RFC 2547bis: BGP/MPLS VPN Fundamentals
... Provider Edge Routers PE routers exchange routing information with CE routers using static routing, RIPv2, OSPF, or EBGP. While a PE router maintains VPN routing information, it is only required to maintain VPN routes for those VPNs to which it is directly attached. This design enhances the scalabil ...
... Provider Edge Routers PE routers exchange routing information with CE routers using static routing, RIPv2, OSPF, or EBGP. While a PE router maintains VPN routing information, it is only required to maintain VPN routes for those VPNs to which it is directly attached. This design enhances the scalabil ...
Secure Efficient Distance Vector Routing for Mobile Wireless Ad Hoc
... widely used in IP networks of moderate size. Distance vector routing can be used for routing within an ad hoc network by having each node in the network act as a router and participate in the routing protocol. In distance vector routing, each router maintains a routing table listing all possible des ...
... widely used in IP networks of moderate size. Distance vector routing can be used for routing within an ad hoc network by having each node in the network act as a router and participate in the routing protocol. In distance vector routing, each router maintains a routing table listing all possible des ...
Safety
... A vehicle reports road congestion to vehicles or road-site units in other regions for the purposes of route and trip planning Vehicles aggregate traffic probe information and transmit to road side units for traffic management Vehicle toll collection at highway toll booths (non-stop) A vehicle receiv ...
... A vehicle reports road congestion to vehicles or road-site units in other regions for the purposes of route and trip planning Vehicles aggregate traffic probe information and transmit to road side units for traffic management Vehicle toll collection at highway toll booths (non-stop) A vehicle receiv ...
PicOS Overview WHITEPAPER
... 1) The higher-level (also known as user level) subsystem consists of the routing protocols themselves, along with routing information bases and support processes. These routing daemons are updating the kernel routing table using a standard netlink interface. 2) A vASIC daemon is monitoring the kerne ...
... 1) The higher-level (also known as user level) subsystem consists of the routing protocols themselves, along with routing information bases and support processes. These routing daemons are updating the kernel routing table using a standard netlink interface. 2) A vASIC daemon is monitoring the kerne ...
GlobeSurfer® II 1.8 - 7.2 - 7.2 S
... The GlobeSurfer ® II management console allows you to control various GlobeSurfer ® II system parameters. The interface is accessed through a web browser: 1. Start a web browser on your PC. 2. Enter the address 192.168.1.1 to display the GlobeSurfer ® II management console. When first logging on to t ...
... The GlobeSurfer ® II management console allows you to control various GlobeSurfer ® II system parameters. The interface is accessed through a web browser: 1. Start a web browser on your PC. 2. Enter the address 192.168.1.1 to display the GlobeSurfer ® II management console. When first logging on to t ...
Market Guide for Enterprise SBC
... Routing — Session control for routing a call over different carriers or networks is based on cost, day, region, quality (QoS), username, IP address, IP network, codec type, domain name or other variables. For example, if the SBC is detecting errors on some calls going over one network, the SBC can t ...
... Routing — Session control for routing a call over different carriers or networks is based on cost, day, region, quality (QoS), username, IP address, IP network, codec type, domain name or other variables. For example, if the SBC is detecting errors on some calls going over one network, the SBC can t ...
OSPF
... Note: In the context of BGP, a gateway is nothing else but an IP router that connects autonomous systems. Interdomain routing protocol for routing between autonomous systems Uses TCP to send routing messages BGP is neither a link state, nor a distance vector protocol. Routing messages in BGP contain ...
... Note: In the context of BGP, a gateway is nothing else but an IP router that connects autonomous systems. Interdomain routing protocol for routing between autonomous systems Uses TCP to send routing messages BGP is neither a link state, nor a distance vector protocol. Routing messages in BGP contain ...
Avaya Data Ports List for Products
... device to the correct upper layer application. These ports are logical descriptors (numbers) that help devices multiplex and demultiplex information streams. Consider your desktop PC. Multiple applications may be simultaneously receiving information. In this example, email may use destination TCP po ...
... device to the correct upper layer application. These ports are logical descriptors (numbers) that help devices multiplex and demultiplex information streams. Consider your desktop PC. Multiple applications may be simultaneously receiving information. In this example, email may use destination TCP po ...
Congestion Control Without a Startup Phase
... 5 This is the worst-case in that it assumes that when data transmission starts all the data that will be transferred is available to be sent. ...
... 5 This is the worst-case in that it assumes that when data transmission starts all the data that will be transferred is available to be sent. ...
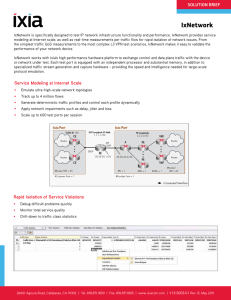
IxNetwork
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
WWW.BSSVE.IN
... Both users and administrators will be aware, to varying extents, of the trust and scope characteristics of a network. Again using TCP/IP architectural terminology, an intranet is a community of interest under private administration usually by an enterprise, and is only accessible by authorized users ...
... Both users and administrators will be aware, to varying extents, of the trust and scope characteristics of a network. Again using TCP/IP architectural terminology, an intranet is a community of interest under private administration usually by an enterprise, and is only accessible by authorized users ...
Coding and Error Control
... automation, energy savings, farming, environmental monitoring, security, surveillance, education, and many others. ...
... automation, energy savings, farming, environmental monitoring, security, surveillance, education, and many others. ...
7050SX Data Sheet
... The Arista 7050X runs the same Arista EOS software as all Arista products, simplifying network administration. Arista EOS is a modular switch operating system with a unique state sharing architecture that cleanly separates switch state from protocol processing and application logic. Built on top of ...
... The Arista 7050X runs the same Arista EOS software as all Arista products, simplifying network administration. Arista EOS is a modular switch operating system with a unique state sharing architecture that cleanly separates switch state from protocol processing and application logic. Built on top of ...
LoRa® ® FAQs
... other industries the definition of gateway and concentrator imply different components. 6.) How well does LoRa® handle Interference? The LoRa modem is capable of co‐channel GMSK rejection of up to 19.5 dB, or stated differently, it can receive signals 19.5dB below an interfering signal or the ...
... other industries the definition of gateway and concentrator imply different components. 6.) How well does LoRa® handle Interference? The LoRa modem is capable of co‐channel GMSK rejection of up to 19.5 dB, or stated differently, it can receive signals 19.5dB below an interfering signal or the ...
Chapter 6 - Network Layer
... Itself - This is a special IP address of 127.0.0.1 which is referred to as the loopback interface. Local host - This is a host on the same network as the sending host. The hosts share the same network address. Remote host - This is a host on a remote network. The hosts do not share the same network ...
... Itself - This is a special IP address of 127.0.0.1 which is referred to as the loopback interface. Local host - This is a host on the same network as the sending host. The hosts share the same network address. Remote host - This is a host on a remote network. The hosts do not share the same network ...
Chapter 7
... Protocol (DHCP). What information does DHCP automatically assign to local hosts? a. b. c. 23. DHCP is generally the preferred method of assigning IPv4 addresses to hosts on large networks. ...
... Protocol (DHCP). What information does DHCP automatically assign to local hosts? a. b. c. 23. DHCP is generally the preferred method of assigning IPv4 addresses to hosts on large networks. ...
Network Infrastructure for EtherNet/IP
... Note from the Publisher The application of Ethernet and Internet technologies is permeating every aspect of manufacturing automation today—control, safety, configuration and diagnostics, synchronization and motion, and information. To realize the benefits of these technologies, the network infrastru ...
... Note from the Publisher The application of Ethernet and Internet technologies is permeating every aspect of manufacturing automation today—control, safety, configuration and diagnostics, synchronization and motion, and information. To realize the benefits of these technologies, the network infrastru ...
TIE Breaking: Tunable Interdomain Egress Selection
... to be consistent with the other routers along the forwarding path, because packets are forwarded to neighboring routers that have selected a BGP route with the same (closest) egress point. Although consistent forwarding is clearly an important property for any routing system, routers now have other ...
... to be consistent with the other routers along the forwarding path, because packets are forwarded to neighboring routers that have selected a BGP route with the same (closest) egress point. Although consistent forwarding is clearly an important property for any routing system, routers now have other ...
Fundamentals of Embedded Software Development Technology
... Usually vendors of ZigBee devices use system-on-chip (SoC) solutions with integrated radio and 60-250KB of flash memory. ...
... Usually vendors of ZigBee devices use system-on-chip (SoC) solutions with integrated radio and 60-250KB of flash memory. ...
Accurate Real-time Identification of IP Prefix
... the semantics, design, and application of origin authentication services by formalizing address delegation semantics and exploring the use of various cryptographic structures for asserting block ownership and delegation. Compared to these related work, our approach focuses on practical, readily depl ...
... the semantics, design, and application of origin authentication services by formalizing address delegation semantics and exploring the use of various cryptographic structures for asserting block ownership and delegation. Compared to these related work, our approach focuses on practical, readily depl ...
cisco 7500 series router
... propagation delays, or where there might be many high-bandwidth media vying for access to a smaller number of slower media. • Offload processing—By operating a subset of the Cisco IOS Software, a VIP in a Cisco 7500 can offload some of the interface-specific functions that run in the central process ...
... propagation delays, or where there might be many high-bandwidth media vying for access to a smaller number of slower media. • Offload processing—By operating a subset of the Cisco IOS Software, a VIP in a Cisco 7500 can offload some of the interface-specific functions that run in the central process ...
Carrier Ethernet: The next generation network and service
... SDH ADMs / Transport replaced by Ethernet Transport Shortest possible Ethernet over E1 (PDH) loops CLE at customer premise enables converged Ethernet and IP services Local switching of locally attached subscribers reduces backhaul bandwidth © Copyright 2008 Turin Networks, Inc. All Rights Reserved ...
... SDH ADMs / Transport replaced by Ethernet Transport Shortest possible Ethernet over E1 (PDH) loops CLE at customer premise enables converged Ethernet and IP services Local switching of locally attached subscribers reduces backhaul bandwidth © Copyright 2008 Turin Networks, Inc. All Rights Reserved ...
route
... routing table in an area Link state routing: a process by which each router shares its knowledge about its neighbor with every router in the area ...
... routing table in an area Link state routing: a process by which each router shares its knowledge about its neighbor with every router in the area ...
The Transport Layer: Tutorial and Survey
... Token Ring, X.25, ATM, PPP, SONET, just to name a few. However, a programmer writing a Web client or server does not want to be concerned with the details of how communication takes place between client and server. The programmer simply wants to send and receive messages in a way that does not chang ...
... Token Ring, X.25, ATM, PPP, SONET, just to name a few. However, a programmer writing a Web client or server does not want to be concerned with the details of how communication takes place between client and server. The programmer simply wants to send and receive messages in a way that does not chang ...
ppt
... Provides some level of security, but with a great deal of cost If security is the only goal, avoid NAT NAT has been required for sites with IP address allocation problems RSIP may get NAT users back on track Spring 2000 ...
... Provides some level of security, but with a great deal of cost If security is the only goal, avoid NAT NAT has been required for sites with IP address allocation problems RSIP may get NAT users back on track Spring 2000 ...