Web-Based Operating Systems
... personal files to provide illusion of one cohesive system. Not just a service but a platform. ...
... personal files to provide illusion of one cohesive system. Not just a service but a platform. ...
I/O Systems 2.
... Key to performance Spooling - hold output for a device If device can serve only one request at a time i.e., Printing Device reservation - provides exclusive access to a ...
... Key to performance Spooling - hold output for a device If device can serve only one request at a time i.e., Printing Device reservation - provides exclusive access to a ...
Diploma in Computer Systems and Network Technology
... and Exchange Server. Topics include the architecture and communication abilities of Exchange Server; installation of Exchange Server, backward integration and compatibility, client support, and configuration; Exchange Server management; Microsoft® Web Access and Web Storage System, real-time collabo ...
... and Exchange Server. Topics include the architecture and communication abilities of Exchange Server; installation of Exchange Server, backward integration and compatibility, client support, and configuration; Exchange Server management; Microsoft® Web Access and Web Storage System, real-time collabo ...
Virtual Private Network(VPN)
... authentication—ensuring that the data originates at the source that it claims access control—restricting unauthorized users from gaining admission to the network confidentiality—preventing anyone from reading or copying data as it travels across the Internet data integrity—ensuring that no o ...
... authentication—ensuring that the data originates at the source that it claims access control—restricting unauthorized users from gaining admission to the network confidentiality—preventing anyone from reading or copying data as it travels across the Internet data integrity—ensuring that no o ...
COSC A365 Chapter 1
... Process termination requires reclaim of any reusable resources Program is passive, process is active, unit of work within system Single-threaded process has one program counter specifying location of next instruction to execute ...
... Process termination requires reclaim of any reusable resources Program is passive, process is active, unit of work within system Single-threaded process has one program counter specifying location of next instruction to execute ...
The Sprite Network Operating System
... the migrated process and to the user, as described below. The only noticeable difference after migration will be a reduction in the load of the home machine. Initially, we expect migration to be used in two ways. First, there are shell commands for manual migration, which allow users to migrate proc ...
... the migrated process and to the user, as described below. The only noticeable difference after migration will be a reduction in the load of the home machine. Initially, we expect migration to be used in two ways. First, there are shell commands for manual migration, which allow users to migrate proc ...
Guide to Operating System Security
... Programs that replicate on the same computer or send themselves to many other computers Can open a back door ...
... Programs that replicate on the same computer or send themselves to many other computers Can open a back door ...
abstract - Chennaisunday.com
... sector but also to the government sector. As a result, many aspects required for successful PKI, such as insurance and legal aspects, have been greatly improved. The Public-key system makes it possible for two parties to communicate securely without either having to know or trust the other party. Ho ...
... sector but also to the government sector. As a result, many aspects required for successful PKI, such as insurance and legal aspects, have been greatly improved. The Public-key system makes it possible for two parties to communicate securely without either having to know or trust the other party. Ho ...
Quick UNIX Tutorial
... home directory or any of its subdirectories. x: means the right to access files in the directory. This implies that you may read files in the directory if you have read permission on the individual files. example: CS4315 ...
... home directory or any of its subdirectories. x: means the right to access files in the directory. This implies that you may read files in the directory if you have read permission on the individual files. example: CS4315 ...
course outline - Clackamas Community College
... Demonstrate and explain the desktop metaphor as exemplified in both the Windows and Mac OS GUIs with a focus on the concepts and skills that are common amongst four versions of Windows. (NT, 98, 2000, and XP.) For all of these operating systems, demonstrate and explain their basic features, plus the ...
... Demonstrate and explain the desktop metaphor as exemplified in both the Windows and Mac OS GUIs with a focus on the concepts and skills that are common amongst four versions of Windows. (NT, 98, 2000, and XP.) For all of these operating systems, demonstrate and explain their basic features, plus the ...
Firewall Evolution
... second generation firewalls had the same capabilities as packet filter firewalls, but they monitored and stored the session and connection state. They associated related packets in a flow based on source and destination IP addresses, source and destination ports, and the protocol used. If a packet m ...
... second generation firewalls had the same capabilities as packet filter firewalls, but they monitored and stored the session and connection state. They associated related packets in a flow based on source and destination IP addresses, source and destination ports, and the protocol used. If a packet m ...
Slide 1
... User wants to access his account from the web browser. As his data is stored in database, web server run a program to access database. This database server may, in turn, fetch financial transaction records from another database server. An application server interprets the returned data by following ...
... User wants to access his account from the web browser. As his data is stored in database, web server run a program to access database. This database server may, in turn, fetch financial transaction records from another database server. An application server interprets the returned data by following ...
Lecture 5
... I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. File-system manipulation – program capability to read, write, create, and delete files. Communications – exchange of information between processes executing eithe ...
... I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. File-system manipulation – program capability to read, write, create, and delete files. Communications – exchange of information between processes executing eithe ...
2. OS Structures - FSU Computer Science
... concurrently, resources must be allocated to each of them ...
... concurrently, resources must be allocated to each of them ...
Chapter 2: Operating-System Structures Silberschatz, Galvin and Gagne ©2013 – 9
... Operating System Services User Operating System Interface System Calls Types of System Calls ...
... Operating System Services User Operating System Interface System Calls Types of System Calls ...
Key To Personal Information Security
... Exploit the way that the Internet Protocol (IP) requires a packet that is too large for the next router to handle be divided into fragments. The fragmented packet identifies an offset to the beginning of the first packet that enables the entire packet to be reassembled by the receiving system. In th ...
... Exploit the way that the Internet Protocol (IP) requires a packet that is too large for the next router to handle be divided into fragments. The fragmented packet identifies an offset to the beginning of the first packet that enables the entire packet to be reassembled by the receiving system. In th ...
Operating Systems for Parallel Processing - Current Activities
... applications will remain important users of parallel computing technology. A parallel computer is a set of processors that are able to work cooperatively to solve a computational problem. Based on this definition, a parallel computer could be a supercomputer with hundreds or thousands of processors ...
... applications will remain important users of parallel computing technology. A parallel computer is a set of processors that are able to work cooperatively to solve a computational problem. Based on this definition, a parallel computer could be a supercomputer with hundreds or thousands of processors ...
Ch. 7 Windows NT/2000/XP Operating Systems
... much more obscure type of file system. • The OS/2 software that uses this file system is still in use today. • HPFS used physical sectors. Overall system performance increased as a result of this file system but it lacked the necessary tools and security that NTFS would provide. ...
... much more obscure type of file system. • The OS/2 software that uses this file system is still in use today. • HPFS used physical sectors. Overall system performance increased as a result of this file system but it lacked the necessary tools and security that NTFS would provide. ...
THE USER VIEW OF OPERATING SYSTEMS
... In Chapter 15, we introduced you to two different views of the role of the operating system as part of the overall computer architecture. Specifically, we looked at the operating system both as a means of delivering services to the user and as a way of controlling and operating the system facilities ...
... In Chapter 15, we introduced you to two different views of the role of the operating system as part of the overall computer architecture. Specifically, we looked at the operating system both as a means of delivering services to the user and as a way of controlling and operating the system facilities ...
IMPACT OF SECURITY BREACHES
... environment, it cannot be considered secure. For example, a maintenance engineer might swap a single failed disk from a RAID1 array that contains customer data. This disk might be repairable. The data is now in the hands of a third party. The first step is to separate servers from human operators an ...
... environment, it cannot be considered secure. For example, a maintenance engineer might swap a single failed disk from a RAID1 array that contains customer data. This disk might be repairable. The data is now in the hands of a third party. The first step is to separate servers from human operators an ...
Chapter 1
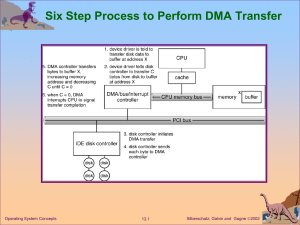
... seven or more devices can be attached to a SCSI (small computer system interface) controller. Each device controller maintains local buffer storage and a set of special purpose registers Typically, operating systems have a device driver for each device controller. To start an I/O, the device drive ...
... seven or more devices can be attached to a SCSI (small computer system interface) controller. Each device controller maintains local buffer storage and a set of special purpose registers Typically, operating systems have a device driver for each device controller. To start an I/O, the device drive ...
chap4 seq7
... the transaction file has served its purpose. System Analysis and Design System Design ...
... the transaction file has served its purpose. System Analysis and Design System Design ...
Lecture #1
... CPU moves data between main memory and local buffers I/O is from the device to local buffer of controller Device controller informs CPU that it has finished its operation by ...
... CPU moves data between main memory and local buffers I/O is from the device to local buffer of controller Device controller informs CPU that it has finished its operation by ...