MCSA_MCSE Exam 70-29..
... production (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY. You may have other legal rights, ...
... production (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY. You may have other legal rights, ...
Guía de Soluciones: Seguridad
... Utilizando tecnologías como VPNs (Virtual Private Networks), firewalls, sistemas de detección de intrusiones y calidad del servicio (QoS), las organizaciones pueden asegurar la privacidad ■ La seguridad de la red debe considerarse parte de sus estudiantes, proteger su propiedad de todas las decision ...
... Utilizando tecnologías como VPNs (Virtual Private Networks), firewalls, sistemas de detección de intrusiones y calidad del servicio (QoS), las organizaciones pueden asegurar la privacidad ■ La seguridad de la red debe considerarse parte de sus estudiantes, proteger su propiedad de todas las decision ...
Command Line Interface Guide
... assumes that you have read the information about the router and installed the hardware using the Internet Quick Start Guide. The guide is divided into eight parts: Introduction. Describes the features of the Command Line Interface. Advanced Topics. Contains additional information on topics such as i ...
... assumes that you have read the information about the router and installed the hardware using the Internet Quick Start Guide. The guide is divided into eight parts: Introduction. Describes the features of the Command Line Interface. Advanced Topics. Contains additional information on topics such as i ...
Avaya Session Border Controller for Enterprise
... Party Components and the Third Party Terms that apply is available ...
... Party Components and the Third Party Terms that apply is available ...
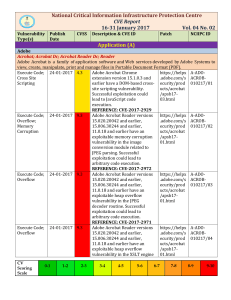
16-31 Jan`17 - National Critical Information Infrastructure Protection
... MuJS is a lightweight Javascript interpreter designed for embedding in other software to extend them ...
... MuJS is a lightweight Javascript interpreter designed for embedding in other software to extend them ...
ESBC Administrator`s Guide
... Understand the network factors which affect quality of service .......................................... 38 ...
... Understand the network factors which affect quality of service .......................................... 38 ...
user manual
... part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmfu ...
... part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmfu ...
Virtual Private Networks
... The terms and conditions for using this software are described in the software license contained in the acknowledgment to your purchase order or, to the extent applicable, to any reseller agreement or end-user purchase agreement executed between you and Juniper Networks. By using this software, you ...
... The terms and conditions for using this software are described in the software license contained in the acknowledgment to your purchase order or, to the extent applicable, to any reseller agreement or end-user purchase agreement executed between you and Juniper Networks. By using this software, you ...
ProSafe VPN Firewall 200 FVX538 Reference Manual
... part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmfu ...
... part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmfu ...
SNMP/MIB Management
... Applications Ware SET PDUs let you invoke controls and actions such as node boots, port boots, and station resets. Most objects allow for control GETs for device monitoring. ...
... Applications Ware SET PDUs let you invoke controls and actions such as node boots, port boots, and station resets. Most objects allow for control GETs for device monitoring. ...
INR11%20-%20OSPF
... If you want to influence the election of DR and BDR with further configurations then do one of the following: Boot up the DR first, followed by the BDR, and then boot all other routers, OR Shut down the interface on all routers, followed by a no shutdown on the DR, then the BDR, and then all oth ...
... If you want to influence the election of DR and BDR with further configurations then do one of the following: Boot up the DR first, followed by the BDR, and then boot all other routers, OR Shut down the interface on all routers, followed by a no shutdown on the DR, then the BDR, and then all oth ...
Brocade ICX Switch Family Data Sheet
... deliver a complete, scalable, and high-performance network solution that supports today’s demanding video, Unified Communications (UC), VDI, and mobile applications. They leverage the innovative Brocade Campus Fabric technology, which provides simplified network deployment and management, scale-out ...
... deliver a complete, scalable, and high-performance network solution that supports today’s demanding video, Unified Communications (UC), VDI, and mobile applications. They leverage the innovative Brocade Campus Fabric technology, which provides simplified network deployment and management, scale-out ...
OSPF
... two current versions in use: – OSPFv2: OSPF for IPv4 networks (RFC 1247 and RFC 2328) – OSPFv3: OSPF for IPv6 networks (RFC 2740) ...
... two current versions in use: – OSPFv2: OSPF for IPv4 networks (RFC 1247 and RFC 2328) – OSPFv3: OSPF for IPv6 networks (RFC 2740) ...
Small Network Equipment 2015 Annual Report
... signed the Voluntary Agreement for Ongoing Improvement to the Energy Efficiency of Small Network Equipment. This agreement is modeled on the successful Voluntary Agreement for Ongoing Improvement to the Energy Efficiency of Set-Top Boxes. The primary objective of the agreement is to increase the ene ...
... signed the Voluntary Agreement for Ongoing Improvement to the Energy Efficiency of Small Network Equipment. This agreement is modeled on the successful Voluntary Agreement for Ongoing Improvement to the Energy Efficiency of Set-Top Boxes. The primary objective of the agreement is to increase the ene ...
29061-ae0
... Access-Request message (sent from GGSN/P-GW to AAA server) .......................................................... 67 Access-Accept (sent from AAA server to GGSN/P-GW) .......................................................................... 69 Accounting-Request START (sent from GGSN/P-GW to AA ...
... Access-Request message (sent from GGSN/P-GW to AAA server) .......................................................... 67 Access-Accept (sent from AAA server to GGSN/P-GW) .......................................................................... 69 Accounting-Request START (sent from GGSN/P-GW to AA ...
29061-bc0
... Access-Request message (sent from GGSN/P-GW to AAA server) .......................................................... 69 Access-Accept (sent from AAA server to GGSN/P-GW) .......................................................................... 71 Accounting-Request START (sent from GGSN/P-GW to AA ...
... Access-Request message (sent from GGSN/P-GW to AAA server) .......................................................... 69 Access-Accept (sent from AAA server to GGSN/P-GW) .......................................................................... 71 Accounting-Request START (sent from GGSN/P-GW to AA ...
XTM 2 and 5 Series
... spamBlocker •Securely, Simply, Detecting Mass Outbreaks in Real-time •How it works: – Detects the repetitive component of each outbreak – Uniquely identifies the DNA of each outbreak – Compares incoming messages with spam DNA in real-time ...
... spamBlocker •Securely, Simply, Detecting Mass Outbreaks in Real-time •How it works: – Detects the repetitive component of each outbreak – Uniquely identifies the DNA of each outbreak – Compares incoming messages with spam DNA in real-time ...
ProSafe Gigabit 8 Port VPN Firewall FVS318G Reference Manual
... part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmfu ...
... part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmfu ...
Unix System Administration
... • Source and stateful routing and failover functions Route traffic more efficiant and faster than regular IP routers. ...
... • Source and stateful routing and failover functions Route traffic more efficiant and faster than regular IP routers. ...
ProSafe VPN Firewall 50 FVS338 Reference Manual
... part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmfu ...
... part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmfu ...
PDF version
... Writing Scripts.......................................................................................................................................35 Console scripting introduction........................................................................................................35 Command... ...
... Writing Scripts.......................................................................................................................................35 Console scripting introduction........................................................................................................35 Command... ...
ITU ngn-fg-book-2 http://Certificate.Moscow
... service level agreement (SLA) is a formal definition of the contractual relationship between service provider and its end user [14]. It specifies what the end user wants and what the supplier commits to provide. It defines the level for the quality of services provided, setting performance objective ...
... service level agreement (SLA) is a formal definition of the contractual relationship between service provider and its end user [14]. It specifies what the end user wants and what the supplier commits to provide. It defines the level for the quality of services provided, setting performance objective ...
PCCE - Cisco Live
... Understanding of the Cisco Unified Wireless Networking for enterprise deployment scenarios. In this course, you will learn the basics of how to install, configure, operate, and maintain a wireless network, both as an add-on to an existing wireless LAN (WLAN) and as a new Cisco Unified Wireless Netwo ...
... Understanding of the Cisco Unified Wireless Networking for enterprise deployment scenarios. In this course, you will learn the basics of how to install, configure, operate, and maintain a wireless network, both as an add-on to an existing wireless LAN (WLAN) and as a new Cisco Unified Wireless Netwo ...
HERE - Lobometrics High Power Outdoor/Indoor Wireless
... • Wireless - IEEE802.11a/b/g wireless client and Access Point; Nsetreme and Nstreme2 proprietary protocols; Wireless Distribution System (WDS) support; virtual AP; 40 and 104 bit WEP; WPA pre-shared key authentication; access control list; authentication on RADIUS server; roaming (for wireless clien ...
... • Wireless - IEEE802.11a/b/g wireless client and Access Point; Nsetreme and Nstreme2 proprietary protocols; Wireless Distribution System (WDS) support; virtual AP; 40 and 104 bit WEP; WPA pre-shared key authentication; access control list; authentication on RADIUS server; roaming (for wireless clien ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.