OSI layers
... communicate with each other, and use a star topology. Like a repeater, a hub regenerates the signal. Hubs have the same disadvantage as a repeater, anything it receives on one port, it FLOODS out all other ports. Wherever possible, hubs should be replace by switches. ...
... communicate with each other, and use a star topology. Like a repeater, a hub regenerates the signal. Hubs have the same disadvantage as a repeater, anything it receives on one port, it FLOODS out all other ports. Wherever possible, hubs should be replace by switches. ...
Information-centric networking – Ready for the real world?
... Information-centric networking proposals attract much attention in the ongoingsearch for a future communication paradigm of the Internet. Replacing the host-to-host connectivity by a data-oriented publish/subscribe service eases content distribution and authentication by concept, while eliminating t ...
... Information-centric networking proposals attract much attention in the ongoingsearch for a future communication paradigm of the Internet. Replacing the host-to-host connectivity by a data-oriented publish/subscribe service eases content distribution and authentication by concept, while eliminating t ...
Distance Vector Routing Protocols
... Characteristics of Distance Vector routing protocols – Periodic updates – RIP routing updates include the entire routing table – Neighbors are defined as routers that share a link and are configured to use the same protocol ...
... Characteristics of Distance Vector routing protocols – Periodic updates – RIP routing updates include the entire routing table – Neighbors are defined as routers that share a link and are configured to use the same protocol ...
Intelligent WAN and WAN Design Summary (CVD) – October
... smaller sites or as a backup path because of the risks. Now this cost-effective, performance-enhancing opportunity can be realized at all your branch offices with Cisco IWAN. Cisco IWAN enables organizations to deliver an uncompromised experience over any connection. With Cisco IWAN, IT organization ...
... smaller sites or as a backup path because of the risks. Now this cost-effective, performance-enhancing opportunity can be realized at all your branch offices with Cisco IWAN. Cisco IWAN enables organizations to deliver an uncompromised experience over any connection. With Cisco IWAN, IT organization ...
Final Thesis - University of South Australia
... Like any team based organisation or group, the military adheres to a structure that helps define rankings of power, positioning of people, as well as task separation and allocation of those people. There are many proven key advantages to the utilization of team-based structures in solving problems. ...
... Like any team based organisation or group, the military adheres to a structure that helps define rankings of power, positioning of people, as well as task separation and allocation of those people. There are many proven key advantages to the utilization of team-based structures in solving problems. ...
思科运营商网络研讨会: 苏远超 思科中国电信运营商事业部 高级顾问工程师 2011.10.27
... Management of packet networks Device and connectivity discovery nV support, ASR 9000, ASR 901, ASR 903 device management including single-click upgrades Visualization of physical and virtual RAN topologies ...
... Management of packet networks Device and connectivity discovery nV support, ASR 9000, ASR 901, ASR 903 device management including single-click upgrades Visualization of physical and virtual RAN topologies ...
Chapter 14
... • OSPF divides an autonomous system (AS) into areas, with each area given an Area ID • An area is a collection of networks, hosts & routers contained within an AS • Each AS has a backbone area with an Area ID of 0 (can be written as 0.0.0.0). Routers inside the backbone area are called backbone rout ...
... • OSPF divides an autonomous system (AS) into areas, with each area given an Area ID • An area is a collection of networks, hosts & routers contained within an AS • Each AS has a backbone area with an Area ID of 0 (can be written as 0.0.0.0). Routers inside the backbone area are called backbone rout ...
“Networking is IPC”: A Guiding Principle to a
... Figure 3 shows a repeated instantiation of IPC layers, where bottom IPC layers are tailored to the physical media, including wireless links. Higher IPC layers are built on top of lower layers, for example a higher-level DIF is configured over (and tailored to) the bottom wireless DIFs. This figure i ...
... Figure 3 shows a repeated instantiation of IPC layers, where bottom IPC layers are tailored to the physical media, including wireless links. Higher IPC layers are built on top of lower layers, for example a higher-level DIF is configured over (and tailored to) the bottom wireless DIFs. This figure i ...
x510 Series Datasheet
... »» Comprehensive SNMP MIB support for standardsbased device management »» Built-in text editor »» Event-based triggers allow user-defined scripts to be executed upon selected system events »» USB interface allows software release files, configurations and other files to be stored for backup and dist ...
... »» Comprehensive SNMP MIB support for standardsbased device management »» Built-in text editor »» Event-based triggers allow user-defined scripts to be executed upon selected system events »» USB interface allows software release files, configurations and other files to be stored for backup and dist ...
Powerpoint
... and topology information in the same LSA’s. A change in an IP address means a Type 1 LSA is originated. But because Type 1 LSA’s also carry topology information, a full SPF is run in the local OSPF area – unnecessary; only IP address is ...
... and topology information in the same LSA’s. A change in an IP address means a Type 1 LSA is originated. But because Type 1 LSA’s also carry topology information, a full SPF is run in the local OSPF area – unnecessary; only IP address is ...
Addressing the Network – IPv4 - Information Systems Technology
... Preventing duplication of addresses – keep up with IP addresses as they are assigned. Duplication is NOT allowed! Providing and controlling access - if a server has a random address assigned (DHCP), blocking access to its address is difficult and clients may not be able to locate this resource. ...
... Preventing duplication of addresses – keep up with IP addresses as they are assigned. Duplication is NOT allowed! Providing and controlling access - if a server has a random address assigned (DHCP), blocking access to its address is difficult and clients may not be able to locate this resource. ...
Chapter14 (Unicast Routing Protocols)
... AS can be divided into many different areas. All networks inside an area must be connected. Routers inside an area flood the area with routing information. Area Border Router Summarizes the information about the area and sends it to other ...
... AS can be divided into many different areas. All networks inside an area must be connected. Routers inside an area flood the area with routing information. Area Border Router Summarizes the information about the area and sends it to other ...
WorldNet Data Warehouse Albert Greenberg albert@research
... Refining Initial IP-to-AS Mapping Start with initial IP-to-AS mapping Mapping from BGP tables is usually correct Good starting point for computing the mapping ...
... Refining Initial IP-to-AS Mapping Start with initial IP-to-AS mapping Mapping from BGP tables is usually correct Good starting point for computing the mapping ...
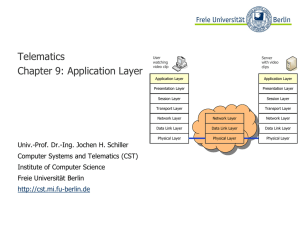
Application Layer - Freie Universität Berlin
... ● The reverse tree represents the Domain Name Space ● The depth of the tree is limited to 127 levels ● Each label can have up to 63 characters ● The whole domain name can have up to 255 characters ● A label of the length 0 is reserved for the root node (“”) ● The Fully Qualified Domain Name (FQDN) i ...
... ● The reverse tree represents the Domain Name Space ● The depth of the tree is limited to 127 levels ● Each label can have up to 63 characters ● The whole domain name can have up to 255 characters ● A label of the length 0 is reserved for the root node (“”) ● The Fully Qualified Domain Name (FQDN) i ...
Wireless sensor network monitoring using the Simple Network
... Wireless sensor networks (WSNs) are networks of low power devices that use their onboard sensors to cooperatively monitor their surroundings. Even though various real world and test WSNs have been designed and constructed they are not always easy to connect to other networks. WSNs are mostly separat ...
... Wireless sensor networks (WSNs) are networks of low power devices that use their onboard sensors to cooperatively monitor their surroundings. Even though various real world and test WSNs have been designed and constructed they are not always easy to connect to other networks. WSNs are mostly separat ...
ipv6 ospf - AfNOG 2017 Workshop on Network Technology
... and topology information in the same LSA’s. A change in an IP address means a Type 1 LSA is originated. But because Type 1 LSA’s also carry topology information, a full SPF is run in the local OSPF area – unnecessary; only IP address is ...
... and topology information in the same LSA’s. A change in an IP address means a Type 1 LSA is originated. But because Type 1 LSA’s also carry topology information, a full SPF is run in the local OSPF area – unnecessary; only IP address is ...
IPv6 Security Threats and Mitigations
... Rogue clients and servers can be mitigated by using the authentication option in DHCPv6 There are not many DHCPv6 client or server implementations using this today ...
... Rogue clients and servers can be mitigated by using the authentication option in DHCPv6 There are not many DHCPv6 client or server implementations using this today ...
OS fingerprinting with IPv6
... Over the next years to come IPv6 will eventually replace IPv4 in private and public networks. This paper attempts to describe upcoming challenges and limitations as well as new methods of OS fingerprinting with the shift to IPv6. This includes performing network scans and finding live hosts to finge ...
... Over the next years to come IPv6 will eventually replace IPv4 in private and public networks. This paper attempts to describe upcoming challenges and limitations as well as new methods of OS fingerprinting with the shift to IPv6. This includes performing network scans and finding live hosts to finge ...
AndroDialysis: Analysis of Android Intent
... Intent is a complex messaging system in the Android platform, and is considered as a security mechanism to hinder applications from gaining access to other applications directly. Applications must have specific permissions to use Intents. This is a way of controlling what applications can do once th ...
... Intent is a complex messaging system in the Android platform, and is considered as a security mechanism to hinder applications from gaining access to other applications directly. Applications must have specific permissions to use Intents. This is a way of controlling what applications can do once th ...
VoIP
... audio VOIP PDU’s divided into smaller units, e.g. four 5 msec units per 20 msec audio VOIP PDU PDU contains small units from different VOIP PDU’s if PDU lost, still have most of every original VOIP PDU no redundancy overhead, but increases playout delay ...
... audio VOIP PDU’s divided into smaller units, e.g. four 5 msec units per 20 msec audio VOIP PDU PDU contains small units from different VOIP PDU’s if PDU lost, still have most of every original VOIP PDU no redundancy overhead, but increases playout delay ...
ch02 - Test Bank 1
... 81. At the ____________________ layer, the user is provided with a number of services, perhaps most aptly called application protocols. 82. Any communications medium may be subject to various types of interference, which is commonly called ____________________. 83. The ____________________ is the pr ...
... 81. At the ____________________ layer, the user is provided with a number of services, perhaps most aptly called application protocols. 82. Any communications medium may be subject to various types of interference, which is commonly called ____________________. 83. The ____________________ is the pr ...
HPE 5900 Switch Series
... reachability, no matter what happens in the data plane • Remote configuration and management is available through a secure command-line interface (CLI) over Telnet and SSH; Role-Based Access Control (RBAC) provides multiple levels of access; Configuration Rollback and multiple configurations on the ...
... reachability, no matter what happens in the data plane • Remote configuration and management is available through a secure command-line interface (CLI) over Telnet and SSH; Role-Based Access Control (RBAC) provides multiple levels of access; Configuration Rollback and multiple configurations on the ...
MuON: Epidemic Based Mutual Anonymity
... Unlinkability of initiator and responder means that the initiator and responder cannot be identified as communicating with each other, even though they can be identified as participating in some communication. Different approaches have successfully achieved various forms of anonymity. In the simples ...
... Unlinkability of initiator and responder means that the initiator and responder cannot be identified as communicating with each other, even though they can be identified as participating in some communication. Different approaches have successfully achieved various forms of anonymity. In the simples ...