Do you know someone may be watching you?
... sources that are hacking into your system by using various techniques in computer science and mathematics. ...
... sources that are hacking into your system by using various techniques in computer science and mathematics. ...
Part 1
... A firewall is built into Windows XP More robust firewalls are available from other vendors. Firewalls are critical if you have an always-on broadband connection. ...
... A firewall is built into Windows XP More robust firewalls are available from other vendors. Firewalls are critical if you have an always-on broadband connection. ...
Lecture 1 - cda college
... ring – All the devices share a single cable Dual ring – Allows data to be sent in both directions and provides redundancy ...
... ring – All the devices share a single cable Dual ring – Allows data to be sent in both directions and provides redundancy ...
ch2
... if adapter receives frame with matching destination address, or with broadcast address (eg ARP packet), it passes data in frame to net-layer protocol otherwise, adapter discards frame ...
... if adapter receives frame with matching destination address, or with broadcast address (eg ARP packet), it passes data in frame to net-layer protocol otherwise, adapter discards frame ...
Internetworking - National Tsing Hua University
... HardwareType: type of physical network (e.g., Ethernet) ProtocolType: type of higher layer protocol (e.g., IP) HLEN & PLEN: length of physical and protocol addresses Operation: request or response Source/Target-Physical/Protocol addresses ...
... HardwareType: type of physical network (e.g., Ethernet) ProtocolType: type of higher layer protocol (e.g., IP) HLEN & PLEN: length of physical and protocol addresses Operation: request or response Source/Target-Physical/Protocol addresses ...
Factsheet - KFSensor
... New threats are constantly emerging to the security of organisations' information systems infrastructure. Firewalls and VPNs cannot prevent all intrusions and do little to prevent attacks from within the organisation itself. Intrusion detection plays a vital role in ensuring the integrity of a netwo ...
... New threats are constantly emerging to the security of organisations' information systems infrastructure. Firewalls and VPNs cannot prevent all intrusions and do little to prevent attacks from within the organisation itself. Intrusion detection plays a vital role in ensuring the integrity of a netwo ...
Network Management - Department of Computer Science, HKBU
... the modem will not require a password to connect and the attacker will have access to the system. COMP4690, HKBU ...
... the modem will not require a password to connect and the attacker will have access to the system. COMP4690, HKBU ...
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661,p-ISSN: 2278-8727 PP 37-41 www.iosrjournals.org
... (b) The model proposed is incentive based, fast responsive and light weighted which isindependent from any central authority and easy to detection for individual nodes. (c) Incremental approach is used for designing the detection system as soon as anyspecific attack is identified. It is easy to add ...
... (b) The model proposed is incentive based, fast responsive and light weighted which isindependent from any central authority and easy to detection for individual nodes. (c) Incremental approach is used for designing the detection system as soon as anyspecific attack is identified. It is easy to add ...
Networks - Computer Science@IUPUI
... going everywhere on the network) •computers will be talking to each other and the direction of the traffic is controlled by the various protocols (like Ethernet) ...
... going everywhere on the network) •computers will be talking to each other and the direction of the traffic is controlled by the various protocols (like Ethernet) ...
A6_Oct_07_08 - Raadio- ja sidetehnika instituut
... Internet protocol • Provides best effort, connectionless packet delivery – motivated by need to keep routers simple and by adaptibility to failure of network elements – packets may be lost, out of order, or even duplicated – higher layer protocols must deal with these, if necessary ...
... Internet protocol • Provides best effort, connectionless packet delivery – motivated by need to keep routers simple and by adaptibility to failure of network elements – packets may be lost, out of order, or even duplicated – higher layer protocols must deal with these, if necessary ...
DIR-657 A1 Sales Guide - D-Link
... Family Home Users who want to a better performance to share media streaming and data transmission simultaneously. ...
... Family Home Users who want to a better performance to share media streaming and data transmission simultaneously. ...
1. DIGISCENT 2. TYPES OF NETWORK 3. NETWORK
... comunicate without the use of cables. IEEE 802.11b defines two pieces of equipment, a wireless station, which is usually a PC or a Laptop with a wireless network interface card (NIC), and an Access Point (AP),which acts as a bridge between the wireless stations and Distribution System (DS) or wired ...
... comunicate without the use of cables. IEEE 802.11b defines two pieces of equipment, a wireless station, which is usually a PC or a Laptop with a wireless network interface card (NIC), and an Access Point (AP),which acts as a bridge between the wireless stations and Distribution System (DS) or wired ...
Chapter07.pdf
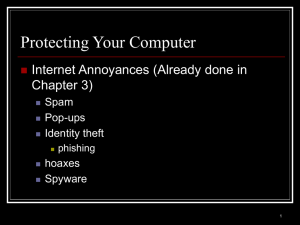
... – Access can be gained through an open port. A port is any pathway of data in or out of a computer – Port scanning software looks for unprotected computers and can attack an unprotected computer within 9 minutes – To protect your computer: ...
... – Access can be gained through an open port. A port is any pathway of data in or out of a computer – Port scanning software looks for unprotected computers and can attack an unprotected computer within 9 minutes – To protect your computer: ...
TCPdump
... by the data in the packet Ack: sequence number of the next data Window: the number of byte of receive buffer space Urg: indicates there is “urgent” data in the packet Options: tcp options enclosed in angle brackets ...
... by the data in the packet Ack: sequence number of the next data Window: the number of byte of receive buffer space Urg: indicates there is “urgent” data in the packet Options: tcp options enclosed in angle brackets ...
Network Management
... Why Active Audit? • The hacker might be an employee or ‘trusted’ partner Up to 80% of security breaches are from insiders -- FBI ...
... Why Active Audit? • The hacker might be an employee or ‘trusted’ partner Up to 80% of security breaches are from insiders -- FBI ...
Screened-host firewall
... When a message is received, it references what was sent to confirm it is a response Advantages are; control the flow of IP traffic by matching information contained in the headers of connection-oriented or connectionless IP packets at the transport layer Disadvantages include being difficult t ...
... When a message is received, it references what was sent to confirm it is a response Advantages are; control the flow of IP traffic by matching information contained in the headers of connection-oriented or connectionless IP packets at the transport layer Disadvantages include being difficult t ...
15 - MCCC Faculty Page
... someone registering a domain name may be liable to the owner of a trademark or to others that may be affected by the “bad faith” of the domain name registrant ...
... someone registering a domain name may be liable to the owner of a trademark or to others that may be affected by the “bad faith” of the domain name registrant ...
Lec.4.Communication software and the internet
... • A set of computers connected together so that they can communicate is called a computer network. • This involves installing network cards in each computer. • Each computer is then connected through cabling to a central device called a hub. • The most commonly used protocol for establishing and ma ...
... • A set of computers connected together so that they can communicate is called a computer network. • This involves installing network cards in each computer. • Each computer is then connected through cabling to a central device called a hub. • The most commonly used protocol for establishing and ma ...
ppt
... • Allow users (campus LAN administrators and network engineers) to manage network devices, change device configurations, troubleshoot, inspect traffic data, coordinate with users, and perform other network management tasks. ...
... • Allow users (campus LAN administrators and network engineers) to manage network devices, change device configurations, troubleshoot, inspect traffic data, coordinate with users, and perform other network management tasks. ...
Essential Elements of Medical Networks
... - connects all the nodes of a network using Twisted Pair cables - the hub repeats the signal to all ports, but does not look into the packet - signals received on one port are transmitted to all other ports - all work stations connected to the hub ‘listen’ to one another - these older devices often ...
... - connects all the nodes of a network using Twisted Pair cables - the hub repeats the signal to all ports, but does not look into the packet - signals received on one port are transmitted to all other ports - all work stations connected to the hub ‘listen’ to one another - these older devices often ...
ppt
... • Guideline not a law • Argument • If you have to implement a function end-to-end anyway (e.g., because it requires the knowledge and help of the end-point host or application), don’t implement it inside the communication system • Unless there’s a compelling performance enhancement Further Reading: ...
... • Guideline not a law • Argument • If you have to implement a function end-to-end anyway (e.g., because it requires the knowledge and help of the end-point host or application), don’t implement it inside the communication system • Unless there’s a compelling performance enhancement Further Reading: ...