IT2042-UNIT3-Notes
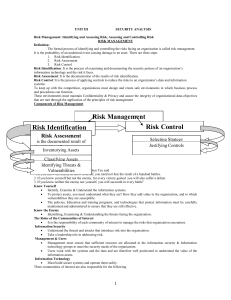
... Serial Number: For hardware devices, the serial number can uniquely identify a specific device. Manufacturer Name: Record the manufacturer of the device or software component. This can be useful when responding to incidents that involve these devices or when certain manufacturers announce specific v ...
... Serial Number: For hardware devices, the serial number can uniquely identify a specific device. Manufacturer Name: Record the manufacturer of the device or software component. This can be useful when responding to incidents that involve these devices or when certain manufacturers announce specific v ...
Saimaa University of Applied Sciences Technology, Lappeenranta Mechanical Engineering and Production Technology
... - Direct and simultaneous access to resources (including valuable information) a great number of users of various categories; - Varity of different hardware and software; - Absence of special protection utilities that could be used in specific computer network. Generally computer network system cons ...
... - Direct and simultaneous access to resources (including valuable information) a great number of users of various categories; - Varity of different hardware and software; - Absence of special protection utilities that could be used in specific computer network. Generally computer network system cons ...
MAC Address Authentication - Faculty Website Directory
... to broadcast the SSID, so anyone can easily join the wireless network. • Change the default SSID. Wireless AP’s have a default SSID set by the factory. Linksys wireless products use Linksys. Change the network's SSID to something unique, and make sure it doesn't refer to the networking products, you ...
... to broadcast the SSID, so anyone can easily join the wireless network. • Change the default SSID. Wireless AP’s have a default SSID set by the factory. Linksys wireless products use Linksys. Change the network's SSID to something unique, and make sure it doesn't refer to the networking products, you ...
Protocols and network security in ICS infrastructures
... From the point of view of security, when a network architecture is being designed it is always advisable to set up a model with differentiation of network segments. Separation of networks into sections with differing functions and purposes makes it possible to apply greater granularity in security m ...
... From the point of view of security, when a network architecture is being designed it is always advisable to set up a model with differentiation of network segments. Separation of networks into sections with differing functions and purposes makes it possible to apply greater granularity in security m ...
Slide 1
... SNAP Supports Spiral Security Insertions to Support Fiscal Constraints MLS Architected-System High ...
... SNAP Supports Spiral Security Insertions to Support Fiscal Constraints MLS Architected-System High ...
Acceptable Guidlines for Technologies and Resources_final word
... ADSB recognizes the benefits that technology can bring to support student learning, staff development, communication with stakeholders, and other administrative and operational activities aligned with the core business functions of the District. All users of the Algoma District School Board (ADSB) i ...
... ADSB recognizes the benefits that technology can bring to support student learning, staff development, communication with stakeholders, and other administrative and operational activities aligned with the core business functions of the District. All users of the Algoma District School Board (ADSB) i ...
Chap 12
... IDS analyzes information it gathers and compares it to a database of known attacks, which are identified by ...
... IDS analyzes information it gathers and compares it to a database of known attacks, which are identified by ...
Intrusion Detection Systems (IDSs): Perspective
... According to a recent study by the Computer Security Institute (CSI) and the Federal Bureau of Investigation (FBI), a staggering 70 percent of organizations surveyed reported a security incident. This figure is up from 42 percent reported in 1996. Taking into account organizations’ reluctance to adm ...
... According to a recent study by the Computer Security Institute (CSI) and the Federal Bureau of Investigation (FBI), a staggering 70 percent of organizations surveyed reported a security incident. This figure is up from 42 percent reported in 1996. Taking into account organizations’ reluctance to adm ...
Intrusion Detection Systems (IDSs): Perspective
... According to a recent study by the Computer Security Institute (CSI) and the Federal Bureau of Investigation (FBI), a staggering 70 percent of organizations surveyed reported a security incident. This figure is up from 42 percent reported in 1996. Taking into account organizations’ reluctance to adm ...
... According to a recent study by the Computer Security Institute (CSI) and the Federal Bureau of Investigation (FBI), a staggering 70 percent of organizations surveyed reported a security incident. This figure is up from 42 percent reported in 1996. Taking into account organizations’ reluctance to adm ...
ALTA Assessment Procedures
... a. Obtain and review change management procedures when technology and business function changes are made. ...
... a. Obtain and review change management procedures when technology and business function changes are made. ...
"rooting"?
... iOS: Many users are lured into jailbreaking to take advantage of apps made available through third party app sources, such as Cydia, which are otherwise banned or not approved by Apple. There is an inherent risk in installing such applications as they are not quality controlled nor have they gone th ...
... iOS: Many users are lured into jailbreaking to take advantage of apps made available through third party app sources, such as Cydia, which are otherwise banned or not approved by Apple. There is an inherent risk in installing such applications as they are not quality controlled nor have they gone th ...
Advanced Topics in Computer Networking
... Year: 2008 Other supplemental material: Lab handouts and other handouts for topics not covered by the textbook. Introduction to the Course: a) Catalog Description (2010-2011 Academic Catalog): This course is a continuation of ECET 36700. Topics include emerging technologies in computer networks and ...
... Year: 2008 Other supplemental material: Lab handouts and other handouts for topics not covered by the textbook. Introduction to the Course: a) Catalog Description (2010-2011 Academic Catalog): This course is a continuation of ECET 36700. Topics include emerging technologies in computer networks and ...
Evoluation of Network Technologies and its Impact on Traffic Engineering Universität Stuttgart
... • Change of Paradigms in the Communication Sector - heterogeneous network technologies, broad spectrum of applications - trend directs to IP-based network and transport protocols - technology push and market pull • Success Factors - time to market - open platforms - user acceptance • Design Processe ...
... • Change of Paradigms in the Communication Sector - heterogeneous network technologies, broad spectrum of applications - trend directs to IP-based network and transport protocols - technology push and market pull • Success Factors - time to market - open platforms - user acceptance • Design Processe ...
DOC
... 06.06 Configure a server for multiple network protocols and frame types. 06.07 Configure a server to handle multiple languages for international applications. 06.09 Describe management issues and procedures for handling multiple servers on a network. 06.10 Install and connect multiple servers (inclu ...
... 06.06 Configure a server for multiple network protocols and frame types. 06.07 Configure a server to handle multiple languages for international applications. 06.09 Describe management issues and procedures for handling multiple servers on a network. 06.10 Install and connect multiple servers (inclu ...
Lecture 4
... to any other is through the central computer. Peer-to-peer architectures are not an option with this topology. • Star networks are still used, but hark back to the mainframe days of heavily centralised computing. ...
... to any other is through the central computer. Peer-to-peer architectures are not an option with this topology. • Star networks are still used, but hark back to the mainframe days of heavily centralised computing. ...
E-Learning
... perform the "traffic directing" functions on the Internet. A data packet is typically forwarded from one router to another through the networks that constitute the internetwork until it reaches its destination node. Fundamentals of Information Systems Security ...
... perform the "traffic directing" functions on the Internet. A data packet is typically forwarded from one router to another through the networks that constitute the internetwork until it reaches its destination node. Fundamentals of Information Systems Security ...
Establish bounds on the total rate of data exfiltration
... uploads some information externally, e.g. to respond to user queries, report sensor readings, or send an email • The Attacker unleashes self-propagating malware, which spreads from infected nodes to clean nodes when they communicate • Infected nodes additionally exfiltrate sensitive data at a rate p ...
... uploads some information externally, e.g. to respond to user queries, report sensor readings, or send an email • The Attacker unleashes self-propagating malware, which spreads from infected nodes to clean nodes when they communicate • Infected nodes additionally exfiltrate sensitive data at a rate p ...
Sponsored by: US Department of Housing and
... Those who implement and properly use security products to protect data Those who collect, input, or otherwise have access to data ...
... Those who implement and properly use security products to protect data Those who collect, input, or otherwise have access to data ...
IPSec
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
PDF
... Object identifier. Values are defined in specific MIB modules. The Event MIB allows you or an NMS to watch over specified objects and to set event triggers based on existence, threshold, and Boolean tests. An event occurs when a trigger is fired; this means that a specified test on an object returns ...
... Object identifier. Values are defined in specific MIB modules. The Event MIB allows you or an NMS to watch over specified objects and to set event triggers based on existence, threshold, and Boolean tests. An event occurs when a trigger is fired; this means that a specified test on an object returns ...
TCP/IP Networks - Northern Kentucky University
... – 1492 or 1500 bytes, depending on ethernet std ...
... – 1492 or 1500 bytes, depending on ethernet std ...