POSITION DESCRIPTION
... Ability to communicate effectively and maintain working relationships with department heads, other City employees, outside vendors and the public; Ability to prepare accurate and reliable reports containing findings, recommendations and conclusions on network hardware/software; Ability to train othe ...
... Ability to communicate effectively and maintain working relationships with department heads, other City employees, outside vendors and the public; Ability to prepare accurate and reliable reports containing findings, recommendations and conclusions on network hardware/software; Ability to train othe ...
Networking
... • Ex: file servers, web servers, data base servers • Client - to get services from those servers. • Ex: web client • Protocols - A protocol is an agreement (rules) between the communicating parties on how communication is proceed. • Ex: TCP/IP suite • Transmission media – to transfer data between tw ...
... • Ex: file servers, web servers, data base servers • Client - to get services from those servers. • Ex: web client • Protocols - A protocol is an agreement (rules) between the communicating parties on how communication is proceed. • Ex: TCP/IP suite • Transmission media – to transfer data between tw ...
Computer Confluence 6/e
... Fiber-Optic: far faster than any other technology. However, fiberoptic wiring is still only available in a small number of locations. • 1 FO cable can transmit the equivalent of 10,000 copper (e.g. cable) cables ...
... Fiber-Optic: far faster than any other technology. However, fiberoptic wiring is still only available in a small number of locations. • 1 FO cable can transmit the equivalent of 10,000 copper (e.g. cable) cables ...
WhatsUp® Gold 2017 BasicView Edition
... WhatsUp Gold automatically generates Layer 2/3 network maps of your core infrastructure, Windows® infrastructure, servers, printers and more. The unique interactive network map displays your entire IT environment from end-to-end, quickly showing the status of every device and letting you see your en ...
... WhatsUp Gold automatically generates Layer 2/3 network maps of your core infrastructure, Windows® infrastructure, servers, printers and more. The unique interactive network map displays your entire IT environment from end-to-end, quickly showing the status of every device and letting you see your en ...
JOB DESCRIPTION NETWORK ADMINISTRATOR
... environments, experience with network management utilities. • Certification in network operating system’s software, other appropriate hardware certifications such as Cisco, or any equivalent combination of training, certification, and/or experience which provides the required knowledge, skills, and ...
... environments, experience with network management utilities. • Certification in network operating system’s software, other appropriate hardware certifications such as Cisco, or any equivalent combination of training, certification, and/or experience which provides the required knowledge, skills, and ...
1- A well-structured document usually contains a number of clues
... 8- transceivers, perform both the sending and receiving of signals (T) 9- (WANs) connect together two or more LANs that are geographically separated. (T) 10-Messages between nodes are sent in one continuous stream and no need to broken up into small chunks called frames (F) 11- A repeater increases ...
... 8- transceivers, perform both the sending and receiving of signals (T) 9- (WANs) connect together two or more LANs that are geographically separated. (T) 10-Messages between nodes are sent in one continuous stream and no need to broken up into small chunks called frames (F) 11- A repeater increases ...
Chapter 2
... • Transceivers sense that a signal is present and will not send from their connected station • If two signals are on the line at once, neither signal will make sense and a collision occurs • When a collision is detected, the host interface aborts transmission and waits (how long?) for the line to be ...
... • Transceivers sense that a signal is present and will not send from their connected station • If two signals are on the line at once, neither signal will make sense and a collision occurs • When a collision is detected, the host interface aborts transmission and waits (how long?) for the line to be ...
tutorial 1 - Portal UniMAP
... lnetwork layer can operate without knowledge of other layers, or of the package itself. Instead, the layers use specific headers; each layer only pays attention to its own header’s directions. The layers then pass the package on to an adjacent layer accordingly. This process begins with the sending ...
... lnetwork layer can operate without knowledge of other layers, or of the package itself. Instead, the layers use specific headers; each layer only pays attention to its own header’s directions. The layers then pass the package on to an adjacent layer accordingly. This process begins with the sending ...
BT International Corporate Presentation
... • Building high-capacity, scalable data centric networks that are low cost… – Simplifying the network architecture – Lowering equipment costs – Lowering operational costs ...
... • Building high-capacity, scalable data centric networks that are low cost… – Simplifying the network architecture – Lowering equipment costs – Lowering operational costs ...
No Slide Title - Institute of Technology Sligo
... traffic throughput host/client computer speeds (for example, network interface cards and hard drive access speeds). ...
... traffic throughput host/client computer speeds (for example, network interface cards and hard drive access speeds). ...
What is the internet - New Mexico State University
... * a collection of resources that can be reached from those networks. ...
... * a collection of resources that can be reached from those networks. ...
Centre for Defence Communications and Information Networking
... Information Networking (CDCIN) at the University of Adelaide is Australia’s leading university based concentration of defence network analysis capability. CDCIN focusses on the modelling, measurement and management of networked systems, enhancing the robustness, efficiency and effectiveness of exist ...
... Information Networking (CDCIN) at the University of Adelaide is Australia’s leading university based concentration of defence network analysis capability. CDCIN focusses on the modelling, measurement and management of networked systems, enhancing the robustness, efficiency and effectiveness of exist ...
Rex Spell - rabidcat.org
... Planned SONET ring using Cisco ONS 15454 equipment for OTJAG connection to the Pentagon Metro Area Network. Implemented OSPF and QoS changes to client’s network in order to reduce their routing table and improve video conferencing abilities. Designed next generation DWDM network for a large military ...
... Planned SONET ring using Cisco ONS 15454 equipment for OTJAG connection to the Pentagon Metro Area Network. Implemented OSPF and QoS changes to client’s network in order to reduce their routing table and improve video conferencing abilities. Designed next generation DWDM network for a large military ...
HyperText Transfer Protocol
... Session Layer Controls the dialogues/connections (sessions) between computers. It establishes, manages and terminates the connections between the local and remote application. ...
... Session Layer Controls the dialogues/connections (sessions) between computers. It establishes, manages and terminates the connections between the local and remote application. ...
CH07 - Cameron School of Business
... • There have been many network security problems - networks are a tempting target for mischief and fraud • An organization has to be concerned about… – Proper identification of users and authorization of network access – The control of access, and the protection of data integrity ...
... • There have been many network security problems - networks are a tempting target for mischief and fraud • An organization has to be concerned about… – Proper identification of users and authorization of network access – The control of access, and the protection of data integrity ...
physcial_sci_networks_part2
... • Need to trade off the strength of security with the practicality of the measures – Users when faced with a complex process may attempt to undermine the system ...
... • Need to trade off the strength of security with the practicality of the measures – Users when faced with a complex process may attempt to undermine the system ...
ITT04103-Lecture-1
... transmitted from one direction to the other. The terminals have ability to either receives or sends out the data. However, sending and receiving can not be done at same time. For example; FAX (it can sends or receives letter but not in same time) and Walkie- ...
... transmitted from one direction to the other. The terminals have ability to either receives or sends out the data. However, sending and receiving can not be done at same time. For example; FAX (it can sends or receives letter but not in same time) and Walkie- ...
Slide 1
... • How to shape the technical architecture? • Pervasive, many cyberinfrastructures, constantly evolving/changing capabilities • How to customize CI to particular S&E domains ...
... • How to shape the technical architecture? • Pervasive, many cyberinfrastructures, constantly evolving/changing capabilities • How to customize CI to particular S&E domains ...
iVMS - IneoQuest
... • Services categorized by program type (SD, HD, VOD, etc.) management up-to-date on the daily performance of the network. • Northbound interface to third-party NMS/OSS systems • SCTE-35 events allows users to see incoming cue tone traps • Assign user privileges for added security ...
... • Services categorized by program type (SD, HD, VOD, etc.) management up-to-date on the daily performance of the network. • Northbound interface to third-party NMS/OSS systems • SCTE-35 events allows users to see incoming cue tone traps • Assign user privileges for added security ...
Part I: Introduction
... Networking: A Top Down Approach Featuring the Internet, Third Edition, J.F. Kurose and K.W. Ross, AddisonWesley, ISBN: 0-321-22735-2. ...
... Networking: A Top Down Approach Featuring the Internet, Third Edition, J.F. Kurose and K.W. Ross, AddisonWesley, ISBN: 0-321-22735-2. ...
Sensor Networks
... Intelligence have to Sensor Networks? Problem: Randomly distributed sensor network, low power nodes, remote monitoring in a large scale environment Power efficiency Maximize Sensory function ...
... Intelligence have to Sensor Networks? Problem: Randomly distributed sensor network, low power nodes, remote monitoring in a large scale environment Power efficiency Maximize Sensory function ...
Introduction to Network Simulators
... ◦ IT Guru Network Planner helps enterprises plan their network for new applications or technologies. ◦ SP Guru Network Planner and SP Guru Transport Planner optimize service provider network designs for capacity, cost, QoS, and survivability. ◦ Sentinel is OPNET's network configuration auditing solu ...
... ◦ IT Guru Network Planner helps enterprises plan their network for new applications or technologies. ◦ SP Guru Network Planner and SP Guru Transport Planner optimize service provider network designs for capacity, cost, QoS, and survivability. ◦ Sentinel is OPNET's network configuration auditing solu ...
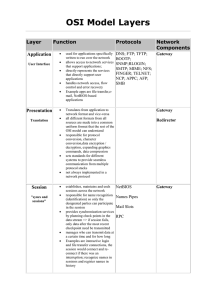
OSI Model Layers
... sets standards for different systems to provide seamless communication from multiple protocol stacks not always implemented in a network protocol establishes, maintains and ends sessions across the network responsible for name recognition (identification) so only the designated parties can participa ...
... sets standards for different systems to provide seamless communication from multiple protocol stacks not always implemented in a network protocol establishes, maintains and ends sessions across the network responsible for name recognition (identification) so only the designated parties can participa ...
Network Topology Bus Topology Bus topology uses a common
... pronunciation in Australia and Canada) is a computer whose software and hardware are usually tailored to the tasks of routing and forwarding information. For example on the internet information gets routed to different places using routers. Routers connect two or more logical subnets, which do not n ...
... pronunciation in Australia and Canada) is a computer whose software and hardware are usually tailored to the tasks of routing and forwarding information. For example on the internet information gets routed to different places using routers. Routers connect two or more logical subnets, which do not n ...