Networking & Security
... Ignorance (being unaware of implications.) Damage (Sadist) Prank (Just for Fun) Respect (By proving special skills) Analysis (Long term commercial gain) ...
... Ignorance (being unaware of implications.) Damage (Sadist) Prank (Just for Fun) Respect (By proving special skills) Analysis (Long term commercial gain) ...
Slides on Security
... • Cryptography in general represents the process of encrypting a plain-text message into an unreadable cipher so that it can be sent through a network to be decrypted/deciphered by the intended recipient. • Cryptography is an important tool for security. Key Plaintext ...
... • Cryptography in general represents the process of encrypting a plain-text message into an unreadable cipher so that it can be sent through a network to be decrypted/deciphered by the intended recipient. • Cryptography is an important tool for security. Key Plaintext ...
Public Key Encryption
... algorithms. Symmetric cryptography uses a single private key to both encrypt and decrypt data. Any party that has the key can use it to encrypt and decrypt data. Symmetric cryptography algorithms are typically fast and are suitable for processing large streams of data. The disadvantage of symmetric ...
... algorithms. Symmetric cryptography uses a single private key to both encrypt and decrypt data. Any party that has the key can use it to encrypt and decrypt data. Symmetric cryptography algorithms are typically fast and are suitable for processing large streams of data. The disadvantage of symmetric ...
Problem Set 3 [Word]
... When you attempt to decipher the message, you suspect that your colleague made a mistake when applying the keyword technique. What mistake did she make and what is the correct plaintext message? 2. Consider the following plain text: how much wood would a woodchuck chuck if a woodchuck could chuck wo ...
... When you attempt to decipher the message, you suspect that your colleague made a mistake when applying the keyword technique. What mistake did she make and what is the correct plaintext message? 2. Consider the following plain text: how much wood would a woodchuck chuck if a woodchuck could chuck wo ...
Lecture 6: Computational Security 1 Vernam Cipher (1917)
... 1. Fix an integer l > 0. Then the message space M, key space K, and ciphertext space C are all equal to {0, 1}l . 2. The key-generation algorithm Gen works by choosing a string k from {0, 1}l according to uniform distribution. 3. Encryption Enc works as follows: given a key k ∈ {0, 1}l and a message ...
... 1. Fix an integer l > 0. Then the message space M, key space K, and ciphertext space C are all equal to {0, 1}l . 2. The key-generation algorithm Gen works by choosing a string k from {0, 1}l according to uniform distribution. 3. Encryption Enc works as follows: given a key k ∈ {0, 1}l and a message ...
Ecommerce: Security and Control
... Public key cryptography uses two keys, rather than one – hence, sometimes referred to asymmetric. Symmetric encryption is still in use, and will continue to be This is because of the computational overhead associated with public key encryption ...
... Public key cryptography uses two keys, rather than one – hence, sometimes referred to asymmetric. Symmetric encryption is still in use, and will continue to be This is because of the computational overhead associated with public key encryption ...
Lecture 7
... takes data in blocks of b bytes and outputs blocks of l bytes. k´ is cryptographic key of length b bytes (from k) ...
... takes data in blocks of b bytes and outputs blocks of l bytes. k´ is cryptographic key of length b bytes (from k) ...
Packaging Information: Data Compression and
... keys) for both encryption and decryption The secret key must be transferred securely in order for secret key methods to be secure Data Encryption Standard (DES) is a US government sponsored secret key cipher. DES uses a 56-bit key. International Data Encryption Algorithm (IDEA) has been proposed to ...
... keys) for both encryption and decryption The secret key must be transferred securely in order for secret key methods to be secure Data Encryption Standard (DES) is a US government sponsored secret key cipher. DES uses a 56-bit key. International Data Encryption Algorithm (IDEA) has been proposed to ...
Web Security
... • once the source accepts the authenticity of the certificate it uses the public-key from the certificate to encrypt the generated session key for protecting the conversation between the source and destination. • Session is encrypted using a symmetric cipher (slow) • conversation is encrypted using ...
... • once the source accepts the authenticity of the certificate it uses the public-key from the certificate to encrypt the generated session key for protecting the conversation between the source and destination. • Session is encrypted using a symmetric cipher (slow) • conversation is encrypted using ...
Web Security
... certificate ( sent in the http header (uncncrypted)) • once the source accepts the authenticity of the certificate it uses the public-key from the certificate to encrypt the generated session key for protecting the conversation between the source and destination. • Session is encrypted using a symme ...
... certificate ( sent in the http header (uncncrypted)) • once the source accepts the authenticity of the certificate it uses the public-key from the certificate to encrypt the generated session key for protecting the conversation between the source and destination. • Session is encrypted using a symme ...
Three challenges with secret key encryption
... 1. What is “brute-force attack”? How the “brute-force attack” is related to Keyspace (the range of possible value of the Key)? Why the issue of number of bit required in a key to ensure secure encryption is controversial? A brute -force attack is applying all possible value of a key to the algorithm ...
... 1. What is “brute-force attack”? How the “brute-force attack” is related to Keyspace (the range of possible value of the Key)? Why the issue of number of bit required in a key to ensure secure encryption is controversial? A brute -force attack is applying all possible value of a key to the algorithm ...
Adopting Number Sequences for Shielding Information
... Cryptography is the branch of information security. The basic goal of cryptography is to make communication secure in the presence of third party (intruder). Encryption is the mechanism of transforming information into unreadable (cipher) form. This is accomplished for data integrity, forward secrec ...
... Cryptography is the branch of information security. The basic goal of cryptography is to make communication secure in the presence of third party (intruder). Encryption is the mechanism of transforming information into unreadable (cipher) form. This is accomplished for data integrity, forward secrec ...
Chapter 9 Public Key Cryptography and RSA
... 9.1 Principles of Public Key cryptosystems Security of Public Key Schemes like private key schemes brute force exhaustive search attack is always theoretically possible but keys used are too large (>512bits) security relies on a large enough difference in difficulty between easy (en/decrypt) ...
... 9.1 Principles of Public Key cryptosystems Security of Public Key Schemes like private key schemes brute force exhaustive search attack is always theoretically possible but keys used are too large (>512bits) security relies on a large enough difference in difficulty between easy (en/decrypt) ...
Chapter 10: Electronic Commerce Security
... today as Caesar Cyphers. The simplest replaces A with B, B with C etc. This is called a one-rotate code. The following is encrypted using a simple Caesar rotation cypher. See if you can decrypt it: ...
... today as Caesar Cyphers. The simplest replaces A with B, B with C etc. This is called a one-rotate code. The following is encrypted using a simple Caesar rotation cypher. See if you can decrypt it: ...
• Overview of Cyber Security & need of cyber security • Introduction
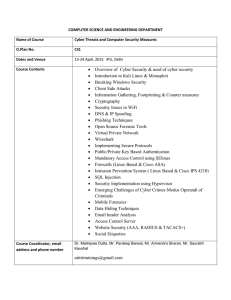
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
Network Security For Distributed Simulation Systems
... 5: If data is the same as the original then authentication is successful ...
... 5: If data is the same as the original then authentication is successful ...
Chapter 6
... encryption standard adopted by the U.S. government. • DES is the most widely used private-key encryption system. • Triple Data Encryption Standard (3DES) is a more robust version of DES. • The U.S. government’s National Institute of Standards and Technology (NIST) has been developing a new encryptio ...
... encryption standard adopted by the U.S. government. • DES is the most widely used private-key encryption system. • Triple Data Encryption Standard (3DES) is a more robust version of DES. • The U.S. government’s National Institute of Standards and Technology (NIST) has been developing a new encryptio ...
10 March 2009 - Computer Science
... The use of cryptographic protocols as a means to provide security to web servers and applications at the transport layer is becoming increasingly popular. However it is difficult to analyze this sort of traffic as it is encrypted •ISP's are often served with court orders to provide logs of clients a ...
... The use of cryptographic protocols as a means to provide security to web servers and applications at the transport layer is becoming increasingly popular. However it is difficult to analyze this sort of traffic as it is encrypted •ISP's are often served with court orders to provide logs of clients a ...
Public Key Encryption and Digital Signatures
... • Encryption – Simple or more complex substitutions – Key based approaches require secure ways to transmit a key – Public Key encryption • does not require communication of a key • security depends on the difficulty of factoring very large numbers (hundreds of digits) ...
... • Encryption – Simple or more complex substitutions – Key based approaches require secure ways to transmit a key – Public Key encryption • does not require communication of a key • security depends on the difficulty of factoring very large numbers (hundreds of digits) ...
The CyberFence Difference
... defense industrial networks for which efficiently secured machine-to-machine (M2M) communications are essential. ...
... defense industrial networks for which efficiently secured machine-to-machine (M2M) communications are essential. ...
lecture3.1 - Computer and Information Sciences
... • Good: Quite efficient (as you’ll see from the HW#2 programming exercise on AES) • Bad: Key distribution and management is a serious problem – for N users O(N2) keys are needed ...
... • Good: Quite efficient (as you’ll see from the HW#2 programming exercise on AES) • Bad: Key distribution and management is a serious problem – for N users O(N2) keys are needed ...
Lecture 9
... Factoring Problem of factoring a number is very hard Fermat’s factoring method sometimes can be used to find any large factors of a number fair quickly (pg.251) Want to make sure Fermat’s factoring method does not work for your key p and q should be at least 155 decimal ...
... Factoring Problem of factoring a number is very hard Fermat’s factoring method sometimes can be used to find any large factors of a number fair quickly (pg.251) Want to make sure Fermat’s factoring method does not work for your key p and q should be at least 155 decimal ...
Overview
... – those who encrypt messages or verify signatures cannot decrypt messages or create signatures ...
... – those who encrypt messages or verify signatures cannot decrypt messages or create signatures ...
Cryptography

Cryptography or cryptology; from Greek κρυπτός kryptós, ""hidden, secret""; and γράφειν graphein, ""writing"", or -λογία -logia, ""study"", respectively is the practice and study of techniques for secure communication in the presence of third parties (called adversaries). More generally, it is about constructing and analyzing protocols that block adversaries; various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce.Cryptography prior to the modern age was effectively synonymous with encryption, the conversion of information from a readable state to apparent nonsense. The originator of an encrypted message shared the decoding technique needed to recover the original information only with intended recipients, thereby precluding unwanted persons from doing the same. Since World War I and the advent of the computer, the methods used to carry out cryptology have become increasingly complex and its application more widespread.Modern cryptography is heavily based on mathematical theory and computer science practice; cryptographic algorithms are designed around computational hardness assumptions, making such algorithms hard to break in practice by any adversary. It is theoretically possible to break such a system, but it is infeasible to do so by any known practical means. These schemes are therefore termed computationally secure; theoretical advances, e.g., improvements in integer factorization algorithms, and faster computing technology require these solutions to be continually adapted. There exist information-theoretically secure schemes that provably cannot be broken even with unlimited computing power—an example is the one-time pad—but these schemes are more difficult to implement than the best theoretically breakable but computationally secure mechanisms.The growth of cryptographic technology has raised a number of legal issues in the information age. Cryptography's potential for use as a tool for espionage and sedition has led many governments to classify it as a weapon and to limit or even prohibit its use and export. In some jurisdictions where the use of cryptography is legal, laws permit investigators to compel the disclosure of encryption keys for documents relevant to an investigation. Cryptography also plays a major role in digital rights management and piracy of digital media.

![Problem Set 3 [Word]](http://s1.studyres.com/store/data/019170310_1-579dc2e4bff01e038f7e8fb41a8fb2e8-300x300.png)