3rd Edition, Chapter 5
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully uti ...
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully uti ...
Random Graph Theory - Jackson State University
... Just based on the N and L values for the real networks, we could predict (according to the principles of Random Network Theory) that: – All real networks should have a giant component (since their exceeds
...
... Just based on the N and L values for the real networks, we could predict (according to the principles of Random Network Theory) that: – All real networks should have a giant component (since their
IOSR Journal of Computer Engineering (IOSR-JCE)
... Mobile Ad Hoc Networks (MANETs) is a class of wireless networks that have been researched widely over the recent years [1]. MANETs do not require the support of wired access points or base stations for intercommunication. A mobile ad hoc network, unlike a static network, has no infrastructure. It is ...
... Mobile Ad Hoc Networks (MANETs) is a class of wireless networks that have been researched widely over the recent years [1]. MANETs do not require the support of wired access points or base stations for intercommunication. A mobile ad hoc network, unlike a static network, has no infrastructure. It is ...
VLAN History
... Allows creation of two or more virtual switches from a single switch. Assigning individual ports to a specific virtual switch. First products allowed switching of multiple segments on a single switch, as well as offering a monetary advantage over switched Ethernet ports which cost $700 or more a ...
... Allows creation of two or more virtual switches from a single switch. Assigning individual ports to a specific virtual switch. First products allowed switching of multiple segments on a single switch, as well as offering a monetary advantage over switched Ethernet ports which cost $700 or more a ...
CS412 Computer Networks - Winona State University
... End-to-end layer Talk to destination machine directly (virtually) Layers 4 through 7 are end-to-end Layers 1 through 3 are node-to-node (chained) ...
... End-to-end layer Talk to destination machine directly (virtually) Layers 4 through 7 are end-to-end Layers 1 through 3 are node-to-node (chained) ...
Leveraging Identity-based Cryptography for Node ID Assignment in
... node’s public key is synonymous with its ID. Key expiry can be incorporated in an ID-based system by including the current date or time as part of the public key, along with the node ID [2]. However, the validity period affects the security of the system; if the time period is too short, updating th ...
... node’s public key is synonymous with its ID. Key expiry can be incorporated in an ID-based system by including the current date or time as part of the public key, along with the node ID [2]. However, the validity period affects the security of the system; if the time period is too short, updating th ...
ppt in chapter 12
... The standard IP ACLs controls the telnet access to the router. The access-class command enables you to accomplish this. The syntax of this command is: access-class standard_ACL_# in|out ...
... The standard IP ACLs controls the telnet access to the router. The access-class command enables you to accomplish this. The syntax of this command is: access-class standard_ACL_# in|out ...
SNMP
... device. It is performed to retrieve one or more values from the managed device. GET NEXT: This operation is similar to the GET. The significant difference is that the GET NEXT operation retrieves the value of the next Object Identifier (OID) in the MIB tree. GET BULK: The GET BULK operation is u ...
... device. It is performed to retrieve one or more values from the managed device. GET NEXT: This operation is similar to the GET. The significant difference is that the GET NEXT operation retrieves the value of the next Object Identifier (OID) in the MIB tree. GET BULK: The GET BULK operation is u ...
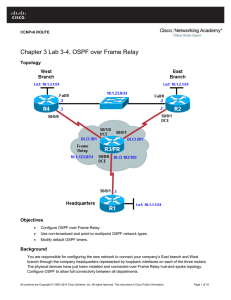
Chapter 3 Lab 3-4, OSPF over Frame Relay
... Frame Relay is inherently a non-broadcast multi-access (NBMA) network. In this step, you configure OSPF for hub-and-spoke over Frame Relay using the NBMA OSPF network type, which is the default for Frame Relay physical interfaces and multipoint-type subinterfaces. HQ is the hub; EAST and WEST are th ...
... Frame Relay is inherently a non-broadcast multi-access (NBMA) network. In this step, you configure OSPF for hub-and-spoke over Frame Relay using the NBMA OSPF network type, which is the default for Frame Relay physical interfaces and multipoint-type subinterfaces. HQ is the hub; EAST and WEST are th ...
yun-MPLS - KEMT FEI TUKE
... MPLS provides two options to set up an LSP hop-by-hop routing Each LSR independently selects the next hop for a given FEC. LSRs support any available routing protocols (OSPF, ATM …). explicit routing Is similar to source routing. The ingress LSR specifies the list of nodes through which the pa ...
... MPLS provides two options to set up an LSP hop-by-hop routing Each LSR independently selects the next hop for a given FEC. LSRs support any available routing protocols (OSPF, ATM …). explicit routing Is similar to source routing. The ingress LSR specifies the list of nodes through which the pa ...
Very good – all requirements aptly met. Minor additions/corrections
... completed. The wireless network device has been tested and shown to successful send and receive data in a stand-alone fashion. ...
... completed. The wireless network device has been tested and shown to successful send and receive data in a stand-alone fashion. ...
Introduction - School of Computing and Information Sciences
... Is to transform a raw transmission facility into a line that appears free of undetected transmission errors. ...
... Is to transform a raw transmission facility into a line that appears free of undetected transmission errors. ...
Slide 1
... Information Centric Networks: Built upon the need to separate the what from the where Most communications are exchange of data which does not require to set-up a host-to-host path ...
... Information Centric Networks: Built upon the need to separate the what from the where Most communications are exchange of data which does not require to set-up a host-to-host path ...
ppt
... Periodic Updates: Updates to the routing tables are sent at the end of a certain time period. A typical value is 30 seconds. Triggered Updates: If a metric changes on a link, a router immediately sends out an update without waiting for the end of the update period. Full Routing Table Update: Most di ...
... Periodic Updates: Updates to the routing tables are sent at the end of a certain time period. A typical value is 30 seconds. Triggered Updates: If a metric changes on a link, a router immediately sends out an update without waiting for the end of the update period. Full Routing Table Update: Most di ...
S02_M2MARCHITECTURE_ELLOUMI - Docbox
... MACHINE” • Identification, tracking, monitoring, metering, … • Semantically structured and shared data… ...
... MACHINE” • Identification, tracking, monitoring, metering, … • Semantically structured and shared data… ...
IOSR Journal of Electronics and Communication Engineering (IOSRJECE)
... The research in this MANET area has continued with prominent studies on routing protocols such as Ad hoc On-demand Distance Vector (AODV), Destination-Sequenced Distance-Vector Routing protocol, (DSDV) and Dynamic Source Routing Protocol (DSR). Several studies have been done on the performance evalu ...
... The research in this MANET area has continued with prominent studies on routing protocols such as Ad hoc On-demand Distance Vector (AODV), Destination-Sequenced Distance-Vector Routing protocol, (DSDV) and Dynamic Source Routing Protocol (DSR). Several studies have been done on the performance evalu ...
CROSS-ROAD: CROSS-layer Ring Overlay for AD hoc networks
... Pastry uses a DHT to convert nodes and data identifiers on logical addresses that are used to route messages through the network There is no correspondence between logical and ...
... Pastry uses a DHT to convert nodes and data identifiers on logical addresses that are used to route messages through the network There is no correspondence between logical and ...
The Virtual Local Area Network (VLAN) Technology
... amounts of layer 3 intelligence into their switches, enabling functions normally associated with routing. Furthermore, “layer 3 aware” or “multi-layer” switches often have the packet-forwarding function of routing built into ASIC chip sets, greatly improving performance over CPU based routers. Never ...
... amounts of layer 3 intelligence into their switches, enabling functions normally associated with routing. Furthermore, “layer 3 aware” or “multi-layer” switches often have the packet-forwarding function of routing built into ASIC chip sets, greatly improving performance over CPU based routers. Never ...
Development of DNS
... Large numbers of low speed links Poor or no implementation of caching Hard to measure perfomance • Too many changing parameters (network changes, new DNS software) ...
... Large numbers of low speed links Poor or no implementation of caching Hard to measure perfomance • Too many changing parameters (network changes, new DNS software) ...
Unicast Routing Protocols
... An internet is a combination of networks connected by routers. When a datagram goes from a source to a destination, it will probably pass through many routers until it reaches the router attached to the destination network. ...
... An internet is a combination of networks connected by routers. When a datagram goes from a source to a destination, it will probably pass through many routers until it reaches the router attached to the destination network. ...
After Detection of an Incident
... resources to be unavailable during the time the incident was reported? Was there an unscheduled and unreported outage of network service provider that caused resources to be unavailable during the time the suspected incident was reported? Was the affected system recently upgraded, patched, reconfigu ...
... resources to be unavailable during the time the incident was reported? Was there an unscheduled and unreported outage of network service provider that caused resources to be unavailable during the time the suspected incident was reported? Was the affected system recently upgraded, patched, reconfigu ...