Chapter 3 Transport Layer
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
EE29 Shilpi Agrawal - RJIT paper
... wireless but the nodes cannot move from their place. An Infrastructure less Wireless Network is the wireless networks in which the nodes can move from one place to another place and thus has no fix infrastructure or topology. This type of networks crate dynamic topology. The nodes of these type of n ...
... wireless but the nodes cannot move from their place. An Infrastructure less Wireless Network is the wireless networks in which the nodes can move from one place to another place and thus has no fix infrastructure or topology. This type of networks crate dynamic topology. The nodes of these type of n ...
CCNA3 3.0-04 Questions Review of Switching
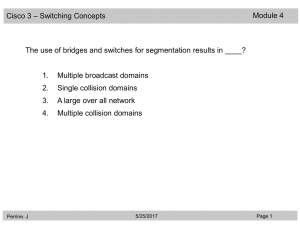
... After a collision occurs on a half-duplex Ethernet network, how does a transmitting host proceed? (Choose two.) ...
... After a collision occurs on a half-duplex Ethernet network, how does a transmitting host proceed? (Choose two.) ...
(1.8 MB)
... • You can start ProjectorView by directly entering the URL of the Web browser “http://IP address you set” instead of by clicking the External Browser button. • When you are using a proxy server, don’t enable the proxy when accessing this IP address. • You can open only 1 browser screen from the d ...
... • You can start ProjectorView by directly entering the URL of the Web browser “http://IP address you set” instead of by clicking the External Browser button. • When you are using a proxy server, don’t enable the proxy when accessing this IP address. • You can open only 1 browser screen from the d ...
Multi-Layer versus Single-Layer MG
... Summary for Offline case Near-optimal ILP model perform better Single-Layer MG-OXC requires up to 20% fewer ports than Multi-Layer MG-OXC With appropriate wavelength granuularity (W=4), MG-OXC can achieve more than 50% ports reduction when compared to ordinary OXCs – The maximum size of a node over ...
... Summary for Offline case Near-optimal ILP model perform better Single-Layer MG-OXC requires up to 20% fewer ports than Multi-Layer MG-OXC With appropriate wavelength granuularity (W=4), MG-OXC can achieve more than 50% ports reduction when compared to ordinary OXCs – The maximum size of a node over ...
Media Streaming over the Internet
... the current point in the media’s timeline and the user’s settings (such as the sound volume level). ! It only uses the exact network bandwidth it really needs. If the streaming content exceeds the connection speed, some data packets get lost and the content may break up. ! It allows for streaming tr ...
... the current point in the media’s timeline and the user’s settings (such as the sound volume level). ! It only uses the exact network bandwidth it really needs. If the streaming content exceeds the connection speed, some data packets get lost and the content may break up. ! It allows for streaming tr ...
LAN - Temple CIS
... The Link Layer and LANs A note on the use of these Powerpoint slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs ...
... The Link Layer and LANs A note on the use of these Powerpoint slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs ...
plaNET - Semantic Scholar
... us to dimension the buffering space available for each class differently. As discussed in section 6.2 (see also [23] for details), the network resources allocated to a connection determine the amount of traffic it is entitled to send. It can, however, be allowed to send in excess of its allocation, ...
... us to dimension the buffering space available for each class differently. As discussed in section 6.2 (see also [23] for details), the network resources allocated to a connection determine the amount of traffic it is entitled to send. It can, however, be allowed to send in excess of its allocation, ...
(DTN) Program
... DTN Network Persistence Can Solve Fundamental Internet Application Shortfalls • DTN makes applications over disrupted networks robust • DTN is also an Opportunity to solve Fundamental Problems we’ve never before had a handle on, using Network-Managed Persistence ...
... DTN Network Persistence Can Solve Fundamental Internet Application Shortfalls • DTN makes applications over disrupted networks robust • DTN is also an Opportunity to solve Fundamental Problems we’ve never before had a handle on, using Network-Managed Persistence ...
xia-nsdi2012-public
... • Service, content, mobility, and cloud did not receive much attention before as now • Yet more networking styles may be useful in the future – E.g., DTN, wide-area multicast, …? Problem: Introducing additional communication types to the existing network can be very challenging Can we support future ...
... • Service, content, mobility, and cloud did not receive much attention before as now • Yet more networking styles may be useful in the future – E.g., DTN, wide-area multicast, …? Problem: Introducing additional communication types to the existing network can be very challenging Can we support future ...
Linux Networking and Security
... create a binary file of public key gpg –a –o frank.key –export [email protected] create the text of public key, so that it can be pasted into ...
... create a binary file of public key gpg –a –o frank.key –export [email protected] create the text of public key, so that it can be pasted into ...
International Telecommunication Union
... Link Aggregation was originally standardized in 802.3ad-2000 (it has been later incorporated in 802.3 as clause 43 of 802.3-2005). Since 2000 there has been a growing demand that Link Aggregation should not be specific to an individual MAC technology, and that the maintenance work should be done in ...
... Link Aggregation was originally standardized in 802.3ad-2000 (it has been later incorporated in 802.3 as clause 43 of 802.3-2005). Since 2000 there has been a growing demand that Link Aggregation should not be specific to an individual MAC technology, and that the maintenance work should be done in ...
General
... A good security product must defend against every possible attack, even attacks that haven’t been invented yet! Attackers often only need find one flaw in order to defeat a system. In addition, they can collude & conspire. They can wait for technology to give them the edge. But don’t worry ...
... A good security product must defend against every possible attack, even attacks that haven’t been invented yet! Attackers often only need find one flaw in order to defeat a system. In addition, they can collude & conspire. They can wait for technology to give them the edge. But don’t worry ...
SDN Getting Started Guide
... Programmable data plane—ideally, virtual networks should forward packets at rates that are comparable to native, hardware-based approaches. Virtualization of the network—virtualization can occur in two ways: (1) Use of virtual compute (VMs), virtual switches, and virtual storage to produce elastic, ...
... Programmable data plane—ideally, virtual networks should forward packets at rates that are comparable to native, hardware-based approaches. Virtualization of the network—virtualization can occur in two ways: (1) Use of virtual compute (VMs), virtual switches, and virtual storage to produce elastic, ...
Title: First Slide in a Presentation
... Module 9 – Configure Filtering on a PIX Security Appliance ...
... Module 9 – Configure Filtering on a PIX Security Appliance ...
TCP - Rudra Dutta
... 2. After ACKing the FIN, the receiver can still send data on its part of the connection (halfclose) 3. Finally, the receiver closes its part of the ...
... 2. After ACKing the FIN, the receiver can still send data on its part of the connection (halfclose) 3. Finally, the receiver closes its part of the ...
Adaptive Usage of Cellular and WiFi Bandwidth
... 16]. Thus, both to address infrastructure limits, as well as to abide by user cost and coverage preferences, it makes sense to consider optimized network communication in which cellular data traffic is offloaded to other mediums (e.g. WiFi) where possible. If WiFi is only intermittently available, o ...
... 16]. Thus, both to address infrastructure limits, as well as to abide by user cost and coverage preferences, it makes sense to consider optimized network communication in which cellular data traffic is offloaded to other mediums (e.g. WiFi) where possible. If WiFi is only intermittently available, o ...
What is an L3 Master Device?
... The Linux networking stack has supported policy routing with FIB rules since v2.2. Rules can use the oif (outgoing interface index) or iif (incoming interface index) to direct lookups to a specific table. The l3mdev code leverages this capability to direct lookups to the table associated with the ma ...
... The Linux networking stack has supported policy routing with FIB rules since v2.2. Rules can use the oif (outgoing interface index) or iif (incoming interface index) to direct lookups to a specific table. The l3mdev code leverages this capability to direct lookups to the table associated with the ma ...
Dictionary of IBM and Computing Terminology
... Boolean operation 1. n. Any operation in which each of the operands and the result take one of two values. 2. n. An operation that follows the rules of Boolean algebra. boot v. To prepare a computer system for operation by loading an operating system. bottleneck n. A hardware or software component t ...
... Boolean operation 1. n. Any operation in which each of the operands and the result take one of two values. 2. n. An operation that follows the rules of Boolean algebra. boot v. To prepare a computer system for operation by loading an operating system. bottleneck n. A hardware or software component t ...
Manus 1 - IFM - Linköping University
... deviation, σ. Here, a kurtosis value of 10/3 and a standard deviation of one were used. The constant K normalized the distribution so that the probabilities of all possible links were summed to one. With the random linking scenario, all animal holdings have the same probability to connect to each ot ...
... deviation, σ. Here, a kurtosis value of 10/3 and a standard deviation of one were used. The constant K normalized the distribution so that the probabilities of all possible links were summed to one. With the random linking scenario, all animal holdings have the same probability to connect to each ot ...
pdf - at www.arxiv.org.
... when the owner is away, but in the closed access mode when the owner is back. Third, it may be user-dependent, as users who have subscribed to different data plans or Wi-Fi services (e.g., Skype Wi-Fi) can have different privileges to access different Wi-Fi networks. Given these practical considerat ...
... when the owner is away, but in the closed access mode when the owner is back. Third, it may be user-dependent, as users who have subscribed to different data plans or Wi-Fi services (e.g., Skype Wi-Fi) can have different privileges to access different Wi-Fi networks. Given these practical considerat ...
Tata Consultancy Services
... applications and database systems with no change of IP address. Virtual cluster switching and Brocade VCS Fabric technologies improved network utilization and maximized application availability by eliminating the spanning tree protocol and providing active connections to redundant links with full th ...
... applications and database systems with no change of IP address. Virtual cluster switching and Brocade VCS Fabric technologies improved network utilization and maximized application availability by eliminating the spanning tree protocol and providing active connections to redundant links with full th ...
Campus Fabric Design Guide - CVD - October 2016
... RFC 6830 and other RFCs define LISP as a network architecture and set of protocols that implement a new semantic for IP addressing and forwarding. In traditional IP networks, the IP address is used to identify both an endpoint and its physical location as part of a subnet assignment on a router. In ...
... RFC 6830 and other RFCs define LISP as a network architecture and set of protocols that implement a new semantic for IP addressing and forwarding. In traditional IP networks, the IP address is used to identify both an endpoint and its physical location as part of a subnet assignment on a router. In ...
Template
... 1. Describe standard and extended ACLs 2. Describe applications of standard and extended ACLs 3. Describe the relationship between topology and flow for ACLs and describe the proper selection of ACL types for particular topologies (ACL design methodology) 4. Describe how to implement ACLs with SDM 5 ...
... 1. Describe standard and extended ACLs 2. Describe applications of standard and extended ACLs 3. Describe the relationship between topology and flow for ACLs and describe the proper selection of ACL types for particular topologies (ACL design methodology) 4. Describe how to implement ACLs with SDM 5 ...
manet-intro
... protocol which provides one or more modes of operation, each mode specialized for efficient operation in a given mobile networking “context”, where a context is a predefined set of network characteristics. ...
... protocol which provides one or more modes of operation, each mode specialized for efficient operation in a given mobile networking “context”, where a context is a predefined set of network characteristics. ...