SNMP/MIB Management
... Information and software in this document are proprietary to Vanguard Networks. (or its Suppliers) and without the express prior permission of an officer of Vanguard Networks, may not be copied, reproduced, disclosed to others, published, or used, in whole or in part, for any purpose other than that ...
... Information and software in this document are proprietary to Vanguard Networks. (or its Suppliers) and without the express prior permission of an officer of Vanguard Networks, may not be copied, reproduced, disclosed to others, published, or used, in whole or in part, for any purpose other than that ...
JNCIA Study Guide - Open Shortest Path First (OSPF)
... Before delving into the specific details of OSPF, let’s look at the theory behind its operation as well as the overall goals of the protocol. First, we discuss how a router utilizes a link-state routing protocol, and then we examine the exchange of link-state databases. We also discuss how the route ...
... Before delving into the specific details of OSPF, let’s look at the theory behind its operation as well as the overall goals of the protocol. First, we discuss how a router utilizes a link-state routing protocol, and then we examine the exchange of link-state databases. We also discuss how the route ...
"Resilient Overlay Networks"
... and its constituent networks, usually operated by some network service provider. The information shared with other providers and AS’s is heavily filtered and summarized using the Border Gateway Protocol (BGP-4) running at the border routers between AS’s [21], which allows the Internet to scale to mi ...
... and its constituent networks, usually operated by some network service provider. The information shared with other providers and AS’s is heavily filtered and summarized using the Border Gateway Protocol (BGP-4) running at the border routers between AS’s [21], which allows the Internet to scale to mi ...
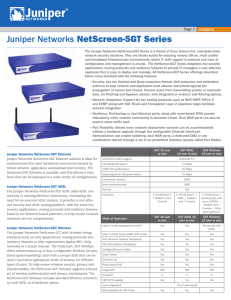
Juniper Networks NetScreen-5GT Series Datasheet
... applications, routing protocols and resiliency features to provide IT managers a cost effective appliance that is easy to deploy and manage. All NetScreen-5GT Series offerings described below come standard with the following features: • Security: Use the Stateful and Deep Inspection firewall, DoS pr ...
... applications, routing protocols and resiliency features to provide IT managers a cost effective appliance that is easy to deploy and manage. All NetScreen-5GT Series offerings described below come standard with the following features: • Security: Use the Stateful and Deep Inspection firewall, DoS pr ...
INR11%20-%20OSPF
... Manipulating the election process If you want to influence the election of DR and BDR with further configurations then do one of the following: Boot up the DR first, followed by the BDR, and then boot all other routers, OR Shut down the interface on all routers, followed by a no shutdown on th ...
... Manipulating the election process If you want to influence the election of DR and BDR with further configurations then do one of the following: Boot up the DR first, followed by the BDR, and then boot all other routers, OR Shut down the interface on all routers, followed by a no shutdown on th ...
Chapter 1 - Introduction
... – the forwarding function must find an entry in the forwarding table that specifies a next hop for D – The software examines each entry in the table by using the mask in the entry to extract a prefix of address D – It compares the resulting prefix to the Destination field of the entry • If the two a ...
... – the forwarding function must find an entry in the forwarding table that specifies a next hop for D – The software examines each entry in the table by using the mask in the entry to extract a prefix of address D – It compares the resulting prefix to the Destination field of the entry • If the two a ...
Understanding Simple Network Management Protocol
... The SNMP master agent listens on port 161 and forwards SNMP packets for Vendor MIBs. The Cisco Unified Communications Manager subagent interacts with the local Cisco Unified Communications Manager only. The Cisco Unified Communications Manager subagents send trap and information messages to the SNMP ...
... The SNMP master agent listens on port 161 and forwards SNMP packets for Vendor MIBs. The Cisco Unified Communications Manager subagent interacts with the local Cisco Unified Communications Manager only. The Cisco Unified Communications Manager subagents send trap and information messages to the SNMP ...
PDF - This Chapter (378.0 KB)
... The hostname is used in CLI prompts and default configuration filenames. If you do not configure the router hostname, the router uses the factory-assigned default hostname “Router.” Do not expect capitalization and lower casing to be preserved in the hostname. Uppercase and lowercase characters are ...
... The hostname is used in CLI prompts and default configuration filenames. If you do not configure the router hostname, the router uses the factory-assigned default hostname “Router.” Do not expect capitalization and lower casing to be preserved in the hostname. Uppercase and lowercase characters are ...
Compatible Systems Reference Guides
... If the device is a multislot product such as a VSR or IntraPort Enterprise, both the slot number and the interface number are shown, separated by a colon (e.g., Ethernet 0:0 indicates Slot 0, Ethernet 0, while Ethernet 1:0 indicates Slot 1, Ethernet 0). Administrative information will also be includ ...
... If the device is a multislot product such as a VSR or IntraPort Enterprise, both the slot number and the interface number are shown, separated by a colon (e.g., Ethernet 0:0 indicates Slot 0, Ethernet 0, while Ethernet 1:0 indicates Slot 1, Ethernet 0). Administrative information will also be includ ...
“Computers in Communication” by Gordon Brebner
... in communication. The end result is to allow the sharing of computer-based resources that are physically located in all parts of the world. From the point of view of most users, the mechanisms by which computers communicate are best kept hidden. However, without these mechanisms, no sharing of resou ...
... in communication. The end result is to allow the sharing of computer-based resources that are physically located in all parts of the world. From the point of view of most users, the mechanisms by which computers communicate are best kept hidden. However, without these mechanisms, no sharing of resou ...
Core of the network
... Impact on existing IPv4 infrastructure • Deploying IPv6 requires changes in the existing infrastructure – Some routers and switches have to be replaced – Some have to be upgraded – There are a lot of bugs in IPv6 code • More often firmware upgrades • New IPv6 related bugs -> CPU overload, Devices c ...
... Impact on existing IPv4 infrastructure • Deploying IPv6 requires changes in the existing infrastructure – Some routers and switches have to be replaced – Some have to be upgraded – There are a lot of bugs in IPv6 code • More often firmware upgrades • New IPv6 related bugs -> CPU overload, Devices c ...
Lifesize UVC Platform™ Installation and Deployment Guide
... 9. Adjust the settings to ensure that the virtual machine meets the vCPU, memory, disk space, and network interface requirements as specified on your application’s datasheet. You must also reserve a percentage of the host’s overall CPU resources for the virtual machine. Reserving resources is requir ...
... 9. Adjust the settings to ensure that the virtual machine meets the vCPU, memory, disk space, and network interface requirements as specified on your application’s datasheet. You must also reserve a percentage of the host’s overall CPU resources for the virtual machine. Reserving resources is requir ...
Dynamics of Hot-Potato Routing in IP Networks
... fully instrumenting all of the routers is not possible; instead, we must work with data from a limited number of vantage points. In addition, commercial routers offer limited opportunities for collecting detailed routing data—we can only collect measurements of the routing protocol messages that the ...
... fully instrumenting all of the routers is not possible; instead, we must work with data from a limited number of vantage points. In addition, commercial routers offer limited opportunities for collecting detailed routing data—we can only collect measurements of the routing protocol messages that the ...
Datagram
... . يمكن ان يستخدم في طريقتينcodepoint subfield • A. When the 3 rightmost bits are Os, the 3 leftmost bits are interpreted the same as the precedence bits in the service type interpretation. In other words, it is compatible with the old ...
... . يمكن ان يستخدم في طريقتينcodepoint subfield • A. When the 3 rightmost bits are Os, the 3 leftmost bits are interpreted the same as the precedence bits in the service type interpretation. In other words, it is compatible with the old ...
TOSCA Simple Profile for Network Functions Virtualization
... any patent claims that would necessarily be infringed by implementations of this specification by a patent holder that is not willing to provide a license to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee that produced this specification. OASIS may inclu ...
... any patent claims that would necessarily be infringed by implementations of this specification by a patent holder that is not willing to provide a license to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee that produced this specification. OASIS may inclu ...
PDF
... for critical applications. Application optimization technologies such as Cisco WAAS can improve performance with data-reduction techniques, but fluctuating network performance can still affect applications. Cisco Performance Routing (PfR) addresses network performance problems by allowing the networ ...
... for critical applications. Application optimization technologies such as Cisco WAAS can improve performance with data-reduction techniques, but fluctuating network performance can still affect applications. Cisco Performance Routing (PfR) addresses network performance problems by allowing the networ ...
Demystifying Layer 2 and Layer 3 VPNs
... 4.3 Business Features of Layer 2 and Layer 3 Services ................................................................................................................................................................... 37 4.3.1 Multi-point Any-to-Any Connectivity ..................................... ...
... 4.3 Business Features of Layer 2 and Layer 3 Services ................................................................................................................................................................... 37 4.3.1 Multi-point Any-to-Any Connectivity ..................................... ...
ospf_1 - D-Link
... Routers find the best paths to destinations by applying Dijkstra’s SPF algorithm to linkstate database as follows: Every router in an area has the identical link-state DB Each router in the area places itself into the root of the tree that is built The best path is calculated with respect to the ...
... Routers find the best paths to destinations by applying Dijkstra’s SPF algorithm to linkstate database as follows: Every router in an area has the identical link-state DB Each router in the area places itself into the root of the tree that is built The best path is calculated with respect to the ...
dynamic metric in ospf networks
... The massive growth of the Internet has led to increased requirements for reliable network infrastructure. The effectiveness of network communication depends on the ability of routers to determine the best path to send and forward packets to the desired destination. Open Shortest Path First (OSPF) pr ...
... The massive growth of the Internet has led to increased requirements for reliable network infrastructure. The effectiveness of network communication depends on the ability of routers to determine the best path to send and forward packets to the desired destination. Open Shortest Path First (OSPF) pr ...
Users Manual - Physics, Computer Science and Engineering
... 2.8. Choose Partitions to Be Formatted . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11 2.9. Actual Packages Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
... 2.8. Choose Partitions to Be Formatted . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11 2.9. Actual Packages Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
PDF - This Chapter (2.12 MB)
... configures the UMS to mix the Security, Facilities, and Combined VTG channels. Users who have been added to the VTG will see the new Combined VTG channel on their mobile clients or Cisco Unified IP Phones. LMR endpoints do not have associated users. An LMR channel is statically configured, so an LMR ...
... configures the UMS to mix the Security, Facilities, and Combined VTG channels. Users who have been added to the VTG will see the new Combined VTG channel on their mobile clients or Cisco Unified IP Phones. LMR endpoints do not have associated users. An LMR channel is statically configured, so an LMR ...
Discovering-Computers-2008-1st-Edition-Shelly-Test-Bank
... 22. Search engines like the one in Figure 2-2 ____. a. are particularly helpful in locating pages about certain topics b. require that you enter search text c. allow you to use operators to refine a search d. all of the above ANS: D OBJ: 6 ...
... 22. Search engines like the one in Figure 2-2 ____. a. are particularly helpful in locating pages about certain topics b. require that you enter search text c. allow you to use operators to refine a search d. all of the above ANS: D OBJ: 6 ...