Defense in Depth / Firewalls Presentation
... by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
... by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
Introduction to Database
... Monitor server logs for unauthorized activity Disable unrequired services to reduce risk of unauthorized access ...
... Monitor server logs for unauthorized activity Disable unrequired services to reduce risk of unauthorized access ...
Introduction
... proprietary business terms, intellectual property, and more, you can’t afford to take risks. That’s why DocuSign emphasizes security and always-on availability in everything that we do. Protecting customers is DocuSign’s number one priority, and our comprehensive approach addresses the security, pri ...
... proprietary business terms, intellectual property, and more, you can’t afford to take risks. That’s why DocuSign emphasizes security and always-on availability in everything that we do. Protecting customers is DocuSign’s number one priority, and our comprehensive approach addresses the security, pri ...
Layered Approach Using Conditional Random Fields for Intrusion
... attackers come up with newer and more advanced penetration methods to defeat the ...
... attackers come up with newer and more advanced penetration methods to defeat the ...
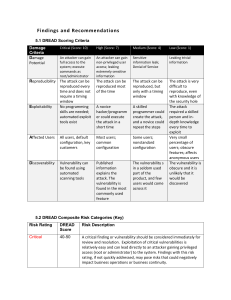
Findings and Recommendations
... resolution within a short time frame. These vulnerabilities can lead to an attacker gaining non-privileged access (standard user) to a system, or the vulnerability can be leveraged to gain elevated level of access. Moderate risk finding or vulnerabilities should be considered once the high critical ...
... resolution within a short time frame. These vulnerabilities can lead to an attacker gaining non-privileged access (standard user) to a system, or the vulnerability can be leveraged to gain elevated level of access. Moderate risk finding or vulnerabilities should be considered once the high critical ...
Defense in Depth / Firewalls Presentation
... by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
... by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
No Slide Title
... – "Fusion" of intrusion-detection data reported by different detectors – The monitoring is also adapted as part of the response, to help pinpoint the problem and its source ...
... – "Fusion" of intrusion-detection data reported by different detectors – The monitoring is also adapted as part of the response, to help pinpoint the problem and its source ...
Firewalls
... – IP address of firewall – IP address of one system in internal network – Number of hops to the firewall ...
... – IP address of firewall – IP address of one system in internal network – Number of hops to the firewall ...
FLAX: Systematic Discovery of Client-Side Validation Vulnerabilities
... Dealing with reflected flows This is done by testing the client-side code independently of the server-side cody by generating candidate inputs that make simple assumptions about the transformations occurring in reflected flows. Subsequently, the tool verifies the assumption by running the candidat ...
... Dealing with reflected flows This is done by testing the client-side code independently of the server-side cody by generating candidate inputs that make simple assumptions about the transformations occurring in reflected flows. Subsequently, the tool verifies the assumption by running the candidat ...
國立聯合大學電子工程學系蕭裕弘
... computers (plus the information and services they provide to their users) that uses the TCP/IP suite of packet switching communications protocols. The Internet is composed of many interconnected computer networks. Each network may link tens, hundreds, or even thousands of computers, enabling them ...
... computers (plus the information and services they provide to their users) that uses the TCP/IP suite of packet switching communications protocols. The Internet is composed of many interconnected computer networks. Each network may link tens, hundreds, or even thousands of computers, enabling them ...
Ch 12 Connectivity - Cisco Networking Academy
... Either topology can use any resource by connecting it to cable or hub. ...
... Either topology can use any resource by connecting it to cable or hub. ...
Using Public Network Infrastructures for UAV Remote Sensing in
... interoperability between heterogeneous and distributed systems. For the servers at ground level wireline communication is utilized (e.g. ADSL) that typically allows for IP communication. If wired communication is not available, directional ad hoc links have to be set up or again public networks (HSP ...
... interoperability between heterogeneous and distributed systems. For the servers at ground level wireline communication is utilized (e.g. ADSL) that typically allows for IP communication. If wired communication is not available, directional ad hoc links have to be set up or again public networks (HSP ...
Detection of Vampire Attack in Wireless Adhoc Network
... Abstract: Mobile ad-hoc network is an infrastructure-less network in which the routing operation play important role in route discovery between communicating nodes. Due to infrastructure-less characteristic of ad-hoc network, it has different issues like routing, MAC layer, security etc. One of them ...
... Abstract: Mobile ad-hoc network is an infrastructure-less network in which the routing operation play important role in route discovery between communicating nodes. Due to infrastructure-less characteristic of ad-hoc network, it has different issues like routing, MAC layer, security etc. One of them ...
11. Building Information Systems
... Essentials of Management Information Systems Chapter 9 The Internet and the New information Technology Infrastructure The Internet: Information Technology Infrastructure for the Digital Firm ...
... Essentials of Management Information Systems Chapter 9 The Internet and the New information Technology Infrastructure The Internet: Information Technology Infrastructure for the Digital Firm ...
Book Title: Confidentiality and Data Access in the Use of Big Data
... where the attacker can retrieve it, or denying access to the data to legitimate users. It is also possible for vulnerabilities to be engineered into operating systems, compilers, network support, and applications by those responsible for developing or maintaining them. For example, a developer may d ...
... where the attacker can retrieve it, or denying access to the data to legitimate users. It is also possible for vulnerabilities to be engineered into operating systems, compilers, network support, and applications by those responsible for developing or maintaining them. For example, a developer may d ...
Attacks and vulnerabilities
... Friel, Steve. SQL Injection Attacks by Example. 2005 (05 March 2005)
Lucas, Julie. The Effective Incident Response Team. Chapter 4. 2003
...
... Friel, Steve. SQL Injection Attacks by Example. 2005
Chapter 7 Local Area Networks: The Basics Data
... Under light loads, this acts similar to CSMA/CD. Under heavy loads, this acts similar to token ring. Powerful access method but again losing out to CSMA/CD. Most common example of reservation protocol is demand priority protocol. ...
... Under light loads, this acts similar to CSMA/CD. Under heavy loads, this acts similar to token ring. Powerful access method but again losing out to CSMA/CD. Most common example of reservation protocol is demand priority protocol. ...
Learn About Secure VPNs
... in the US is now from mobile devices. Additionally, the app industry is continuing to grow (app downloads have increased 15% in 2016), as is, time spent using the apps (total time spent in apps was up by over 150 billion hours totaling almost 900 billion hours in 2016) See link to TechCrunch. All of ...
... in the US is now from mobile devices. Additionally, the app industry is continuing to grow (app downloads have increased 15% in 2016), as is, time spent using the apps (total time spent in apps was up by over 150 billion hours totaling almost 900 billion hours in 2016) See link to TechCrunch. All of ...
layered security.
... • IT@Intel : Enterprise Security http://www.intel.com/content/www/us/en/it-management/intel-it/intelit-managing-it.html • Managing Risk and Information Security: Protect to Enable, by Malcom Harkins, Apress 2012 Link for reference ...
... • IT@Intel : Enterprise Security http://www.intel.com/content/www/us/en/it-management/intel-it/intelit-managing-it.html • Managing Risk and Information Security: Protect to Enable, by Malcom Harkins, Apress 2012 Link for reference ...
USING A RASPBERRY PI AS A MAIN DEVICE IN HIGHER
... cautiously using trial and error practices with the device. By encouraging students to actively participate in development of projects for the Raspberry Pi, it was possible to experience first-hand how a student approached development while having complete control over the hardware and software. Als ...
... cautiously using trial and error practices with the device. By encouraging students to actively participate in development of projects for the Raspberry Pi, it was possible to experience first-hand how a student approached development while having complete control over the hardware and software. Als ...
How to Hack Your Mini Cooper: Reverse Engineering CAN Jason Staggs
... CAN standard does not include inherent security mechanisms for authentication and validation of messages sent to various ECUs over a CAN network. Currently the only data security methods for CAN networks on passenger vehicles are the use of proprietary CAN message IDs and a physical boundary between ...
... CAN standard does not include inherent security mechanisms for authentication and validation of messages sent to various ECUs over a CAN network. Currently the only data security methods for CAN networks on passenger vehicles are the use of proprietary CAN message IDs and a physical boundary between ...
QUESTION DRILL TELECOM 020504 - Answers
... 75. Which of the following denial of service attacks requires three components (source site, bounce site, and target site) to launch the attack? A: A smurf attack requires the three components of a source site, bounce site, and target site to perpetrate its attack. A smurf attack sends a spoofed pin ...
... 75. Which of the following denial of service attacks requires three components (source site, bounce site, and target site) to launch the attack? A: A smurf attack requires the three components of a source site, bounce site, and target site to perpetrate its attack. A smurf attack sends a spoofed pin ...
Network Security Threats CERT Centers, Software Engineering Institute Carnegie Mellon University
... © 2000 by Carnegie Mellon University ...
... © 2000 by Carnegie Mellon University ...