Password Security
... choosing a sentence that incorporates something unique about the website or account, and then using the first letter of each word as your password. For example the sentence: "This is my August password for the Center for Internet Security website." would become "TimAp4tCfISw." Since a strong passwor ...
... choosing a sentence that incorporates something unique about the website or account, and then using the first letter of each word as your password. For example the sentence: "This is my August password for the Center for Internet Security website." would become "TimAp4tCfISw." Since a strong passwor ...
Document
... • In a true IP architecture, every phone will be an Internet server with a global (IPv6) address – any host anywhere can send it packets ...
... • In a true IP architecture, every phone will be an Internet server with a global (IPv6) address – any host anywhere can send it packets ...
Fundamentals of Multimedia 2 nd ed., Chapter 15
... Mbps, which is faster than most DSL accesses that are up to 10 Mbps. • In most areas, both DSL and cable accesses are available, although some areas may have only one choice. ...
... Mbps, which is faster than most DSL accesses that are up to 10 Mbps. • In most areas, both DSL and cable accesses are available, although some areas may have only one choice. ...
EE579S Computer Security
... • Mobile IPv4 Challenge/Response Extensions: RFC 4721 • Reverse Tunneling for Mobile IP: RFC ...
... • Mobile IPv4 Challenge/Response Extensions: RFC 4721 • Reverse Tunneling for Mobile IP: RFC ...
(Seven Layers of Open Systems Interconnection (OSI
... Student C read about Layers 4 and 3 in the Four layers of TCP/IP model text below Student D read about layers 2 and 1 in the Four layers of TCP/IP model text below Student A: If network communications need to happen without any trouble, many problems must be solved. Coordinating all these problems i ...
... Student C read about Layers 4 and 3 in the Four layers of TCP/IP model text below Student D read about layers 2 and 1 in the Four layers of TCP/IP model text below Student A: If network communications need to happen without any trouble, many problems must be solved. Coordinating all these problems i ...
nGenius Subscriber Intelligence
... nGenius® Subscriber Intelligence takes IP performance management and analysis of mobile networks to the next level by seamlessly integrating core-to-access data plane and control plane session analysis with deep-dive packet and protocol analysis to enable rapid, more efficient troubleshooting and is ...
... nGenius® Subscriber Intelligence takes IP performance management and analysis of mobile networks to the next level by seamlessly integrating core-to-access data plane and control plane session analysis with deep-dive packet and protocol analysis to enable rapid, more efficient troubleshooting and is ...
Evaluating OBS by Effective Utilization
... occupied, a new higher priority burst can preempt a lower priority burst on the output trunk. The entire preempted lower priority burst is then dropped. Problems: Preempting the entire burst is not efficient Difficult to control in a distributed system ...
... occupied, a new higher priority burst can preempt a lower priority burst on the output trunk. The entire preempted lower priority burst is then dropped. Problems: Preempting the entire burst is not efficient Difficult to control in a distributed system ...
Enabling Stateful Networking Solutions with Mellanox Indigo (NPS)
... what is running on them. Mellanox is focusing n this stateful infrastructure and providing the best environment for it in terms of scale, performance and flexibility. This enables application developers to focus on the development of features developed on top of the stateful infrastructure. Mellanox ...
... what is running on them. Mellanox is focusing n this stateful infrastructure and providing the best environment for it in terms of scale, performance and flexibility. This enables application developers to focus on the development of features developed on top of the stateful infrastructure. Mellanox ...
Connecting computers
... Wireless network benefits, continued Production on manufacturing shop floors can be readily evaluated Wireless network infrastructure can be moved to a new building more easily The cost of providing network access to buildings is substantially lowered ...
... Wireless network benefits, continued Production on manufacturing shop floors can be readily evaluated Wireless network infrastructure can be moved to a new building more easily The cost of providing network access to buildings is substantially lowered ...
Network-on-Chip Architectures and Building Blocks
... No buffers mean less implementation cost If more than one packet shall be routed to the same output, one has to be ...
... No buffers mean less implementation cost If more than one packet shall be routed to the same output, one has to be ...
Optical Network Infrastructure for GRID
... During the past years it has become evident to the technical community that computational resources cannot keep up with the demands generated by some applications. As an example, particle physics experiments [1, 2] produce more data than can be realistically processed and stored in one location (i.e ...
... During the past years it has become evident to the technical community that computational resources cannot keep up with the demands generated by some applications. As an example, particle physics experiments [1, 2] produce more data than can be realistically processed and stored in one location (i.e ...
Threats To Windows Users and Countermeasures
... to this threat, a common source of security problem under Windows operating systems. The flaw in an unsecured windows shares can be exploited by intruders in an automated way to place tools on large numbers of Windows based computers attached to the Internet. An unsecured windows shares together wit ...
... to this threat, a common source of security problem under Windows operating systems. The flaw in an unsecured windows shares can be exploited by intruders in an automated way to place tools on large numbers of Windows based computers attached to the Internet. An unsecured windows shares together wit ...
Top-Down Network Design
... • A phone needs to talk to a server or phone switch that understands phone numbers, IP addresses, capabilities negotiation, and so on. ...
... • A phone needs to talk to a server or phone switch that understands phone numbers, IP addresses, capabilities negotiation, and so on. ...
of the OSI model.
... In bus topology, a bridge is a traffic controller. It can divide a long bus into smaller segments so that each segment is independent trafficwise. The bridge uses a table to decide if the frame needs to be forwarded to another segment. With a bridge, two or more pairs of stations can communi ...
... In bus topology, a bridge is a traffic controller. It can divide a long bus into smaller segments so that each segment is independent trafficwise. The bridge uses a table to decide if the frame needs to be forwarded to another segment. With a bridge, two or more pairs of stations can communi ...
Solving remote access problems
... All SSL VPN deployments link to external authentication servers Common examples are RADIUS (which would include SecurID-type services) and LDAP Advanced devices talk directly to Windows via Kerberos Certificate-based authentication is a possibility, but is unusual ...
... All SSL VPN deployments link to external authentication servers Common examples are RADIUS (which would include SecurID-type services) and LDAP Advanced devices talk directly to Windows via Kerberos Certificate-based authentication is a possibility, but is unusual ...
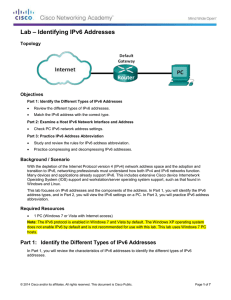
8.2.5.4 Lab – Identifying IPv6 Addresses
... If we read an IPv6 address starting from the left, the first (or far left) hextet identifies the IPv6 address type. For example, if the IPv6 address has all zeros in the far left hextet, then the address is possibly a loopback address. 0000:0000:0000:0000:0000:0000:0000:0001 = loopback address ::1 = ...
... If we read an IPv6 address starting from the left, the first (or far left) hextet identifies the IPv6 address type. For example, if the IPv6 address has all zeros in the far left hextet, then the address is possibly a loopback address. 0000:0000:0000:0000:0000:0000:0000:0001 = loopback address ::1 = ...
Network Monitoring
... It is a freely LAN traffic analyzer for MS-DOS with an Ethernet or Token Ring controller It basically captures each packet running through a LAN and provides various information on the packet. It can be used to check which host is generating the most traffic, which host is sending to which host, and ...
... It is a freely LAN traffic analyzer for MS-DOS with an Ethernet or Token Ring controller It basically captures each packet running through a LAN and provides various information on the packet. It can be used to check which host is generating the most traffic, which host is sending to which host, and ...
Route Optimization in IP Networks Jennifer Rexford
... of the complexity of the underlying routing protocols and the diversity of the network objectives. The conventional IP routing protocols were not designed with optimization in mind, and the optimization of the tunable parameters is computationally difficult even for the simplest of metrics (e.g., su ...
... of the complexity of the underlying routing protocols and the diversity of the network objectives. The conventional IP routing protocols were not designed with optimization in mind, and the optimization of the tunable parameters is computationally difficult even for the simplest of metrics (e.g., su ...
T201xxxx MM7 – Use Cases, Goals and Requirements
... VASP controls basic service charging VASP should get individual „low-credit“ or „no-credit“ result codes for push messages to prepaid subscribers Support of reverse charging (part of commercial agreement with VASP) Support of reply-charging (part of commercial agreement with VASP) ...
... VASP controls basic service charging VASP should get individual „low-credit“ or „no-credit“ result codes for push messages to prepaid subscribers Support of reverse charging (part of commercial agreement with VASP) Support of reply-charging (part of commercial agreement with VASP) ...
Routes - Chabot College
... • What happens to a packet sent to 209.33.45.177 • It is dropped because there is no entry for that network in the routing table: oak#show ip route Gateway of last resort is not set R C C R R S C ...
... • What happens to a packet sent to 209.33.45.177 • It is dropped because there is no entry for that network in the routing table: oak#show ip route Gateway of last resort is not set R C C R R S C ...
Chapter 7 TCP Traffic Control
... • Timer associated with each segment as it is sent • If timer expires before acknowledgement, sender must retransmit • Value of retransmission timer is a key factor —Too small: many unnecessary retransmissions, wasting network bandwidth —Too large: delay in handling lost segments —Timer should be lo ...
... • Timer associated with each segment as it is sent • If timer expires before acknowledgement, sender must retransmit • Value of retransmission timer is a key factor —Too small: many unnecessary retransmissions, wasting network bandwidth —Too large: delay in handling lost segments —Timer should be lo ...