McAfee Database Security Solution Brief
... Secure Databases from the Inside-Out with McAfee Database Security McAfee Database Security offers real-time protection for business-critical databases from all types of threats: external, internal, and even intra-database exploits. This software-based solution provides robust security and continuou ...
... Secure Databases from the Inside-Out with McAfee Database Security McAfee Database Security offers real-time protection for business-critical databases from all types of threats: external, internal, and even intra-database exploits. This software-based solution provides robust security and continuou ...
PCI Self-Assessment Questionnaire
... PCI Data Security Standard. Visa Asia Pacific, however, makes no warranty or claim that completion or compliance with the questionnaire will prevent security breaches or losses, and disclaims any responsibility or liability for any security breaches or losses incurred, whether the recommendation of ...
... PCI Data Security Standard. Visa Asia Pacific, however, makes no warranty or claim that completion or compliance with the questionnaire will prevent security breaches or losses, and disclaims any responsibility or liability for any security breaches or losses incurred, whether the recommendation of ...
Vulnerability Management: Tools, Challenges and Best Practices
... CSIRT. This poses a problem to the CSIRT’s efforts because they should be the ones to make and communicate the strategy for the organization as a whole. These tasks must be handled efficiently to ensure the appropriate response times and actions from systems administrators, security teams, and the g ...
... CSIRT. This poses a problem to the CSIRT’s efforts because they should be the ones to make and communicate the strategy for the organization as a whole. These tasks must be handled efficiently to ensure the appropriate response times and actions from systems administrators, security teams, and the g ...
IT2042-UNIT3-Notes
... Serial Number: For hardware devices, the serial number can uniquely identify a specific device. Manufacturer Name: Record the manufacturer of the device or software component. This can be useful when responding to incidents that involve these devices or when certain manufacturers announce specific v ...
... Serial Number: For hardware devices, the serial number can uniquely identify a specific device. Manufacturer Name: Record the manufacturer of the device or software component. This can be useful when responding to incidents that involve these devices or when certain manufacturers announce specific v ...
Chapter 7
... • Secure system should be simple enough for those on the inside to understand and use • Challenge is to make the system simple from the inside but complex from the outside – Will reap a large benefit in information security ...
... • Secure system should be simple enough for those on the inside to understand and use • Challenge is to make the system simple from the inside but complex from the outside – Will reap a large benefit in information security ...
Firewalls: An Effective Solution for Internet Security
... administering security on a network and for logging incoming and outgoing traffic to allow for accountability of user actions and for triggering incident response activity if unauthorized activity occurs. Firewalls are typically placed at gateways to networks to create a security perimeter, as shown ...
... administering security on a network and for logging incoming and outgoing traffic to allow for accountability of user actions and for triggering incident response activity if unauthorized activity occurs. Firewalls are typically placed at gateways to networks to create a security perimeter, as shown ...
Slide 1
... ARO MURI: Computer-aided Human-Centric Cyber Situation Awareness: SKRM Inspired Cyber SA Analytics ...
... ARO MURI: Computer-aided Human-Centric Cyber Situation Awareness: SKRM Inspired Cyber SA Analytics ...
The Importance of Computer Network Incident Reporting
... (1) host or end user systems; (2) enclaves and the enclave boundary; typically a local area network (LAN); (3) networks that link the enclaves, typically wide area networks; and (4) supporting infrastructures, which are typically the cryptographic solutions like public key infrastructure (PKI) (Join ...
... (1) host or end user systems; (2) enclaves and the enclave boundary; typically a local area network (LAN); (3) networks that link the enclaves, typically wide area networks; and (4) supporting infrastructures, which are typically the cryptographic solutions like public key infrastructure (PKI) (Join ...
ch06
... distributing pirated software using an unsecured modem to access net impersonating a user to reset password ...
... distributing pirated software using an unsecured modem to access net impersonating a user to reset password ...
Speech Title Here
... DREAD potential D Damage What are the consequences of a successful exploit? R Reproducibility Would an exploit work every time or only under certain circumstances? E Exploitability How skilled must an attacker be to exploit the vulnerability? users A Affected How many users would be affected by a s ...
... DREAD potential D Damage What are the consequences of a successful exploit? R Reproducibility Would an exploit work every time or only under certain circumstances? E Exploitability How skilled must an attacker be to exploit the vulnerability? users A Affected How many users would be affected by a s ...
Practice Questions with Solutions
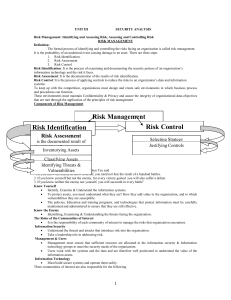
... 14. An organization recently completed a risk assessment. Based on the findings in the risk assessment, the organization chose to purchase insurance to cover possible losses. This approach is known as: a. Risk transfer b. Risk avoidance c. Risk acceptance d. Risk reduction 15. After completing a ri ...
... 14. An organization recently completed a risk assessment. Based on the findings in the risk assessment, the organization chose to purchase insurance to cover possible losses. This approach is known as: a. Risk transfer b. Risk avoidance c. Risk acceptance d. Risk reduction 15. After completing a ri ...
Governance Guidance - Top Actions
... corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise information security has been dealt with or relegated as a technology issue with little or ...
... corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise information security has been dealt with or relegated as a technology issue with little or ...
Governance Guidance
... corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise information security has been dealt with or relegated as a technology issue with little or ...
... corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise information security has been dealt with or relegated as a technology issue with little or ...
ch07 - Cisco Academy
... • Secure system should be simple enough for those on the inside to understand and use • Challenge is to make the system simple from the inside but complex from the outside – Will reap a large benefit in information security ...
... • Secure system should be simple enough for those on the inside to understand and use • Challenge is to make the system simple from the inside but complex from the outside – Will reap a large benefit in information security ...
Governance Guidance - Top Actions
... corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise information security has been dealt with or relegated as a technology issue with little or ...
... corresponding information systems is truly massive to enterprises. Securing that information and incorporating it into an overall corporate or enterprise governance approach are critical. Too often, enterprise information security has been dealt with or relegated as a technology issue with little or ...
Slides - School of Information Sciences
... 1. Actions of users/processes conform to statistically predictable patterns 2. Actions of users/processes do not include sequences of commands to subvert security policy 3. Actions of processes conform to specifications describing allowable actions ...
... 1. Actions of users/processes conform to statistically predictable patterns 2. Actions of users/processes do not include sequences of commands to subvert security policy 3. Actions of processes conform to specifications describing allowable actions ...
www.cs.hofstra.edu
... 1. Try default passwords used with standard accounts shipped with the system 2. Exhaustive try of all short passwords 3. Try words in system’s dictionary or list of likely passwords (hacker bulletin boards) 4. Collect information about users (full names, names of spouses and children, pictures and b ...
... 1. Try default passwords used with standard accounts shipped with the system 2. Exhaustive try of all short passwords 3. Try words in system’s dictionary or list of likely passwords (hacker bulletin boards) 4. Collect information about users (full names, names of spouses and children, pictures and b ...
MYDIGIPASS for Healthcare
... MYDIGIPASS for Healthcare is a comprehensive solution for healthcare organizations, EHR and eRx vendors that helps ensure EPCS compliance for prescribers and offers enhanced security for HIE, provider and patient portal access. From identity proofing and provisioning to secure login and fulfilment – ...
... MYDIGIPASS for Healthcare is a comprehensive solution for healthcare organizations, EHR and eRx vendors that helps ensure EPCS compliance for prescribers and offers enhanced security for HIE, provider and patient portal access. From identity proofing and provisioning to secure login and fulfilment – ...
Chapter 1. Introduction to Data Communications
... Preventing Unauthorized Access • A proactive approach that includes routinely testing your security systems is key to preventing unauthorized access. • Access related security issues include: ...
... Preventing Unauthorized Access • A proactive approach that includes routinely testing your security systems is key to preventing unauthorized access. • Access related security issues include: ...
MS Word template for internal docs
... Objective: To ensure that information receives an appropriate level of protection in accordance with its importance to the organization. Classification of information Control Information shall be classified in terms of its value, legal requirements, sensitivity or criticality to the organization L ...
... Objective: To ensure that information receives an appropriate level of protection in accordance with its importance to the organization. Classification of information Control Information shall be classified in terms of its value, legal requirements, sensitivity or criticality to the organization L ...
Security Services Gateways
... security real-time operating system, the Juniper Networks® Junos® operating system. Unlike general-purpose operating systems, the Junos operating system is not plagued by inefficiencies and vulnerabilities as it has been designed from the ground up to provide superior networking and security capabil ...
... security real-time operating system, the Juniper Networks® Junos® operating system. Unlike general-purpose operating systems, the Junos operating system is not plagued by inefficiencies and vulnerabilities as it has been designed from the ground up to provide superior networking and security capabil ...
Defense In Depth
... management or by referencing situations at the company like recent acquisitions or layoffs. These attacks are also successful because they play on a person’s desire to be helpful or even to keep one’s job. The only way to combat this type of attack is through education. Kevin Mitnick, who said he ha ...
... management or by referencing situations at the company like recent acquisitions or layoffs. These attacks are also successful because they play on a person’s desire to be helpful or even to keep one’s job. The only way to combat this type of attack is through education. Kevin Mitnick, who said he ha ...
updated system threat and requirements analysis for high assurance
... hacking [1] [2] [3]. “Blended” attacks against commercial wireless interfaces have been studied by standardization groups such as the 3rd Generation Partnership Program [4]. Five attack methods (unauthorized access to data, threats to integrity, denial of service, unauthorized access to services, an ...
... hacking [1] [2] [3]. “Blended” attacks against commercial wireless interfaces have been studied by standardization groups such as the 3rd Generation Partnership Program [4]. Five attack methods (unauthorized access to data, threats to integrity, denial of service, unauthorized access to services, an ...