What are the three basic LAN topologies? 2. What common WAN
... What network model draws a clear distinction between devices that share their resources and devices that do not? ...
... What network model draws a clear distinction between devices that share their resources and devices that do not? ...
Computer Network
... • the Internet is a global public network facilitating all sorts of services; the Internet is the largest world-wide network • Like in smaller networks, resources are shared over the Internet using services ...
... • the Internet is a global public network facilitating all sorts of services; the Internet is the largest world-wide network • Like in smaller networks, resources are shared over the Internet using services ...
Network Notes - w w w .conta.uom .gr
... Distributed Processing • more than one processor is used to perform a task • the processors are interconnected and communicate with each other • architecture is multiple computers distributed throughout the system interconnected through networks using communications lines ...
... Distributed Processing • more than one processor is used to perform a task • the processors are interconnected and communicate with each other • architecture is multiple computers distributed throughout the system interconnected through networks using communications lines ...
ASSIGNMENT #3
... Routers use a combination of hardware and software to forward data packets to their destination on the internet. They are more efficient and sophisticated than bridges and switches. They can divide large networks into logical segments called Subnets on the basis of IP addressing scheme. A router can ...
... Routers use a combination of hardware and software to forward data packets to their destination on the internet. They are more efficient and sophisticated than bridges and switches. They can divide large networks into logical segments called Subnets on the basis of IP addressing scheme. A router can ...
Appendix C Computer Networking
... • Use: This topology is useful in LANs. • Advantages: – It does not rely on central host. – The connecting wire, cable, or optical fiber forms a closed loop. Data are passed along the ring from one computer to another and always flow in one direction. The message is regenerated and passed to the nex ...
... • Use: This topology is useful in LANs. • Advantages: – It does not rely on central host. – The connecting wire, cable, or optical fiber forms a closed loop. Data are passed along the ring from one computer to another and always flow in one direction. The message is regenerated and passed to the nex ...
Pres 1 Protocol Architectures
... • Logic needed to support various applications • Each type of application (file transfer, remote access) requires different software on this layer ...
... • Logic needed to support various applications • Each type of application (file transfer, remote access) requires different software on this layer ...
Appendix 5 to the TD – Environment Description and the
... Appendix 5 to the TD – Environment Description and the Cooperation of the Contracting Entity and the Bidder a) Cooperation The Contracting Entity shall provide to the Bidder (Supplier) the following at regular pricelist prices: Premises for the placement of the (core) BRS Information System. Cab ...
... Appendix 5 to the TD – Environment Description and the Cooperation of the Contracting Entity and the Bidder a) Cooperation The Contracting Entity shall provide to the Bidder (Supplier) the following at regular pricelist prices: Premises for the placement of the (core) BRS Information System. Cab ...
Quality Of Service
... Mean Opinion Score (MOS) provides a simple listening quality scale the represents the user experience ...
... Mean Opinion Score (MOS) provides a simple listening quality scale the represents the user experience ...
Introduction to Computers
... Main frame Supercomputer Distributed or Grid Computing Server Mini-computer ...
... Main frame Supercomputer Distributed or Grid Computing Server Mini-computer ...
Abstract - PG Embedded systems
... Channel Allocation and Routing in Hybrid Multichannel Multiradio Wireless Mesh Networks ...
... Channel Allocation and Routing in Hybrid Multichannel Multiradio Wireless Mesh Networks ...
CSCI 1200 / ASSC 1000
... Telecommunications • long distance, electronic communications. • protocol : rules. ...
... Telecommunications • long distance, electronic communications. • protocol : rules. ...
Network Security
... (NAT) (continued) • These IP addresses are not assigned to any specific user or organization; anyone can use them on their own private internal network ...
... (NAT) (continued) • These IP addresses are not assigned to any specific user or organization; anyone can use them on their own private internal network ...
Cognitive Networking
... confidential information may be stolen if message pass through bad communication channel ◦ Increase number of mobile device ...
... confidential information may be stolen if message pass through bad communication channel ◦ Increase number of mobile device ...
Trading Power Savings for Blocking Probability in Dynamically
... In those networking scenarios (e.g., the stationary/mobile wireless paradigm) where limited energy storage capabilities is a limiting factor, power efficiency has been studied extensively for a long time. In the last few years, the steadily growing power consumption figures of ICT [1][2] along with ...
... In those networking scenarios (e.g., the stationary/mobile wireless paradigm) where limited energy storage capabilities is a limiting factor, power efficiency has been studied extensively for a long time. In the last few years, the steadily growing power consumption figures of ICT [1][2] along with ...
Hopfield networks
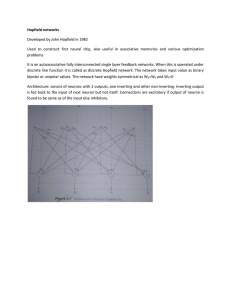
... Developed by John Hopfield in 1982 Used to construct first neural chip, also useful in associative memories and various optimization problems It is an autoassociative fully interconnected single layer feedback networks. When this is operated under discrete line function it is called as discrete Hopf ...
... Developed by John Hopfield in 1982 Used to construct first neural chip, also useful in associative memories and various optimization problems It is an autoassociative fully interconnected single layer feedback networks. When this is operated under discrete line function it is called as discrete Hopf ...
pres
... Packet Capturing (pcap) • Kernel modules – passively capture network traffic and pass them to user space processes through a well-defined Application Programming Interface (API) ...
... Packet Capturing (pcap) • Kernel modules – passively capture network traffic and pass them to user space processes through a well-defined Application Programming Interface (API) ...
Antenna for 2G/3G/4G modem
... TOSIBOX automatically connects the network devices over the Internet in minutes, with a flexible and scalable system Lower IT costs, lower capital cost, lower maintenance cost, faster connectivity to end-users ...
... TOSIBOX automatically connects the network devices over the Internet in minutes, with a flexible and scalable system Lower IT costs, lower capital cost, lower maintenance cost, faster connectivity to end-users ...
Monitoring Grid Services - Informatics Homepages Server
... Benefits of Pull (Cont.) The Pull model is based on distributed intelligence to the asset site - it becomes automated. Using machine-to-machine communications with connected sensors and autonomic computing the asset does self-diagnostics, self maintain and repair, re-routes energy flows, schedu ...
... Benefits of Pull (Cont.) The Pull model is based on distributed intelligence to the asset site - it becomes automated. Using machine-to-machine communications with connected sensors and autonomic computing the asset does self-diagnostics, self maintain and repair, re-routes energy flows, schedu ...
Eric Kha Professor Shin 4/13/15 Chapter 8 PowerPoint Answer
... baseband) as well as protocols (IP addresses, domain name servers, and packetization). ...
... baseband) as well as protocols (IP addresses, domain name servers, and packetization). ...
Network Components Presentation
... Now it can use the address information in each packet to route data efficiently (either directing it back to the segment it came from or on to the other segment). ...
... Now it can use the address information in each packet to route data efficiently (either directing it back to the segment it came from or on to the other segment). ...
tutorial 1 - UniMAP Portal
... 8. (a) What universal set of communication services is provided by TCP/IP? (b) How is independence from underlying network technologies achieved? (c) What economies of scale result from (a) and (b)? 9. What difference does it make to the network layer if the underlying data link layer provides a con ...
... 8. (a) What universal set of communication services is provided by TCP/IP? (b) How is independence from underlying network technologies achieved? (c) What economies of scale result from (a) and (b)? 9. What difference does it make to the network layer if the underlying data link layer provides a con ...