Securing IPv6 Backbones
... •Look at a fixed offset into the packet •Match based on the bits you find at that offset ...
... •Look at a fixed offset into the packet •Match based on the bits you find at that offset ...
CCNP-IV-ONT_Mod_4_Lesson_9
... IPsec AH is for authentication only and does not perform encryption. With tunnel mode, the ToS byte value is copied automatically from the original IP header to the tunnel header. With transport mode, the original header is used, and therefore the ToS byte is accessible. © 2006 Cisco Systems, ...
... IPsec AH is for authentication only and does not perform encryption. With tunnel mode, the ToS byte value is copied automatically from the original IP header to the tunnel header. With transport mode, the original header is used, and therefore the ToS byte is accessible. © 2006 Cisco Systems, ...
Netware - The University of New Mexico
... easy to use – NetWare makes file server disks look like local disks to your PC. – NetWare MAP command lets you assign the drive letter of your choice to any disk, directory, or subdirectory on any file server that you are logged in to. – NetWare allows you to create a login script that automatically ...
... easy to use – NetWare makes file server disks look like local disks to your PC. – NetWare MAP command lets you assign the drive letter of your choice to any disk, directory, or subdirectory on any file server that you are logged in to. – NetWare allows you to create a login script that automatically ...
Memphis - Andrew.cmu.edu - Carnegie Mellon University
... • exploiting known vulnerabilities • exploiting protocol flaws • examining source and binary files for new security flaws • abusing anonymous FTP, web servers, email • installing sniffer programs • IP source address spoofing • denial of service attacks • widespread, automated scanning of the Interne ...
... • exploiting known vulnerabilities • exploiting protocol flaws • examining source and binary files for new security flaws • abusing anonymous FTP, web servers, email • installing sniffer programs • IP source address spoofing • denial of service attacks • widespread, automated scanning of the Interne ...
NATIONAL OPEN UNIVERSITY OF NIGERIA SCHOOL OF SCIENCE AND TECHNOLOGY 1
... Technology (CTT). A computer network is simply two or more computers connected together so they can exchange information. A small network can be as simple as two computers linked together by a single cable. This course introduces you to the hardware and software needed for a network, and explains ho ...
... Technology (CTT). A computer network is simply two or more computers connected together so they can exchange information. A small network can be as simple as two computers linked together by a single cable. This course introduces you to the hardware and software needed for a network, and explains ho ...
UNIT - Webs
... communication system made up of a combination of hardware (physical equipment) and software (programs). The effectiveness of a data communications system depends on four fundamental characteristics: delivery, accuracy, timeliness, and jitter. 1. Delivery. The system must deliver data to the correct ...
... communication system made up of a combination of hardware (physical equipment) and software (programs). The effectiveness of a data communications system depends on four fundamental characteristics: delivery, accuracy, timeliness, and jitter. 1. Delivery. The system must deliver data to the correct ...
(Radmin) 2.2 - User Manual
... authentication method (MD5 and Twofish). This method is similar to the authentication method used in Windows NT, but uses a much more sophisticated encoding. • Radmin prevents incorrect Server configurations. Radmin Server 2.2 does not allow empty passwords. • Radmin Server 2.2 actively protects its ...
... authentication method (MD5 and Twofish). This method is similar to the authentication method used in Windows NT, but uses a much more sophisticated encoding. • Radmin prevents incorrect Server configurations. Radmin Server 2.2 does not allow empty passwords. • Radmin Server 2.2 actively protects its ...
IPv6 - Labs
... – Either we all move and move the entire Internet to supporting IPv6 by around 2015 – Or we’ll lose focus and momentum and turn our collective attention to engineering insane adornments for CDNs, ALGs and similar active middleware in an all-IPv4 network ...
... – Either we all move and move the entire Internet to supporting IPv6 by around 2015 – Or we’ll lose focus and momentum and turn our collective attention to engineering insane adornments for CDNs, ALGs and similar active middleware in an all-IPv4 network ...
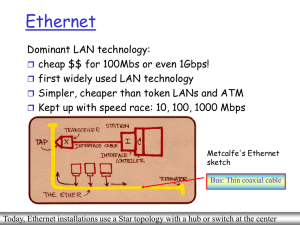
Ethernet Switches
... • connects hosts to base station or another wireless host • e.g. 802.11a, 802.11g, 802.11b, UMTS/WCDMA, GSM, etc. Base Station • sends/receives packets to and from a wireless host associated with base station; coordinates multiple transmissions of hosts • e.g. cell towers (cellular networks), Access ...
... • connects hosts to base station or another wireless host • e.g. 802.11a, 802.11g, 802.11b, UMTS/WCDMA, GSM, etc. Base Station • sends/receives packets to and from a wireless host associated with base station; coordinates multiple transmissions of hosts • e.g. cell towers (cellular networks), Access ...
Sensor Networks for Medical Care
... sensors, collecting detailed real-time data on physiological status can be greatly simplified. However, there is a significant gap between existing sensor network systems and the needs of medical care. In particular, medical sensor networks must support multicast routing topologies, node mobility, a ...
... sensors, collecting detailed real-time data on physiological status can be greatly simplified. However, there is a significant gap between existing sensor network systems and the needs of medical care. In particular, medical sensor networks must support multicast routing topologies, node mobility, a ...
Comparing different handover schemes in IP based Micro
... Typically, fixed hosts connected to the Internet remain online for extended periods of time even though most of the time they do not communicate. Mobile subscribers connected to the wireless Internet will expect similar services. If mobile hosts were to maintain their location information in support ...
... Typically, fixed hosts connected to the Internet remain online for extended periods of time even though most of the time they do not communicate. Mobile subscribers connected to the wireless Internet will expect similar services. If mobile hosts were to maintain their location information in support ...
Efficient Micro-Mobility using Intra-domain Multicast
... provides a more scalable and robust approach, and we develop efficient, yet simple, mechanisms to realize it. Furthermore, we conduct extensive simulations to compare the handover performance of our approach to other main approaches to micro-mobility. Results show that our scheme provides, on averag ...
... provides a more scalable and robust approach, and we develop efficient, yet simple, mechanisms to realize it. Furthermore, we conduct extensive simulations to compare the handover performance of our approach to other main approaches to micro-mobility. Results show that our scheme provides, on averag ...
01101014
... At the end of our thesis, we acknowledge all the persons who have cooperated and worked together with us. Without their help, this report writing would have been absolutely impossible. So our earnest tanks to them for their collaboration and support. We would like to thank Yousuf Mahbubul Islam Ph.D ...
... At the end of our thesis, we acknowledge all the persons who have cooperated and worked together with us. Without their help, this report writing would have been absolutely impossible. So our earnest tanks to them for their collaboration and support. We would like to thank Yousuf Mahbubul Islam Ph.D ...
Cisco Network Registrar 7.2 - Lyme Computer Systems, Inc
... provisioning system. Additionally, Cisco Network Registrar plays an important role in service activation for data, voice-over-IP (VoIP), and mobile services. As IP networks continue to experience exponential growth in size, complexity, and traffic volume, and as the volume of IP addresses and device ...
... provisioning system. Additionally, Cisco Network Registrar plays an important role in service activation for data, voice-over-IP (VoIP), and mobile services. As IP networks continue to experience exponential growth in size, complexity, and traffic volume, and as the volume of IP addresses and device ...
ECI Emanuel Nachum CANTO 2006
... Large share are at GbE & 10 GbE rates Optical transport delivers majority of IP based services WDM – a service delivery and transport vehicle Optical Networks Division ...
... Large share are at GbE & 10 GbE rates Optical transport delivers majority of IP based services WDM – a service delivery and transport vehicle Optical Networks Division ...
Cisco Structured Wireless-Aware Network
... • AP & bridge security misconfiguration detection and alerts • Proactive fault and performance monitoring of APs, bridges • Authentication server and attached switch/router monitoring • AP/Bridge summary and utilization reports ...
... • AP & bridge security misconfiguration detection and alerts • Proactive fault and performance monitoring of APs, bridges • Authentication server and attached switch/router monitoring • AP/Bridge summary and utilization reports ...
SMART WIRELESS GATEWAY HART MANUAL
... This section describes how to connect to the Gateway for the first time and what settings should be configured before placing it on a live control network. It is important to note that some Gateways are used in stand-alone applications and do not reside on a network. In these cases it is still impor ...
... This section describes how to connect to the Gateway for the first time and what settings should be configured before placing it on a live control network. It is important to note that some Gateways are used in stand-alone applications and do not reside on a network. In these cases it is still impor ...
Wide-Area Ethernet Network Configuration for System
... between the control centers. The crosslink traffic from A to B consists solely of the aggregated incoming values from all the substations tied to LAN A, made available to central controller B so it can remain in service for situations of maintenance or of failure of a substation source somewhere in ...
... between the control centers. The crosslink traffic from A to B consists solely of the aggregated incoming values from all the substations tied to LAN A, made available to central controller B so it can remain in service for situations of maintenance or of failure of a substation source somewhere in ...
GPSDTN: Predictive Velocity-Enabled Delay-Tolerant
... remote areas that are connected by highly dynamic networks. DTN is like current email systems in the sense that each bundle or message has an address, is forwarded toward the recipient via a series of servers (hosts, nodes), each of which stores and keeps trying to forward the message until it eithe ...
... remote areas that are connected by highly dynamic networks. DTN is like current email systems in the sense that each bundle or message has an address, is forwarded toward the recipient via a series of servers (hosts, nodes), each of which stores and keeps trying to forward the message until it eithe ...
AnywhereUSB datasheet
... CLI and AnywhereUSB web configuration tool, Digi Remote Manager® (cloud based) firmware uploads and monitoring of ports ...
... CLI and AnywhereUSB web configuration tool, Digi Remote Manager® (cloud based) firmware uploads and monitoring of ports ...