Mainline How Secure Are You K12 Security Preseo Rev 1
... requires schools and libraries using E-Rate discounts to operate "a technology protection measure with respect to any of its computers with Internet access that protects against access through such computers to visual depictions that are obscene, child pornography, or harmful to minors..." Such a te ...
... requires schools and libraries using E-Rate discounts to operate "a technology protection measure with respect to any of its computers with Internet access that protects against access through such computers to visual depictions that are obscene, child pornography, or harmful to minors..." Such a te ...
ch02
... Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network Social engineering: using social skills to convince people to reveal access credentials or other valuable information to attacker ...
... Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network Social engineering: using social skills to convince people to reveal access credentials or other valuable information to attacker ...
spear-phishing attacks
... Some of the most notorious cyber crimes in recent history — such as the attacks on major banks, media companies and even security firms — started with just one person clicking on a spear-phishing email. Spear phishing is on the rise because it works. Traditional security defenses simply do not detec ...
... Some of the most notorious cyber crimes in recent history — such as the attacks on major banks, media companies and even security firms — started with just one person clicking on a spear-phishing email. Spear phishing is on the rise because it works. Traditional security defenses simply do not detec ...
procedure name - Siskiyou Central Credit Union
... or disparages an individual, Credit Union, or business. o They may not be used to conduct personal business. Solicitations, offers to buy and sell goods or services, and other personal messages to groups are not an appropriate use of these systems. o You must not make any copies of the Credit Union’ ...
... or disparages an individual, Credit Union, or business. o They may not be used to conduct personal business. Solicitations, offers to buy and sell goods or services, and other personal messages to groups are not an appropriate use of these systems. o You must not make any copies of the Credit Union’ ...
Cyber insurance market set to reach $7.5 billion in annual
... “Many insurers and reinsurers are looking to take advantage of what they see as a rare opportunity to secure high margins in an otherwise soft market,” Mr Britten said. “Yet many others may still be wary of cyber risk due to limited historic data and the challenges in evaluating and pricing the risk ...
... “Many insurers and reinsurers are looking to take advantage of what they see as a rare opportunity to secure high margins in an otherwise soft market,” Mr Britten said. “Yet many others may still be wary of cyber risk due to limited historic data and the challenges in evaluating and pricing the risk ...
Rocket® Blue Zone Security Server
... access to host systems, increasing data stream privacy, and strengthening authentication. Rocket® BlueZone Security Server secures confidential information, authenticates users and reinforces network and perimeter security. ...
... access to host systems, increasing data stream privacy, and strengthening authentication. Rocket® BlueZone Security Server secures confidential information, authenticates users and reinforces network and perimeter security. ...
Web Application Security Vulnerabilities Yen
... before they are used. Data type (string, integer, real, etc.) Allowed character set Minimum and maximum length Whether null is allowed Whether the parameter is required or not Whether duplicates are allowed Numeric range Specific legal values (enumeration) Specific patterns (regula ...
... before they are used. Data type (string, integer, real, etc.) Allowed character set Minimum and maximum length Whether null is allowed Whether the parameter is required or not Whether duplicates are allowed Numeric range Specific legal values (enumeration) Specific patterns (regula ...
Computer and System Logging Policy
... controls, operations, and general security. This policy provides a set of logging policies and procedures aimed to establish baseline components across the [LEP]. ...
... controls, operations, and general security. This policy provides a set of logging policies and procedures aimed to establish baseline components across the [LEP]. ...
File
... victim and to his or her‘s loved ones. But where and how do you attract stalkers on the internet? Well you can pick up stalkers wherever you go on the internet to socialize; this includes chat rooms, email. However, not all stalkers start of with intentions to stalk someone, several become stalkers ...
... victim and to his or her‘s loved ones. But where and how do you attract stalkers on the internet? Well you can pick up stalkers wherever you go on the internet to socialize; this includes chat rooms, email. However, not all stalkers start of with intentions to stalk someone, several become stalkers ...
PPT - CS
... • The server knows all passwords, but they are never transmitted across the network • Passwords are used to generate encryption keys. ...
... • The server knows all passwords, but they are never transmitted across the network • Passwords are used to generate encryption keys. ...
Survey of online attacks on E-Commerce sites
... Web based attacks are considered to be the greatest threat to the online business as it is related to confidentiality, availability, and integrity. The motive behind e-commerce attack is significantly different then other attacks; Web based attacks focus on an application itself and functions on lay ...
... Web based attacks are considered to be the greatest threat to the online business as it is related to confidentiality, availability, and integrity. The motive behind e-commerce attack is significantly different then other attacks; Web based attacks focus on an application itself and functions on lay ...
Lecture1
... of subjects to objects are in accordance with a security policy. To determine whether a specific access mode is allowed, the clearance of a subject is compared to the classification of the object (more precisely, to the combination of classification and set of compartments, making up the security le ...
... of subjects to objects are in accordance with a security policy. To determine whether a specific access mode is allowed, the clearance of a subject is compared to the classification of the object (more precisely, to the combination of classification and set of compartments, making up the security le ...
Data and Applications Security - The University of Texas at Dallas
... Defined “normal” and “suspicious” behavior and classify events in ...
... Defined “normal” and “suspicious” behavior and classify events in ...
Detection of the security mechanism` violations and other
... detection break-ins (i.e. attacks resulting in unauthorized control over the system) and explaining security breaches. The analysis of events logged by IDP/IDS systems is difficult because Internet worms generate many attacks and therefore well-thought-of intruders' attacks can go unspotted. The ana ...
... detection break-ins (i.e. attacks resulting in unauthorized control over the system) and explaining security breaches. The analysis of events logged by IDP/IDS systems is difficult because Internet worms generate many attacks and therefore well-thought-of intruders' attacks can go unspotted. The ana ...
Financial Reporting: The Institutional Setting
... to be protected, what threats should be protected against, and how likely the threats are. These questions can be answered via a detailed risk assessment. Assets to protect include hardware, software, data, people, documentation, and supplies. Likewise, classic threats include unauthorized access, u ...
... to be protected, what threats should be protected against, and how likely the threats are. These questions can be answered via a detailed risk assessment. Assets to protect include hardware, software, data, people, documentation, and supplies. Likewise, classic threats include unauthorized access, u ...
Payment Card Industry Security Standards
... that store, process or transmit this data Vendors Standard – with new requirements for software developers and manufacturers of Ecosystem of payment devices, applications, infrastructure and users applications and devices used in those transactions. Compliance with the PCI set of standards is mandat ...
... that store, process or transmit this data Vendors Standard – with new requirements for software developers and manufacturers of Ecosystem of payment devices, applications, infrastructure and users applications and devices used in those transactions. Compliance with the PCI set of standards is mandat ...
8. Enabling cybersecurity information exchange
... and services. This framework will be revised as those specifications evolve. As a result of implementing this Recommendation, telecommunication/ICT organizations, including Computer Incident Response Teams (CIRTs), both within and between jurisdictions, will: a) have information to enable decision m ...
... and services. This framework will be revised as those specifications evolve. As a result of implementing this Recommendation, telecommunication/ICT organizations, including Computer Incident Response Teams (CIRTs), both within and between jurisdictions, will: a) have information to enable decision m ...
5th Chapter - information systems and it audit
... • Reduces Administrative overheads • Reduces the time taken by user • Disadvantages : • Support for all major OS is difficult • Significant cost associated with SSO development • Single point of failure and total compromise of an organization’s IS assets ...
... • Reduces Administrative overheads • Reduces the time taken by user • Disadvantages : • Support for all major OS is difficult • Significant cost associated with SSO development • Single point of failure and total compromise of an organization’s IS assets ...
Slide 1
... Instead, IPSec provides a set of security algorithms plus a general framework that allows a pair of communicating entities to use whichever algorithms provide security appropriate for the communication. ...
... Instead, IPSec provides a set of security algorithms plus a general framework that allows a pair of communicating entities to use whichever algorithms provide security appropriate for the communication. ...
Security+ Guide to Network Security Fundamentals, Third
... There are several reasons why it is difficult to defend against today’s attacks Information security may be defined as that which protects the integrity, confidentiality, and availability of information on the devices that store, manipulate, and transmit the information through products, people, and ...
... There are several reasons why it is difficult to defend against today’s attacks Information security may be defined as that which protects the integrity, confidentiality, and availability of information on the devices that store, manipulate, and transmit the information through products, people, and ...
The CyberFence Difference
... used by other ICS data. This practice renders those solutions vulnerable to any malware that has penetrated the data network. 3eTI's CyberFence solution separates data and management across different tunnels and interfaces. In so doing, CyberFence isolates access to the management interface from any ...
... used by other ICS data. This practice renders those solutions vulnerable to any malware that has penetrated the data network. 3eTI's CyberFence solution separates data and management across different tunnels and interfaces. In so doing, CyberFence isolates access to the management interface from any ...
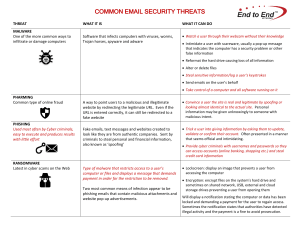
COMMON EMAIL SECURITY THREATS
... that indicates the computer has a security problem or other false information Reformat the hard drive causing loss of all information Alter or delete files Steal sensitive information/log a user’s keystrokes Send emails on the user’s behalf Take control of a computer and all software runni ...
... that indicates the computer has a security problem or other false information Reformat the hard drive causing loss of all information Alter or delete files Steal sensitive information/log a user’s keystrokes Send emails on the user’s behalf Take control of a computer and all software runni ...