Slide 1
... update its database with the list in another DNS server. – An incorrectly configured DNS server may allow any Internet user to perform a zone transfer. – nslookup ...
... update its database with the list in another DNS server. – An incorrectly configured DNS server may allow any Internet user to perform a zone transfer. – nslookup ...
Understanding Networks II
... infrared light instead of cables or wires to connect computers or other devices. • Connections are made using a wireless NIC, which includes an antenna to send and receive signals. • Wireless devices can communicate directly, or they can connect to a LAN by way of a wireless access point (AP). ...
... infrared light instead of cables or wires to connect computers or other devices. • Connections are made using a wireless NIC, which includes an antenna to send and receive signals. • Wireless devices can communicate directly, or they can connect to a LAN by way of a wireless access point (AP). ...
NT Security Overview
... organization will have access to the network. In most businesses or organizations there are employees, staff, management and officers. Some can be trusted to access all of the network and others do not have the trust level to access any of the network. The administrator must decide who has access an ...
... organization will have access to the network. In most businesses or organizations there are employees, staff, management and officers. Some can be trusted to access all of the network and others do not have the trust level to access any of the network. The administrator must decide who has access an ...
Hacking - Computer Engineering
... Reconnaissance: Port Scans Applications on a system use ports to listen for network traffic or send it out. 216 ports available, some for known services such as http (80), ftp, ... Port scans send various type of IP packages to target on different ports. Reaction tells them whether the port i ...
... Reconnaissance: Port Scans Applications on a system use ports to listen for network traffic or send it out. 216 ports available, some for known services such as http (80), ftp, ... Port scans send various type of IP packages to target on different ports. Reaction tells them whether the port i ...
PPT - 清華大學資訊工程學系
... – If the channel is busy, it waits another random period. After waiting, if the channel is silent, it sends data immediately. ...
... – If the channel is busy, it waits another random period. After waiting, if the channel is silent, it sends data immediately. ...
Intrusion Detection Systems
... has already been established and whether this packet was requested. – If a packet arrives with no record of its being part of legitimate session, the firewall will block access by dropping it. ...
... has already been established and whether this packet was requested. – If a packet arrives with no record of its being part of legitimate session, the firewall will block access by dropping it. ...
Acceptable Use Policy (AUP)
... ... use moral and ethical guidelines ... regarding network use. Students are expected to use moral and ethical guidelines in making appropriate decisions regarding network use. Use of the district network is not a right, but a privilege, and inappropriate use will result in cancellation of that pri ...
... ... use moral and ethical guidelines ... regarding network use. Students are expected to use moral and ethical guidelines in making appropriate decisions regarding network use. Use of the district network is not a right, but a privilege, and inappropriate use will result in cancellation of that pri ...
DoS Attacks On Wireless Voice Over IP Systems
... • wVoIP is extremely vulnerable to DoS attacks because access to the transmission medium is open to anybody with 802.11 hardware. • Because real-time traffic such as VoIP and video conferencing media is intolerable of even small delays it is relatively easy to disrupt the service long enough to make ...
... • wVoIP is extremely vulnerable to DoS attacks because access to the transmission medium is open to anybody with 802.11 hardware. • Because real-time traffic such as VoIP and video conferencing media is intolerable of even small delays it is relatively easy to disrupt the service long enough to make ...
TCP/IP
... The method used for splitting IP networks into a series of subgroups, or subnets. The mask is a binary pattern that is matched up with the IP address to turn part of the host ID address field into a field for subnets. It's called a mask because it can be used to identify the subnet to which an IP ad ...
... The method used for splitting IP networks into a series of subgroups, or subnets. The mask is a binary pattern that is matched up with the IP address to turn part of the host ID address field into a field for subnets. It's called a mask because it can be used to identify the subnet to which an IP ad ...
is accepting applications for a Network Engineer who will be
... correlates computer reports, files, logs, and messages produced by engineers, system administrators, and systems identifying instances of possible information security incidents, supports the incident response plan and process, and supports investigations as required. ...
... correlates computer reports, files, logs, and messages produced by engineers, system administrators, and systems identifying instances of possible information security incidents, supports the incident response plan and process, and supports investigations as required. ...
Logical addressing
... addressed packets from their source toward their ultimate destination through intermediate nodes; typically hardware devices called routers, bridges, gateways, firewalls, or switches. General-purpose computers with multiple network cards can also forward packets and perform routing, though they are ...
... addressed packets from their source toward their ultimate destination through intermediate nodes; typically hardware devices called routers, bridges, gateways, firewalls, or switches. General-purpose computers with multiple network cards can also forward packets and perform routing, though they are ...
$doc.title
... • MAC address (e.g., 00-‐15-‐C5-‐49-‐04-‐A9) – Numerical address used within a link – Unique, hard-‐coded in the adapter when it is built – Flat name space of 48 bits ...
... • MAC address (e.g., 00-‐15-‐C5-‐49-‐04-‐A9) – Numerical address used within a link – Unique, hard-‐coded in the adapter when it is built – Flat name space of 48 bits ...
IP spoofing - University Of Worcester
... Distributed Denial of Service (DDoS) attack » Ping from multiple (may be many thousands!) of “Internet-ready” devices ...
... Distributed Denial of Service (DDoS) attack » Ping from multiple (may be many thousands!) of “Internet-ready” devices ...
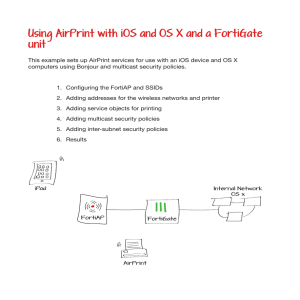
Using AirPrint with iOS and OS X and a FortiGate unit
... Adding multicast security policies Go to Policy > Policy > Multicast Policy. Create two policies to allow multicast traffic from WLAN1 and WLAN2 for iOS devices. For the first policy, set Incoming Interface to WLAN1, Source Address to the SSID1 IP, Outgoing Interface to WLAN2, and Destination Addre ...
... Adding multicast security policies Go to Policy > Policy > Multicast Policy. Create two policies to allow multicast traffic from WLAN1 and WLAN2 for iOS devices. For the first policy, set Incoming Interface to WLAN1, Source Address to the SSID1 IP, Outgoing Interface to WLAN2, and Destination Addre ...
What is a Network? A network consists of two or more nodes
... minutes. A WAN uses multiplexers (a device that allows multiple logical signals to be transmitted simultaneously across a single physical channel) to connect local and metropolitan networks to global communications networks like the Internet. To users, a WAN will not appear to be much different than ...
... minutes. A WAN uses multiplexers (a device that allows multiple logical signals to be transmitted simultaneously across a single physical channel) to connect local and metropolitan networks to global communications networks like the Internet. To users, a WAN will not appear to be much different than ...
PowerPoint
... • Network is a graph with routers and links – Each unidirectional link has a weight (1-63,535) – Shortest-path routes from sum of link weights ...
... • Network is a graph with routers and links – Each unidirectional link has a weight (1-63,535) – Shortest-path routes from sum of link weights ...
David Taylor (PowerPoint)
... • It’s a network link between EUMETSAT in Darmstadt and your home. • Packets of data are sent out from EUMETSAT (actually from Usingen). • They look like digital TV signals but have more robust protection. • Your job is to capture them. ...
... • It’s a network link between EUMETSAT in Darmstadt and your home. • Packets of data are sent out from EUMETSAT (actually from Usingen). • They look like digital TV signals but have more robust protection. • Your job is to capture them. ...
Chapter 3 - Network Protocols
... A port scanner is a tool used to query a network device to determine all the ports / services that are open on for use on a system. Port scanners are important tools for both network defenders as well as attackers. nmap is probably the most popular port scanner available http://www.nmap.org ...
... A port scanner is a tool used to query a network device to determine all the ports / services that are open on for use on a system. Port scanners are important tools for both network defenders as well as attackers. nmap is probably the most popular port scanner available http://www.nmap.org ...
IP Traceback With Deterministic Packet Marking
... suitable for a variety of attacks [not just (D)DoS] Backward compatible with equipment which does not implement it does not have inherent security flaws Do not reveal internet topology No mark spoofing Scalable ...
... suitable for a variety of attacks [not just (D)DoS] Backward compatible with equipment which does not implement it does not have inherent security flaws Do not reveal internet topology No mark spoofing Scalable ...
DHCP Server Configuration - Brookdale Community College
... Setup Wizard • Follow these steps to access the Access Point.s HTTP interface and launch the Setup Wizard: 1. Open a Web browser on a network computer. 2. If necessary, disable the browser.s Internet proxy settings. For Internet Explorer users, ...
... Setup Wizard • Follow these steps to access the Access Point.s HTTP interface and launch the Setup Wizard: 1. Open a Web browser on a network computer. 2. If necessary, disable the browser.s Internet proxy settings. For Internet Explorer users, ...