Ibrahim Aljubayri`s presentation on Secure Network Channel among
... and can transfer security information of the subject. It is significant that SOSTC can be used to extend a security range of secure operating system to the network environment. ...
... and can transfer security information of the subject. It is significant that SOSTC can be used to extend a security range of secure operating system to the network environment. ...
Chapter 1 Security Problems in Computing
... Popular Encryption Algorithms – Merkle-Hellman Knapsacks – RSA Encryption – El Gamal Algorithms – DES Hashing Algorithms ...
... Popular Encryption Algorithms – Merkle-Hellman Knapsacks – RSA Encryption – El Gamal Algorithms – DES Hashing Algorithms ...
Chapter 12
... Data Communications and Computer Networks: A Business User's Approach, Fifth Edition ...
... Data Communications and Computer Networks: A Business User's Approach, Fifth Edition ...
Teaching Computer Security using Minix
... Each project adds a new functionality to the base system or replaces a functionality It is NOT a toy system, and it is NOT so complicated (some of the instructional OS has been used in some embedded systems) ...
... Each project adds a new functionality to the base system or replaces a functionality It is NOT a toy system, and it is NOT so complicated (some of the instructional OS has been used in some embedded systems) ...
Application research and analysis based on Bitlocker
... on trusted computing technology In Windows 7[2],. Due to the use of a series of security boot measures with focus on Bitlocker, thus it is very difficult to apply to Windows 7 of Bootkit attack that makes use of tampering with the operating system and starting up files to achieve the kernel hijackin ...
... on trusted computing technology In Windows 7[2],. Due to the use of a series of security boot measures with focus on Bitlocker, thus it is very difficult to apply to Windows 7 of Bootkit attack that makes use of tampering with the operating system and starting up files to achieve the kernel hijackin ...
An IPSec-based Host Architecture for Secure
... • Develop overall architecture for secure IP multicast and research for appropriate protocols that can be standardized ...
... • Develop overall architecture for secure IP multicast and research for appropriate protocols that can be standardized ...
CH10
... Encryption Solutions (cont’d.) • Asymmetric encryption (public-key encryption) – Encodes messages using two mathematically related numeric keys – Public key: one key freely distributed to public • Encrypt messages using encryption algorithm ...
... Encryption Solutions (cont’d.) • Asymmetric encryption (public-key encryption) – Encodes messages using two mathematically related numeric keys – Public key: one key freely distributed to public • Encrypt messages using encryption algorithm ...
A Survey of BGP Security: Issues and Solutions
... • BGP: Dominant Interdomain Routing Protocol ▫ Deployed Since Internet First Commercialized ▫ Current Version 4 In Use for Over Ten Years ▫ Popular Despite Providing No Performance/Security Guarantees ...
... • BGP: Dominant Interdomain Routing Protocol ▫ Deployed Since Internet First Commercialized ▫ Current Version 4 In Use for Over Ten Years ▫ Popular Despite Providing No Performance/Security Guarantees ...
Introduction CS 239 Security for Networks and System
... Communications • Operating systems provide various kinds of interprocess communications – Messages – Semaphores – Shared memory – Sockets • How can we be sure they’re used properly? ...
... Communications • Operating systems provide various kinds of interprocess communications – Messages – Semaphores – Shared memory – Sockets • How can we be sure they’re used properly? ...
Auditing (cont'd.) - Elgin Community College
... Windows Defender is antispyware software Microsoft Security Essentials is free antivirus software EFS protects individual files by encrypting them BitLocker Drive Encryption encrypts an entire partition Windows Update ensures that patches are applied to Windows 7 as they are made available ...
... Windows Defender is antispyware software Microsoft Security Essentials is free antivirus software EFS protects individual files by encrypting them BitLocker Drive Encryption encrypts an entire partition Windows Update ensures that patches are applied to Windows 7 as they are made available ...
EAP
... Was supposed to provide authentication and privacy Secret 40 bit keys, but unsafe at any length Static-manually-configured keys Weakness due to long life of keys and they are shared among many users ...
... Was supposed to provide authentication and privacy Secret 40 bit keys, but unsafe at any length Static-manually-configured keys Weakness due to long life of keys and they are shared among many users ...
CHAPTER FIVE
... The notion of one- way function is central to public key cryptography .One way function are easy to compute , but it is significantly hard (computationally) to reverse. That is given x , it is easy to compute f(x) , but given f(x), it is hard to compute x .Breaking plate is a good example of a one-w ...
... The notion of one- way function is central to public key cryptography .One way function are easy to compute , but it is significantly hard (computationally) to reverse. That is given x , it is easy to compute f(x) , but given f(x), it is hard to compute x .Breaking plate is a good example of a one-w ...
Algorithms for Public Key Cryptography Computing Square Roots
... • Primes ∈ coRP (Solovay-Strassen 77, Rabin 80). Primes ∈ RP. Thus, Primes ∈ ZPP = RP T coRP. ...
... • Primes ∈ coRP (Solovay-Strassen 77, Rabin 80). Primes ∈ RP. Thus, Primes ∈ ZPP = RP T coRP. ...
Security & Cryptography
... Generally speaking, IKE is a method for securely exchanging encryption ciphers that will be used in a later encrypted session IPSec is an overall term used to describe encrypted data communication over IP, using the keys exchanged with IKE ...
... Generally speaking, IKE is a method for securely exchanging encryption ciphers that will be used in a later encrypted session IPSec is an overall term used to describe encrypted data communication over IP, using the keys exchanged with IKE ...
Electronic Commerce and Information Security
... along in the alphabet Stream cipher: Encodes one character at a time Substitution cipher: A single letter of plaintext generates a single letter of ciphertext ...
... along in the alphabet Stream cipher: Encodes one character at a time Substitution cipher: A single letter of plaintext generates a single letter of ciphertext ...
Computer Network Security Protocols and Standards
... for a Web that was simple, that did not have dynamic graphics, that did not require, at that time, hard encryption for end-to-end transactions that have since developed. – As the Web became popular for businesses users realized that current HTTP protocols needed more cryptographic and graphic improv ...
... for a Web that was simple, that did not have dynamic graphics, that did not require, at that time, hard encryption for end-to-end transactions that have since developed. – As the Web became popular for businesses users realized that current HTTP protocols needed more cryptographic and graphic improv ...
Cryptographic hashing - comp
... Consider a message m is split into blocks m1, m2, …, mk without padding and hashed to a value h(m). Choose a message m’ that splits into the block m1, m2, …, mk, mk+1 (the first k blocks are identical to m’s). Therefore, h(m) is the intermediate hash value after k blocks in the computation of h(m’). ...
... Consider a message m is split into blocks m1, m2, …, mk without padding and hashed to a value h(m). Choose a message m’ that splits into the block m1, m2, …, mk, mk+1 (the first k blocks are identical to m’s). Therefore, h(m) is the intermediate hash value after k blocks in the computation of h(m’). ...
Data Encryption Standard - gozips.uakron.edu
... corresponds to the public key used for the encryption Well regarded asymmetric techniques include: RSA (Rivest, Shamir, and Adleman), DSS (Digital Signature Standard), and EIGamal Internet protocols using asymmetric ciphers include: Secure Socket Layer (SSL), Transport Layer Security (TLS), Secu ...
... corresponds to the public key used for the encryption Well regarded asymmetric techniques include: RSA (Rivest, Shamir, and Adleman), DSS (Digital Signature Standard), and EIGamal Internet protocols using asymmetric ciphers include: Secure Socket Layer (SSL), Transport Layer Security (TLS), Secu ...
Systeemanalyse in Ontwerpprojecten
... Framework of Thinking, cont. • Security Services (SSs) are functions that enhance the security requirements of an information system (i.e., the probability that an IS is in a secure state) • Example SSs are identification, authentication, authorization, (role-based) access control, certification, d ...
... Framework of Thinking, cont. • Security Services (SSs) are functions that enhance the security requirements of an information system (i.e., the probability that an IS is in a secure state) • Example SSs are identification, authentication, authorization, (role-based) access control, certification, d ...
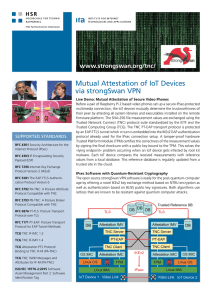
Mutual Attestation of IoT Devices via strongSwan VPN
... Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport protocol is protected by an EAP-TTLS tunnel which in turn is embedded into the IKEv2 EAP authentication protocol already used for the IPsec connection setup. A tamper ...
... Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport protocol is protected by an EAP-TTLS tunnel which in turn is embedded into the IKEv2 EAP authentication protocol already used for the IPsec connection setup. A tamper ...
Heap Sort
... a dictionary, if it can be arranged such that the key is also the index to the array that stores the entries, searching and inserting items would be very fast ► Example: empdata[1000] index = employee ID number ► Search ...
... a dictionary, if it can be arranged such that the key is also the index to the array that stores the entries, searching and inserting items would be very fast ► Example: empdata[1000] index = employee ID number ► Search ...
Computer and Information Security
... The Good News... • There a lot of techniques for defense • Educating people on security solves many problems • About threats and on the existence of security mechanisms, qualified personnel, usability and economics • We will study a lot of network defenses – Certainly not all ...
... The Good News... • There a lot of techniques for defense • Educating people on security solves many problems • About threats and on the existence of security mechanisms, qualified personnel, usability and economics • We will study a lot of network defenses – Certainly not all ...
Security Features in Windows CE
... Additionally, databases that are stored within the object store can be given a system flag. System databases cannot be read or modified by untrusted applications. Databases that are stored in separate database volumes rather than in the object store can be protected by setting the system attribute o ...
... Additionally, databases that are stored within the object store can be given a system flag. System databases cannot be read or modified by untrusted applications. Databases that are stored in separate database volumes rather than in the object store can be protected by setting the system attribute o ...
Introduction to Information Security Chapter N
... – the message is divided into blocks, i.e., 8 or 16 bit – and then each block is transformed using the algorithm and key ...
... – the message is divided into blocks, i.e., 8 or 16 bit – and then each block is transformed using the algorithm and key ...
PCI Compliance Without Compensating Controls – How to Take Ulf Mattsson
... mitigated the risk associated with the requirement through implementation of other, or compensating, controls. • Compensating controls must satisfy the following criteria: • Meet the intent and rigor of the original PCI DSS requirement. • Provide a similar level of defense as the original PCI DSS re ...
... mitigated the risk associated with the requirement through implementation of other, or compensating, controls. • Compensating controls must satisfy the following criteria: • Meet the intent and rigor of the original PCI DSS requirement. • Provide a similar level of defense as the original PCI DSS re ...
Cryptography

Cryptography or cryptology; from Greek κρυπτός kryptós, ""hidden, secret""; and γράφειν graphein, ""writing"", or -λογία -logia, ""study"", respectively is the practice and study of techniques for secure communication in the presence of third parties (called adversaries). More generally, it is about constructing and analyzing protocols that block adversaries; various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce.Cryptography prior to the modern age was effectively synonymous with encryption, the conversion of information from a readable state to apparent nonsense. The originator of an encrypted message shared the decoding technique needed to recover the original information only with intended recipients, thereby precluding unwanted persons from doing the same. Since World War I and the advent of the computer, the methods used to carry out cryptology have become increasingly complex and its application more widespread.Modern cryptography is heavily based on mathematical theory and computer science practice; cryptographic algorithms are designed around computational hardness assumptions, making such algorithms hard to break in practice by any adversary. It is theoretically possible to break such a system, but it is infeasible to do so by any known practical means. These schemes are therefore termed computationally secure; theoretical advances, e.g., improvements in integer factorization algorithms, and faster computing technology require these solutions to be continually adapted. There exist information-theoretically secure schemes that provably cannot be broken even with unlimited computing power—an example is the one-time pad—but these schemes are more difficult to implement than the best theoretically breakable but computationally secure mechanisms.The growth of cryptographic technology has raised a number of legal issues in the information age. Cryptography's potential for use as a tool for espionage and sedition has led many governments to classify it as a weapon and to limit or even prohibit its use and export. In some jurisdictions where the use of cryptography is legal, laws permit investigators to compel the disclosure of encryption keys for documents relevant to an investigation. Cryptography also plays a major role in digital rights management and piracy of digital media.