PPT - Communications
... entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this counter will include only those packets which were Source-Routed via this entity, and the SourceRoute optio ...
... entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this counter will include only those packets which were Source-Routed via this entity, and the SourceRoute optio ...
Research Journal of Applied Sciences, Engineering and Technology 3(12): 1374-1383,... ISSN: 2040-7467
... (MAN) technology. To meet different applications and performance demands, WiMAX specifies two classes of services, ie, fixed WiMAX and mobile WiMAX. The former is designed to deliver fixed wireless connection through backbone network and IP network, while the latter provides mobile connectivity serv ...
... (MAN) technology. To meet different applications and performance demands, WiMAX specifies two classes of services, ie, fixed WiMAX and mobile WiMAX. The former is designed to deliver fixed wireless connection through backbone network and IP network, while the latter provides mobile connectivity serv ...
IP Multicast
... • A sender simply sends data packets as they are available. • Each router uses the network topology, the group membership table, and the multicast group ID in the data packets to compute the route(s) to the destination(s). ...
... • A sender simply sends data packets as they are available. • Each router uses the network topology, the group membership table, and the multicast group ID in the data packets to compute the route(s) to the destination(s). ...
Campus LAN Reference Design
... Campus LAN Design The Campus LAN enables communication between devices in one or more buildings in close proximity. It also provides communication to devices not in the campus through interconnections to the Data Center, MAN/WAN, and Internet. Standard applications (web browsing and email), communi ...
... Campus LAN Design The Campus LAN enables communication between devices in one or more buildings in close proximity. It also provides communication to devices not in the campus through interconnections to the Data Center, MAN/WAN, and Internet. Standard applications (web browsing and email), communi ...
Explicit Congestion Notification (ECN) RFC 3168
... it gets a TCP-PDU with CWR set Any more IP-PDUs with CE set are treated as new instances of congestion in the network In delayed ACKs, ECE in ACK is set if CE is set for any of the IP-PDUs being acknowledged What does the receipt of CWR guarantee? ...
... it gets a TCP-PDU with CWR set Any more IP-PDUs with CE set are treated as new instances of congestion in the network In delayed ACKs, ECE in ACK is set if CE is set for any of the IP-PDUs being acknowledged What does the receipt of CWR guarantee? ...
No Slide Title
... • Request received: Routers that receive above request send their entire routing table in a response message • Response received: Update the routing table • Regular routing updates: Every 30 seconds, send all or part of the routing tables to every neighbor in an response message • Triggered Updates: ...
... • Request received: Routers that receive above request send their entire routing table in a response message • Response received: Update the routing table • Regular routing updates: Every 30 seconds, send all or part of the routing tables to every neighbor in an response message • Triggered Updates: ...
(CCNA) 5.CISCO Routing Protocols
... Characteristics of Distance Vector routing protocols – Periodic updates – RIP routing updates include the entire routing table – Neighbors are defined as routers that share a link and are configured to use the same protocol ...
... Characteristics of Distance Vector routing protocols – Periodic updates – RIP routing updates include the entire routing table – Neighbors are defined as routers that share a link and are configured to use the same protocol ...
Slide 1
... SHARKFEST '09 | Stanford University | June 15 –18, 2009 http://www.plixer.com/blog/general/plixer-and-cisco-ip-sla-jitter-part-1-of-4/ ...
... SHARKFEST '09 | Stanford University | June 15 –18, 2009 http://www.plixer.com/blog/general/plixer-and-cisco-ip-sla-jitter-part-1-of-4/ ...
Chapter 6: The Transport Layer
... The transport service Elements of transport protocols A simple transport protocol The Internet transport protocol: UDP The Internet transport protocol: TCP ...
... The transport service Elements of transport protocols A simple transport protocol The Internet transport protocol: UDP The Internet transport protocol: TCP ...
A New Service for Increasing the Effectiveness of Network Address Blacklists
... intrusion attempts against local network assets. For example, a local network may produce an LWOL to capture those addresses that are the most prolific producers of unwanted incoming packets, or that have been detected as significant attack sources from local IDS logs. LWOLs have the property of cap ...
... intrusion attempts against local network assets. For example, a local network may produce an LWOL to capture those addresses that are the most prolific producers of unwanted incoming packets, or that have been detected as significant attack sources from local IDS logs. LWOLs have the property of cap ...
module10-rip
... • Request received: Routers that receive above request send their entire routing table • Response received: Update the routing table • Regular routing updates: Every 30 seconds, send all or part of the routing tables to every neighbor in an response message • Triggered Updates: Whenever the metric f ...
... • Request received: Routers that receive above request send their entire routing table • Response received: Update the routing table • Regular routing updates: Every 30 seconds, send all or part of the routing tables to every neighbor in an response message • Triggered Updates: Whenever the metric f ...
C-Linking - Elsevier Store
... Hardware Disable, allowing other software to disable hardware on-the-fly. Hardware Enable, allowing other software to enable hardware on-the-fly. Hardware Acquire, allowing other software gain singular (locking) access to hardware. Hardware Release, allowing other software to free (unlock) hardware. ...
... Hardware Disable, allowing other software to disable hardware on-the-fly. Hardware Enable, allowing other software to enable hardware on-the-fly. Hardware Acquire, allowing other software gain singular (locking) access to hardware. Hardware Release, allowing other software to free (unlock) hardware. ...
slides - Inria
... Customer does not export from one provider to another Univ is customer of Medium1 traffic to/from Medium2 is a customer Univ of Big and Large Big ...
... Customer does not export from one provider to another Univ is customer of Medium1 traffic to/from Medium2 is a customer Univ of Big and Large Big ...
Link Layer
... r broadcast (shared wire or medium) m traditional Ethernet m upstream HFC m 802.11 wireless LAN ...
... r broadcast (shared wire or medium) m traditional Ethernet m upstream HFC m 802.11 wireless LAN ...
MPLS Transport Profile (MPLS-TP) - Center for Integrated Access
... plane may have applicability in scenarios where some equipment, especially equipment used at the edges of the network, does not support a dynamic control plane, or in which static configuration is preferred for security reasons. The NMS-driven control plane also allows operators to manage the packet ...
... plane may have applicability in scenarios where some equipment, especially equipment used at the edges of the network, does not support a dynamic control plane, or in which static configuration is preferred for security reasons. The NMS-driven control plane also allows operators to manage the packet ...
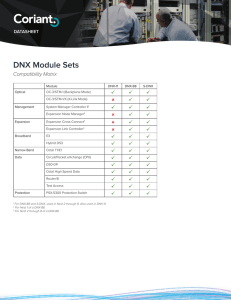
DNX Module Sets
... of a reference clock failure, the DNX automatically selects an alternate input based on the source clock configuration setting. Any of the following optional channel cards can provide port timing: Octal T1/E1, Octal High Speed, HDS3 and OC-3/STM-1. When the internal timing source is used to deliver ...
... of a reference clock failure, the DNX automatically selects an alternate input based on the source clock configuration setting. Any of the following optional channel cards can provide port timing: Octal T1/E1, Octal High Speed, HDS3 and OC-3/STM-1. When the internal timing source is used to deliver ...
Asynchronous Transfer Mode (ATM)
... • GFC---4 bits of generic flow control that are used to provide local functions, such as identifying multiple stations that share a single ATM interface. The GFC field is typically not used and is set to a default value. • VPI---8 bits of virtual path identifier that is used, in conjunction with the ...
... • GFC---4 bits of generic flow control that are used to provide local functions, such as identifying multiple stations that share a single ATM interface. The GFC field is typically not used and is set to a default value. • VPI---8 bits of virtual path identifier that is used, in conjunction with the ...
Era of Spybots - A Secure Design Solution Using
... Tipping Point IPS Secure Design ................................................................ 17 Figure 2: GIACE Network Design............................................................... 19 Figure 3: GIACE Network Design - Detailed ....................................... 20 GIACE Infrastructu ...
... Tipping Point IPS Secure Design ................................................................ 17 Figure 2: GIACE Network Design............................................................... 19 Figure 3: GIACE Network Design - Detailed ....................................... 20 GIACE Infrastructu ...
IPv6 - LINK@KoreaTech
... Each customer can have only some “limited” numbers of sessions simultaneously. ...
... Each customer can have only some “limited” numbers of sessions simultaneously. ...
Link Layer
... multiple access protocol distributed algorithm that determines how nodes share channel, i.e., determine when node can transmit communication about channel sharing must use channel itself! • no out-of-band channel for coordination ...
... multiple access protocol distributed algorithm that determines how nodes share channel, i.e., determine when node can transmit communication about channel sharing must use channel itself! • no out-of-band channel for coordination ...
Introduction Module 1:
... at MIT in 1957.(Answer: John McCarthy). Q15: ARPA’s networking project Managed by ______________ from MIT. (Answer: Lawrence Robert). Q16: Nodes with large time-sharing computers at the connected sites are called _____________. (Answer: hosts). Q17: What’s the different between Circuit-switching vs. ...
... at MIT in 1957.(Answer: John McCarthy). Q15: ARPA’s networking project Managed by ______________ from MIT. (Answer: Lawrence Robert). Q16: Nodes with large time-sharing computers at the connected sites are called _____________. (Answer: hosts). Q17: What’s the different between Circuit-switching vs. ...
Network Probe User Guide
... The Home Edition (free) of Network Probe supports single-computer mode only, so only traffic going from/to the computer where Network Probe is installed will be picked up. It can be connected to a normal port on the switch. For full utilization of Network Probe, a license key is required, which will ...
... The Home Edition (free) of Network Probe supports single-computer mode only, so only traffic going from/to the computer where Network Probe is installed will be picked up. It can be connected to a normal port on the switch. For full utilization of Network Probe, a license key is required, which will ...
UNI - MEF
... Frame Delay Variation is therefore the variation in this delay for a number of frames. This delay is an important factor in the transmission of unbuffered video and where variation occurs in the millisecond range can affect voice quality. For data can cause a number of undesirable effects such as pe ...
... Frame Delay Variation is therefore the variation in this delay for a number of frames. This delay is an important factor in the transmission of unbuffered video and where variation occurs in the millisecond range can affect voice quality. For data can cause a number of undesirable effects such as pe ...