networking - Department of Computer Engineering
... Building blocks of networks (PCs, Servers, Hubs, Switches, Routers, Cables, etc.) ...
... Building blocks of networks (PCs, Servers, Hubs, Switches, Routers, Cables, etc.) ...
Chapter1R_v2
... To interconnect local workstations To access local shared resources (printers, storage, servers) ...
... To interconnect local workstations To access local shared resources (printers, storage, servers) ...
Penetration Testing Presentation
... – Find running services – Find live hosts • fping, ICMPenum, Ethereal ...
... – Find running services – Find live hosts • fping, ICMPenum, Ethereal ...
A Wireless Intrusion Detection System and a new
... The data send process is done by splitting the chosen text file into packets for transmission. The data send process is invoked after the source finds out an intruder free path. In the case of jamming/network malfunction, the source waits till the network is restored, starts the training process to ...
... The data send process is done by splitting the chosen text file into packets for transmission. The data send process is invoked after the source finds out an intruder free path. In the case of jamming/network malfunction, the source waits till the network is restored, starts the training process to ...
Project Title: Wireless Multimedia Mesh Networks
... QoS optimization: Since various digital media applications are co-existence in the network and each of them requires different types of QoS requirement such as delay, data rate, error rate and cost. An efficient QoS algorithm is needed to satisfy their QoS requirement and at the same time it can max ...
... QoS optimization: Since various digital media applications are co-existence in the network and each of them requires different types of QoS requirement such as delay, data rate, error rate and cost. An efficient QoS algorithm is needed to satisfy their QoS requirement and at the same time it can max ...
Computer Networks - Texas State Department of Computer Science
... allowing traffic between the two. Can be hardware or software ...
... allowing traffic between the two. Can be hardware or software ...
Document
... Network: system for connecting computer using a single transmission technology Internet: set of networks connected by routers that are configured to pass traffic among any computers attached to networks in the set •Data transmission - media, data encoding •Packet transmission - data exchange over a ...
... Network: system for connecting computer using a single transmission technology Internet: set of networks connected by routers that are configured to pass traffic among any computers attached to networks in the set •Data transmission - media, data encoding •Packet transmission - data exchange over a ...
fn-4127-nic network interface card
... the expansion of up to 64 nodes (combination of FACP’s or annuciators) on a single FireNET network wide system. Using the Loop Explorer configuration software up to 64 nodes can be programmed to respond to in a variety ways-independently or system wide. The flexibility extends the comprehensive caus ...
... the expansion of up to 64 nodes (combination of FACP’s or annuciators) on a single FireNET network wide system. Using the Loop Explorer configuration software up to 64 nodes can be programmed to respond to in a variety ways-independently or system wide. The flexibility extends the comprehensive caus ...
Troubleshooting your PC - Hill City SD 51-2
... Span relatively large areas Typically consist of two or more LANs Are connected using telephone or leased lines ...
... Span relatively large areas Typically consist of two or more LANs Are connected using telephone or leased lines ...
ITEC350 Networks I
... Connection-Oriented and Connectionless Services The software used to maintain each protocol is often called a protocol stack Transport layer protocols can be: Connectionless, or stateless, which sends each packet without regard to whether any other packet was received by the destination compute ...
... Connection-Oriented and Connectionless Services The software used to maintain each protocol is often called a protocol stack Transport layer protocols can be: Connectionless, or stateless, which sends each packet without regard to whether any other packet was received by the destination compute ...
Computer Network
... computing devices pass data to each other along data connections. The connections (network links) between nodes are established using either cable media or wireless media. The best-known computer network is the Internet. ...
... computing devices pass data to each other along data connections. The connections (network links) between nodes are established using either cable media or wireless media. The best-known computer network is the Internet. ...
How the Internet works
... protocol stacks • layered architecture each layer is an abstraction that assumes the functionality of the layer underneath files unencrypted streams buffers packets frames bytes bits drivers, network card ...
... protocol stacks • layered architecture each layer is an abstraction that assumes the functionality of the layer underneath files unencrypted streams buffers packets frames bytes bits drivers, network card ...
• Overview of Cyber Security & need of cyber security • Introduction
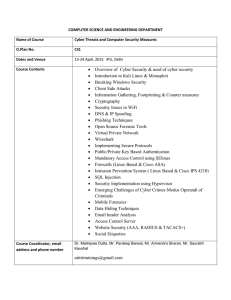
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
Networks
... Network servers that manage the networks and host applications that are shared with client computers Two types: Two-tiered Three-tiered ...
... Network servers that manage the networks and host applications that are shared with client computers Two types: Two-tiered Three-tiered ...
presentation source
... IPFWADM (Firewall) • Manages Permit/Deny Firewall Access Lists • Controls which networks are allowed to IP Masquerade • Deny access to all other networks. ...
... IPFWADM (Firewall) • Manages Permit/Deny Firewall Access Lists • Controls which networks are allowed to IP Masquerade • Deny access to all other networks. ...
Wireless LAN Management
... IEEE 802.11 outline that the secret key used by WEP needs to be controlled by external key management ...
... IEEE 802.11 outline that the secret key used by WEP needs to be controlled by external key management ...
ppt
... • Uses info on the infected host to find the next target Morris Worm used /etc/hosts , .rhosts Email address books P2P software usually store info about peers that each host connects to ...
... • Uses info on the infected host to find the next target Morris Worm used /etc/hosts , .rhosts Email address books P2P software usually store info about peers that each host connects to ...
The University of Oklahoma Virtual Private Network
... instead a direct way to send and receive datagrams over an IP network. It's used primarily for broadcasting messages over a network. A machine sends out information without confirming whether the recipient successfully received the message or not. ...
... instead a direct way to send and receive datagrams over an IP network. It's used primarily for broadcasting messages over a network. A machine sends out information without confirming whether the recipient successfully received the message or not. ...
10 the internet and the new information technology infrastructure
... • Incorporates public infrastructure (telephone system, Internet, etc.) ...
... • Incorporates public infrastructure (telephone system, Internet, etc.) ...
Download the bC Wireless datasheet here
... METTLER TOLEDO Wireless Solution benefit from increased network convenience without cable clutter and tripping hazards. The METTLER TOLEDO Wireless Solution does not require any technical knowledge and gives retailers more independence and flexibility in the configuration and use of their sales area ...
... METTLER TOLEDO Wireless Solution benefit from increased network convenience without cable clutter and tripping hazards. The METTLER TOLEDO Wireless Solution does not require any technical knowledge and gives retailers more independence and flexibility in the configuration and use of their sales area ...