* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chapter 3 - Network Protocols
Extensible Authentication Protocol wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
TCP congestion control wikipedia , lookup
Computer security wikipedia , lookup
Airborne Networking wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Wireless security wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
Zero-configuration networking wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
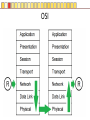
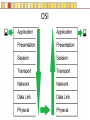
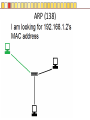
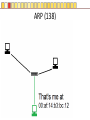
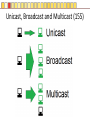
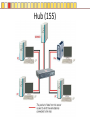
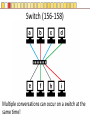
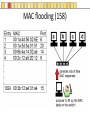
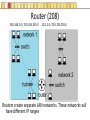
Slides copyright 2010 by Paladin Group, LLC used with permission by UMBC Training Centers, LLC Security+ Chapter 3 – Understanding Basic Network Security Brian E. Brzezicki OSI (135-137) All People Seem To Need Data Processing OSI (135-137) The OSI is a model of how network communications should be broken down into functional “tasks”. Each layer performs one task. It provides “services” to the layer above it, and uses services from the layer below it. Remote devices talk to each other at the same level. The OSI model is broken down into 7 levels (layers) which we will discuss. OSI OSI OSI model – layer 1 physical (135-137) • Layer 1 Physical – simply put is concerned with physically sending electric signals over a medium. Is concerned with – specific cabling, – voltages and – Timings • This level actually sends data as electrical signals that other equipment using the same “physical” medium understand – ex. Ethernet OSI model – layer 2 data link (135-137) • Layer 2 Data Link – data link goes hand in hand with physical layer. The data link level actually defines the format of how data frames will be sent over the physical medium, so that two network cards of the same network type will actually be able to communicate. These frames are sent to physical level to be turned into the electronic signals that are sent over a specific network. (layer 2 uses the services of layer 1) • Two network cards on the same LAN communicate at the data link layer. OSI model – layer 3 network (135-137) Layer 3 Network – Layer 3 is concerned with network addressing and specifically moving packets between networks in an optimal manner (routing). Some Layer 3 network protocols are – IP – IPX/SPX – Apple Talk OSI model Layer 4 Transport (135-137) • OSI Layer 4 Transport – Provides end-to-end data transport services and establishes a logical connection between 2 computers systems. • Virtual connection between COMPUTERS OSI Model Layer 5 Session (135-137) • OSI Layer 5 Session – responsible for establishing a connection between two APPLICATIONS! Either on the same computer or two different computers • Create connection • Transfer data • Release connection OSI model Layer 6 – Presentation (135-137) • OSI Layer 6 – present the data in a format that all computers can understand – Concerned with encryption, compression and formatting OSI model Layer 7 – Application (135-137) • This layers is concerned the communications / protocols between two applications communicating with each other. – HTTP – SMTP – DNS • This is the layer that most software uses to talk with other software. Protocols Protocols What does protocol mean? TCP/IP Protocols (138) Some TCP/IP protocols you should be familiar with • IP • ARP • TCP • UDP • IGMP • ICMP IP and IP addresses (138) IP is the protocol of network communication on the Internet. All computers using the Internet MUST use IP. It is mainly concerned with • Host addressing • Routing IP and IP addresses (138) IP addresses are global unique network identifiers. IPv4 addresses follow the format 0-255 . 0-255 . 0-255 . 0-255 Example: 130.85.1.4 There are a few ranges of IPv4 addresses that are considered private and can be re-used • 10.x.x.x • 192.168.x.x • 172.16.x.x – 172.31.x.x ARP (138) • ARP – Network Adapters have 2 addresses, and IP address (layer 3), and a MAC address (layer 4). – ARP is the glue for relating the IP and the MAC addresses ARP (138) ARP (138) TCP (138) Connection oriented “guaranteed” delivery. Uses a 3-way handshake to establish a connection. Advantages – Easier to program with – Truly implements a “session” – Adds security Disadvantages – More overhead / slower UDP (138) Connectionless, non-guaranteed delivery also called best effort Advantages – Fast / low overhead Disadvantages – Harder to program with – No true sessions – Less security – A pain to firewall IGMP (138) Internet Group Message Protocol – Used to manage group communications. ICMP (138) Internet Control Message Protocol – Used for network troubleshooting and diagnostics. Common tools that use ICMP • ping • traceroute Application Protocols Application Protocols we will discuss • HTTP • HTTPS • TFTP • FTP • TFTP • SNMP • DNS • LDAP • Telnet • Kerberos • Remote Desktop HTTP (139) Hyper Text Transport Protocol • Web communication • TCP/80 • Common software – Apache – ISS – Internet Explorer – Firefox HTTPS (139) HTTP using SSL/TLS for encryption and server authentication • TCP / 443 FTP (139) File Transfer Protocol • TCP/21 and TCP/20 Problems • No encryption of data TFTP (139) Trivial File Transfer Protocol • UDP / 69 • Used for network equipment provisioning Problems • No encryption • No authentication SNMP (139) Simple Network Management Protocol – used for managing network devices • UDP / 161 Problems • Early versions are un-encrypted • Early versions used weak authentication • Early versions still widely enabled DNS (140) Domain Name Service – Turns Internet names into resources records, usually IP addresses. • TCP / 53 and UDP / 53 • Understand what a zone transfer is Problems • IF subverted easy to direct people away from their intended destination LDAP (141) Lightweight Directory Access Protocol – a protocol for accessing directory information. Windows Active Directory implements LDAP. • TCP / 389 • TCP / 636 for SSL protected access Telnet (140) Telnet - A virtual network terminal, a way of remotely simulating terminals (such as vt100) to control network devices and servers • TCP / 23 Problems • No encryption SSH (141) SSH – Secure Shell, a secure replacement for telnet functionality as well as tunneling • • • • TCP / 22 Traffic is encrypted Can use digital signatures for authentication Used to tunnel other insecure network protocols Kerberos (140) Kerberos (140) A network authentication protocol designed from MITs project Athena. Kerberos tries to ensure authentication security in an insecure environment • Used in Windows2000+ and some Unix • Allows for single sign on • Never transfers passwords • Uses PRIVATE key encryption to verify Identifications • Avoids replay attacks • TCP / 88 and UDP / 88 Kerberos Components (n/b) • Principals – users or network services • KDC – Key Distribution Center, stores secret keys (passwords) for principals • Tickets – Ticket Granting Ticket (TGT) gets you more tickets – Service Tickets – access to specific network services (ex. File sharing) • Realms – a grouping of principals that a KDC provides service for, looks like a domain name – Example: somedepartment.mycompany.com Kerberos Concerns (n/b) • Computers must have clocks synchronized within 5 minutes of each other • Tickets are stored on the workstation. If the workstation is compromised your identity can be forged. • Single point of failure if not backup KDC • If your KDC is hacked, security is lost • KDC is a single point of failure and performance bottleneck… must be scalable. • Often hard for admins and end users • Still vulnerable to password guessing attacks RDP RDP (140) Remote Desktop Protocol • A Microsoft remote desktop protocol • Encryption with RC4 (newer versions of RDP) • Audio, printer, and file redirection • TCP / 3389 Email Protocols SMTP (141) Simple Mail Transport Protocol – method of moving email from sender to receiver • TCP / 25 Problems • No encryption • No authentication Common server software • Sendmail • Exchange • Lotus Notes • Postfix POP (141) Post Office Protocol – used to move email from server to clients. Email is downloaded to client. It is not very scalable or useful when reading email from multiple different computers. • TCP / 110 • TCP / 995 when using SSL By default (not using SSL) • No encryption IMAP Internet Message Access Protocol – Used to access email stored on server. Much more efficient and scalable than POP. Mail is retained on server rather than downloaded to clients. • TCP / 143 • TCP / 993 when using SSL By default (not using SSL) • No encryption Remote Access Protocols PPTP (142) Point to Point Tunneling protocol • Lead by Microsoft protocol for tunneling VPN • Uses TCP port 1723 (must keep open on firewall) • Uses RC4 encryption with 40 or 128 key • Generally implemented in software L2TP (142) Layer 2 Tunneling Protocol • Cisco protocol • Designed for use over multiple different networks including Layer 2 networks (ATM, Frame Relay etc) • Uses UDP port 1701 (must allow firewall access) • Generally implemented in hardware Problems • Doesn’t encrypt data, though can be combined with IPSec to do encryption IP Sec (142) • Intended to add security to IPv6, back ported to IPv4 • Can provide Integrity and Confidentiality as well as data origin authentication. • Uses additional headers – AH – ESP • Tunnel, or Transport • Uses Security Associations (SA) • Uses IP protocol 50 ESP headers, 51 for AH headers. Routing Protocols RIP (143) Routing Information Protocol – Distance Vector protocol used in small internal networks OSPF (143) Open Shortest First – Link State algorithm used in larger internal networks BGP (143) Border Gateway Protocol – External routing protocol that is used to interconnect networks of different organizations. Antiquated Protocols NetBEUI (143) NetBIOS Extended User Interface – simple protocol to connect computers on the same physical network • Not routable • Not commonly used anymore IPX/SPX (143) Novell’s protocol used in old versions of Netware • It is routable • Not used in modern versions of Netware Appletalk (144) Apple’s old networking protocol • It is routable • Not used in modern versions of Apple OS (OS X) Understanding Ports Ports (145) Ports are endpoint identifiers. Computers use IP addresses to determine which systems are conversing, however there are multiple applications communicating on a system. Ports are used to identify which applications are communicating on a system. • 65,536 TCP ports • 65,536 UDP ports Well Known Ports (145-146) Ports below 1024 are called well known ports. These ports are reserved for services running as the administrator of a computer. Most services listen on ports in this range. These ports are defined and allocated to commonly used services. For each protocol on the next page, you should know the ports numbers they use as well as the transport protocols (TCP/UDP) used. Well known ports FTP SSH IMAP IMAPS SMTP DNS Kerberos HTTP LDAP Telnet POP POPS L2TP PPTP RDP HTTPS Ports and Security (148) Firewalls use port numbers to determine what network traffic is allowed. To allow access to a service, you have to open the port(s) related to the service in question. You should ONLY open a port if it is absolutely necessary. Any port not explicitly allowed should be implicitly denied. Port Scanners (149) A port scanner is a tool used to query a network device to determine all the ports / services that are open on for use on a system. Port scanners are important tools for both network defenders as well as attackers. nmap is probably the most popular port scanner available http://www.nmap.org Security Zones (154) It is common practice in network to group systems into different networks or zones. Each zone is either more or less trusted then the other zones. Zones are generally separated by firewalls to restrict communication between zones. Common network zones are • Internet • DMZ • Intranet • Extranet Private Addresses and NAT (152-153) Private addresses 10.x.x.x 172.16.x.x 172.31.x.x 192.168.x.x NAT is used to translate private addresses to public addresses. Bastion Host (n/b) • Bastion Host – a server that is highly locked down (hardened). Usually put in a DMZ. Network Devices and Transmission Unicast, Broadcast and Multicast (155) Hub (155) Switch (156-158) Multiple conversations can occur on a switch at the same time! Switch (156-158) • Looks at the MAC (layer 2) address. • A switch only sends traffic from the sending computer to the receiving computer, therefore stops sniffing attacks • Since switches inspect the MAC address on all traffic, a switch can be programmed to only allow certain MAC addresses to communicate, and ignore other MAC addresses. • Switches also greatly increase performance and create multiple collision domains. MAC flooding(158) Mac Flooding – Putting out tons of packets with different MAC addresses in the attempts to overfill the switches MAC tables. If this happens a switch might simply drop into “hub mode” and start simply sending traffic down each port. (see visualization next slide) MAC flooding (158) Switch Security • Ensure Physical Security of a Switch • Keep switch operating system/firmware up to date • Manage a switch from the console, or a secure connection via the management interface. • If using a management interface restrict access to authorized IP addresses or networks VLAN Routers (159) Routers connect different networks (LANS/subnets) and allow these LANs to communicate with each other. They allow traffic to leave a local network and help direct the best path to get to the destination network. • Look at IP addresses (layer 3) NOT MAC addresses • Routers do NOT forward broadcasts, as such they create different broadcasts domains! • Can statically determine routes, or dynamically • Can apply access control lists to allow or deny certain types of traffic see visualization next page Router (208) 192.168.1.0 / 255.255.255.0 10.1.2.0 / 255.255.255.0 Routers create separate LAN networks. These networks will have different IP ranges Router Security (159) • Ensure Physical Security of a Router • Keep router operating system/firmware up to date • Manage a router from the console, or a secure connection via the management interface. • If using a management interface restrict access to authorized IP addresses or networks Hubs, Routers and Switches • Hubs operate at OSI layer 1 • Traditional switches operate at OSI layer 2 • Routers operate at OSI layer 3 Older equipment • A repeater is a simple hub with only 2 ports • A bridge is a simple switch with only 2 ports Firewalls (161) Devices designed to implement and enforce an organizations network security policy. Firewalls inspect incoming / outgoing packets and compare it against an access control list in order to determine whether that network packet should be allowed to pass through or be rejected • Can be hardware or software based • Can operate on layer 4 and above Stateless Packet Filters (160) • Very basic filtering of network packets based on IP addresses, protocol and port numbers • Many routers contain this functionality • Layer 4 device Statefull firewall (162) A statefull firewall is like a packet filter, in that it has a list of rules to determine what traffic is allowed or denied, but also has the understanding of the context of a communication session. • Layer 4 device Pros / Cons? Application Firewall (163) Understands the application/data that of the protocols they are protecting. • Layer 7 device Pros / Cons? Content Filtering (164) Application firewalls and server filters can understand the data being communicated. They can filter based on content or context. Some types of content they may filter on are • SPAM • Attachments • URLS • Certificates Proxy Server An application layer device which may or may not be a firewall. Sometimes they are used for application acceleration or to enforce acceptable use policies. Sometimes they are also perform firewall functionality. Transmission Media Vampire Taps Interference (172) Different energies can cause interference with electrical signals. Two types of interference are EMI – Electromagnetic Interference • Motors and electric wires RFI – Radio Frequency Interference • Fluorescent lights, radio, computers Signal Emanation (173) When using network equipment not only are you concerned with interference, but you also must be concerned with signal emanation especially in high security environment. • Fiber is best as there is no signal emanation Cable Types Coaxial cable (174) Twisted Pair (175) Fiber Optic (175)