4th Edition: Chapter 1
... • Investigate building blocks of general purpose networks • Want to ask ... what requirements must a network designer be aware of in order to design a sound network? ...
... • Investigate building blocks of general purpose networks • Want to ask ... what requirements must a network designer be aware of in order to design a sound network? ...
Commercial Sales
... IPC Communication Services specializes in the production and distribution of materials and services for the computer industry, and printing of association publications. ...
... IPC Communication Services specializes in the production and distribution of materials and services for the computer industry, and printing of association publications. ...
A Simple and Efficient MAC-Routing Integrated Algorithm for Sensor
... A Simple and Efficient MACRouting Integrated Algorithm for Sensor Network R. Rugin and G. Mazzini University of Ferrara, via Saragat 1, 44100 Ferrara, Italy ...
... A Simple and Efficient MACRouting Integrated Algorithm for Sensor Network R. Rugin and G. Mazzini University of Ferrara, via Saragat 1, 44100 Ferrara, Italy ...
Acronym
... Consortium for Computer Interchange of Museum Information Commercial Internet Exchange A cookie is a way for web sites to recognize whether or not you have visited the site before. It is a piece of data given to a browser by a web server, so that the browser will hand it back to the server on subseq ...
... Consortium for Computer Interchange of Museum Information Commercial Internet Exchange A cookie is a way for web sites to recognize whether or not you have visited the site before. It is a piece of data given to a browser by a web server, so that the browser will hand it back to the server on subseq ...
Quality of Service (QoS)
... punish other, “better-behaved applications”, or so the average of dropped packets is evenly distributed ...
... punish other, “better-behaved applications”, or so the average of dropped packets is evenly distributed ...
Internet Protocol (IP):
... Every host has an address on every network Gateways know how to map from an address in one network address space to an address in another network space ...
... Every host has an address on every network Gateways know how to map from an address in one network address space to an address in another network space ...
Blocking HTTPS traffic with web filtering
... Blocking HTTPS traffic with web filtering Some websites are accessible using HTTPS protocol, such as Youtube. This example shows how to use web filtering to block HTTPS access. ...
... Blocking HTTPS traffic with web filtering Some websites are accessible using HTTPS protocol, such as Youtube. This example shows how to use web filtering to block HTTPS access. ...
downloading
... The smallest value that is larger than 95% of the values in a given sample This means that 95% of the time the channel utilization is equal to or less than this value Or ...
... The smallest value that is larger than 95% of the values in a given sample This means that 95% of the time the channel utilization is equal to or less than this value Or ...
ROUTING PROTOCOL IGRP
... – routed - used by hosts, can be directed or routed – routing -used by routers, directs routed data to the destination – examples - RIP, IGRP ...
... – routed - used by hosts, can be directed or routed – routing -used by routers, directs routed data to the destination – examples - RIP, IGRP ...
Telecommunications and Networking
... remote sites or users together. Instead of using a dedicated, real-world connection such as leased line, a VPN uses "virtual" connections routed through the Internet from the company's private network to the remote site or employee. Source: computer.Howstuffworks.com ...
... remote sites or users together. Instead of using a dedicated, real-world connection such as leased line, a VPN uses "virtual" connections routed through the Internet from the company's private network to the remote site or employee. Source: computer.Howstuffworks.com ...
SDN evolution - FSU Computer Science
... Three principles • The network should be governed by policies declared over high level names • Policy should determine the path that packets follow • The network should enforce a strong binding between a packet and its origin. ...
... Three principles • The network should be governed by policies declared over high level names • Policy should determine the path that packets follow • The network should enforce a strong binding between a packet and its origin. ...
Lecture Notes - Computer Science & Engineering
... There is a hierarchy of domain name servers Each client system uses one domain name server which in turn queries up and down the hierarchy to find the address If your server does not know the address, it goes up the hierarchy possibly to the top and works its way ...
... There is a hierarchy of domain name servers Each client system uses one domain name server which in turn queries up and down the hierarchy to find the address If your server does not know the address, it goes up the hierarchy possibly to the top and works its way ...
Firewalls
... prevent denial of service attacks: SYN flooding: attacker establishes many bogus TCP connections, no resources left for “real” connections prevent illegal modification/access of internal data. e.g., attacker replaces CIA’s homepage with something else allow only authorized access to inside netwo ...
... prevent denial of service attacks: SYN flooding: attacker establishes many bogus TCP connections, no resources left for “real” connections prevent illegal modification/access of internal data. e.g., attacker replaces CIA’s homepage with something else allow only authorized access to inside netwo ...
Document
... creation of the Transmission Control Protocol and the internet protocol (TCP/IP). This decentralized structure together with standard communication methods made expansion easy. ...
... creation of the Transmission Control Protocol and the internet protocol (TCP/IP). This decentralized structure together with standard communication methods made expansion easy. ...
Networking questions
... characterization of the quality of service offered by a network used for digitized voice traffic? 3. A client-server system uses a satellite network, with the satellite at a height of 40,000 km. What is the best case delay in response to a request? 4. Wireless networks are easy to install, which mak ...
... characterization of the quality of service offered by a network used for digitized voice traffic? 3. A client-server system uses a satellite network, with the satellite at a height of 40,000 km. What is the best case delay in response to a request? 4. Wireless networks are easy to install, which mak ...
Powerpoint - Chapter 13
... When users log on to their computers, they are authenticated against an account on that system. If several people use the same computer, each must have a separate user account. When users elsewhere on the network attempt to access server resources on that computer, they are also authenticated agains ...
... When users log on to their computers, they are authenticated against an account on that system. If several people use the same computer, each must have a separate user account. When users elsewhere on the network attempt to access server resources on that computer, they are also authenticated agains ...
Introduction - Department of Information Technologies
... Office Hour: Open Door Policy Class Schedule:Wednesday 17:00-19:45 ...
... Office Hour: Open Door Policy Class Schedule:Wednesday 17:00-19:45 ...
History of the Internet
... – Messages broken into a number of packets + data to help the packet find its way through the Internet (TCP) – Series of switchs called routers (IP) ensures that the packages arrive at their correct destination – Packets are sent over many different routes at the same time • Hardware restriction – d ...
... – Messages broken into a number of packets + data to help the packet find its way through the Internet (TCP) – Series of switchs called routers (IP) ensures that the packages arrive at their correct destination – Packets are sent over many different routes at the same time • Hardware restriction – d ...
network
... 1.1 what is the Internet? 1.2 network edge end systems, access networks, links 1.3 network core packet switching, circuit switching, network structure 1.4 delay, loss, throughput in networks 1.5 protocol layers, service models 1.7 history ...
... 1.1 what is the Internet? 1.2 network edge end systems, access networks, links 1.3 network core packet switching, circuit switching, network structure 1.4 delay, loss, throughput in networks 1.5 protocol layers, service models 1.7 history ...
Application level gateway Firewalls - Mercer University
... Check Point Software debuted Firewall-1, inaugurating the stateful firewall market. The emergence of stateful firewalls represented a middle ground between the performance of packet filtering firewalls and the intelligence and demarcation of proxy firewalls. STATEFUL Firewall Stateful firewalls can ...
... Check Point Software debuted Firewall-1, inaugurating the stateful firewall market. The emergence of stateful firewalls represented a middle ground between the performance of packet filtering firewalls and the intelligence and demarcation of proxy firewalls. STATEFUL Firewall Stateful firewalls can ...
Lec6
... : handles the movement of packets, i.e. Routing Transport Layer : provides a reliable flow of data between two hosts Application Layer : handles the details of the particular application ...
... : handles the movement of packets, i.e. Routing Transport Layer : provides a reliable flow of data between two hosts Application Layer : handles the details of the particular application ...
Lecture 12
... policy, which provides a set of constraints that the set of possible actions must satisfy So, audit functions that may violate the ...
... policy, which provides a set of constraints that the set of possible actions must satisfy So, audit functions that may violate the ...
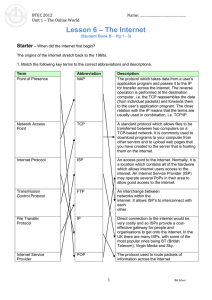
U1L6_The_Internet
... An Internet Service Provider (ISP) is a company which provides access to the internet for individuals or other companies (e.g. BT). An ISP will have many servers to do different things depending on the size of the company and amount of customers, e.g. one for outgoing email, one for incoming email, ...
... An Internet Service Provider (ISP) is a company which provides access to the internet for individuals or other companies (e.g. BT). An ISP will have many servers to do different things depending on the size of the company and amount of customers, e.g. one for outgoing email, one for incoming email, ...
P4P: Proactive Provider Assistance for P2P
... Up to 50-70% of Internet traffic is contributed by P2P applications Cache logic research: Internet protocol breakdown 1993 – 2006; Velocix: File-types on major P2P networks. ...
... Up to 50-70% of Internet traffic is contributed by P2P applications Cache logic research: Internet protocol breakdown 1993 – 2006; Velocix: File-types on major P2P networks. ...
TCPdump
... To demonstrate how to install and use tcpdump and windump and how to analyze data that is collected To understand what the basic functionality of network-based intrusion detection. More information about WinDump, plz visit http://windump.polito.it/docs/defaul t.htm ...
... To demonstrate how to install and use tcpdump and windump and how to analyze data that is collected To understand what the basic functionality of network-based intrusion detection. More information about WinDump, plz visit http://windump.polito.it/docs/defaul t.htm ...