(IP) routers
... • Network virtualization, such as ETSI network functions virtualization (NFV) , is a promising technology for next generation networks. • resource portability of Internet protocol (IP) routers (e.g., routing state, traffic state, configurations) is expected to result in a sustainable network that ha ...
... • Network virtualization, such as ETSI network functions virtualization (NFV) , is a promising technology for next generation networks. • resource portability of Internet protocol (IP) routers (e.g., routing state, traffic state, configurations) is expected to result in a sustainable network that ha ...
Maintenance ST - Common Criteria
... Asynchronous Transfer Mode (ATM) is a standardized digital data Asynchronous Transfer transmission technology. ATM is a cell-based switching technique Mode that uses asynchronous time division multiplexing. Border Gateway Protocol The Border Gateway Protocol (BGP) is the core routing protocol of the ...
... Asynchronous Transfer Mode (ATM) is a standardized digital data Asynchronous Transfer transmission technology. ATM is a cell-based switching technique Mode that uses asynchronous time division multiplexing. Border Gateway Protocol The Border Gateway Protocol (BGP) is the core routing protocol of the ...
Mobile Ad-hoc Clouds
... landscape. The ease of access to a pool of devices is much more arbitrary and based purely on the needs of the user. This pool can act as a provider of an infrastructure for various services that can be processed with volunteer node participation, where the node in the vicinity is itself a service p ...
... landscape. The ease of access to a pool of devices is much more arbitrary and based purely on the needs of the user. This pool can act as a provider of an infrastructure for various services that can be processed with volunteer node participation, where the node in the vicinity is itself a service p ...
1 Introduction
... “in flight” (data that has been transmitted, but not yet acknowledged) at any time to fully utilize the available channel capacity. The delay is the round trip time (RTT) and the bandwidth is the capacity of the bottleneck link in the path. For links with a large BDP, such as in geostationary satell ...
... “in flight” (data that has been transmitted, but not yet acknowledged) at any time to fully utilize the available channel capacity. The delay is the round trip time (RTT) and the bandwidth is the capacity of the bottleneck link in the path. For links with a large BDP, such as in geostationary satell ...
Nokia IP1280
... module and Check Point SecureXL software. The optional Nokia ADP services modules are available with 12 ports of Gigabit Ethernet in 1000Base-T, as well as 12 ports of Gigabit Ethernet in 1000Base-X, with interchangeable small form-factor pluggable (SFP) modules for SX, LX, and copper interfaces as ...
... module and Check Point SecureXL software. The optional Nokia ADP services modules are available with 12 ports of Gigabit Ethernet in 1000Base-T, as well as 12 ports of Gigabit Ethernet in 1000Base-X, with interchangeable small form-factor pluggable (SFP) modules for SX, LX, and copper interfaces as ...
FCTC_Zamer_iscsi
... So how can an iSCSI adapter determine where a message begins and ends?? By reading the length field in the iSCSI header Determines where in byte stream current message ends and next begins NIC must stay “in sync” with beginning of byte stream Works well in a perfect world (Maybe a SAN or LAN ...
... So how can an iSCSI adapter determine where a message begins and ends?? By reading the length field in the iSCSI header Determines where in byte stream current message ends and next begins NIC must stay “in sync” with beginning of byte stream Works well in a perfect world (Maybe a SAN or LAN ...
Scaling Up Clustered Network Appliances with
... to pin flows to a specific handling node combined with the requirement of maintaining as little states at each node as possible (which makes keeping a full per-flow forwarding table at each node a less viable option). ScaleBricks achieves these goals without increasing the inter-cluster latency. Com ...
... to pin flows to a specific handling node combined with the requirement of maintaining as little states at each node as possible (which makes keeping a full per-flow forwarding table at each node a less viable option). ScaleBricks achieves these goals without increasing the inter-cluster latency. Com ...
12.[2014-286](제정). - TTA표준화 위원회
... but which is not absolutely required. Thus this requirement need not be present to claim conformance. ...
... but which is not absolutely required. Thus this requirement need not be present to claim conformance. ...
IP Multicast
... •IP multicast packet is encapsulated in an Ethernet broadcast frame and transmitted on the bus. •Every host picks up the Ethernet frame and does filtering at the IP layer to decide whether to keep or discard the frame. 2. Link-layer (Ethernet) multicast •Requires a mapping of IP multicast address to ...
... •IP multicast packet is encapsulated in an Ethernet broadcast frame and transmitted on the bus. •Every host picks up the Ethernet frame and does filtering at the IP layer to decide whether to keep or discard the frame. 2. Link-layer (Ethernet) multicast •Requires a mapping of IP multicast address to ...
Machine-to-Machine (M2M) Gateway: Trusted and Connected
... machines than people and Machine-to-Machine (M2M) technology will help us to be more energy and cost-efficient, safer and more secure. This is the era of connected intelligence. The number of mobile connections is forecast by the GSM association to grow to 50 billion by the end of the decade. There ...
... machines than people and Machine-to-Machine (M2M) technology will help us to be more energy and cost-efficient, safer and more secure. This is the era of connected intelligence. The number of mobile connections is forecast by the GSM association to grow to 50 billion by the end of the decade. There ...
ch4
... • the station that chooses the smallest delay will proceed to send a packet and the network will return to normal operation • In the case where two or more computers happen to choose nearly the same amount of delay • they will both begin to transmit at nearly the same time • producing a second colli ...
... • the station that chooses the smallest delay will proceed to send a packet and the network will return to normal operation • In the case where two or more computers happen to choose nearly the same amount of delay • they will both begin to transmit at nearly the same time • producing a second colli ...
Product Overview (PDF)
... tem.Using a Patton Model 3086/RIK, telephony services can be transported to a local PBX over standard T1/E1 WAN connections. As the E1/T1 is transparently interconnected to the PBX through the 3086, any signaling protocol can be used, including ...
... tem.Using a Patton Model 3086/RIK, telephony services can be transported to a local PBX over standard T1/E1 WAN connections. As the E1/T1 is transparently interconnected to the PBX through the 3086, any signaling protocol can be used, including ...
VoIPTutorial FCC 2011-05 - Computer Science, Columbia
... • TCP/IP (Transmission Control Protocol / Internet Protocol) – The protocol suite that the Internet uses – Private IP networks can use TCP/IP without being part of Internet. ...
... • TCP/IP (Transmission Control Protocol / Internet Protocol) – The protocol suite that the Internet uses – Private IP networks can use TCP/IP without being part of Internet. ...
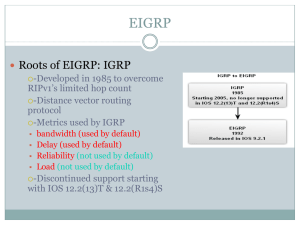
EIGRP
... maintains a list of backup routes it has already determined to be loop-free. If the primary route in the routing table fails, the best backup route is immediately added to the routing table. ...
... maintains a list of backup routes it has already determined to be loop-free. If the primary route in the routing table fails, the best backup route is immediately added to the routing table. ...
2. HBR Overview - Computer Science, Columbia University
... Figure 4: MIPv6 MIP is designed to work with IPv4. MIPv6 is the corresponding framework for IPv6. Since address autoconfiguration is a standard part of IPv6, the MH will always be able to obtain a COA routable to the foreign network. Furthermore, there are more than enough address in the IPv6 space ...
... Figure 4: MIPv6 MIP is designed to work with IPv4. MIPv6 is the corresponding framework for IPv6. Since address autoconfiguration is a standard part of IPv6, the MH will always be able to obtain a COA routable to the foreign network. Furthermore, there are more than enough address in the IPv6 space ...
TCP for Mobile and Wireless Hosts
... • Nodes for which all paths from S go through the destination D also do not receive packet P (example: node N) ...
... • Nodes for which all paths from S go through the destination D also do not receive packet P (example: node N) ...
AirLive WT-2000ARM Manual
... Step 3. Connect the Power Adapter to the Router Connect the power adapter to the power jack on the rear panel of router. Step4: Check the ADSL LED on the Router The ADSL LED will be ON if the router is connected to the ADSL cable and receives the ADSL signals successfully. If the LED is blinking, pl ...
... Step 3. Connect the Power Adapter to the Router Connect the power adapter to the power jack on the rear panel of router. Step4: Check the ADSL LED on the Router The ADSL LED will be ON if the router is connected to the ADSL cable and receives the ADSL signals successfully. If the LED is blinking, pl ...
show route
... •Creates a complete database of network •Calculates best path to each destination •Uses areas to incorporate hierarchy and allow for scalability ...
... •Creates a complete database of network •Calculates best path to each destination •Uses areas to incorporate hierarchy and allow for scalability ...
Network Training 2008-05-25
... The main difference between each of the category “levels” is the amount of “twists per inch” of the cable. Each pair within a cable has a different rate of twist, the blue from the orange, etc. Also important is how the pairs run inside the outer jacket in relationship with each other. This all impa ...
... The main difference between each of the category “levels” is the amount of “twists per inch” of the cable. Each pair within a cable has a different rate of twist, the blue from the orange, etc. Also important is how the pairs run inside the outer jacket in relationship with each other. This all impa ...
NAT - Hong Kong University of Science and Technology
... far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices ...
... far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices ...
Junos Pulse Access Control Service
... the standalone Juniper Networks IDP Series Intrusion Detection and Prevention Appliances, to deliver broad application traffic visibility—mitigating insider threats by isolating them to the user or device level, and employing an applicable policy action against an offending user or device. The Pulse ...
... the standalone Juniper Networks IDP Series Intrusion Detection and Prevention Appliances, to deliver broad application traffic visibility—mitigating insider threats by isolating them to the user or device level, and employing an applicable policy action against an offending user or device. The Pulse ...
Border Gateway Protocol (BGP4)
... • Represented as a numeric value (0-0xffffffff) • Used to convey the relative preference of entry points • Comparable if paths are from the same AS • Path with lower MED wins • IGP metric can be conveyed as MED ...
... • Represented as a numeric value (0-0xffffffff) • Used to convey the relative preference of entry points • Comparable if paths are from the same AS • Path with lower MED wins • IGP metric can be conveyed as MED ...
An Experimenter`s Guide to OpenFlow
... Load-Balancing Web Traffic using OpenFlow Goal: Load-balancing requests in unstructured networks What we are showing OpenFlow-based distributed load-balancer Smart load-balancing based on network and server load Allows incremental deployment of additional resources ...
... Load-Balancing Web Traffic using OpenFlow Goal: Load-balancing requests in unstructured networks What we are showing OpenFlow-based distributed load-balancer Smart load-balancing based on network and server load Allows incremental deployment of additional resources ...







. - TTA표준화 위원회](http://s1.studyres.com/store/data/004568034_1-cea0cb43984c16e12bdd271f5f03676e-300x300.png)