The Internet
... – have a way to address one another. – use a common language or a protocol to organize the exchange of messages. ...
... – have a way to address one another. – use a common language or a protocol to organize the exchange of messages. ...
NetworkConcepts
... A bridge is a device that connects different networks together, e.g. connecting an electrical network to an optical network, or a wired network to a wireless network. A router is a sophisticated device that connects different networks. Network data is routed to different networks based on the rules ...
... A bridge is a device that connects different networks together, e.g. connecting an electrical network to an optical network, or a wired network to a wireless network. A router is a sophisticated device that connects different networks. Network data is routed to different networks based on the rules ...
ICDL Module 1 Concepts Information Technology
... processing speed. The capacity of a modern mainframe can be hundreds or even thousands of times that of a modern personal computer. Cost: Mainframes are also the most expensive machines in terms of both initial cost and maintenance. A mainframe can cost millions of Rands. Typical users: Because the ...
... processing speed. The capacity of a modern mainframe can be hundreds or even thousands of times that of a modern personal computer. Cost: Mainframes are also the most expensive machines in terms of both initial cost and maintenance. A mainframe can cost millions of Rands. Typical users: Because the ...
CIS484-FIREWALL
... through file sharing (like Kazaa or Gnucleus) or through direct download of a malicious program. Firewalls can't prevent this - only a good anti-virus software program can. ...
... through file sharing (like Kazaa or Gnucleus) or through direct download of a malicious program. Firewalls can't prevent this - only a good anti-virus software program can. ...
Computer networks, data communication and the Internet
... definition • When 2 computer systems communicate via network, they do that by exchanging messages. • The structure of network messages varies from network to network. • Thus the message structure in a particular network is agreed upon a priori and is described in a set of rules, each defined in a pr ...
... definition • When 2 computer systems communicate via network, they do that by exchanging messages. • The structure of network messages varies from network to network. • Thus the message structure in a particular network is agreed upon a priori and is described in a set of rules, each defined in a pr ...
Power point
... Redirection Attack • Suppose we can guess destination IP in encrypted packet • Flip bits to change IP to Evil 2, send it to AP – Tricks to adjust IP checksum (in paper) ...
... Redirection Attack • Suppose we can guess destination IP in encrypted packet • Flip bits to change IP to Evil 2, send it to AP – Tricks to adjust IP checksum (in paper) ...
SIP over identifier/locator splitted next generation - DCA
... Phoenix Park, South Korea, 18/02/2008 ...
... Phoenix Park, South Korea, 18/02/2008 ...
Firewalls
... • Routers may implement some security functionality – Packet filtering through the use of access control lists – Reducing load on other devices – Screening traffic with suspicious IP addresses to protect against spoofing – Egress filtering ...
... • Routers may implement some security functionality – Packet filtering through the use of access control lists – Reducing load on other devices – Screening traffic with suspicious IP addresses to protect against spoofing – Egress filtering ...
circuit-level gateway
... • In days of old, brick walls were built between buildings in apartment complexes so that if a fire broke out, it would not spread from one building to another • Quite naturally, these walls were called firewalls • Today, when a private network (i.e., intranet) is connected to a public network (i.e. ...
... • In days of old, brick walls were built between buildings in apartment complexes so that if a fire broke out, it would not spread from one building to another • Quite naturally, these walls were called firewalls • Today, when a private network (i.e., intranet) is connected to a public network (i.e. ...
Oracle9i Security
... Anyone doing business in Europe Reasonable steps to secure from unauthorized access ...
... Anyone doing business in Europe Reasonable steps to secure from unauthorized access ...
OWASP`s Ten Most Critical Web Application Security Vulnerabilities
... Not Network Security Securing the “custom code” that drives a web application ...
... Not Network Security Securing the “custom code” that drives a web application ...
irewall Presentation F Mike Shinn Casey Priester
... • Employee goes to trusted website, which has link to infected website, employees computer is infected ...
... • Employee goes to trusted website, which has link to infected website, employees computer is infected ...
The future solutions and technologies of public safety communications
... systems are constantly monitoring critical traffic having capabilities for using alternative routes if data traffic problems are encountered in the network. [1] Operational tasks and working methods in organizations have evolved and changed over the years. Various communication devices, software, se ...
... systems are constantly monitoring critical traffic having capabilities for using alternative routes if data traffic problems are encountered in the network. [1] Operational tasks and working methods in organizations have evolved and changed over the years. Various communication devices, software, se ...
Computer Security: Principles and Practice, 1/e
... 1. Protect the United States from terrorist attack 2. Protect the United States against foreign intelligence operations and espionage 3. Protect the United States against cyber-based attacks and high-technology crimes 4. Combat public corruption at all levels 5. Protect civil rights 6. Combat transn ...
... 1. Protect the United States from terrorist attack 2. Protect the United States against foreign intelligence operations and espionage 3. Protect the United States against cyber-based attacks and high-technology crimes 4. Combat public corruption at all levels 5. Protect civil rights 6. Combat transn ...
Penetration Testing Report - Network Intelligence India
... The purpose of the test is to determine security vulnerabilities in the server configurations and web applications running on the servers specified as part of the scope. The tests are carried out assuming the identity of an attacker or a user with malicious intent. At the same time due care is taken ...
... The purpose of the test is to determine security vulnerabilities in the server configurations and web applications running on the servers specified as part of the scope. The tests are carried out assuming the identity of an attacker or a user with malicious intent. At the same time due care is taken ...
CCNPv5 Module 5 Lesson 1
... Router MIB variables can point to entities like routing tables and other security-critical components of a router configuration, so it is very important that custom SNMP community strings are created ...
... Router MIB variables can point to entities like routing tables and other security-critical components of a router configuration, so it is very important that custom SNMP community strings are created ...
ICMP Nuke Attack
... An attacker breaks a message into 3 fragments He sends fragment 1 and 2 to both router and windows. Both accepts the fragments He then sends fragment 2 and 3. The retransmitted fragment 2 is of the same size and offset as the original fragment but different ...
... An attacker breaks a message into 3 fragments He sends fragment 1 and 2 to both router and windows. Both accepts the fragments He then sends fragment 2 and 3. The retransmitted fragment 2 is of the same size and offset as the original fragment but different ...
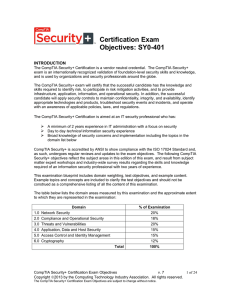
CompTIA Security (SY0-401)
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
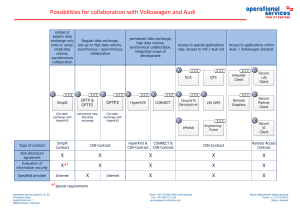
Possibilities for collaboration with Volkswagen
... If users are absent from their workplaces, they have to remove the authorization objects (PKI card or similar) provided to them for performing their activities from the working environment and from the terminal and personally hold them in safe keeping. The commissioning department and/or corporate s ...
... If users are absent from their workplaces, they have to remove the authorization objects (PKI card or similar) provided to them for performing their activities from the working environment and from the terminal and personally hold them in safe keeping. The commissioning department and/or corporate s ...
Enterprise computing systems
... system served, but today, it makes more sense to identify a system by its functions. As a system analyst, part of your job will be to determine which kind of system will best address the organizational problem or opportunity on which you are focusing. ...
... system served, but today, it makes more sense to identify a system by its functions. As a system analyst, part of your job will be to determine which kind of system will best address the organizational problem or opportunity on which you are focusing. ...
Blueprint For Security Chapter 6
... Pose more management issues Vulnerable both to direct attacks and attacks against host operating system ...
... Pose more management issues Vulnerable both to direct attacks and attacks against host operating system ...
William Stallings, Cryptography and Network Security 3/e
... – Router IDs: All routers can be forced to use these loopback IP addresses as source addresses when accessing the servers. – Access Control: The servers can then also be locked down to allow access only from this block of IP addresses. – Accesses from addresses outside this block are denied. ...
... – Router IDs: All routers can be forced to use these loopback IP addresses as source addresses when accessing the servers. – Access Control: The servers can then also be locked down to allow access only from this block of IP addresses. – Accesses from addresses outside this block are denied. ...
Data Communications and Computer Networks Chapter 10
... examines the destination address, and forwards the packet on to a particular telecommunications line. How does a router decide which line to transmit on? A router must select the one transmission line that will best provide a path to the destination and in an optimal manner. Often many possible rout ...
... examines the destination address, and forwards the packet on to a particular telecommunications line. How does a router decide which line to transmit on? A router must select the one transmission line that will best provide a path to the destination and in an optimal manner. Often many possible rout ...
IBM Presentations: Blue Onyx Basic template
... – Enable disk quotas at 4GB, so that someone with mal-intent cannot fill up the disk with extraneous data. – Lock down network access to the FTP server(s) to specific IP addresses. – Enable a strong password policy for each user ID that has access to the FTP server. – Enable account lockout after 5 ...
... – Enable disk quotas at 4GB, so that someone with mal-intent cannot fill up the disk with extraneous data. – Lock down network access to the FTP server(s) to specific IP addresses. – Enable a strong password policy for each user ID that has access to the FTP server. – Enable account lockout after 5 ...