security
... •Copyright 2017, Oracle &/or its affiliates. All rights reserved. Oracle & Java are registered trademarks of Oracle &/or its affiliates.Other names may be trademarks of their respective owners •SPEC and the benchmark name SPECjEnterprise are registered trademarks of the Standard Performance Evaluati ...
... •Copyright 2017, Oracle &/or its affiliates. All rights reserved. Oracle & Java are registered trademarks of Oracle &/or its affiliates.Other names may be trademarks of their respective owners •SPEC and the benchmark name SPECjEnterprise are registered trademarks of the Standard Performance Evaluati ...
here - HOET
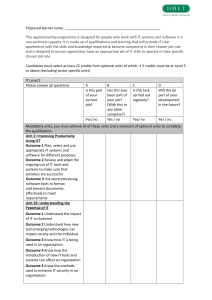
... Proposed learner name: _________________________________________________ This apprenticeship programme is designed for people who work with IT systems and software in a non-technical capacity. It is made up of qualifications and learning that will provide IT User apprentices with the skills and know ...
... Proposed learner name: _________________________________________________ This apprenticeship programme is designed for people who work with IT systems and software in a non-technical capacity. It is made up of qualifications and learning that will provide IT User apprentices with the skills and know ...
Information Technology (IT) Security Policy
... This policy is authorised by HSE Senior Management Team and represents the HSE’s national position. The policy takes precedence over all other relevant policies which may have been developed at a local level. This policy applies to all HSE staff, students, contractors, sub-contractors, agency staff ...
... This policy is authorised by HSE Senior Management Team and represents the HSE’s national position. The policy takes precedence over all other relevant policies which may have been developed at a local level. This policy applies to all HSE staff, students, contractors, sub-contractors, agency staff ...
ISO27001 and 27002
... Stage 3 is a follow-up reassessment audit to confirm that a previouslycertified organization remains in compliance with the standard. Certification maintenance involves periodic reviews and reassessments to confirm that the ISMS continues to operate as specified and intended. ...
... Stage 3 is a follow-up reassessment audit to confirm that a previouslycertified organization remains in compliance with the standard. Certification maintenance involves periodic reviews and reassessments to confirm that the ISMS continues to operate as specified and intended. ...
PP_ch23f
... • Can view errors that a user saw and forgot • Can get help with errors by clicking the Microsoft link ...
... • Can view errors that a user saw and forgot • Can get help with errors by clicking the Microsoft link ...
Umfang von PCI-Audits reduzieren mit Cisco TrustSec - Analyse und Bewertung von Verizon
... resulting rules are no longer simple to understand and may not clearly correlate with the original business goals. They also do not account for user, device, or server roles, leading to some complexity in how protected assets are classified, and are at risk of misconfiguration. Cisco TrustSec simpli ...
... resulting rules are no longer simple to understand and may not clearly correlate with the original business goals. They also do not account for user, device, or server roles, leading to some complexity in how protected assets are classified, and are at risk of misconfiguration. Cisco TrustSec simpli ...
white paper - Nuage Networks
... Last year over $US227 billion credit card transactions were used to purchase goods and services around the world. These transactions were processed using various payment systems and supporting technologies. Yet the threat of a breach or compromise continues to be a real concern for all banks and mer ...
... Last year over $US227 billion credit card transactions were used to purchase goods and services around the world. These transactions were processed using various payment systems and supporting technologies. Yet the threat of a breach or compromise continues to be a real concern for all banks and mer ...
Top Five DNS Security Attack Risks and How to Avoid Them
... That’s just four headlines reported by the press, but there are likely thousands of other DNS attacks that never reach the press because of their size or because the organization wants to keep the information private. The motives for hacking into an organization’s internal servers can be for financi ...
... That’s just four headlines reported by the press, but there are likely thousands of other DNS attacks that never reach the press because of their size or because the organization wants to keep the information private. The motives for hacking into an organization’s internal servers can be for financi ...
William Stallings, Cryptography and Network Security 5/e
... • Acts as a relay of application-level traffic • If the gateway does not implement the proxy code for a specific application, the service is not supported and cannot be forwarded across the firewall • The gateway can be configured to support only specific features of an application that the network ...
... • Acts as a relay of application-level traffic • If the gateway does not implement the proxy code for a specific application, the service is not supported and cannot be forwarded across the firewall • The gateway can be configured to support only specific features of an application that the network ...
chap1-slide - GEOCITIES.ws
... – Information (Information Security) • Secure computing resources against unauthorized users (attackers, outsider) as well as from natural disasters ...
... – Information (Information Security) • Secure computing resources against unauthorized users (attackers, outsider) as well as from natural disasters ...
CN 2015 5 - SNGCE DIGITAL LIBRARY
... Cryptographic techniques allow sender to mask data. Cryptographic techniques allow receiver to recover data from masked data. It is the study of Encryption and Decryption methods. Encryption—Plain text to cipher text Decryption—Cipher text to Plain text ...
... Cryptographic techniques allow sender to mask data. Cryptographic techniques allow receiver to recover data from masked data. It is the study of Encryption and Decryption methods. Encryption—Plain text to cipher text Decryption—Cipher text to Plain text ...
Application Security
... web server, database server, and platform. • All these settings should be defined, implemented, and maintained as many are not shipped with secure defaults. This includes keeping all software up to date, including all code libraries used by the application. ...
... web server, database server, and platform. • All these settings should be defined, implemented, and maintained as many are not shipped with secure defaults. This includes keeping all software up to date, including all code libraries used by the application. ...
How to Detect Zero-Day Malware And Limit Its Impact
... Pollutro, president and founder of cloud security vendor Taasera. While “there will always be a place for signatures,” security products have to begin identifying malware by what it’s doing rather than what it looks like, he says. Several things have to happen before the malware infection results in ...
... Pollutro, president and founder of cloud security vendor Taasera. While “there will always be a place for signatures,” security products have to begin identifying malware by what it’s doing rather than what it looks like, he says. Several things have to happen before the malware infection results in ...
Security - The University of Texas at Dallas
... •Security attacks cost U.S. corporations $266 million last year. That's more than double the average annual losses over the past three years. •Cyber-crimes being investigated by the FBI have more than doubled in the past year. • In 1999, the number soared to over 8,300 according to reports filed wit ...
... •Security attacks cost U.S. corporations $266 million last year. That's more than double the average annual losses over the past three years. •Cyber-crimes being investigated by the FBI have more than doubled in the past year. • In 1999, the number soared to over 8,300 according to reports filed wit ...
1 Notification of the Office of the Securities and Exchange
... unit responsible for the following functions by an independent auditor: (a) operation associated with the policy in Clause 5 (1) (2) and (3); (b) reporting on compliance in Clause 6 (4). (2) conduct control self-assessment to measure the effectiveness of the operating procedures; (3) engage an indep ...
... unit responsible for the following functions by an independent auditor: (a) operation associated with the policy in Clause 5 (1) (2) and (3); (b) reporting on compliance in Clause 6 (4). (2) conduct control self-assessment to measure the effectiveness of the operating procedures; (3) engage an indep ...
Linux+ Guide to Linux Certification
... • Can’t overemphasize the importance of keeping the system secure • System is only as good as the integrity of the data that’s stored on it • A single breach of security – whether catastrophic or not, whether accidental or not – damages the system’s integrity • Damaged integrity threatens the viabil ...
... • Can’t overemphasize the importance of keeping the system secure • System is only as good as the integrity of the data that’s stored on it • A single breach of security – whether catastrophic or not, whether accidental or not – damages the system’s integrity • Damaged integrity threatens the viabil ...
Lab1Overview - ECE Users Pages
... add new material give the exact wording and instructions you would give to future students in the new lab handout. You may cross out and edit the text of the lab on previous pages to make minor corrections/suggestions. General suggestions like add tool xyz to do more capable scanning will not be awa ...
... add new material give the exact wording and instructions you would give to future students in the new lab handout. You may cross out and edit the text of the lab on previous pages to make minor corrections/suggestions. General suggestions like add tool xyz to do more capable scanning will not be awa ...
OSI Defense in Depth to Increase Application Security
... protection methods are the responsibility of the programmer at this layer. Backdoor attacks occur at this level and it is the programmer’s responsibility to close those doors. IT managers can use access control methods described to assist in preventing backdoor attacks; also, IT managers can set up ...
... protection methods are the responsibility of the programmer at this layer. Backdoor attacks occur at this level and it is the programmer’s responsibility to close those doors. IT managers can use access control methods described to assist in preventing backdoor attacks; also, IT managers can set up ...
Lecture 8 - Faculty Web Pages
... controlled by a company, but concerning it, that can be beneficial or risky – Social Media Policy outlines guidelines or principles that should govern employee online communications about the company – Should include blog and personal blog policies – Cover employee social network and personal social ...
... controlled by a company, but concerning it, that can be beneficial or risky – Social Media Policy outlines guidelines or principles that should govern employee online communications about the company – Should include blog and personal blog policies – Cover employee social network and personal social ...
Cyber-Multi-Attribute Task Battery (C-MATB)
... An example of the PCap tab. Packets in this list are arranged in the serial order they arrive on the network. Each packet in this tab has seven data fields, corresponding to: 1) the number of the packet, which is determined by its serial position in the packet list; 2) the time the packet arrived on ...
... An example of the PCap tab. Packets in this list are arranged in the serial order they arrive on the network. Each packet in this tab has seven data fields, corresponding to: 1) the number of the packet, which is determined by its serial position in the packet list; 2) the time the packet arrived on ...
Security+ Guide to Network Security Fundamentals
... are and identify some major characteristics of intrusion detection products Detail the differences between host-based and network-based intrusion detection Identify active detection and passive detection features of both host- and network-based IDS products ...
... are and identify some major characteristics of intrusion detection products Detail the differences between host-based and network-based intrusion detection Identify active detection and passive detection features of both host- and network-based IDS products ...
Teaching Computer Security using Minix
... Learn IPSec protocol, understand how it is implemented Apply comprehensive knowledge: networking, encryption/decryption, key management, access control, authentication, and security in OS kernels ...
... Learn IPSec protocol, understand how it is implemented Apply comprehensive knowledge: networking, encryption/decryption, key management, access control, authentication, and security in OS kernels ...
1 | I.C.T.C. “International Computer Training Center” www.ictc.gr info
... This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems. Students then learn how intruders escalate privileges and what steps can be taken to secure a system. Who Should Attend This course will significantly be ...
... This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems. Students then learn how intruders escalate privileges and what steps can be taken to secure a system. Who Should Attend This course will significantly be ...