Osma prednaska: Cryptography of eliptic curves, factorization
... Basis idea: To factorize an integer n choose an elliptic curve E, a point on E (mod n) and compute either iP for i=2,3,4,… or 2j P for j=1,2,…. In doing that one needs to compute gcd(k,n) for various k. If one if these values is between 1 and n we have a factor of n. Factoring of large integers: The ...
... Basis idea: To factorize an integer n choose an elliptic curve E, a point on E (mod n) and compute either iP for i=2,3,4,… or 2j P for j=1,2,…. In doing that one needs to compute gcd(k,n) for various k. If one if these values is between 1 and n we have a factor of n. Factoring of large integers: The ...
Microsoft PowerPoint - file [jen pro \350ten\355]
... momentum and has a tendency to replace the public key cryptography based on unfeasibility of the factorization of integers, or on unfeasibility of the computation of discrete logarithms. For example, US-government has recommended to use elliptic curve cryptography. The main advantage of elliptic cur ...
... momentum and has a tendency to replace the public key cryptography based on unfeasibility of the factorization of integers, or on unfeasibility of the computation of discrete logarithms. For example, US-government has recommended to use elliptic curve cryptography. The main advantage of elliptic cur ...
Osma prednaska: Cryptography of eliptic curves, factorization
... momentum and has a tendency to replace the public key cryptography based on unfeasibility of the factorization of integers, or on unfeasibility of the computation of discrete logarithms. For example, US-government has recommended to use elliptic curve cryptography. The main advantage of elliptic cur ...
... momentum and has a tendency to replace the public key cryptography based on unfeasibility of the factorization of integers, or on unfeasibility of the computation of discrete logarithms. For example, US-government has recommended to use elliptic curve cryptography. The main advantage of elliptic cur ...
X - FI MUNI
... momentum and has a tendency to replace the public key cryptography based on unfeasibility of the factorization of integers, or on unfeasibility of the computation of discrete logarithms. For example, US-government has recommended to use elliptic curve cryptography. The main advantage of elliptic cur ...
... momentum and has a tendency to replace the public key cryptography based on unfeasibility of the factorization of integers, or on unfeasibility of the computation of discrete logarithms. For example, US-government has recommended to use elliptic curve cryptography. The main advantage of elliptic cur ...
Cryptanalysis of Shieh-Lin-Yang
... The message m is first signed by an initiator U1, and then is sent separately to all signer. Finally,U1 is responsible for combining these individual signature into a multisignature. ...
... The message m is first signed by an initiator U1, and then is sent separately to all signer. Finally,U1 is responsible for combining these individual signature into a multisignature. ...
Fast Variants of RSA
... modulus) and even faster processors are coming out. In this paper we survey four simple variants of RSA that are designed to speed up RSA decryption in software. Throughout the paper we focus on a 1024-bit RSA modulus. We emphasize backwards compatibility: A system using one of these variants for fa ...
... modulus) and even faster processors are coming out. In this paper we survey four simple variants of RSA that are designed to speed up RSA decryption in software. Throughout the paper we focus on a 1024-bit RSA modulus. We emphasize backwards compatibility: A system using one of these variants for fa ...
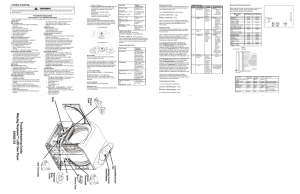
Troubleshooting Guide Maytag Neptune™ LED Gas Dryer 6390 2110
... Press the Wrinkle Release key to access the Diagnostic Codes. Scroll through the Diagnostic Codes by pressing the Temperature (^) key. The first time the key is pressed the newest code will be displayed. Each additional key press shows the next code. Once all the codes have been displayed a “d” is d ...
... Press the Wrinkle Release key to access the Diagnostic Codes. Scroll through the Diagnostic Codes by pressing the Temperature (^) key. The first time the key is pressed the newest code will be displayed. Each additional key press shows the next code. Once all the codes have been displayed a “d” is d ...
Cardenas_Claudia_WorkShopSlides
... In terms of the PHY layer most of these attacks can be counteracted by using different signals and proper configuration of the protocol. Some of MAC flaws have been fixed by the enhanced security of IEEE 802.16e but not all of them. The lack of encryption of MAC management messages that can affect t ...
... In terms of the PHY layer most of these attacks can be counteracted by using different signals and proper configuration of the protocol. Some of MAC flaws have been fixed by the enhanced security of IEEE 802.16e but not all of them. The lack of encryption of MAC management messages that can affect t ...
CHAPTER 01 - Basics of coding theory
... IV054 Practicality of Factoring Using ECC (1) Let us continue to discuss the following key problem for factorization using elliptic curves: Problem: How to choose k such that for a given point P we should try to compute iP or 2iP for multiples of P smaller than kP? Idea: If one searches for m-digit ...
... IV054 Practicality of Factoring Using ECC (1) Let us continue to discuss the following key problem for factorization using elliptic curves: Problem: How to choose k such that for a given point P we should try to compute iP or 2iP for multiples of P smaller than kP? Idea: If one searches for m-digit ...
Datasäkerhet/Data security EDA625 – Lect2 CRYPTOGRAPHY
... strong collision resistance: it is infeasable to find x,x’ such that h(x)=h(x’) ...
... strong collision resistance: it is infeasable to find x,x’ such that h(x)=h(x’) ...
Document
... Subroutine ? is more efficient. This measure is good for all large input sizes In fact, we will not worry about the exact values, but will look at ``broad classes’ of values, or the growth rates Let there be n inputs. If an algorithm needs n basic operations and another needs 2n basic operations, we ...
... Subroutine ? is more efficient. This measure is good for all large input sizes In fact, we will not worry about the exact values, but will look at ``broad classes’ of values, or the growth rates Let there be n inputs. If an algorithm needs n basic operations and another needs 2n basic operations, we ...
Lakshmi Nannapaneni`s presentation on Patterns for Secure Boot
... The bootloader loads the operating system kernel, and the operating system kernel loads system services, device drivers, and other applications. At any stage of the bootstrap process, software components could have been exchanged or modified by another user or by malicious software that has been ...
... The bootloader loads the operating system kernel, and the operating system kernel loads system services, device drivers, and other applications. At any stage of the bootstrap process, software components could have been exchanged or modified by another user or by malicious software that has been ...
Chapter 4
... 5 : allows inter-realm authentication, in beta test Kerberos v5 is an Internet standard specified in RFC1510, and used by many utilities To use Kerberos: need to have a KDC on your network need to have Kerberised applications running on all participating systems major problem - US export restriction ...
... 5 : allows inter-realm authentication, in beta test Kerberos v5 is an Internet standard specified in RFC1510, and used by many utilities To use Kerberos: need to have a KDC on your network need to have Kerberised applications running on all participating systems major problem - US export restriction ...
Public-Key Cryptosystems from the Worst
... art in lattice algorithms) to be exponentially hard in the dimension n. In our reduction, the modulus q grows with ζ, so relying on this (potentially) easier variant of GapSVP permits a smaller choice of q. • We then consider prior LWE-based schemes, such as public-key cryptosystems [Reg05, PVW08] a ...
... art in lattice algorithms) to be exponentially hard in the dimension n. In our reduction, the modulus q grows with ζ, so relying on this (potentially) easier variant of GapSVP permits a smaller choice of q. • We then consider prior LWE-based schemes, such as public-key cryptosystems [Reg05, PVW08] a ...
CSIT560 Project Presentation
... standard is becoming the international standard for VPN. IPSec has created a secure means for interoperable security, which guarantees that encrypted information is protected on its way from one network to another, while also allowing partner companies to link their respective VPNs together, even ...
... standard is becoming the international standard for VPN. IPSec has created a secure means for interoperable security, which guarantees that encrypted information is protected on its way from one network to another, while also allowing partner companies to link their respective VPNs together, even ...
Split-Ordered Lists: Lock-Free Extensible Hash Tables
... hash table needs to be extended. A common way of doing this, is to increase the size of the bucket array and redistribute the items among the new buckets. In the context of concurrent programming, the operations find, delete and resize requires special care since several parallel threads may be acce ...
... hash table needs to be extended. A common way of doing this, is to increase the size of the bucket array and redistribute the items among the new buckets. In the context of concurrent programming, the operations find, delete and resize requires special care since several parallel threads may be acce ...
CIS 5357 - FSU Computer Science
... If every attacker has only a negligible probability of success, we say that the scheme is secure under chosen-plaintext attacks. ...
... If every attacker has only a negligible probability of success, we say that the scheme is secure under chosen-plaintext attacks. ...
Using Digital Signature with DNS
... • Public KEYs can be used to verify the SIGs • The authenticity of public KEYs is established by a SIGnature over the keys with the parent’s private key • In the ideal case, only one public KEY needs to be distributed off-band (the root’s public KEY) ...
... • Public KEYs can be used to verify the SIGs • The authenticity of public KEYs is established by a SIGnature over the keys with the parent’s private key • In the ideal case, only one public KEY needs to be distributed off-band (the root’s public KEY) ...
Chapter 10
... • Biometric security devices – Identification using element of person’s biological makeup • Writing pads, eye scanners, palm reading scanners, reading back of hand vein pattern E-Business, Eighth Edition ...
... • Biometric security devices – Identification using element of person’s biological makeup • Writing pads, eye scanners, palm reading scanners, reading back of hand vein pattern E-Business, Eighth Edition ...
Slide 1
... Stateful Inspection Firewall Wirespeed IP Security VPN Attack Detection Integrated Hardware Accelerated Encryption HTTP & SMTP Proxies Traffic Filtering with event logging AES / 3DES 802.1x Authentication SNMPv3 ...
... Stateful Inspection Firewall Wirespeed IP Security VPN Attack Detection Integrated Hardware Accelerated Encryption HTTP & SMTP Proxies Traffic Filtering with event logging AES / 3DES 802.1x Authentication SNMPv3 ...
Chapter 9 - EECS People Web Server
... – Know and understand access control approaches, including authentication, authorization, and biometric access controls – Define and identify the various types of firewalls and the common approaches to firewall implementation – Discuss the current issues in dial-up access and protection – Identify a ...
... – Know and understand access control approaches, including authentication, authorization, and biometric access controls – Define and identify the various types of firewalls and the common approaches to firewall implementation – Discuss the current issues in dial-up access and protection – Identify a ...
Issue 43 Key RSC Discussion
... KeyRSC, the AC currently has no way to know precisely what the correct value is at the point at which message 3 is constructed. To work around this, LWAPP designers chose to have the AC simply set this value to 0. This decision does not affect the WTP, who maintains this counter; it only affects the ...
... KeyRSC, the AC currently has no way to know precisely what the correct value is at the point at which message 3 is constructed. To work around this, LWAPP designers chose to have the AC simply set this value to 0. This decision does not affect the WTP, who maintains this counter; it only affects the ...
Organizations That Use TLS/SSL
... TLS/SSL may be a requirement of the Payment Card Industry Data Security Standard (PCI DSS). This standard was created by the PCI Security Standards Council, a group of several major payment card brands, to protect cardholder data. Organizations may be required to comply with the PCI DSS by their acq ...
... TLS/SSL may be a requirement of the Payment Card Industry Data Security Standard (PCI DSS). This standard was created by the PCI Security Standards Council, a group of several major payment card brands, to protect cardholder data. Organizations may be required to comply with the PCI DSS by their acq ...
Chapter12-Security
... Data Communications and Computer Networks: A Business User's Approach, Sixth Edition ...
... Data Communications and Computer Networks: A Business User's Approach, Sixth Edition ...
Number Theory: Applications
... Recall that we can find the gcd (and thus lcm) by finding the prime factorization of the two integers. However, the only algorithms known for doing this are exponential (indeed, computer security depends on this). We can, however, compute the gcd in polynomial time using Euclid’s Algorithm. ...
... Recall that we can find the gcd (and thus lcm) by finding the prime factorization of the two integers. However, the only algorithms known for doing this are exponential (indeed, computer security depends on this). We can, however, compute the gcd in polynomial time using Euclid’s Algorithm. ...
Cryptography

Cryptography or cryptology; from Greek κρυπτός kryptós, ""hidden, secret""; and γράφειν graphein, ""writing"", or -λογία -logia, ""study"", respectively is the practice and study of techniques for secure communication in the presence of third parties (called adversaries). More generally, it is about constructing and analyzing protocols that block adversaries; various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce.Cryptography prior to the modern age was effectively synonymous with encryption, the conversion of information from a readable state to apparent nonsense. The originator of an encrypted message shared the decoding technique needed to recover the original information only with intended recipients, thereby precluding unwanted persons from doing the same. Since World War I and the advent of the computer, the methods used to carry out cryptology have become increasingly complex and its application more widespread.Modern cryptography is heavily based on mathematical theory and computer science practice; cryptographic algorithms are designed around computational hardness assumptions, making such algorithms hard to break in practice by any adversary. It is theoretically possible to break such a system, but it is infeasible to do so by any known practical means. These schemes are therefore termed computationally secure; theoretical advances, e.g., improvements in integer factorization algorithms, and faster computing technology require these solutions to be continually adapted. There exist information-theoretically secure schemes that provably cannot be broken even with unlimited computing power—an example is the one-time pad—but these schemes are more difficult to implement than the best theoretically breakable but computationally secure mechanisms.The growth of cryptographic technology has raised a number of legal issues in the information age. Cryptography's potential for use as a tool for espionage and sedition has led many governments to classify it as a weapon and to limit or even prohibit its use and export. In some jurisdictions where the use of cryptography is legal, laws permit investigators to compel the disclosure of encryption keys for documents relevant to an investigation. Cryptography also plays a major role in digital rights management and piracy of digital media.
![Microsoft PowerPoint - file [jen pro \350ten\355]](http://s1.studyres.com/store/data/013242156_1-6d27a8b2fd52728ab8cdcdca733b5a2d-300x300.png)