* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Week 6 - cda college
Asynchronous Transfer Mode wikipedia , lookup
Distributed firewall wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Internet protocol suite wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Computer network wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Peer-to-peer wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
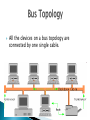
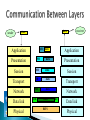
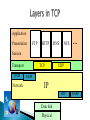
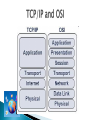
A collection of autonomous computers interconnected by a single technology. Two computers are said to be interconnected if they are able to exchange information. Interconnect machines. Maintain data confidentiality, data integrity, and system accessibility. Support growth by allowing more and more computers, or nodes, to join in (scalability). Support increases in geographical coverage. Is not a single network but a network of networks World is complex – Network representations are also complex – but indeed we can gain important information: How the infrastructure is of a road/electrical power grid is? ◦ Connections/behaviours ◦ Mark Lombardi: tracked and mapped global financial fiascos in the 1980s and 1990s from public sources, such as news articles How? Studied connections between political entities and financial corporations/institutions. Reading connections can see things that are not obvious by just reading articles. Lombardi showed some people from the Department of Homeland Security at an exhibition. Connections (which were not new) but may be useful for security reasons. This is another example of data in HP labs showing email communication between their researchers. If people exchanged a number of emails they get a grey edge. Black edges represent the formal organization, who reports to whom. Result of study: Email communication is more likely between people that are close to each other in the organizational hierarchy. This is Facebook network example of a single account. In automated way, a network layout is created showing ties between people in your network and different colors for people You met in different ways (e.g., through school, work etc.) In this way you can understand some things about this person’s personal life. Finally, this is a network of recipe ingredients. Analyzed ten of thousands recipes to see which ingredients go well together. In this network you can divide the ingredients into communities - savories ingredients and sweeter ingredients. On top there is a small community of mix drinks, e.g., lime juice. Each node needs one interface for each link. (a) point-to-point (b) multiple-access Geographical coverage and scalability are limited. Transmission technology ◦ Broadcast links ◦ Point – to – point links A single communication channel that is shared by all the machines on the networks Packets (short messages) sent by any machine are received by all the others The machines ignored or processes the packet from the address field Broadcasting: addressing a packet to all destinations Multicasting: transmission to a subset of the machines Unicasting: one sender and one receiver Consist of many connections between individual pairs of machines To go from the source to the destination, a packet may have first visit one or more intermediate machines Often multiple routes, of different lengths, are possible ◦ Find the good ones As a general rule ◦ Smaller geographically localized networks tend to use broadcasting ◦ Large networks usually are point – to -point Defines the way in which computers, printers, and other devices are connected Describes the layout of the wire and devices as well as the paths used by data transmissions. This topology connects all devices to each other for redundancy and fault tolerance It is used in WANs to interconnect LANs and for mission critical networks (banks, financial institutions, etc.) Implementing the mesh topology is expensive and difficult All the devices on a bus topology are connected by one single cable. The star topology is the most commonly used architecture in Ethernet LANs. Larger networks use the extended star topology also called tree topology. When used with network devices that filter frames or packets, like bridges, switches, and routers, this topology significantly reduces the traffic on the wires by sending packets only to the wires of the destination host. A frame travels around the ring, stopping at each node. If a node wants to transmit data, it adds the data as well as the destination address to the frame. The frame then continues around the ring until it finds the destination node, which takes the data out of the frame. Types: Single ring – All the devices share a single cable Dual ring – Allows data to be sent in both directions and provides redundancy Physical Media Network Devices Computers Protocols Services Twisted Pair Coaxial Fiber Optics Wireless Transmissions Hub Switches ( Level 2 and 3 ) Routers Wireless Access Points Modems NIC’s End Devices: Acts as a source/destination. For message transmitting or receiving. Server: In a client/server network environment, network services are located in a dedicated computer whose only function is to respond to the requests of clients. The server contains file sharing, http and other services that are continuously available to respond to client requests. Client: Our computers. We request a service from a server (ex. We log into gmail to check our email ) A protocol, in contrast, is a set of rules governing the format and meaning of the packets, or messages that are exchanged by the peer entities within a layer. Entities use protocols to implement their service definitions. They are free to change their protocols at will, provided they do not change the service visible to their users. TCP, UDP, IP, X.25, ICMP, IPSec DHCP - Dynamic Host Configuration Protocol DNS – Domain Name System HTTP - Hypertext Transfer Protocol SSH – Secure Shell Telnet SNMP - Simple Network Management Protocol SMTP - Simple Mail Transfer Protocol FTP – File Transfer Protocol IRC – Internet Relay Chat POP – Post Office Protocol To interconnect two or more networks, one needs a gateway or router. Host-tohost connectivity is only possible if there’s a uniform addressing scheme and a routing mechanism. Messages can be sent to a single destination (unicast), to multiple destinations (multicast), or to all possible destinations (broadcast). Divide time into equal-sized quanta and assign each them to flows on the physical link in round-robin fashion. Flows are transmitted simultaneously on the link, but each one uses a different frequency. Flows are transmitted simultaneously on the link, but each one uses a different coding scheme. For a chosen group of nodes, a unique coding scheme can be used. Each bit is encoded in multiple pulses. Multiple senders may use the same time slots with different coding. Flow is broken into packets and sent to a switch, which can deal with the arriving packets according to the switch policy (FIFO, round-robin, etc). Computer A Computer B queue switch Computer C Computer networks can be classified according to their geographical coverage: In Interconnecting multiple networks (internetworking), we are interested in the seamless integration of all these levels. Have in mind that different levels use different technologies! • LAN: local area network • WLAN: wireless local area network • MAN: metropolitan area network • WAN: wide area network Privately-owned networks Within a single building or campus of up to a few kilometers in size Covers a city A large antenna send the signal to the host Large geographical area Often a country or continent Application The protocol stack: The idea behind the model: Break up the design to make implementation simpler. Each layer has a well-defined function. Layers pass to one another only the information that is relevant at each level. Communication happens only between adjacent layers. Presentation Session Transport Network Data link Physical • Physical: Transmit raw bits over the medium. • Data Link: Implements the abstraction of an error free medium (handle losses, duplication, errors, flow control). • Network: Routing and Addressing. IP • Transport: Break up data into chunks, send them down the protocol stack, receive chunks, put them in the right order, pass them up. • Session: Establish connections between different users and different hosts. • Presentation: Handle syntax and semantics of the info, such as encoding, encrypting. • Application: Protocols commonly needed by applications (cddb, http, ftp, telnet, etc). sender receiver data data AH Application PH Presentation data Application data Presentation Session SH data Session Transport TH data Transport Network NH data Network Data link Physical DH data BITS DT Data link Physical Application Presentation FTP HTTP DNS NFS … Session Transport ICMP Network TCP UDP IGMP IP ARP Data link Physical RARP Questions??