Unit 6 - WordPress.com
... Share Resources and Information Using a Computer network we can share expensive resources such as laser printers, CD-ROM Drives, Fax machines etc. We can share information and many persons can work together on projects and tasks that require co-ordination and communication, even though these users m ...
... Share Resources and Information Using a Computer network we can share expensive resources such as laser printers, CD-ROM Drives, Fax machines etc. We can share information and many persons can work together on projects and tasks that require co-ordination and communication, even though these users m ...
pSHIELD STS DEMO Poster
... A monitoring system can be structured into 2 main layers: sensor network layer Physical level: is responsible of the processing of the locally generated data at the node level Transport level: controls the communication between the nodes of the network application layer Integration level: is respons ...
... A monitoring system can be structured into 2 main layers: sensor network layer Physical level: is responsible of the processing of the locally generated data at the node level Transport level: controls the communication between the nodes of the network application layer Integration level: is respons ...
What is a Network? A network consists of two or more nodes
... Wide Area Networks (WANs) connect larger geographic areas, such as Ontario, Canada, or the world. For instance, Nova Corp. has a plant in Sarnia and a plant in Calgary. Dedicated transoceanic cabling or satellite uplinks may be used to connect this type of network. The largest WAN is the Internet. U ...
... Wide Area Networks (WANs) connect larger geographic areas, such as Ontario, Canada, or the world. For instance, Nova Corp. has a plant in Sarnia and a plant in Calgary. Dedicated transoceanic cabling or satellite uplinks may be used to connect this type of network. The largest WAN is the Internet. U ...
Assignment # 3 - UNT Class Server
... campus. A switch serves as a controller, allowing network devices to talk to each other efficiently, they are often referred to as a switching hub. They are used by businesses and schools to make it more efficient for network devices to communicate with each other. Network switches can range in pric ...
... campus. A switch serves as a controller, allowing network devices to talk to each other efficiently, they are often referred to as a switching hub. They are used by businesses and schools to make it more efficient for network devices to communicate with each other. Network switches can range in pric ...
New Hampshire Department of Transportation I
... “Given that NHSafeNet is one of the first projects of its kind for a state in the U.S., we are very pleased with the planning, execution, and results of this complex microwave network project... The ultimate goal of this project was to increase bandwidth and functionality across multiple public inst ...
... “Given that NHSafeNet is one of the first projects of its kind for a state in the U.S., we are very pleased with the planning, execution, and results of this complex microwave network project... The ultimate goal of this project was to increase bandwidth and functionality across multiple public inst ...
glossary - Homework Market
... One that buys goods or services. Distinct pieces of digital information. Data is usually formatted in a specific way and can exist in a variety of forms, such as numbers, text, etc. When used in the context of transmission media, data refers to information in binary digital format. A device is a uni ...
... One that buys goods or services. Distinct pieces of digital information. Data is usually formatted in a specific way and can exist in a variety of forms, such as numbers, text, etc. When used in the context of transmission media, data refers to information in binary digital format. A device is a uni ...
Measuring Application Performance with the Fluke Networks
... analyzers and other network monitoring tools could connect directly to a shared media hub port to gain network access. With switched networks, mirror ports or SPAN ports provided access for the network monitoring tools. The advent of full-duplex lines and the high traffic load on today’s switched ne ...
... analyzers and other network monitoring tools could connect directly to a shared media hub port to gain network access. With switched networks, mirror ports or SPAN ports provided access for the network monitoring tools. The advent of full-duplex lines and the high traffic load on today’s switched ne ...
Members First Credit Union
... Lead the design, test, and deployment of new or enhanced network services, both physically and virtually. Perform server troubleshooting and triage during service failure scenarios and participate in detailed investigations to determine root cause and corrective actions. Support the current LAN/WAN ...
... Lead the design, test, and deployment of new or enhanced network services, both physically and virtually. Perform server troubleshooting and triage during service failure scenarios and participate in detailed investigations to determine root cause and corrective actions. Support the current LAN/WAN ...
Job Description - Members First Credit Union
... Lead the design, test, and deployment of new or enhanced network services, both physically and virtually. Perform server troubleshooting and triage during service failure scenarios and participate in detailed investigations to determine root cause and corrective actions. Support the current LAN/WAN ...
... Lead the design, test, and deployment of new or enhanced network services, both physically and virtually. Perform server troubleshooting and triage during service failure scenarios and participate in detailed investigations to determine root cause and corrective actions. Support the current LAN/WAN ...
ITEC 370 Midterm
... ____ 21. The ____ frame type is generally used on the AppleTalk Phase 2 networks. a. Ethernet 802.2 c. Ethernet SNAP b. Ethernet 802.3 d. Ethernet II ____ 22. ____ is a high-speed, baseband digital networking standard that specifies incrementally increasing data rates across fiber-optic links. a. SO ...
... ____ 21. The ____ frame type is generally used on the AppleTalk Phase 2 networks. a. Ethernet 802.2 c. Ethernet SNAP b. Ethernet 802.3 d. Ethernet II ____ 22. ____ is a high-speed, baseband digital networking standard that specifies incrementally increasing data rates across fiber-optic links. a. SO ...
This morning one of our programmers, Zundra Daniel went up to
... This mass replication of packets leads to extremely high levels of network traffic and causes severe packet collision problems. This does not occur on most wired networks because most networks use switches or routers (wired not wireless) instead of hubs. Switches and routers are "intelligent" and kn ...
... This mass replication of packets leads to extremely high levels of network traffic and causes severe packet collision problems. This does not occur on most wired networks because most networks use switches or routers (wired not wireless) instead of hubs. Switches and routers are "intelligent" and kn ...
Ch01
... on the same network switch. Network reconfiguration is done through software (more on chapter 11, if we go that far). A virtual private network (VPN) is a network that uses a public telecommunication infrastructure, such as the Internet, to provide secure access to a user’s intranet (more on chapter ...
... on the same network switch. Network reconfiguration is done through software (more on chapter 11, if we go that far). A virtual private network (VPN) is a network that uses a public telecommunication infrastructure, such as the Internet, to provide secure access to a user’s intranet (more on chapter ...
Global Engagement of People Networks: Building e
... Towards exponential and broad new scientific and educational uses! ...
... Towards exponential and broad new scientific and educational uses! ...
HorstmannSymposium_2017.doc
... Kristen M. Horstmann*1,2, Ben G. Fitzpatrick2, Kam D. Dahlquist1 ...
... Kristen M. Horstmann*1,2, Ben G. Fitzpatrick2, Kam D. Dahlquist1 ...
Basic LAN Devices Repeaters There are many types of media, and
... The purpose of a hub is to regenerate and retime network signals. This is done at the bit level to a large number of hosts (e.g. 4, 8, or even 24) using a process known as concentration. You will notice that this definition is very similar to the repeater's, which is why a hub is also known as a mul ...
... The purpose of a hub is to regenerate and retime network signals. This is done at the bit level to a large number of hosts (e.g. 4, 8, or even 24) using a process known as concentration. You will notice that this definition is very similar to the repeater's, which is why a hub is also known as a mul ...
IntroductiontoInform.. - Home (www.dginter.net)
... • Barney Cell Tower to Barney’s cell using SMS. ...
... • Barney Cell Tower to Barney’s cell using SMS. ...
ppt
... • Operate as a repeater – Broadcast an incoming frame to all ports, except for the ingress port – Like having a longer Ethernet cable that all the hosts tap into – All ports are on single collision domain! ...
... • Operate as a repeater – Broadcast an incoming frame to all ports, except for the ingress port – Like having a longer Ethernet cable that all the hosts tap into – All ports are on single collision domain! ...
Connectrix B-Series Management Simplified and Automated Network Management
... SAN and IP Storage Networking environment, such as: Real-time and historical performance data reporting: Organizations gain visibility into in-depth performance measures and historical data for advanced troubleshooting and performance management. Network time and scope: Administrators can set all da ...
... SAN and IP Storage Networking environment, such as: Real-time and historical performance data reporting: Organizations gain visibility into in-depth performance measures and historical data for advanced troubleshooting and performance management. Network time and scope: Administrators can set all da ...
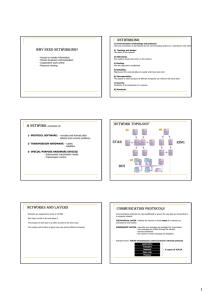
WHY NEED NETWORKING? NETWORKING NETWORK
... be grouped logically, without regard to physical location. ...
... be grouped logically, without regard to physical location. ...
Career Highlights - University of the Pacific
... Engineer III/Broadband Engineering Collaborated on the development, test, and support of DSL test bed project as part of SMART building technology. Assisted network engineers with provisioning and turn up of IAD and dedicated data lines. Bundled local, long distance, and data services using the CISC ...
... Engineer III/Broadband Engineering Collaborated on the development, test, and support of DSL test bed project as part of SMART building technology. Assisted network engineers with provisioning and turn up of IAD and dedicated data lines. Bundled local, long distance, and data services using the CISC ...
Cancer site-specific multidisciplinary team
... CANCER SITE SPECIFIC AND SPECIALIST SERVICES LEAD CLINICIANS The Lead Clinicians will support the Network Advisory Groups and will be expected to work with the Network Chair, Lead Clinician and Directors to ensure: The continued development of the tumour site specific cancers clinical networks R ...
... CANCER SITE SPECIFIC AND SPECIALIST SERVICES LEAD CLINICIANS The Lead Clinicians will support the Network Advisory Groups and will be expected to work with the Network Chair, Lead Clinician and Directors to ensure: The continued development of the tumour site specific cancers clinical networks R ...
Analyze Your Data Network, Solve Problems Faster with
... with PacketPortal™ and Wireshark Wireshark, the world’s most popular protocol analyzer, can resolve the most complex and difficult-to-find network, data, VoIP, and quality-of-experience impacting issues. Now, breakthrough PacketPortal technology from Viavi Solutions™ extends those capabilities and l ...
... with PacketPortal™ and Wireshark Wireshark, the world’s most popular protocol analyzer, can resolve the most complex and difficult-to-find network, data, VoIP, and quality-of-experience impacting issues. Now, breakthrough PacketPortal technology from Viavi Solutions™ extends those capabilities and l ...
18th International Conference on Transparent Optical Networks
... Fiber-wireless networks that rely on the collaborative use of both fiber-based and wireless communication technologies are currently turning into a highly important research area in view of the forthcoming era of 5G mobile networks. The FiWi communication paradigm aims to equip future networks with ...
... Fiber-wireless networks that rely on the collaborative use of both fiber-based and wireless communication technologies are currently turning into a highly important research area in view of the forthcoming era of 5G mobile networks. The FiWi communication paradigm aims to equip future networks with ...
ppt - CSE
... Latest technology excavation: Wireless & Wired network Fault analysis and solution in different levels Software skills with routing & switching technologies, AutoCAD, SpatialNet etc. Hardware skills of rollout, integration and operations with ...
... Latest technology excavation: Wireless & Wired network Fault analysis and solution in different levels Software skills with routing & switching technologies, AutoCAD, SpatialNet etc. Hardware skills of rollout, integration and operations with ...