Document
... • ISPs – Too much & diverse traffic to monitor – Hard to get a complete picture – Routers barely keep up with core tasks ...
... • ISPs – Too much & diverse traffic to monitor – Hard to get a complete picture – Routers barely keep up with core tasks ...
The Network Layer
... A basic idea is to allocate the remaining class C networks (more than 2 million, and later A and B) in variable sized blocks of 254 addresses, a site needing 8000 addresses then gets 32 contiguous class C networks. The world was divided up into 4 zones to easy hierarchical routing. A site outside Eu ...
... A basic idea is to allocate the remaining class C networks (more than 2 million, and later A and B) in variable sized blocks of 254 addresses, a site needing 8000 addresses then gets 32 contiguous class C networks. The world was divided up into 4 zones to easy hierarchical routing. A site outside Eu ...
JRA1.4 AAs in eduGAIN
... the VOOT protocol (based on SCHIM) to describe groups and memberships offline from user authentication. ...
... the VOOT protocol (based on SCHIM) to describe groups and memberships offline from user authentication. ...
Part I: Introduction
... network protocols: machines rather than humans all communication activity in Internet governed by protocols protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt, other events ...
... network protocols: machines rather than humans all communication activity in Internet governed by protocols protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt, other events ...
Covert channel
... Yiqi Dai, Department of Computer Science and Technology, Tsinghua University, Beijing 10084, China ...
... Yiqi Dai, Department of Computer Science and Technology, Tsinghua University, Beijing 10084, China ...
Security Considerations for Health Care Organizations
... Do you trust wireless Cell phone Communications? Are you sure that the person at the other end of the ...
... Do you trust wireless Cell phone Communications? Are you sure that the person at the other end of the ...
Overlay Network and Data Transmission over Wireless
... How to combat with channel error What should we do when packet loss happens But one step back @ what rate should we send multimedia data? Send @ maximum available rate, how? Over wired network: TCP-friendly Over wireless network?... Could we reduce the number of packet loss in case o ...
... How to combat with channel error What should we do when packet loss happens But one step back @ what rate should we send multimedia data? Send @ maximum available rate, how? Over wired network: TCP-friendly Over wireless network?... Could we reduce the number of packet loss in case o ...
Metro & CPE Flow Router - Monarch Network Architects
... People in less developed areas will have more capacity than is available in developed areas today! Users in developed areas could see 3-10 hours of video per day (HD or SD) Requires a 60 times increase in capacity (Moore’s Law increase) ...
... People in less developed areas will have more capacity than is available in developed areas today! Users in developed areas could see 3-10 hours of video per day (HD or SD) Requires a 60 times increase in capacity (Moore’s Law increase) ...
Secure Group Communications in Wireless Sensor Networks
... Its long-term goal is to acquire and save Internet topological data over a long period of time. This data has been used in the study of routing problems and changes, DDoS attacks, and graph theory. IPSonar inject small non-intrusive measurement packets ...
... Its long-term goal is to acquire and save Internet topological data over a long period of time. This data has been used in the study of routing problems and changes, DDoS attacks, and graph theory. IPSonar inject small non-intrusive measurement packets ...
cpt1 - NDSU Computer Science
... – Packets of different sources interleaved on link – Buffer packets that are contending for the link – Packet queue processed FIFO/priority – Buffer overflow is called congestion Physical link shared over time (like TDM) but data transmitted on demand, not during predetermined time slots. Flow gets ...
... – Packets of different sources interleaved on link – Buffer packets that are contending for the link – Packet queue processed FIFO/priority – Buffer overflow is called congestion Physical link shared over time (like TDM) but data transmitted on demand, not during predetermined time slots. Flow gets ...
Overview
... • A free open source utility for network exploration or security auditing. • Designed to rapidly scan large networks, although it works fine against single hosts. ...
... • A free open source utility for network exploration or security auditing. • Designed to rapidly scan large networks, although it works fine against single hosts. ...
Network Technology Foundations
... Firewalls can cause a bottleneck Firewalls may not allow homebased account access to the corporate e-mail server To troubleshoot firewall problems: • Verify that you are using the correct IP address and subnet mask • Check your default gateway and verify that the computer can communicate with system ...
... Firewalls can cause a bottleneck Firewalls may not allow homebased account access to the corporate e-mail server To troubleshoot firewall problems: • Verify that you are using the correct IP address and subnet mask • Check your default gateway and verify that the computer can communicate with system ...
pptx
... Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
... Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
The OSI Networking Model - Oakton Community College
... Organization for Standardization, defines how the various hardware and software components involved in data communication should interact with each other. A good analogy would be a traveler who prepares herself to return home through many dangerous kingdoms by obtaining permits to enter each country ...
... Organization for Standardization, defines how the various hardware and software components involved in data communication should interact with each other. A good analogy would be a traveler who prepares herself to return home through many dangerous kingdoms by obtaining permits to enter each country ...
physcial_sci_networks_part2
... Security Issues • Secrecy – Keeping information out of the hands of unauthorised users. ...
... Security Issues • Secrecy – Keeping information out of the hands of unauthorised users. ...
NJR2 - 100 Delawanna Ave., Clifton, NJ
... NJR2 (100 Delawanna Ave.) is one of the most network-rich, interconnected colocation centers in the New York City metro area. Located just 11-miles outside of Manhattan, this 211,000 sq. ft. data center is an ideal location for financial services firms looking to run low-latency back office operatio ...
... NJR2 (100 Delawanna Ave.) is one of the most network-rich, interconnected colocation centers in the New York City metro area. Located just 11-miles outside of Manhattan, this 211,000 sq. ft. data center is an ideal location for financial services firms looking to run low-latency back office operatio ...
pptx
... Gnutella and BitTorrent for file sharing; the Session Initiation Protocol (SIP) and Skype for voice communication; and many, many more. ...
... Gnutella and BitTorrent for file sharing; the Session Initiation Protocol (SIP) and Skype for voice communication; and many, many more. ...
COS 217, Spring 2005 - Princeton University
... • Revisit definition and placement of function –What are the types of nodes in the system? –What are their powers and limitations? –What information do they exchange? ...
... • Revisit definition and placement of function –What are the types of nodes in the system? –What are their powers and limitations? –What information do they exchange? ...
TDMoIP - dspcsp
... so this issue is orthogonal to that of the previous slides RTP can be used to transport timing across IP networks It does this by providing: a 16 bit sequence number 1 32 bit timestamp at the expense of 12 additional overhead bytes per packet Accurate timing is important in telephony and IP netw ...
... so this issue is orthogonal to that of the previous slides RTP can be used to transport timing across IP networks It does this by providing: a 16 bit sequence number 1 32 bit timestamp at the expense of 12 additional overhead bytes per packet Accurate timing is important in telephony and IP netw ...
pdf
... – in the future, to solve the interesting problems, we will need to get large collections of small machines to cooperate ...
... – in the future, to solve the interesting problems, we will need to get large collections of small machines to cooperate ...
OSI Model Pyramid - Redbird Internet Services
... ethernet, token ring; FDDI occurs here; devices: brouters, routers. Switches; protocols: HDLC, LLS Flow Control, SLSP & PPP ...
... ethernet, token ring; FDDI occurs here; devices: brouters, routers. Switches; protocols: HDLC, LLS Flow Control, SLSP & PPP ...
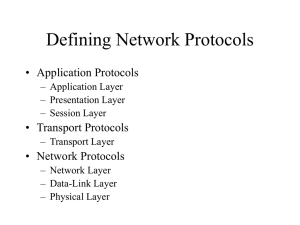
Defining Network Protocols
... • Assigns IP address, gateway (router) address, name server, netmask, time server, and other configuration information based on a NIC’s MAC address • IP addresses may be fixed or taken from a pool of available addresses • Allows assigning temporary addresses for transient computers. ...
... • Assigns IP address, gateway (router) address, name server, netmask, time server, and other configuration information based on a NIC’s MAC address • IP addresses may be fixed or taken from a pool of available addresses • Allows assigning temporary addresses for transient computers. ...
Firewall Categorization Methods
... Extension to PPP that enables dial-up users to establish a VPN connection to a remote access server Uses IPSec to encrypt data Incompatible with NAT but provides a higher level of encryption and ...
... Extension to PPP that enables dial-up users to establish a VPN connection to a remote access server Uses IPSec to encrypt data Incompatible with NAT but provides a higher level of encryption and ...
Home Energy Management
... With the implementation of our Home Energy Management System and the advantage of Real-Time Pricing (RTP) provided by electric utility companies, consumers have the ability to adjust their energy usage in order to reduce their electricity bill. Sponsored by FEEDER – Foundation for Engineering Educ ...
... With the implementation of our Home Energy Management System and the advantage of Real-Time Pricing (RTP) provided by electric utility companies, consumers have the ability to adjust their energy usage in order to reduce their electricity bill. Sponsored by FEEDER – Foundation for Engineering Educ ...