IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... Allows remote users to safely access resources as if their computer is physically attached to the local network encryption Data being transported on a network A program that runs on a computer to allow or deny traffic between the computer and network to which it is connected Approved offsite storage ...
... Allows remote users to safely access resources as if their computer is physically attached to the local network encryption Data being transported on a network A program that runs on a computer to allow or deny traffic between the computer and network to which it is connected Approved offsite storage ...
IS-Networks
... 1. Star: all computers are connected to a central host 2. Ring: computers are linked by a closed loop 3. Bus: all messages are broadcast to the entire network and each device identifies messages sent to it ...
... 1. Star: all computers are connected to a central host 2. Ring: computers are linked by a closed loop 3. Bus: all messages are broadcast to the entire network and each device identifies messages sent to it ...
sec overview
... Reassembly done by destination host Router overload - packet is dropped TTL - Time to Live field avoids infinite loops (decreased at each hop) ...
... Reassembly done by destination host Router overload - packet is dropped TTL - Time to Live field avoids infinite loops (decreased at each hop) ...
01-intro
... Networks course thought by Srinivasan Seshan at CMU. When slides are obtained from other sources, a reference will be noted on the bottom of that slide. ...
... Networks course thought by Srinivasan Seshan at CMU. When slides are obtained from other sources, a reference will be noted on the bottom of that slide. ...
Review Grid - ctaeir.org
... check mapping of pair is switched Straight through with one wire from wires for faults a different pair at Cable tester both ends Split Pair ...
... check mapping of pair is switched Straight through with one wire from wires for faults a different pair at Cable tester both ends Split Pair ...
ppt - CSE
... Latest technology excavation: Wireless & Wired network Fault analysis and solution in different levels Software skills with routing & switching technologies, AutoCAD, SpatialNet etc. Hardware skills of rollout, integration and operations with different vendors Well-organizing power and coordination ...
... Latest technology excavation: Wireless & Wired network Fault analysis and solution in different levels Software skills with routing & switching technologies, AutoCAD, SpatialNet etc. Hardware skills of rollout, integration and operations with different vendors Well-organizing power and coordination ...
Wi-Fi
... • Used generically when referring to any type of 802.11 network, whether 802.11a, 802.11b, 802.11g, dual-band, etc. The term is promulgated by the Wi-Fi Alliance • Wi-Fi users can roam from their networks to cellular networks. For example, let users begin working at an airport on a laptop via a Wi-F ...
... • Used generically when referring to any type of 802.11 network, whether 802.11a, 802.11b, 802.11g, dual-band, etc. The term is promulgated by the Wi-Fi Alliance • Wi-Fi users can roam from their networks to cellular networks. For example, let users begin working at an airport on a laptop via a Wi-F ...
Jaden Terry CIS 280 Final Network Security From browsing the
... There are many techniques of keeping a computer safe from mentioned attacks, such as Mac address filtering, Firewall, and WPA/WPA2. First, a firewall is a system that controls the incoming and outgoing traffic and determines whether or not packets should be allowed through. In the network layer, a f ...
... There are many techniques of keeping a computer safe from mentioned attacks, such as Mac address filtering, Firewall, and WPA/WPA2. First, a firewall is a system that controls the incoming and outgoing traffic and determines whether or not packets should be allowed through. In the network layer, a f ...
Network Security
... PGP (short for Pretty Good Privacy), created by Philip Zimmermann, is the de facto standard program for secure e-mail and file encryption on the Internet. Its public-key cryptography system enables people who have never met to secure transmitted messages against unauthorized reading and to add digit ...
... PGP (short for Pretty Good Privacy), created by Philip Zimmermann, is the de facto standard program for secure e-mail and file encryption on the Internet. Its public-key cryptography system enables people who have never met to secure transmitted messages against unauthorized reading and to add digit ...
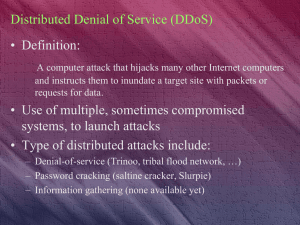
Malwares – Types & Defense
... Can deny by port numbers/IP addr Not flexible Useful where network inside is considered secure ...
... Can deny by port numbers/IP addr Not flexible Useful where network inside is considered secure ...
Network Access Control
... please reply back to this message, leaving the subject line intact, and outline specifically what actions you took. You must take all actions listed in order for us to restore access. Help with these steps can be obtained from the KB article titled "In Windows, how do I rebuild my computer after a s ...
... please reply back to this message, leaving the subject line intact, and outline specifically what actions you took. You must take all actions listed in order for us to restore access. Help with these steps can be obtained from the KB article titled "In Windows, how do I rebuild my computer after a s ...
IP, ATM, Wireless
... IP today • Present networks are based on IPv4 • Packets (called datagrams) – 4 bytes describing IP version and other control, including TOS (type of service, often used to control speed and loss of packets) – 4 bytes: Numbering system for splitting information into different fragments – 4 bytes des ...
... IP today • Present networks are based on IPv4 • Packets (called datagrams) – 4 bytes describing IP version and other control, including TOS (type of service, often used to control speed and loss of packets) – 4 bytes: Numbering system for splitting information into different fragments – 4 bytes des ...
IST 201 - York Technical College
... • Configured router interface that is used to communicate with hosts outside the current segment (network). • Router sends it’s own MAC address. ...
... • Configured router interface that is used to communicate with hosts outside the current segment (network). • Router sends it’s own MAC address. ...
Network Design Project You have been given the assignment to
... Systems, Hardware (workstations, servers, hubs, switches, routers, access points, etc. - include manufacturer, item, specifications, price, etc.), Infrastructure cabling/Wireless solutions, Network Protocols (routed and routing), Internet Access solutions, Email software and protocols, and Network S ...
... Systems, Hardware (workstations, servers, hubs, switches, routers, access points, etc. - include manufacturer, item, specifications, price, etc.), Infrastructure cabling/Wireless solutions, Network Protocols (routed and routing), Internet Access solutions, Email software and protocols, and Network S ...
Position: Senior IA/Security Specialist, (Computer Network Defense
... NAVAIR RDT&E and NMCI/NGEN networks • Recommend solutions as authorized/needed in accordance with cyber security strategy • Manage CND tools including but not limited to IDS/IPS, IAVM/ACAS, HBSS, Blue Scope, CORE Impact, and Advanced Threat Detection (ATD). • Present technical and analytical options ...
... NAVAIR RDT&E and NMCI/NGEN networks • Recommend solutions as authorized/needed in accordance with cyber security strategy • Manage CND tools including but not limited to IDS/IPS, IAVM/ACAS, HBSS, Blue Scope, CORE Impact, and Advanced Threat Detection (ATD). • Present technical and analytical options ...
Wireless Audio Conferencing System (WACS)
... address when only its Internet Layer (IP) or Network Layer address is known. uses a simple message format that contains one address resolution request or response Once local network recognized, the server or networking device returns a response containing the required address. ...
... address when only its Internet Layer (IP) or Network Layer address is known. uses a simple message format that contains one address resolution request or response Once local network recognized, the server or networking device returns a response containing the required address. ...
ppt
... Only 28.6% of IP space is allocated Detect worms by monitoring unused addresses Honeypots/Honeynet ...
... Only 28.6% of IP space is allocated Detect worms by monitoring unused addresses Honeypots/Honeynet ...
PH19510 Lecture 12
... Request For Comment (RFC) Building networks is a collaborative enterprise. RFC mechanism came out of ARPA Serve as mechanism for dissemination for information Some become adopted as standards ...
... Request For Comment (RFC) Building networks is a collaborative enterprise. RFC mechanism came out of ARPA Serve as mechanism for dissemination for information Some become adopted as standards ...
Unbuntu Installation
... human being at a time. Linux, like all Unix variants, is designed to handle multiple concurrent users. Windows, of course, can run many programs concurrently, as can Linux. There is a multi-user version of Windows called Terminal Server but this is not the Windows preinstalled on personal computers. ...
... human being at a time. Linux, like all Unix variants, is designed to handle multiple concurrent users. Windows, of course, can run many programs concurrently, as can Linux. There is a multi-user version of Windows called Terminal Server but this is not the Windows preinstalled on personal computers. ...
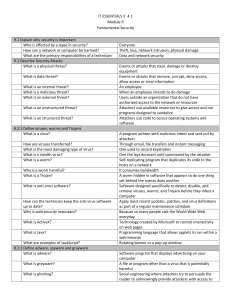
Test 3 review guide 50 questions 10 T/F and 40 multiple choices
... Test 3 review guide 50 questions 10 T/F and 40 multiple choices One hour *** To prepare for the test you must refer to the lecture notes and lecture book posted on the course website and don’t forget the lecture complement posted on the course website (Check the announcement page) 1- Networking and ...
... Test 3 review guide 50 questions 10 T/F and 40 multiple choices One hour *** To prepare for the test you must refer to the lecture notes and lecture book posted on the course website and don’t forget the lecture complement posted on the course website (Check the announcement page) 1- Networking and ...