Slide 1
... Trusted Network Interpretation of the Trusted Computer System Evaluation Criteria (1987) ...
... Trusted Network Interpretation of the Trusted Computer System Evaluation Criteria (1987) ...
History of operating systems
... These operations require in general a functional OS on both platforms involved. In general, it can be said that videogame consoles and arcade coin operated machines used at most a built-in BIOS during the 1970s, 1980s and most of the 1990s, while from the PlayStation era and beyond they started gett ...
... These operations require in general a functional OS on both platforms involved. In general, it can be said that videogame consoles and arcade coin operated machines used at most a built-in BIOS during the 1970s, 1980s and most of the 1990s, while from the PlayStation era and beyond they started gett ...
A Pattern Language for Secure Operating System Architectures
... into segments that correspond to logical units in the programs. Use special words (descriptors) to represent access rights for these segments. • Reference Monitor. How to enforce authorizations when a process requests access to an object? Define an abstract process that intercepts all requests for r ...
... into segments that correspond to logical units in the programs. Use special words (descriptors) to represent access rights for these segments. • Reference Monitor. How to enforce authorizations when a process requests access to an object? Define an abstract process that intercepts all requests for r ...
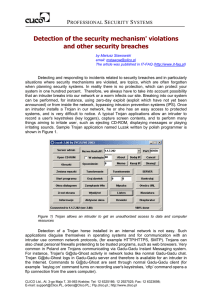
Detection of the security mechanism` violations and other
... hours). With right mouse button click an administrator can read attacks performed by an intruder, services which have been attacked and time of attacks as well as other related data (such as protection system reaction). In order to further explain events, an administrator can analyze sessions relate ...
... hours). With right mouse button click an administrator can read attacks performed by an intruder, services which have been attacked and time of attacks as well as other related data (such as protection system reaction). In order to further explain events, an administrator can analyze sessions relate ...
Bandura® Releases REACT™ Software to Integrate Internal
... security technology, today introduced the REACT™ software product that allows customers to integrate real‐time threat information from their own network into the PoliWall® security appliance, providing a critical element of secure network architecture. PoliWall is an in‐line appliance (physical ...
... security technology, today introduced the REACT™ software product that allows customers to integrate real‐time threat information from their own network into the PoliWall® security appliance, providing a critical element of secure network architecture. PoliWall is an in‐line appliance (physical ...
Week-2
... Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code ...
... Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code ...
Key To Personal Information Security
... (LAN) or Internet run many services that listen at well-known and not so well known ports • By port scanning, the attacker finds which ports are available (i.e., what service might be listing to a port) • A port scan consists of sending a message to each port, one at a time • The kind of response re ...
... (LAN) or Internet run many services that listen at well-known and not so well known ports • By port scanning, the attacker finds which ports are available (i.e., what service might be listing to a port) • A port scan consists of sending a message to each port, one at a time • The kind of response re ...
Data Mining BS/MS Project
... – Detecting threats using network data – Detecting threats using host-based data ...
... – Detecting threats using network data – Detecting threats using host-based data ...
Operating System
... feature the icons we ahve come to recognize in today's graphical user interfaces. • - some Window 1 features, however-menu systems, tiled windows, and mouse access-created a benchmark for future, even more advanced Windows versions. • - Windows 1.x also introduced limited multitasking to the PC worl ...
... feature the icons we ahve come to recognize in today's graphical user interfaces. • - some Window 1 features, however-menu systems, tiled windows, and mouse access-created a benchmark for future, even more advanced Windows versions. • - Windows 1.x also introduced limited multitasking to the PC worl ...
Presentation
... • With a new system called large block allocation (LBA), it is now possible to make file systems much larger than 512 MB under MS-DOS • LBA translates larger logical blocks to smaller ones for support of larger physical disks • However, the disk controller and disk must support LBA, and they must be ...
... • With a new system called large block allocation (LBA), it is now possible to make file systems much larger than 512 MB under MS-DOS • LBA translates larger logical blocks to smaller ones for support of larger physical disks • However, the disk controller and disk must support LBA, and they must be ...
Figure 3.1
... Handling competition for a resource • Semaphore = a control flag telling if resource is in use – Test and set must be done together for proper function ...
... Handling competition for a resource • Semaphore = a control flag telling if resource is in use – Test and set must be done together for proper function ...
601331-OS-QA-2016
... To define the objectives and function s of the modern operating systems. Describe the evolution of the OS from primitive batch systems to sophisticated multi user systems Explain the different types of schedulers; short, medium and long term. To differentiate between user and kernel modes in an oper ...
... To define the objectives and function s of the modern operating systems. Describe the evolution of the OS from primitive batch systems to sophisticated multi user systems Explain the different types of schedulers; short, medium and long term. To differentiate between user and kernel modes in an oper ...
1.1. OS Introduction Operating System Types
... in memory. The main advantage of the virtual-memory scheme is that programs can be larger than physical memory. Further, it abstracts main memory into a large, uniform array of storage, separating logical memory as viewed by the user from physical memory. This arrangement frees programmers from conc ...
... in memory. The main advantage of the virtual-memory scheme is that programs can be larger than physical memory. Further, it abstracts main memory into a large, uniform array of storage, separating logical memory as viewed by the user from physical memory. This arrangement frees programmers from conc ...
No Slide Title - ECE Users Pages
... 2. Operating system – controls and coordinates the use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video game ...
... 2. Operating system – controls and coordinates the use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video game ...
Introduction to Unix
... described in the POSIX.2 specification) has been ported to Linux. This includes commands such as ls, cp, grep, awk, sed, bc, wc, more, and so on. These system utilities are designed to be powerful tools that do a single task extremely well (e.g. grep finds text inside files while wc counts the numbe ...
... described in the POSIX.2 specification) has been ported to Linux. This includes commands such as ls, cp, grep, awk, sed, bc, wc, more, and so on. These system utilities are designed to be powerful tools that do a single task extremely well (e.g. grep finds text inside files while wc counts the numbe ...
Computer security - University of London International Programmes
... This course deals with the more technical means of making a computing system secure. This process starts with defining the proper security requirements, which are usually stated as a security policy. Security models formalise those policies and may serve as a reference to check the correctness of an ...
... This course deals with the more technical means of making a computing system secure. This process starts with defining the proper security requirements, which are usually stated as a security policy. Security models formalise those policies and may serve as a reference to check the correctness of an ...
What is an Operating System?
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
OpenIO SDS with Grid for Apps: a unique solution for media
... compute systems from specific tasks and run them directly on the nodes present in its cluster. ...
... compute systems from specific tasks and run them directly on the nodes present in its cluster. ...
CS430 – Operating Systems 07/06/2006 – 08/27/2006 – Fort Collins Facilitator Information
... Question 2: Discuss the interrupt architecture and Direct Memory Access (DMA). Explain how these techniques work. ...
... Question 2: Discuss the interrupt architecture and Direct Memory Access (DMA). Explain how these techniques work. ...
ppt
... by Linus Torvalds, with the major design goal of UNIX compatibility, released as open source Its history has been one of collaboration by many users from all around the world, corresponding almost exclusively over the Internet It has been designed to run efficiently and reliably on ...
... by Linus Torvalds, with the major design goal of UNIX compatibility, released as open source Its history has been one of collaboration by many users from all around the world, corresponding almost exclusively over the Internet It has been designed to run efficiently and reliably on ...
System Management
... • The network manager allows a network admin to monitor the use of individual computers and shared hardware, and ensure software license agreement ...
... • The network manager allows a network admin to monitor the use of individual computers and shared hardware, and ensure software license agreement ...
Operating System Concepts
... which job to run next, to increase CPU utilization. The most important aspect of job scheduling is the ability to multiprogram : OS keeps several jobs in memory at a time. ...
... which job to run next, to increase CPU utilization. The most important aspect of job scheduling is the ability to multiprogram : OS keeps several jobs in memory at a time. ...
Operating System
... computers sharing a network and users explicitly login and use these computers. Distributed operating system users are not aware that there are multiple computers available to them to run their programs. The system appears to them as if it is a uni-processor operating ...
... computers sharing a network and users explicitly login and use these computers. Distributed operating system users are not aware that there are multiple computers available to them to run their programs. The system appears to them as if it is a uni-processor operating ...