Cisco TrustSec�5.0 - Systemmerkblatt
... secure network access. They show who and what is connecting to the network and mitigate risk through centralized controls over the resources that users and devices can access. The flexible authentication and device-classification functions of Cisco Secure Access enable identity- and contextaware net ...
... secure network access. They show who and what is connecting to the network and mitigate risk through centralized controls over the resources that users and devices can access. The flexible authentication and device-classification functions of Cisco Secure Access enable identity- and contextaware net ...
Skills Assessment – Student Training (Answer Key)
... Instructor Note: Sample scoring and estimated times for each exam part are provided. These can be adjusted by the instructor as necessary to suit the testing environment. Total points for the exam are 100 and total time is estimated at 115 minutes. The instructor may elect to deduct points if excess ...
... Instructor Note: Sample scoring and estimated times for each exam part are provided. These can be adjusted by the instructor as necessary to suit the testing environment. Total points for the exam are 100 and total time is estimated at 115 minutes. The instructor may elect to deduct points if excess ...
A Secure Way to Protect Your Network: IBM
... 3.2.5 Basic logging. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3.2.6 Basic configuration using the command line interface . . 3.2.7 Further configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
... 3.2.5 Basic logging. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3.2.6 Basic configuration using the command line interface . . 3.2.7 Further configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
The Internet of TR-069 Things: One Exploit to
... - Close all open ports to the WAN , accept those which are required and monitored. - Read Misfortune Cookie FAQ at: http://mis.fortunecook.ie ...
... - Close all open ports to the WAN , accept those which are required and monitored. - Read Misfortune Cookie FAQ at: http://mis.fortunecook.ie ...
SnapGear Administration Guide Firmware Version 3.1.5
... Software Product, including all computer programs and documentation, and erasing any copies residing on computer equipment. This Agreement also will automatically terminate if you do not comply with any terms or conditions of this Agreement. Upon such termination you agree to destroy the Software Pr ...
... Software Product, including all computer programs and documentation, and erasing any copies residing on computer equipment. This Agreement also will automatically terminate if you do not comply with any terms or conditions of this Agreement. Upon such termination you agree to destroy the Software Pr ...
motorola solutions wing 5.4.1 cli reference guide
... or otherwise transferred by the user without prior written consent of Motorola Solutions. No right to copy a licensed program in whole or in part is granted, except as permitted under copyright law. The user shall not modify, merge, or incorporate any form or portion of a licensed program with other ...
... or otherwise transferred by the user without prior written consent of Motorola Solutions. No right to copy a licensed program in whole or in part is granted, except as permitted under copyright law. The user shall not modify, merge, or incorporate any form or portion of a licensed program with other ...
Integrating Cisco Press Resources into the
... • Link-state routing raises two concerns: – During the initial discovery process, link-state routing protocols flood the network with LSAs • Significantly decreases the network’s capability to transport data • This is temporary, but noticeable ...
... • Link-state routing raises two concerns: – During the initial discovery process, link-state routing protocols flood the network with LSAs • Significantly decreases the network’s capability to transport data • This is temporary, but noticeable ...
IPv6 and Transition Mechanisms
... Transition Mechanisms - 6DISS Workshop - 5 March 2006 to be dualIPv6 ...
... Transition Mechanisms - 6DISS Workshop - 5 March 2006 to be dualIPv6 ...
HP Jetdirect Print Servers (300X/510X) Administrators Guide ENWW
... print server has no IP address. If the HP Jetdirect print server is not configured with a valid IP address within two minutes after power up, a factory default value of 192.0.0.192 will be automatically assigned. This address must be reconfigured with a valid address for use on your TCP/IP network. ...
... print server has no IP address. If the HP Jetdirect print server is not configured with a valid IP address within two minutes after power up, a factory default value of 192.0.0.192 will be automatically assigned. This address must be reconfigured with a valid address for use on your TCP/IP network. ...
DEPLOYMENT IPV6 OVER IPV4 NETWORK INFRASTRUCTURE Tien Dung Hoang
... or more than two smaller networks. In a big company or in ISP, each department or customer will have a private subnet to increase security and management. 2.1.2 IPv4 limitation IPv4 only supports 32 bits, so IPv4 cannot respond to address requirements on Internet nowadays. Two major issues IPv4 are ...
... or more than two smaller networks. In a big company or in ISP, each department or customer will have a private subnet to increase security and management. 2.1.2 IPv4 limitation IPv4 only supports 32 bits, so IPv4 cannot respond to address requirements on Internet nowadays. Two major issues IPv4 are ...
Configuring Security Access Control Lists
... An implicit deny-all entry exists at the end of each ACL, so you must configure an ACL on each interface that you want to permit connections. Otherwise, the ACE denies all traffic on the interface. ACLs allow you to control network connection setups rather than processing each packet. Such ACLs are ...
... An implicit deny-all entry exists at the end of each ACL, so you must configure an ACL on each interface that you want to permit connections. Otherwise, the ACE denies all traffic on the interface. ACLs allow you to control network connection setups rather than processing each packet. Such ACLs are ...
Lifesize UVC Platform™ Installation and Deployment Guide
... the virtual machine (create a new unique ID). Selecting Duplicate all files so the same virtual machine can be imported again will allow you to create multiple UVC Platform servers. 8. Select Import. 9. Adjust the settings to ensure that the virtual machine meets the vCPU, memory, disk space, and ne ...
... the virtual machine (create a new unique ID). Selecting Duplicate all files so the same virtual machine can be imported again will allow you to create multiple UVC Platform servers. 8. Select Import. 9. Adjust the settings to ensure that the virtual machine meets the vCPU, memory, disk space, and ne ...
IPv6 Infrastructure Security
... • If unique, the address(es) is(are) configured on interface • Note – no DNS automatically configured IPv6 Infrastructure Security v1.1 - Copyright © 2013 Jeffrey L. Carrell ...
... • If unique, the address(es) is(are) configured on interface • Note – no DNS automatically configured IPv6 Infrastructure Security v1.1 - Copyright © 2013 Jeffrey L. Carrell ...
Core of the network
... • Stop pretending that IPv6 does not have any troubles – IPv6 has got many problems – Problems can not be solved by covering them – Unreliable information led to broken trust amongst users. The naked truth is always better than the best dressed lie ...
... • Stop pretending that IPv6 does not have any troubles – IPv6 has got many problems – Problems can not be solved by covering them – Unreliable information led to broken trust amongst users. The naked truth is always better than the best dressed lie ...
PDF - This Chapter (2.12 MB)
... as two endpoints that have activated different channels. When a VTG is enabled to facilitate communications between two or more endpoints with different multicast addresses, a UMS must bridge, or mix, the multicast streams of each channel. In this VTG scenario, the Cisco IPICS sever allocates a loop ...
... as two endpoints that have activated different channels. When a VTG is enabled to facilitate communications between two or more endpoints with different multicast addresses, a UMS must bridge, or mix, the multicast streams of each channel. In this VTG scenario, the Cisco IPICS sever allocates a loop ...
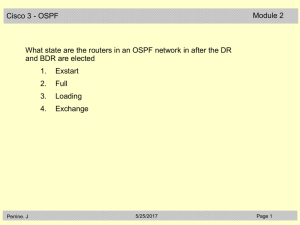
20088-2 CCNA3 3.1-02 Questions OSPF
... The link-state database is stored in a designated router and is accessed by each router in the area as needed. ...
... The link-state database is stored in a designated router and is accessed by each router in the area as needed. ...
Ingate Firewall & SIParator Training
... INVITE (or any SIP Request) Flood in an attempt to slow services or disrupt services ...
... INVITE (or any SIP Request) Flood in an attempt to slow services or disrupt services ...
A. IMS/Internet interworking scenario.
... able to detect this modification. In addition to message integrity, integrity mechanisms always provide some type of proof of data origin. Knowing that a message has not been modified without knowing who initially created the message would be useless. Confidentiality mechanisms keep unauthorized par ...
... able to detect this modification. In addition to message integrity, integrity mechanisms always provide some type of proof of data origin. Knowing that a message has not been modified without knowing who initially created the message would be useless. Confidentiality mechanisms keep unauthorized par ...
PDF-p. 6
... pertaining to these essential IPRs, if any, is publicly available for ETSI members and non-members, and can be found in SR 000 314: "Intellectual Property Rights (IPRs); Essential, or potentially Essential, IPRs notified to ETSI in respect of ETSI standards", which is available from the ETSI Secreta ...
... pertaining to these essential IPRs, if any, is publicly available for ETSI members and non-members, and can be found in SR 000 314: "Intellectual Property Rights (IPRs); Essential, or potentially Essential, IPRs notified to ETSI in respect of ETSI standards", which is available from the ETSI Secreta ...
Advanced VPN Concepts and Tunnel Monitoring
... VPNs (virtual private networks) have emerged as a technology due to their ability to leverage an organization’s existing infrastructure (including the Internet) to both create and augment existing communication links securely. Checkpoint VPNs are based on standard secure protocols defined in the Int ...
... VPNs (virtual private networks) have emerged as a technology due to their ability to leverage an organization’s existing infrastructure (including the Internet) to both create and augment existing communication links securely. Checkpoint VPNs are based on standard secure protocols defined in the Int ...
HP 12500 Switch Series
... provides direct real-time session visibility • Logging: provides local and remote logging of events via SNMP (v2c and v3) and syslog; provides log throttling and log filtering to reduce the number of log events generated • Management interface control: each of the following interfaces can be enabled ...
... provides direct real-time session visibility • Logging: provides local and remote logging of events via SNMP (v2c and v3) and syslog; provides log throttling and log filtering to reduce the number of log events generated • Management interface control: each of the following interfaces can be enabled ...
CN 2015 1-2 - DSpace
... home in which components such as the electrical system, heating and air conditioning system, and plumbing are integrated into the overall design. Taken from the Greek work "Topos" meaning "Place," Specifies the geometric arrangement of the network or a ...
... home in which components such as the electrical system, heating and air conditioning system, and plumbing are integrated into the overall design. Taken from the Greek work "Topos" meaning "Place," Specifies the geometric arrangement of the network or a ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.