Document
... grid and left behind software programs that could be used to disrupt the system, according to current and former national-security officials. The spies came from China, Russia and other countries, these officials said, and were believed to be on a mission to navigate the U.S. electrical system and i ...
... grid and left behind software programs that could be used to disrupt the system, according to current and former national-security officials. The spies came from China, Russia and other countries, these officials said, and were believed to be on a mission to navigate the U.S. electrical system and i ...
What is Operating System, Kernel and Types of kernels
... So, if suppose a basic service like network service crashes due to buffer overflow, then only the networking service's memory would be corrupted, leaving the rest of the system still functional. In this architecture, all the basic OS services which are made part of user space are made to run as serv ...
... So, if suppose a basic service like network service crashes due to buffer overflow, then only the networking service's memory would be corrupted, leaving the rest of the system still functional. In this architecture, all the basic OS services which are made part of user space are made to run as serv ...
Embedded Operating Systems Selection Guide
... Text viewer applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 Security applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 Special features . . . . . . . . . . . . . . . . . ...
... Text viewer applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 Security applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 Special features . . . . . . . . . . . . . . . . . ...
Building the Wolfson Audio drivers into the kernel on
... Please Note: This guide is for medium to advanced users only as it assumes you have at least basic linux knowledge and describes the process of patching and re-compiling the kernel software on the Raspberry Pi in order to provide support for the Wolfson Audio Card. ...
... Please Note: This guide is for medium to advanced users only as it assumes you have at least basic linux knowledge and describes the process of patching and re-compiling the kernel software on the Raspberry Pi in order to provide support for the Wolfson Audio Card. ...
Document
... (e.g., block vs. character devices in Unix) – the OS may provide a system call interface that permits low level interaction between application programs and a device • operating system often buffers data that is moving between devices and application programs’ address spaces – benefits: solve timing ...
... (e.g., block vs. character devices in Unix) – the OS may provide a system call interface that permits low level interaction between application programs and a device • operating system often buffers data that is moving between devices and application programs’ address spaces – benefits: solve timing ...
Change Control Management
... • The process that involves the deployment of security updates. The patch management process must be formalized through documentation and receive management approval to provide the best possible strategy for implementing this type of system change. • Security practitioners should monitor their netwo ...
... • The process that involves the deployment of security updates. The patch management process must be formalized through documentation and receive management approval to provide the best possible strategy for implementing this type of system change. • Security practitioners should monitor their netwo ...
Basic System and Application Software_LAS
... educational packages that they offer, which involve a whole course or lessons bundled together on a particular subject with tests and other materials. We can view this software as ‘computer-formatted’ classroom software that allows an individual to gain learning experience without being physically p ...
... educational packages that they offer, which involve a whole course or lessons bundled together on a particular subject with tests and other materials. We can view this software as ‘computer-formatted’ classroom software that allows an individual to gain learning experience without being physically p ...
Based Platform for Advanced Studies on Operating Systems
... considerable less effort (in large networks, it could be at most 10% than by using the standard working manner, with multi-boot computers and independent OS-es). With this respect, an important facility we created for our system is the automated virtual machines replication on all workstation: when ...
... considerable less effort (in large networks, it could be at most 10% than by using the standard working manner, with multi-boot computers and independent OS-es). With this respect, an important facility we created for our system is the automated virtual machines replication on all workstation: when ...
Survery of Operating Systems 2nd Edition
... Purpose and Functions of Microcomputer Operating systems – You can identify most of the functions provided by your operating system by careful observation. For instance, evidence of support of the security function includes a required logon procedure when you start your computer, and the need fo ...
... Purpose and Functions of Microcomputer Operating systems – You can identify most of the functions provided by your operating system by careful observation. For instance, evidence of support of the security function includes a required logon procedure when you start your computer, and the need fo ...
Migration
... to be saved to a file (much like a persistent object) and then a new process to be created (restored) based on this checkpoint file. This checkpoint file contains all of the "goods" including the kernel material. Univ. of Tehran ...
... to be saved to a file (much like a persistent object) and then a new process to be created (restored) based on this checkpoint file. This checkpoint file contains all of the "goods" including the kernel material. Univ. of Tehran ...
Signs of Intrusion on a Host Computer
... ensuring the integrity of the system by examining software, making sure it is verifiable and updated. The third phase consists of checking for both network and system abnormal activities, as well as file and directory integrity. The fourth phase involves the inspection of unauthorized devices attach ...
... ensuring the integrity of the system by examining software, making sure it is verifiable and updated. The third phase consists of checking for both network and system abnormal activities, as well as file and directory integrity. The fourth phase involves the inspection of unauthorized devices attach ...
lecture2
... users to resources defined by the OS Security – defense of the system against internal and external attacks Huge range of attacks: denial-of-service (using all resources and keeping legitimate users out of the system), worms, viruses, identity theft, theft of service (unauthorized use of a syste ...
... users to resources defined by the OS Security – defense of the system against internal and external attacks Huge range of attacks: denial-of-service (using all resources and keeping legitimate users out of the system), worms, viruses, identity theft, theft of service (unauthorized use of a syste ...
Computer System Arch..
... Other techniques for better memory utilization • Dynamic Loading - Routine is not loaded until it is called. ...
... Other techniques for better memory utilization • Dynamic Loading - Routine is not loaded until it is called. ...
Fatema Nafa`s presentation on "Measures to
... making applications user friendly but not on making them secure. Operating System Security class ...
... making applications user friendly but not on making them secure. Operating System Security class ...
Chapter 7 Review
... Mobile users in your network report that they frequently lose connectivity with the wireless network on some days, but on other days they don’t have any problems. Which of the following types of attacks could cause this? A. IV B. Wireless jamming C. Replay D. WPA cracking ...
... Mobile users in your network report that they frequently lose connectivity with the wireless network on some days, but on other days they don’t have any problems. Which of the following types of attacks could cause this? A. IV B. Wireless jamming C. Replay D. WPA cracking ...
Lab Learning Outcomes - GET
... 1. Operating System Interface: Describe the various operating system interfaces: command line, menu-based, graphical, gesture and application program. Explain the purpose of each (Englander, Chapter 16; Null, Chapter 8) 2. Workload Management: Explain the various workload types: batch, online and re ...
... 1. Operating System Interface: Describe the various operating system interfaces: command line, menu-based, graphical, gesture and application program. Explain the purpose of each (Englander, Chapter 16; Null, Chapter 8) 2. Workload Management: Explain the various workload types: batch, online and re ...
Chapter 4
... Plug and Play (PnP) — A service that allows the Windows operating system to automatically detect new hardware when it is installed on a computer. security vulnerability — A weakness or flaw in an information system that could be exploited to cause harm. slot time — The amount of time that a de ...
... Plug and Play (PnP) — A service that allows the Windows operating system to automatically detect new hardware when it is installed on a computer. security vulnerability — A weakness or flaw in an information system that could be exploited to cause harm. slot time — The amount of time that a de ...
Chap 4: Security Baselines
... • Rule base or access control list (ACL): rules a network device uses to permit or deny a packet (not to be confused with ACLs used in securing a file system) • Rules are composed of several settings (listed on pages 122 and 123 of the text) • Observe the basic guidelines on page 124 of the text ...
... • Rule base or access control list (ACL): rules a network device uses to permit or deny a packet (not to be confused with ACLs used in securing a file system) • Rules are composed of several settings (listed on pages 122 and 123 of the text) • Observe the basic guidelines on page 124 of the text ...
XML: Part - tc3.hccs.edu
... • Rule base or access control list (ACL): rules a network device uses to permit or deny a packet (not to be confused with ACLs used in securing a file system) • Rules are composed of several settings (listed on pages 122 and 123 of the text) • Observe the basic guidelines on page 124 of the text ...
... • Rule base or access control list (ACL): rules a network device uses to permit or deny a packet (not to be confused with ACLs used in securing a file system) • Rules are composed of several settings (listed on pages 122 and 123 of the text) • Observe the basic guidelines on page 124 of the text ...
Incident Response and Honeypots
... Kill attacker’s processes and/or accounts. Block attacker’s network access to system. Patch and repair what you think was changed, ...
... Kill attacker’s processes and/or accounts. Block attacker’s network access to system. Patch and repair what you think was changed, ...
Operating Systems
... Creating Folders (Subdirectories) • Store files on disk – Done after disk partitioned and formatted – Divides disk further into folders or directories • Can also contain subfolders or subdirectories ...
... Creating Folders (Subdirectories) • Store files on disk – Done after disk partitioned and formatted – Divides disk further into folders or directories • Can also contain subfolders or subdirectories ...
Chapter 11 Outline
... B. Telnet allows users to log in remotely and access resources as if the user had a local terminal connection. C. Telnet has little security since information is passed over the TCP/IP connection, including account names and passwords. D. Telnet makes its connection using TCP port 23. III. SSH A. Se ...
... B. Telnet allows users to log in remotely and access resources as if the user had a local terminal connection. C. Telnet has little security since information is passed over the TCP/IP connection, including account names and passwords. D. Telnet makes its connection using TCP port 23. III. SSH A. Se ...
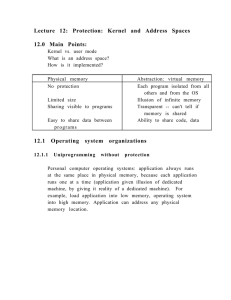
Lecture 12: Protection: Kernel and Address Spaces 12.0 Main Points
... machine, by giving it reality of a dedicated machine). For example, load application into low memory, operating system into high memory. Application can address any physical memory location. ...
... machine, by giving it reality of a dedicated machine). For example, load application into low memory, operating system into high memory. Application can address any physical memory location. ...