CGL Requirements Definition V5.0
... Signs of abandonment may be an official announcement by the developer with no other developers adopting the project; it may be a lack of updates to support new functionality or in response to new developments in the community or simply to support new versions of the underlying software (for example ...
... Signs of abandonment may be an official announcement by the developer with no other developers adopting the project; it may be a lack of updates to support new functionality or in response to new developments in the community or simply to support new versions of the underlying software (for example ...
On Modern DNS Behavior and Properties
... application protocols, as well as Bro’s standard notion of the connection’s ending state (e.g., “normally terminated”) and history of key actions observed during the connection (e.g., three-way handshake completed, TCP reset observed, etc.). The dataset used in this paper was collected continuously ...
... application protocols, as well as Bro’s standard notion of the connection’s ending state (e.g., “normally terminated”) and history of key actions observed during the connection (e.g., three-way handshake completed, TCP reset observed, etc.). The dataset used in this paper was collected continuously ...
Multicast - Virginia Tech
... •A host on the LAN that did not express interest in receiving multicast from that group will ignore such datagram •Destination Ethernet address does not match the interface address •Destination Ethernet address is not the ethernet broadcast address •The interface has not been told to receive any gro ...
... •A host on the LAN that did not express interest in receiving multicast from that group will ignore such datagram •Destination Ethernet address does not match the interface address •Destination Ethernet address is not the ethernet broadcast address •The interface has not been told to receive any gro ...
FRITZ!Box Fon WLAN 7170
... All computers connected to FRITZ!Box Fon WLAN are networked together and can access shared files and printers. Internet Connection for All Computers All of the computers connected to FRITZ!Box Fon WLAN can access the Internet. There are two different ways of establishing an Internet connection. Both ...
... All computers connected to FRITZ!Box Fon WLAN are networked together and can access shared files and printers. Internet Connection for All Computers All of the computers connected to FRITZ!Box Fon WLAN can access the Internet. There are two different ways of establishing an Internet connection. Both ...
Advanced CCIE Routing & Switching
... Configure the routers based on the above topology, DO NOT configure any routing protocol. If this configuration is performed properly, these routers should be able to ping their directly connected routers. The Link-local IPv6 address of the routers should be set to fe80::1, fe80::2, fe80::7 and fe80 ...
... Configure the routers based on the above topology, DO NOT configure any routing protocol. If this configuration is performed properly, these routers should be able to ping their directly connected routers. The Link-local IPv6 address of the routers should be set to fe80::1, fe80::2, fe80::7 and fe80 ...
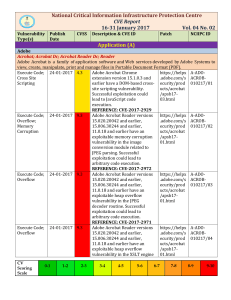
16-31 Jan`17 - National Critical Information Infrastructure Protection
... Cloudvision Portal CloudVision Portal (CVP) is the web-based GUI for the CloudVision platform. The Portal provides a turnkey solution for automating network operations, including network device provisioning, compliance, change management, and network monitoring. NA ...
... Cloudvision Portal CloudVision Portal (CVP) is the web-based GUI for the CloudVision platform. The Portal provides a turnkey solution for automating network operations, including network device provisioning, compliance, change management, and network monitoring. NA ...
12.4 was released in May of 2005
... • Supports a wide range of attack/worm signatures supported (740+) • Used for inline intrusion prevention and event notification • Dynamically loads attack signatures to the router • Integrates technology from Cisco IDS Sensor families Cisco IDS 4200 Series Appliances, Cisco Catalyst® 6500 IDS Modul ...
... • Supports a wide range of attack/worm signatures supported (740+) • Used for inline intrusion prevention and event notification • Dynamically loads attack signatures to the router • Integrates technology from Cisco IDS Sensor families Cisco IDS 4200 Series Appliances, Cisco Catalyst® 6500 IDS Modul ...
slides 3
... • Does the problem occur all the time, frequently, or rarely? • Does the problem occur for only a specific application, many applications, or only some applications? • Is the problem reproducible on other machines? ...
... • Does the problem occur all the time, frequently, or rarely? • Does the problem occur for only a specific application, many applications, or only some applications? • Is the problem reproducible on other machines? ...
CCNPv5 Module 5 Lesson 10
... The open nature of the Internet makes it increasingly important for businesses to pay attention to the security of their networks. As organisations move more of their business functions to the public network, they need to take precautions to ensure that attackers do not compromise their data, or t ...
... The open nature of the Internet makes it increasingly important for businesses to pay attention to the security of their networks. As organisations move more of their business functions to the public network, they need to take precautions to ensure that attackers do not compromise their data, or t ...
OSPF
... - Cisco menghitung Cost dgn rumus = 108 / bandwidth interface. - Nilai cost dapat dimanipulasi dalam range 1 s/d 65.535, perintahnya: ip ospf cost ...
... - Cisco menghitung Cost dgn rumus = 108 / bandwidth interface. - Nilai cost dapat dimanipulasi dalam range 1 s/d 65.535, perintahnya: ip ospf cost ...
21-05-0298-01-0000-Section5-Draft1
... The MIH Function provides asynchronous and synchronous services through well-defined SAPs for lower layers and upper layers. In the case of a system with multiple network interfaces of arbitrary type, the L3MP can use the Event service, Command service and Information service provided by MIH to mana ...
... The MIH Function provides asynchronous and synchronous services through well-defined SAPs for lower layers and upper layers. In the case of a system with multiple network interfaces of arbitrary type, the L3MP can use the Event service, Command service and Information service provided by MIH to mana ...
Cisco Catalyst 3550 Series Switches for Metro Access
... medium-sized business (SMB) market customers. As they continue to put more and more mission-critical applications on their networks, these customers are demanding high bandwidth at speeds greater than T1/E1 and at competitive prices. Enterprise and SMB customers have experienced the speed and cost b ...
... medium-sized business (SMB) market customers. As they continue to put more and more mission-critical applications on their networks, these customers are demanding high bandwidth at speeds greater than T1/E1 and at competitive prices. Enterprise and SMB customers have experienced the speed and cost b ...
On Modern DNS Behavior and Properties
... key actions observed during the connection (e.g., three-way handshake completed, TCP reset observed, etc.). The dataset used in this paper was collected continuously from January 25, 2011 through March 31, 2012. During this period we collect just over 200 million DNS queries and about 162 million DN ...
... key actions observed during the connection (e.g., three-way handshake completed, TCP reset observed, etc.). The dataset used in this paper was collected continuously from January 25, 2011 through March 31, 2012. During this period we collect just over 200 million DNS queries and about 162 million DN ...
ForeRunner
... Copyright © 1995-1998 FORE Systems, Inc. All rights reserved. FORE Systems is a registered trademark, and ForeRunner, ForeRunnerLE, ForeThought, ForeView, PowerHub, and CellPath are trademarks of FORE Systems, Inc. All other brands or product names are trademarks or registered trademarks of their re ...
... Copyright © 1995-1998 FORE Systems, Inc. All rights reserved. FORE Systems is a registered trademark, and ForeRunner, ForeRunnerLE, ForeThought, ForeView, PowerHub, and CellPath are trademarks of FORE Systems, Inc. All other brands or product names are trademarks or registered trademarks of their re ...
Cisco ONS 15305 Multiservice Provisioning Platform for SDH Access Networks
... The Cisco ONS 15305 can serve as an optical transport platform for enterprise private networks (Figure 4). A Cisco ONS 15305 device located at the headquarters or main building of an office, university, or government campus can aggregate Ethernet and TDM traffic from multiple remote sites. Other Cis ...
... The Cisco ONS 15305 can serve as an optical transport platform for enterprise private networks (Figure 4). A Cisco ONS 15305 device located at the headquarters or main building of an office, university, or government campus can aggregate Ethernet and TDM traffic from multiple remote sites. Other Cis ...
Secure and Distributed Multicast Address Allocation on IPv6 Networks M. L. Slaviero
... Why is the exploitation of a resource which promised so much, so limited? A common argument made is that many devices do not support multicast, and this is examined in a later chapter. Jonathan Barter, a self-proclaimed multicast evangelist, believes that better marketing is required to increase mul ...
... Why is the exploitation of a resource which promised so much, so limited? A common argument made is that many devices do not support multicast, and this is examined in a later chapter. Jonathan Barter, a self-proclaimed multicast evangelist, believes that better marketing is required to increase mul ...
Brocade ICX Switch Family Data Sheet
... brings campus networks into the modern era to better support seamless wireless mobility, security, and ease of application deployment. This innovative technology collapses multiple network layers into a single logical switch, flattening the network and eliminating deployment complexity while simplif ...
... brings campus networks into the modern era to better support seamless wireless mobility, security, and ease of application deployment. This innovative technology collapses multiple network layers into a single logical switch, flattening the network and eliminating deployment complexity while simplif ...
PDF
... Due to the shared nature of wireless communications, the experienced throughput varies depending on the number of active users or congestion in a given network. ...
... Due to the shared nature of wireless communications, the experienced throughput varies depending on the number of active users or congestion in a given network. ...
PAN‐OS Web Interface Reference Guide
... Enter the tag number (0‐4094) or range of tag numbers (tag1‐tag2) for the traffic allowed on the virtual wire. A tag value of zero indicates untagged traffic (the default). Multiple tags or ranges must be separated by commas. Traffic that has an excluded tag value is dropped. Tag values are not ...
... Enter the tag number (0‐4094) or range of tag numbers (tag1‐tag2) for the traffic allowed on the virtual wire. A tag value of zero indicates untagged traffic (the default). Multiple tags or ranges must be separated by commas. Traffic that has an excluded tag value is dropped. Tag values are not ...
APNIC Tutorial: IPv6 Essentials
... discovery process [Path MTU Discovery] to determine most optimum MTU size before creating end to end session • In this discovery process, the source IPv6 device attempts to send a packet at the size specified by the upper IP layers [i.e TCP/Application]. • If the device receives an ICMP packet to ...
... discovery process [Path MTU Discovery] to determine most optimum MTU size before creating end to end session • In this discovery process, the source IPv6 device attempts to send a packet at the size specified by the upper IP layers [i.e TCP/Application]. • If the device receives an ICMP packet to ...
Computer Networks and Internets By Douglas E Comer
... Becoming common in personal digital assistants Laser ...
... Becoming common in personal digital assistants Laser ...
Mobile Communication and Mobile Computing
... The Principle of CDMA can be good illustrated by the example of some party: • communication partners stand closely to each other, each transmission station (Sender) is only so loud, that it does not interfere to neighbored groups • transmission stations (Senders) use certain Codes (for instance, jus ...
... The Principle of CDMA can be good illustrated by the example of some party: • communication partners stand closely to each other, each transmission station (Sender) is only so loud, that it does not interfere to neighbored groups • transmission stations (Senders) use certain Codes (for instance, jus ...
Lab 11.6.1: Basic OSPF Configuration Lab (Instructor Version)
... Step 3: Reload the routers to force the new Router IDs to be used. When a new Router ID is configured, it will not be used until the OSPF process is restarted. Make sure that the current configuration is saved to NRAM, and then use the reload command to restart each of the routers.. When the router ...
... Step 3: Reload the routers to force the new Router IDs to be used. When a new Router ID is configured, it will not be used until the OSPF process is restarted. Make sure that the current configuration is saved to NRAM, and then use the reload command to restart each of the routers.. When the router ...
Fachbereich Informatik und Elektrotechnik
... Area Networks or short distance wireless networks. These WPANs address wireless networking of portable and mobile computing devices such as PCs, PDAs, peripherals, cell phones and consumer electronics. The goal is to publish standards, recommended practices, or guides that have broad market applicab ...
... Area Networks or short distance wireless networks. These WPANs address wireless networking of portable and mobile computing devices such as PCs, PDAs, peripherals, cell phones and consumer electronics. The goal is to publish standards, recommended practices, or guides that have broad market applicab ...