Chapter 9: Wavelength Routing Optical Networks
... • Optical channel (Och): An optical connection between two users that uses an entire lightpath. • Optical multiplex section (OMS): Optical channels are multiplexed and transmitted as a single signal over a fiber. The OMS is the section between a multiplexer and a demultiplexer that carries the comb ...
... • Optical channel (Och): An optical connection between two users that uses an entire lightpath. • Optical multiplex section (OMS): Optical channels are multiplexed and transmitted as a single signal over a fiber. The OMS is the section between a multiplexer and a demultiplexer that carries the comb ...
Distance Vector Routing Protocols
... Implementation and maintenance describes the level of knowledge that is required for a network administrator to implement and maintain the network based on the routing protocol deployed. © 2007 Cisco Systems, Inc. All rights reserved. ...
... Implementation and maintenance describes the level of knowledge that is required for a network administrator to implement and maintain the network based on the routing protocol deployed. © 2007 Cisco Systems, Inc. All rights reserved. ...
Tier-1 ISP
... bandwidth and distance Security – difficult to – taplimitsand Less interference loss Optimized forspread longer Light pulses outdistances Small size and weight Greater distance (up to 100 km) ...
... bandwidth and distance Security – difficult to – taplimitsand Less interference loss Optimized forspread longer Light pulses outdistances Small size and weight Greater distance (up to 100 km) ...
International Technical Support Organization High
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1992 1993 1995. All rights reserved. Note to U.S. Government ...
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1992 1993 1995. All rights reserved. Note to U.S. Government ...
ieee 2014 java .net titles be, b.tech, msc, mca projects institute cost
... Secure Routing Hop-by-Hop Message Authenticationand Source Privacy in WirelessSensor ...
... Secure Routing Hop-by-Hop Message Authenticationand Source Privacy in WirelessSensor ...
forscom extranet
... b. An Initial security training and awareness briefing for IA Managers and users. This briefing can consist of training material governing IA in general but must be tailored to the system the employee will be managing or using. The briefing will include the following: (1) Threats, vulnerabilities, a ...
... b. An Initial security training and awareness briefing for IA Managers and users. This briefing can consist of training material governing IA in general but must be tailored to the system the employee will be managing or using. The briefing will include the following: (1) Threats, vulnerabilities, a ...
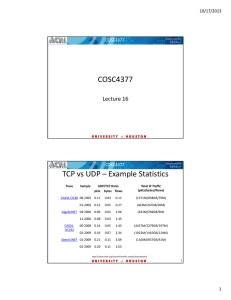
COSC4377 TCP vs UDP – Example Statistics
... growth ia coming from major ISPs within the U.S., as they roll out production IPv6 support to their end‐users, including Verizon Wireless, AT&T, and Comcast. This is on top of some ISPs in Europe and Asia that have had IPv6 deployed in production for a few years, as well as a long tail of thousan ...
... growth ia coming from major ISPs within the U.S., as they roll out production IPv6 support to their end‐users, including Verizon Wireless, AT&T, and Comcast. This is on top of some ISPs in Europe and Asia that have had IPv6 deployed in production for a few years, as well as a long tail of thousan ...
McAfee.com Virus Scan Online
... information possible about the trace and the servers and networks on that trace. This requires a great deal of interaction between Visual Trace and various servers on the Web. McAfee.com operates some of these servers, and some of these servers are operated by public or quasi-public entities. Server ...
... information possible about the trace and the servers and networks on that trace. This requires a great deal of interaction between Visual Trace and various servers on the Web. McAfee.com operates some of these servers, and some of these servers are operated by public or quasi-public entities. Server ...
PDF
... the least bandwidth. The next step will be adding mediatrace. Other plans under consideration include: ...
... the least bandwidth. The next step will be adding mediatrace. Other plans under consideration include: ...
PlanetSeer: Internet Path Failure Monitoring and Characterization in Wide-Area Services
... such as BGP [16], OSPF [15] and IS-IS [12] update messages to identify inter-domain and intra-domain routing failures. This approach usually requires collecting routing updates from multiple vantage points, which may not be easily accessible for normal end users. Other researchers have relied on som ...
... such as BGP [16], OSPF [15] and IS-IS [12] update messages to identify inter-domain and intra-domain routing failures. This approach usually requires collecting routing updates from multiple vantage points, which may not be easily accessible for normal end users. Other researchers have relied on som ...
Using Switches with a PS Series Group
... separate network switches, but with fewer physical switches and less management overhead. Because VLANs use logical rather than physical connections, they are flexible to operate. Note: PS Series storage arrays do not support VLAN tagging. Typically, VLANs are separate subnets in TCP/IP networks, so ...
... separate network switches, but with fewer physical switches and less management overhead. Because VLANs use logical rather than physical connections, they are flexible to operate. Note: PS Series storage arrays do not support VLAN tagging. Typically, VLANs are separate subnets in TCP/IP networks, so ...
The multimedia broadcast/multicast service
... for use with download services. The 3GPP has defined MBMS specific profiles for these protocols, as well as procedures for reception reporting and file repairs [6]. In order to support MBMS, a new functional entity, the Broadcast/Multicast Service Center (BM-SC) must be added to the PS domain of the ...
... for use with download services. The 3GPP has defined MBMS specific profiles for these protocols, as well as procedures for reception reporting and file repairs [6]. In order to support MBMS, a new functional entity, the Broadcast/Multicast Service Center (BM-SC) must be added to the PS domain of the ...
Lecture 5: Network Layer
... Design with QoS for each flow; handles multicast traffic. Admission with RSVP (Resource reSerVation Protocol): • Receiver sends a request back to the sender • Each router along the way reserves resources • Routers merge multiple requests for same flow • Entire path is set up, or reservation not made ...
... Design with QoS for each flow; handles multicast traffic. Admission with RSVP (Resource reSerVation Protocol): • Receiver sends a request back to the sender • Each router along the way reserves resources • Routers merge multiple requests for same flow • Entire path is set up, or reservation not made ...
Configuring RIP
... A node sends periodically a list of routing updates to its neighbors. If all nodes update their distances, the routing tables eventually converge New nodes advertise themselves to their neighbors ...
... A node sends periodically a list of routing updates to its neighbors. If all nodes update their distances, the routing tables eventually converge New nodes advertise themselves to their neighbors ...
29414-d10
... The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented. This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specific ...
... The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented. This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specific ...
Introduction to Computer Networks
... = speed of light ) A simple way to build an all optical-LAN is to use a passive star. To allow multiple transmissions at the same time, the spectrum is divided up into channels (wavelength bands) Each station is assigned two channels: one as a control channel to signal the station, and the other for ...
... = speed of light ) A simple way to build an all optical-LAN is to use a passive star. To allow multiple transmissions at the same time, the spectrum is divided up into channels (wavelength bands) Each station is assigned two channels: one as a control channel to signal the station, and the other for ...
Sample Title Slide Standard Template
... • Vista is the first time IPv6 is enabled by default in Windows • IPv6 has many implications for security that we have previously studied – (sorry, we haven't published on this as yet) ...
... • Vista is the first time IPv6 is enabled by default in Windows • IPv6 has many implications for security that we have previously studied – (sorry, we haven't published on this as yet) ...
Ch03
... switched WANs. A switched WAN is a wide area network that covers a large area (a state or a country) and provides access at several points to the users. Inside the network, there is a mesh of pointto-point networks that connects switches. The switches, multiple port connectors, allow the connection ...
... switched WANs. A switched WAN is a wide area network that covers a large area (a state or a country) and provides access at several points to the users. Inside the network, there is a mesh of pointto-point networks that connects switches. The switches, multiple port connectors, allow the connection ...
lim-previous-version
... What we did in 2008 – ‘Ripple effect & New strategy’ One of Korean major ISP enabled IPv6 on its backbone network for public sector. Local government asked IPv6 connectivity to ISP officially ISP made a quick decision to enable IPv6 because there is customer’s demand Even though IPv6 wasn’t enabl ...
... What we did in 2008 – ‘Ripple effect & New strategy’ One of Korean major ISP enabled IPv6 on its backbone network for public sector. Local government asked IPv6 connectivity to ISP officially ISP made a quick decision to enable IPv6 because there is customer’s demand Even though IPv6 wasn’t enabl ...
Forward-node-set-based broadcast in clustered mobile ad hoc
... neighbors, assuming all hosts have the same transmission range r. Two hosts are neighbors if and only if they are within each other’s transmission range. Therefore, the connections of hosts are based on geographic distances of hosts. The inherent limitations of the MANET, such as scarce resources an ...
... neighbors, assuming all hosts have the same transmission range r. Two hosts are neighbors if and only if they are within each other’s transmission range. Therefore, the connections of hosts are based on geographic distances of hosts. The inherent limitations of the MANET, such as scarce resources an ...
Msc Jian Li 2013 - Department of Electrical and Computer
... other application-specific devices to control and monitor the grid system. Figure 1.1 shows the conceptual diagram in smart grid communications. Currently, the constant improvements of smart grid technology have made a great progress on flexibility, security, reliability and efficiency of the electr ...
... other application-specific devices to control and monitor the grid system. Figure 1.1 shows the conceptual diagram in smart grid communications. Currently, the constant improvements of smart grid technology have made a great progress on flexibility, security, reliability and efficiency of the electr ...
Acceptable use Policy
... Wireless network or customers using the Service, regardless of whether this material or its dissemination is unlawful so long as it violates this Policy. Neither Cibola Wireless nor any of its affiliates, suppliers, employees or agents have any obligation to monitor transmissions or postings (includ ...
... Wireless network or customers using the Service, regardless of whether this material or its dissemination is unlawful so long as it violates this Policy. Neither Cibola Wireless nor any of its affiliates, suppliers, employees or agents have any obligation to monitor transmissions or postings (includ ...
Underlying Technologies
... switched WANs. A switched WAN is a wide area network that covers a large area (a state or a country) and provides access at several points to the users. Inside the network, there is a mesh of pointto-point networks that connects switches. The switches, multiple port connectors, allow the connection ...
... switched WANs. A switched WAN is a wide area network that covers a large area (a state or a country) and provides access at several points to the users. Inside the network, there is a mesh of pointto-point networks that connects switches. The switches, multiple port connectors, allow the connection ...
슬라이드 제목 없음
... The TCP/IP protocol suite is made of five layers: physical, data link, network, transport, and application. The first four layers provide physical standards, network interface, internetworking, and transport functions that correspond to the first four layers of the OSI model. The three topmost layer ...
... The TCP/IP protocol suite is made of five layers: physical, data link, network, transport, and application. The first four layers provide physical standards, network interface, internetworking, and transport functions that correspond to the first four layers of the OSI model. The three topmost layer ...
Chapter 17
... – Acknowledgement points are identified • ACKs are processed further down the tree ...
... – Acknowledgement points are identified • ACKs are processed further down the tree ...