Information Security Incident Management
... • Operations in Montreal, Ottawa, Toronto and Bahamas working with 160 customers in 11 countries ...
... • Operations in Montreal, Ottawa, Toronto and Bahamas working with 160 customers in 11 countries ...
Important Concepts.
... Assurance that data received are exactly as sent by an authorized entity. (i.e., contain no modification, insertion, deletion, or replay). Data integrity can be maintained through the use of various error checking methods and validation procedures. Data integrity and data security are related te ...
... Assurance that data received are exactly as sent by an authorized entity. (i.e., contain no modification, insertion, deletion, or replay). Data integrity can be maintained through the use of various error checking methods and validation procedures. Data integrity and data security are related te ...
Lecture 12
... request be recorded Security event log records security-critical events such as logging in and out, system file accesses, and other events ...
... request be recorded Security event log records security-critical events such as logging in and out, system file accesses, and other events ...
Security
... network and others travel in – Those travelers are not all friendly! Critical and private information can be snooped — sniffed Information can be deleted or destroyed The Internet provides an opportunity for anonymous and rapid theft of lots of money ...
... network and others travel in – Those travelers are not all friendly! Critical and private information can be snooped — sniffed Information can be deleted or destroyed The Internet provides an opportunity for anonymous and rapid theft of lots of money ...
Principals of Information Security, Fourth Edition
... • Upon completion of this material, you should be able to: – Demonstrate that organizations have a business need for information security – Explain why a successful information security program is the responsibility of both an organization’s general management and IT management ...
... • Upon completion of this material, you should be able to: – Demonstrate that organizations have a business need for information security – Explain why a successful information security program is the responsibility of both an organization’s general management and IT management ...
Chapter 1
... See www.alw.nih.gov/Security/FIRST/papers/ legal/statelaw.txt for state computer laws Health Insurance Portability and Accountability Act of 1996, HIPAA ...
... See www.alw.nih.gov/Security/FIRST/papers/ legal/statelaw.txt for state computer laws Health Insurance Portability and Accountability Act of 1996, HIPAA ...
CISSP Guide to Security Essentials, Ch4
... will not be altered by high inputs and outputs • In other words, activities at a higher security level cannot be detected (and will not interfere with) at lower security levels – Prevents data leaking through "covert channels" – Link Ch 9d ...
... will not be altered by high inputs and outputs • In other words, activities at a higher security level cannot be detected (and will not interfere with) at lower security levels – Prevents data leaking through "covert channels" – Link Ch 9d ...
AISE PoIS4E_PP_ch02_48
... • Upon completion of this material, you should be able to: – Demonstrate that organizations have a business need for information security – Explain why a successful information security program is the responsibility of both an organization’s general management and IT management ...
... • Upon completion of this material, you should be able to: – Demonstrate that organizations have a business need for information security – Explain why a successful information security program is the responsibility of both an organization’s general management and IT management ...
Incident Handling Applied Risk Management September 2002
... • Authorizations – Ability to react in a timely fashion ...
... • Authorizations – Ability to react in a timely fashion ...
Green-Aware Security
... services can bring to a new type of attacks based upon multiple profile fusion. Also, such amount of information can ease the automatic and massive user profiling, thus reducing privacy; 4. accessing SNs from mobile devices, mostly performed via the IEEE 802.11, accounts for additional risks in term ...
... services can bring to a new type of attacks based upon multiple profile fusion. Also, such amount of information can ease the automatic and massive user profiling, thus reducing privacy; 4. accessing SNs from mobile devices, mostly performed via the IEEE 802.11, accounts for additional risks in term ...
Why we need IT security - Department of Computer Science and
... between communicating applications • TLS works by negotiating a unique encryption algorithm and cryptographic keys between a client and a server before data is exchanged. ...
... between communicating applications • TLS works by negotiating a unique encryption algorithm and cryptographic keys between a client and a server before data is exchanged. ...
Next Generation Security Operation Center for NCHC
... – No.4 of Most Botnet Activity in 2013 – No.5 of Top Attack Traffic Originating Countries in Top Attack Traffic Originating Countries ...
... – No.4 of Most Botnet Activity in 2013 – No.5 of Top Attack Traffic Originating Countries in Top Attack Traffic Originating Countries ...
Sentry System Health Monitoring Technical Requirements
... technical personnel may begin a remote root cause analysis and remediation action utilizing the communication channel initially established by the outbound alert. To perform these actions, the CSC personnel will generally employ the remote support platform by Bomgar and have access to all devices mo ...
... technical personnel may begin a remote root cause analysis and remediation action utilizing the communication channel initially established by the outbound alert. To perform these actions, the CSC personnel will generally employ the remote support platform by Bomgar and have access to all devices mo ...
Guidelines at a Glance - American Bankers Association
... A bank’s information security program must be designed to ensure the security and confidentiality of customer information, protect against any anticipated threats or hazards to the security or integrity of such information, and protect against unauthorized access to or use of such information that w ...
... A bank’s information security program must be designed to ensure the security and confidentiality of customer information, protect against any anticipated threats or hazards to the security or integrity of such information, and protect against unauthorized access to or use of such information that w ...
Introduction to Information Security
... Critical-infrastructure protection is the study, design and implementation of precautionary measures aimed to reduce the risk that critical infrastructure fails as the result of war, disaster, civil unrest, vandalism, or sabotage. ...
... Critical-infrastructure protection is the study, design and implementation of precautionary measures aimed to reduce the risk that critical infrastructure fails as the result of war, disaster, civil unrest, vandalism, or sabotage. ...
Objects - Information Systems
... Security classification may affect (hamper) the way in which real-world entities must be mapped into the underlying object schema. (e.g. only one authorization for whole complex objects) • Secure update and delete operations: Objects may reference objects with a different security level. E.g. if an ...
... Security classification may affect (hamper) the way in which real-world entities must be mapped into the underlying object schema. (e.g. only one authorization for whole complex objects) • Secure update and delete operations: Objects may reference objects with a different security level. E.g. if an ...
Raz-Lee Solution Brief
... The joint Intel Security-Raz-Lee solution for databases addresses these concerns via IBM i system and database sensor data, including SQL and traditional IBM i input/output (I/O) data. This information is passed to the McAfee® ePolicy Orchestrator® (McAfee ePO™) security management console via inter ...
... The joint Intel Security-Raz-Lee solution for databases addresses these concerns via IBM i system and database sensor data, including SQL and traditional IBM i input/output (I/O) data. This information is passed to the McAfee® ePolicy Orchestrator® (McAfee ePO™) security management console via inter ...
VPNs, PKIs, ISSs, SSLs with narration
... • A PKI automates most aspects of using public key encryption and authentication • Uses a PKI Server ...
... • A PKI automates most aspects of using public key encryption and authentication • Uses a PKI Server ...
Chapter 2
... Upon completion of this material, you should be able to: Recognize that organizations have a business need for information security Understand that a successful information security program is the responsibility of both an organization’s general management and IT management Identify the threat ...
... Upon completion of this material, you should be able to: Recognize that organizations have a business need for information security Understand that a successful information security program is the responsibility of both an organization’s general management and IT management Identify the threat ...
Chapter 2
... Upon completion of this material, you should be able to: Recognize that organizations have a business need for information security Understand that a successful information security program is the responsibility of both an organization’s general management and IT management Identify the threat ...
... Upon completion of this material, you should be able to: Recognize that organizations have a business need for information security Understand that a successful information security program is the responsibility of both an organization’s general management and IT management Identify the threat ...
Key To Personal Information Security
... (LAN) or Internet run many services that listen at well-known and not so well known ports • By port scanning, the attacker finds which ports are available (i.e., what service might be listing to a port) • A port scan consists of sending a message to each port, one at a time • The kind of response re ...
... (LAN) or Internet run many services that listen at well-known and not so well known ports • By port scanning, the attacker finds which ports are available (i.e., what service might be listing to a port) • A port scan consists of sending a message to each port, one at a time • The kind of response re ...
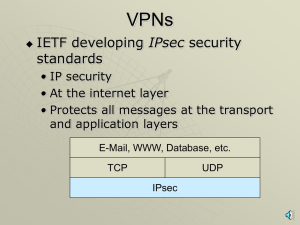
IPSec (IP Security)
... Determine SA details (over SPI) Consult the SA Database to validate/decipher the packet Once validated/deciphered the appropriate action for the packet is determined and it is forwarded according to the rules in the SPD ...
... Determine SA details (over SPI) Consult the SA Database to validate/decipher the packet Once validated/deciphered the appropriate action for the packet is determined and it is forwarded according to the rules in the SPD ...
Introduction to Information Security Chapter N
... Principles of Information Security - Chapter 2 ...
... Principles of Information Security - Chapter 2 ...
Study Material for MCA (SEM-V) Subject: Cyber Security and
... Today corporations like government often spy on the enemy. ...
... Today corporations like government often spy on the enemy. ...
computer security - GH Raisoni Polytechnic, Nagpur
... only those individuals who have the Authority can view a piece of information. 2. Authentication: Authentication deals with the desire to ensure that an individual is who they claim to be. The need for this in an online transaction is obvious. 3. Integrity: Integrity is a related concept but deals w ...
... only those individuals who have the Authority can view a piece of information. 2. Authentication: Authentication deals with the desire to ensure that an individual is who they claim to be. The need for this in an online transaction is obvious. 3. Integrity: Integrity is a related concept but deals w ...