Technologies that make the Internet Robust
... Internet backbone – who owns it? who controls it? – can you tell somebody to stop streaming or hogging all the bandwidth? – the cable and phone companies would sure like to! – a large fraction of Internet traffic is Netflix + ...
... Internet backbone – who owns it? who controls it? – can you tell somebody to stop streaming or hogging all the bandwidth? – the cable and phone companies would sure like to! – a large fraction of Internet traffic is Netflix + ...
Data Communications Data Communications Features
... signals back to a number of earth-based stations Transmitted waves can be received on the all ground through a satellite antenna. Æ security issue ...
... signals back to a number of earth-based stations Transmitted waves can be received on the all ground through a satellite antenna. Æ security issue ...
Module 03 Wireless Media Presentation
... With EAP, the access point does not provide authentication to the client, but passes the duties to a more sophisticated device, possibly a dedicated server, designed for that purpose. EAP-MD5 Challenge – Extensible Authentication Protocol is the earliest authentication type, which is very similar to ...
... With EAP, the access point does not provide authentication to the client, but passes the duties to a more sophisticated device, possibly a dedicated server, designed for that purpose. EAP-MD5 Challenge – Extensible Authentication Protocol is the earliest authentication type, which is very similar to ...
The Internet
... 10-100 machines connected to a hub or a router service providers also provide direct dialup access or over a wireless link 10s of routers on a department backbone 10s of department backbones connected to campus backbone 10s of campus backbones connected to regional service providers 100s of regi ...
... 10-100 machines connected to a hub or a router service providers also provide direct dialup access or over a wireless link 10s of routers on a department backbone 10s of department backbones connected to campus backbone 10s of campus backbones connected to regional service providers 100s of regi ...
Lecture 9 & 10
... LEARNING OUTCOMES 5. Describe TCP/IP along with its primary purpose 6. Identify the different media types found in networks 7. Explain the difference between a VPN and a VAN ...
... LEARNING OUTCOMES 5. Describe TCP/IP along with its primary purpose 6. Identify the different media types found in networks 7. Explain the difference between a VPN and a VAN ...
Windows Vista Security and Compliance
... What Is Defense-in-Depth? Using a layered approach: Increases an attacker’s risk of detection Reduces an attacker’s chance of success ...
... What Is Defense-in-Depth? Using a layered approach: Increases an attacker’s risk of detection Reduces an attacker’s chance of success ...
ppt
... Italian law asks ISSGC06 to record users identification data digitally before giving them access. This is done by scanning passports or ID cards. (More details are on the leaflet you received during registration, if needed ask the registration desk to obtain it again). ...
... Italian law asks ISSGC06 to record users identification data digitally before giving them access. This is done by scanning passports or ID cards. (More details are on the leaflet you received during registration, if needed ask the registration desk to obtain it again). ...
Introduction
... Transceivers: transmitters and receivers on the point-to-point connections Multiplexers, demultiplexers Packet and circuit switches ...
... Transceivers: transmitters and receivers on the point-to-point connections Multiplexers, demultiplexers Packet and circuit switches ...
Introduction
... An IP address is a 32-bit sequence of 1s and 0s. To make the IP address easier to use, the address is usually written as four decimal numbers separated by periods. This way of writing the address is called the dotted decimal format. ...
... An IP address is a 32-bit sequence of 1s and 0s. To make the IP address easier to use, the address is usually written as four decimal numbers separated by periods. This way of writing the address is called the dotted decimal format. ...
William Stallings Data and Computer Communications
... Packets passed from node to node between source and destination Used for terminal to computer and computer to computer communications ...
... Packets passed from node to node between source and destination Used for terminal to computer and computer to computer communications ...
Collecting Information to Visualize Network Status
... http://i-path.goto.info.waseda.ac.jp/trac/i-Path/ • Dai Mochinaga, Katsushi Kobayashi, Shigeki Goto, Akihiro Shimoda, and Ichiro Murase, Collecting Information to Visualize Network Status, 28th APAN Network Research Workshop, ...
... http://i-path.goto.info.waseda.ac.jp/trac/i-Path/ • Dai Mochinaga, Katsushi Kobayashi, Shigeki Goto, Akihiro Shimoda, and Ichiro Murase, Collecting Information to Visualize Network Status, 28th APAN Network Research Workshop, ...
GST 115- INTRODUCTION TO ICT ASSIGNMENT 1
... any other network component. Network Interface Cards are expansions boards either built into the computer system or connected to it via expansion slots. They are used to connect the computer system to a network, and provide the physical, electrical and electronic connections to the network media. Re ...
... any other network component. Network Interface Cards are expansions boards either built into the computer system or connected to it via expansion slots. They are used to connect the computer system to a network, and provide the physical, electrical and electronic connections to the network media. Re ...
Packet switched
... • TCP/IP is the most common There are other protocols which replace TCP, like RTP • Both the receiving and sending device need to have the correct protocols agreed and ability to receive them ...
... • TCP/IP is the most common There are other protocols which replace TCP, like RTP • Both the receiving and sending device need to have the correct protocols agreed and ability to receive them ...
IP Forwarding and ICMP
... IP provide provides an unreliable connectionless best effort service (also called: “datagram service”). ...
... IP provide provides an unreliable connectionless best effort service (also called: “datagram service”). ...
1.Which of the following are true LAN and WAN differ in area they
... 2.Twisted pair cable is an example of which type of Media Physical Media 3.Bus Topology is All computers are linked by a single line of cable 4.Ring Topology is Each computer or workstation is connected to two other computers 5.scrambling the order of symbols Transposition 6.Cryptography is the stud ...
... 2.Twisted pair cable is an example of which type of Media Physical Media 3.Bus Topology is All computers are linked by a single line of cable 4.Ring Topology is Each computer or workstation is connected to two other computers 5.scrambling the order of symbols Transposition 6.Cryptography is the stud ...
Computer Networks BITS ZC481
... Different Communication services provided to apps: reliable data delivery from source to destination. “best effort” (unreliable) data delivery. ...
... Different Communication services provided to apps: reliable data delivery from source to destination. “best effort” (unreliable) data delivery. ...
ITEC 370 Midterm
... ____ 13. ____ is a nonroutable protocol. a. NetBEUI c. IPX b. IP d. SPX ____ 14. ____ is a name-to-address resolution protocol that functionally operates at the Session layer of the OSI model. a. DNS c. ICMP b. ARP d. DHCP ____ 15. An IP address is divided into two distinct parts: one part designate ...
... ____ 13. ____ is a nonroutable protocol. a. NetBEUI c. IPX b. IP d. SPX ____ 14. ____ is a name-to-address resolution protocol that functionally operates at the Session layer of the OSI model. a. DNS c. ICMP b. ARP d. DHCP ____ 15. An IP address is divided into two distinct parts: one part designate ...
My PowerPoint for 6/24/2005 Presentation
... Isaac Rieksts My web site http://studentwebs.kutztown.edu/riek7902/reu%5Fauburn/ ...
... Isaac Rieksts My web site http://studentwebs.kutztown.edu/riek7902/reu%5Fauburn/ ...
Data Communication and Networks
... 6. KavethPahlavan, K.Prasanth Krishnamurthy, ‘Principles of Wireless Networks”, Pearson Education Asia, 2002. 7. Jon W. Mark, Weihua Zhuang, ‘Wireless communication and Networking’, Prentice Hall India, ...
... 6. KavethPahlavan, K.Prasanth Krishnamurthy, ‘Principles of Wireless Networks”, Pearson Education Asia, 2002. 7. Jon W. Mark, Weihua Zhuang, ‘Wireless communication and Networking’, Prentice Hall India, ...
mathcs.slu.edu
... • How is this conversion done? – Originally, there was one big table kept on a computer at Stanford. Whenever a computer needed to know an address, it would ask this computer. – But as the Internet grew, this computer was overloaded with requests and the underlying table was being updated too often. ...
... • How is this conversion done? – Originally, there was one big table kept on a computer at Stanford. Whenever a computer needed to know an address, it would ask this computer. – But as the Internet grew, this computer was overloaded with requests and the underlying table was being updated too often. ...
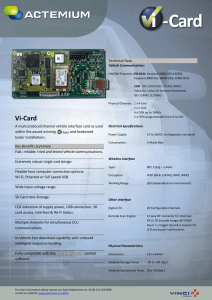
Vi-Card
... LED indication of supply power, USB connection, SD card access, interface & Wi-Fi Status. ...
... LED indication of supply power, USB connection, SD card access, interface & Wi-Fi Status. ...
Wireless Network - Optimal Resume at KAPLAN UNIVERSITY
... The business organization needs to protect their network with automated tools such as encryption with symmetric encryption. The symmetric encryption shares a single encryption/decryption key. A public-key also provides two keys, one for encryption and a paired key for decryption. The secure networki ...
... The business organization needs to protect their network with automated tools such as encryption with symmetric encryption. The symmetric encryption shares a single encryption/decryption key. A public-key also provides two keys, one for encryption and a paired key for decryption. The secure networki ...