The key questions that we`d like to ask at the beginning
... your entire conversation. Because if a hacker does manage to gain access to the private key, he still won’t be able to recover the shared, short-term secret key and will not be able to decrypt any communications. What’s more, PFS continuously changes the key material during a session, generating a n ...
... your entire conversation. Because if a hacker does manage to gain access to the private key, he still won’t be able to recover the shared, short-term secret key and will not be able to decrypt any communications. What’s more, PFS continuously changes the key material during a session, generating a n ...
Guide to Operating System Security
... Adopted by U.S. government to replace DES and 3DES Employs private-key block-cipher form of encryption Employs an algorithm called Rijndael ...
... Adopted by U.S. government to replace DES and 3DES Employs private-key block-cipher form of encryption Employs an algorithm called Rijndael ...
Chapter 19: Security
... – Encompasses the following issues: • Guaranteeing the privacy and integrity of sensitive data • Restricting the use of computer resources • Providing resilience against malicious attempts to incapacitate the system ...
... – Encompasses the following issues: • Guaranteeing the privacy and integrity of sensitive data • Restricting the use of computer resources • Providing resilience against malicious attempts to incapacitate the system ...
Chapter 19: Security
... – Encompasses the following issues: • Guaranteeing the privacy and integrity of sensitive data • Restricting the use of computer resources • Providing resilience against malicious attempts to incapacitate the system ...
... – Encompasses the following issues: • Guaranteeing the privacy and integrity of sensitive data • Restricting the use of computer resources • Providing resilience against malicious attempts to incapacitate the system ...
Chapter 19: Security - Murray State University
... – Encompasses the following issues: • Guaranteeing the privacy and integrity of sensitive data • Restricting the use of computer resources • Providing resilience against malicious attempts to incapacitate the system ...
... – Encompasses the following issues: • Guaranteeing the privacy and integrity of sensitive data • Restricting the use of computer resources • Providing resilience against malicious attempts to incapacitate the system ...
(FIPS) 140-2 - Aviat Networks
... Publicly announced standardizations developed by the United States federal government The strictest security standards on the market today! AVIAT NETWORKS ...
... Publicly announced standardizations developed by the United States federal government The strictest security standards on the market today! AVIAT NETWORKS ...
Lecture 1 - WordPress.com
... unauthorized disclosure Data Integrity - assurance that data received is as sent by an authorized entity Non-Repudiation - protection against denial by one of the parties in a communication Availability – resource accessible/usable ...
... unauthorized disclosure Data Integrity - assurance that data received is as sent by an authorized entity Non-Repudiation - protection against denial by one of the parties in a communication Availability – resource accessible/usable ...
Public Key Cryptography and RSA Review: Number Theory Basics
... • Public key distribution systems – two parties who do not share any private information through communications arrive at some secret not known to any eavesdroppers • Authentication with public keys: Digital Signature – the authentication tag of a message can only be computed by one user, but can be ...
... • Public key distribution systems – two parties who do not share any private information through communications arrive at some secret not known to any eavesdroppers • Authentication with public keys: Digital Signature – the authentication tag of a message can only be computed by one user, but can be ...
Data Encryption and Decryption Using New Pythagorean Triple
... results that only one fundamental solution (x, y, z) exists for p and q (one of which is odd and the other even). Based on 8, the previous definition is re-defined to: for any numbers p and q (one of which is odd and the other even) there are at least two fundamental solutions (x1 , y1 , z1 ) and (x2 ...
... results that only one fundamental solution (x, y, z) exists for p and q (one of which is odd and the other even). Based on 8, the previous definition is re-defined to: for any numbers p and q (one of which is odd and the other even) there are at least two fundamental solutions (x1 , y1 , z1 ) and (x2 ...
XML Security Standards — Overview for the Non - Events
... Key problem: Immaterial changes to XML documents Solution: Canonicalization Defines rules to encrypt XML and record parameters Support all technologies in common use Key problem: Encrypted data not Schema-valid Solution: None ...
... Key problem: Immaterial changes to XML documents Solution: Canonicalization Defines rules to encrypt XML and record parameters Support all technologies in common use Key problem: Encrypted data not Schema-valid Solution: None ...
lecture 3 - Philadelphia University
... third party can also determine who cheated. Adjudicated protocols involve the services of a third party only in case of a dispute. Therefore, they are usually less costly, in terms of machine time or access to a trusted third party software judge, than arbitrated protocols. However, adjudicated prot ...
... third party can also determine who cheated. Adjudicated protocols involve the services of a third party only in case of a dispute. Therefore, they are usually less costly, in terms of machine time or access to a trusted third party software judge, than arbitrated protocols. However, adjudicated prot ...
Virtual Private Network(VPN)
... • Loopholes – Hackers will try to "piggyback" onto an existing VPN connection that a remote worker has established, either inserting viruses into a system or removing and viewing sensitive files ...
... • Loopholes – Hackers will try to "piggyback" onto an existing VPN connection that a remote worker has established, either inserting viruses into a system or removing and viewing sensitive files ...
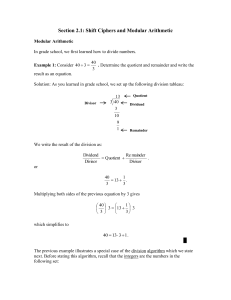
Section2.1notes
... Cryptanalysis of Shift Ciphers As the last two examples illustrate, one must know the key k used in a shift cipher when deciphering a message. This leads to an important question. How can we decipher a message in a shift cipher if we do not know the key k ? Cryptanalysis is the process of trying to ...
... Cryptanalysis of Shift Ciphers As the last two examples illustrate, one must know the key k used in a shift cipher when deciphering a message. This leads to an important question. How can we decipher a message in a shift cipher if we do not know the key k ? Cryptanalysis is the process of trying to ...
XML: Part - Houston Community College System
... Symmetric Cryptography Strengths and Weaknesses • Identical keys are used to both encrypt and decrypt the message • Popular symmetric cipher algorithms include Data Encryption Standard, Triple Data Encryption Standard, Advanced Encryption Standard, Rivest Cipher, International Data Encryption Algor ...
... Symmetric Cryptography Strengths and Weaknesses • Identical keys are used to both encrypt and decrypt the message • Popular symmetric cipher algorithms include Data Encryption Standard, Triple Data Encryption Standard, Advanced Encryption Standard, Rivest Cipher, International Data Encryption Algor ...
Understanding Cryptography
... These slides were prepared by Benedikt Driessen, Christof Paar and Jan Pelzl ...
... These slides were prepared by Benedikt Driessen, Christof Paar and Jan Pelzl ...
AA22161166
... Step 5:- Then this cipher text is communicated to the receiver in public channel. Decryption: - The receiver after receiving the cipher text decrypts the cipher text as follows: Step 1:- The receiver divides the cipher text into data blocks of m characters each. Step 2:- He decrypts the message by e ...
... Step 5:- Then this cipher text is communicated to the receiver in public channel. Decryption: - The receiver after receiving the cipher text decrypts the cipher text as follows: Step 1:- The receiver divides the cipher text into data blocks of m characters each. Step 2:- He decrypts the message by e ...
ISEC0511
... application can also be considered as part of the accounting information. These files need security so that adversaries cannot tamper or delete them. ...
... application can also be considered as part of the accounting information. These files need security so that adversaries cannot tamper or delete them. ...
CVES
... secure VOD service via network, Medical imaging systems, etc. Problems: 1) The well-developed modern ciphers cannot be directly used, because most of them run so slow (especially in software implementation). 2) Compression algorithms make it more difficult to incorporate the ciphers into the video ...
... secure VOD service via network, Medical imaging systems, etc. Problems: 1) The well-developed modern ciphers cannot be directly used, because most of them run so slow (especially in software implementation). 2) Compression algorithms make it more difficult to incorporate the ciphers into the video ...
Insert Title Here
... Make use of on-chip security features FPGA design Make sure all conditions are covered State machines should have default states in place ...
... Make use of on-chip security features FPGA design Make sure all conditions are covered State machines should have default states in place ...
Public-key encryption
... appending a (pseudo) random bit string to the plaintext prior to encryption salting is a solution to the small exponent problem – even if the same message m has to be sent to many recipients, the actual plaintext that is encrypted will be different for everyone due to salting Public-key encrypti ...
... appending a (pseudo) random bit string to the plaintext prior to encryption salting is a solution to the small exponent problem – even if the same message m has to be sent to many recipients, the actual plaintext that is encrypted will be different for everyone due to salting Public-key encrypti ...
Chapter 24 - William Stallings, Data and Computer
... (keeps track of sequence number and other info) ...
... (keeps track of sequence number and other info) ...
Blue Border - Courant Institute of Mathematical Sciences
... “New function” description: log(257)*64*16 ≈ 8192 bits and it's much faster! ...
... “New function” description: log(257)*64*16 ≈ 8192 bits and it's much faster! ...
Well-Tempered Clavier
... – The division of the piece into key sections would allow to infer when the key is changing as well as the “global key” (Timing) – Inertia of a key resolution ...
... – The division of the piece into key sections would allow to infer when the key is changing as well as the “global key” (Timing) – Inertia of a key resolution ...
pps - AquaLab - Northwestern University
... Goal – make plaintext into ciphertext so that only authorized people can convert it back Kerckhoff’s principle – Encryption/decryption algorithms should be public – avoid security by obscurity – Secrecy should depend on keys (parameters) ...
... Goal – make plaintext into ciphertext so that only authorized people can convert it back Kerckhoff’s principle – Encryption/decryption algorithms should be public – avoid security by obscurity – Secrecy should depend on keys (parameters) ...
Security
... • All users pick a public key/private key pair – publish the public key – private key not published ...
... • All users pick a public key/private key pair – publish the public key – private key not published ...
Cryptography

Cryptography or cryptology; from Greek κρυπτός kryptós, ""hidden, secret""; and γράφειν graphein, ""writing"", or -λογία -logia, ""study"", respectively is the practice and study of techniques for secure communication in the presence of third parties (called adversaries). More generally, it is about constructing and analyzing protocols that block adversaries; various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce.Cryptography prior to the modern age was effectively synonymous with encryption, the conversion of information from a readable state to apparent nonsense. The originator of an encrypted message shared the decoding technique needed to recover the original information only with intended recipients, thereby precluding unwanted persons from doing the same. Since World War I and the advent of the computer, the methods used to carry out cryptology have become increasingly complex and its application more widespread.Modern cryptography is heavily based on mathematical theory and computer science practice; cryptographic algorithms are designed around computational hardness assumptions, making such algorithms hard to break in practice by any adversary. It is theoretically possible to break such a system, but it is infeasible to do so by any known practical means. These schemes are therefore termed computationally secure; theoretical advances, e.g., improvements in integer factorization algorithms, and faster computing technology require these solutions to be continually adapted. There exist information-theoretically secure schemes that provably cannot be broken even with unlimited computing power—an example is the one-time pad—but these schemes are more difficult to implement than the best theoretically breakable but computationally secure mechanisms.The growth of cryptographic technology has raised a number of legal issues in the information age. Cryptography's potential for use as a tool for espionage and sedition has led many governments to classify it as a weapon and to limit or even prohibit its use and export. In some jurisdictions where the use of cryptography is legal, laws permit investigators to compel the disclosure of encryption keys for documents relevant to an investigation. Cryptography also plays a major role in digital rights management and piracy of digital media.