (alias commands) • Corrupt packets in transit ...
Lecture 1 - Operating System Overview
... Protection – any mechanism for controlling access of processes or users to resources defined by the OS Security – defense of the system against internal and external attacks Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
... Protection – any mechanism for controlling access of processes or users to resources defined by the OS Security – defense of the system against internal and external attacks Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
Test Bank Chapter Three (Operating Systems)
... 1. Explain the difference between application software and system software. ANSWER: System software provides the infrastructure required by the application software. It includes the operating system and utilities. Application software provides the unique functionality required to perform the particu ...
... 1. Explain the difference between application software and system software. ANSWER: System software provides the infrastructure required by the application software. It includes the operating system and utilities. Application software provides the unique functionality required to perform the particu ...
LINUX
... implementations of UNIX (including every system utility described in the POSIX.2 specification) has been ported to Linux. This includes commands such as ls, cp, grep, awk, sed, bc, wc, more, and so on. These system utilities are designed to be powerful tools that do a single task extremely well (e.g ...
... implementations of UNIX (including every system utility described in the POSIX.2 specification) has been ported to Linux. This includes commands such as ls, cp, grep, awk, sed, bc, wc, more, and so on. These system utilities are designed to be powerful tools that do a single task extremely well (e.g ...
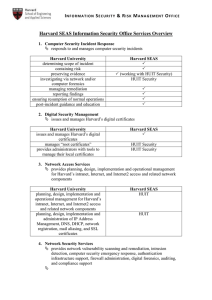
Harvard SEAS Information Security Office Services Overview
... detects and reports on computers that exhibit characteristics consistent with infection by spyware, trojan horse or other malware, via traffic analysis or notification by a trusted third party analyzes network packet data for anomalous activity, targeted system attacks or network Denial of Service a ...
... detects and reports on computers that exhibit characteristics consistent with infection by spyware, trojan horse or other malware, via traffic analysis or notification by a trusted third party analyzes network packet data for anomalous activity, targeted system attacks or network Denial of Service a ...
ch22
... loaded, and manages buffers for I/O requests. Works with VM Manager to provide memory-mapped file I/O. Controls the XP cache manager, which handles caching for the entire I/O system. Supports both synchronous and asynchronous operations, provides time outs for drivers, and has mechanisms for o ...
... loaded, and manages buffers for I/O requests. Works with VM Manager to provide memory-mapped file I/O. Controls the XP cache manager, which handles caching for the entire I/O system. Supports both synchronous and asynchronous operations, provides time outs for drivers, and has mechanisms for o ...
No Slide Title
... Virtual Memory Manager (Cont.) The virtual address translation in 2000 uses several data ...
... Virtual Memory Manager (Cont.) The virtual address translation in 2000 uses several data ...
Preface
... • Protection and security. Chapters 13 and 14 discuss the mechanisms necessary for the protection and security of computer systems. The processes in an operating system must be protected from one another’s activities, and to provide such protection, we must ensure that only processes that have gaine ...
... • Protection and security. Chapters 13 and 14 discuss the mechanisms necessary for the protection and security of computer systems. The processes in an operating system must be protected from one another’s activities, and to provide such protection, we must ensure that only processes that have gaine ...
Syllabus - Jordan University of Science and Technology
... Know how to synchronize processes using semaphores and know how to solve deadlocks using different methods. ...
... Know how to synchronize processes using semaphores and know how to solve deadlocks using different methods. ...
The History of Amoeba
... simplistic way to handle the needs of distributed systems and parallels while maintaining the transparency for its users. The transparency that is being maintained is that the user has no clue how the underlying system works, where the files are stored or on which machine the process is running. Tra ...
... simplistic way to handle the needs of distributed systems and parallels while maintaining the transparency for its users. The transparency that is being maintained is that the user has no clue how the underlying system works, where the files are stored or on which machine the process is running. Tra ...
CS-3013 Week 0:- Introduction
... security: how is the integrity of the OS and its resources ensured? protection: how is one user/program protected from another? performance: how do we make it all go fast? reliability: what happens if something goes wrong – hardware or software extensibility: can we add new features? communication: ...
... security: how is the integrity of the OS and its resources ensured? protection: how is one user/program protected from another? performance: how do we make it all go fast? reliability: what happens if something goes wrong – hardware or software extensibility: can we add new features? communication: ...
Network Operating Systems - Partha Dasgupta`s Workstation!
... well-defined protocol defining the requests that can be made to that server and the responses that are expected. In addition, any process can make a request; that is anyone can become a client, even temporarily. For example, a server process can obtain services from yet another server process, and w ...
... well-defined protocol defining the requests that can be made to that server and the responses that are expected. In addition, any process can make a request; that is anyone can become a client, even temporarily. For example, a server process can obtain services from yet another server process, and w ...
Chapter 4
... 15. A wireless access point that is secretly installed in an office without the employer’s permission is known as a(n) _____. rogue access point 16. Explain how a disassociation frame DoS attack functions. An attacker can pretend to be an access point and send a forged disassociation frame to a wire ...
... 15. A wireless access point that is secretly installed in an office without the employer’s permission is known as a(n) _____. rogue access point 16. Explain how a disassociation frame DoS attack functions. An attacker can pretend to be an access point and send a forged disassociation frame to a wire ...
Are Clouds Secure? - San Francisco Bay Area ISSA Chapter
... • Shared infrastructure • Hardware – CPU, memory, disks, network • Software – virtualization layer (e.g., Xen) • Web Console – provisioning, image management ...
... • Shared infrastructure • Hardware – CPU, memory, disks, network • Software – virtualization layer (e.g., Xen) • Web Console – provisioning, image management ...
Are Clouds Secure?
... • Shared infrastructure • Hardware – CPU, memory, disks, network • Software – virtualization layer (e.g., Xen) • Web Console – provisioning, image management ...
... • Shared infrastructure • Hardware – CPU, memory, disks, network • Software – virtualization layer (e.g., Xen) • Web Console – provisioning, image management ...
Slide 1
... This type of firewall has a set of rules that the packets must pass to get in or out. The primary security feature of a proxy firewall is that it hides the client information. It can be used to hide the internal addresses from the outside would through Network Address Translation, which does not all ...
... This type of firewall has a set of rules that the packets must pass to get in or out. The primary security feature of a proxy firewall is that it hides the client information. It can be used to hide the internal addresses from the outside would through Network Address Translation, which does not all ...