Slide 1
... traffic volume, ingress must be collected on all interfaces and the reporting software then displays outbound traffic. What goes in must go out, right? • NetFlow v9 Egress is collected on traffic going out (i.e. outBound) of an interface. Generally, it is used in combination with Ingress, but it doe ...
... traffic volume, ingress must be collected on all interfaces and the reporting software then displays outbound traffic. What goes in must go out, right? • NetFlow v9 Egress is collected on traffic going out (i.e. outBound) of an interface. Generally, it is used in combination with Ingress, but it doe ...
2 Motivation for HSDPA
... packet-switched traffic will soon surpass circuit-switched traffic. Indeed, in most fixed networks, IP-based traffic volume has eclipsed circuit-switched traffic. Mobile networks are sure to follow suit as new IP-based mobile services emerge and eager users adopt them. So mobile operators need techn ...
... packet-switched traffic will soon surpass circuit-switched traffic. Indeed, in most fixed networks, IP-based traffic volume has eclipsed circuit-switched traffic. Mobile networks are sure to follow suit as new IP-based mobile services emerge and eager users adopt them. So mobile operators need techn ...
Hands-on Labs
... So what’s an administrator to do to mitigate the impact of managing really big networks? Well, it’s possible to divide the network into multiple distinct EIGRP autonomous systems, or ASes. Each AS is populated by a contiguous series of routers, and route information can be shared among the different ...
... So what’s an administrator to do to mitigate the impact of managing really big networks? Well, it’s possible to divide the network into multiple distinct EIGRP autonomous systems, or ASes. Each AS is populated by a contiguous series of routers, and route information can be shared among the different ...
Release Notes for Catalyst 3850 Series Switch, Cisco IOS XE
... In enterprise networks, there is typically a need for providing network access to its guests on the campus. The guest access requirements include providing connectivity to the Internet or other selective enterprise resources to both wired and wireless guests in a consistent and manageable way. The s ...
... In enterprise networks, there is typically a need for providing network access to its guests on the campus. The guest access requirements include providing connectivity to the Internet or other selective enterprise resources to both wired and wireless guests in a consistent and manageable way. The s ...
SNAP® Connect E10 User Guide
... Installing the Drivers ...................................................................................................................... 14 Establishing Connectivity to the E10.............................................................................................. 14 Access Via the Serial ...
... Installing the Drivers ...................................................................................................................... 14 Establishing Connectivity to the E10.............................................................................................. 14 Access Via the Serial ...
BACnet Router FS-ROUTER-BAC
... solution for BACnet/IP, BACnet Ethernet, and BACnet MS/TP networks. This is the first standalone BACnet Router that has been certified by BTL to ensure the highest standard for BACnet integration. The FieldServer BACnet Router is available in two models: The FS-ROUTER-BAC has two RS-485 ports enab ...
... solution for BACnet/IP, BACnet Ethernet, and BACnet MS/TP networks. This is the first standalone BACnet Router that has been certified by BTL to ensure the highest standard for BACnet integration. The FieldServer BACnet Router is available in two models: The FS-ROUTER-BAC has two RS-485 ports enab ...
DNET-UM004 - Literature Library
... Guidelines for the Application, Installation and Maintenance of Solid State Controls (publication SGI-1.1 available from your local Rockwell Automation sales office or online at http://www.rockwellautomation.com/literature/) describes some important differences between solid-state equipment and hard ...
... Guidelines for the Application, Installation and Maintenance of Solid State Controls (publication SGI-1.1 available from your local Rockwell Automation sales office or online at http://www.rockwellautomation.com/literature/) describes some important differences between solid-state equipment and hard ...
Cookbook for IPv6 Renumbering in ISP and Enterprise
... commercial ADSL provider that we were in discussion with in late 2004 has delayed their plans for native IPv6 rollout, leaving us without a practical commercial experimentation point. The deployment done in the Greek School Network (including IPv6 over ADSL) could form the basis for future experimen ...
... commercial ADSL provider that we were in discussion with in late 2004 has delayed their plans for native IPv6 rollout, leaving us without a practical commercial experimentation point. The deployment done in the Greek School Network (including IPv6 over ADSL) could form the basis for future experimen ...
PowerPoint - DePaul University
... Given that an ISP announces netblocks 64.5.0.0/20, 64.5.16.0/20, 192.0.2.0/25 and 192.0.2.192/26 and 192.0.2.128/26: ...
... Given that an ISP announces netblocks 64.5.0.0/20, 64.5.16.0/20, 192.0.2.0/25 and 192.0.2.192/26 and 192.0.2.128/26: ...
L_06_ch_13_DLL_LAN_Ethernet
... The 10-Mbps capacity in each segment is now shared between 6 stations (actually 7 because the bridge acts as a station in each segment), not 12 stations. In a network with a heavy load, each station theoretically is offered 10/6 Mbps instead of 10/12 Mbps, assuming that the traffic is not going thro ...
... The 10-Mbps capacity in each segment is now shared between 6 stations (actually 7 because the bridge acts as a station in each segment), not 12 stations. In a network with a heavy load, each station theoretically is offered 10/6 Mbps instead of 10/12 Mbps, assuming that the traffic is not going thro ...
PDF - Complete Book (3.05 MB)
... 2 Applying the ACL to specific interfacesAfter configuring an access list, you must reference the access list to make it work. Access lists can be applied on inbound interfaces. After receiving a packet, Cisco IOS XR software checks the source address of the packet against the access list. If the ac ...
... 2 Applying the ACL to specific interfacesAfter configuring an access list, you must reference the access list to make it work. Access lists can be applied on inbound interfaces. After receiving a packet, Cisco IOS XR software checks the source address of the packet against the access list. If the ac ...
paper
... rate to adjust for losses without closing down the window in a drastic fashion. Note that network coding does not mask correlated (or bursty) losses due to congestion. With enough correlated losses, network coding cannot correct for all the losses. As a result, the transmission rate will be adjusted ...
... rate to adjust for losses without closing down the window in a drastic fashion. Note that network coding does not mask correlated (or bursty) losses due to congestion. With enough correlated losses, network coding cannot correct for all the losses. As a result, the transmission rate will be adjusted ...
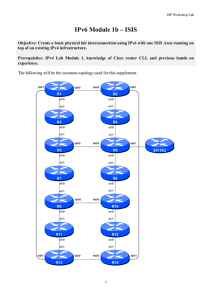
Module 01 - IPv6 ISIS and iBGP
... Nothing will break if IPv6 CEF is not enabled, but more advanced features such as NetFlow will not function without IPv6 CEF being enabled. 3. Disable IPv6 Source Routing. Unless you really believe there is a need for it, source routing should be disabled. This option, enabled by default, allows the ...
... Nothing will break if IPv6 CEF is not enabled, but more advanced features such as NetFlow will not function without IPv6 CEF being enabled. 3. Disable IPv6 Source Routing. Unless you really believe there is a need for it, source routing should be disabled. This option, enabled by default, allows the ...
Current Cost Financial Statements for 2011 including Openreach Undertakings
... Relevant, reliable and timely regulatory financial information informs many of our decisions. We require this information in order to monitor and enforce various obligations that are placed on BT in markets where they are found to have significant market power (“SMP”) and as a source of data for set ...
... Relevant, reliable and timely regulatory financial information informs many of our decisions. We require this information in order to monitor and enforce various obligations that are placed on BT in markets where they are found to have significant market power (“SMP”) and as a source of data for set ...
Lecture 8 - cda college
... Transport of IP over ATM; focuses strictly on IP support Each subnet must have its own ARP server Simpler implementation than LANE; generates less network overhead Any device with a legacy LAN connection must pass through a router to reach destination device ...
... Transport of IP over ATM; focuses strictly on IP support Each subnet must have its own ARP server Simpler implementation than LANE; generates less network overhead Any device with a legacy LAN connection must pass through a router to reach destination device ...
NetApp CN1610 Switch Administrator`s Guide
... The CN1610 switch supports router advertisement as an integral part of IPv6. Numerous options are available, including stateless/stateful address configuration, router and address lifetimes, and neighbor discovery timer control. The switch also supports Ethernet and tunnel interfaces. For Ethernet, ...
... The CN1610 switch supports router advertisement as an integral part of IPv6. Numerous options are available, including stateless/stateful address configuration, router and address lifetimes, and neighbor discovery timer control. The switch also supports Ethernet and tunnel interfaces. For Ethernet, ...
PDF
... Cisco IWAN App (or the Cisco IWAN on APIC-EM) extends Software Defined Networking to the branch with an application-centric approach based on business policy and application rules. This provides IT centralized management with distributed enforcement across the network. Cisco IWAN App automates and o ...
... Cisco IWAN App (or the Cisco IWAN on APIC-EM) extends Software Defined Networking to the branch with an application-centric approach based on business policy and application rules. This provides IT centralized management with distributed enforcement across the network. Cisco IWAN App automates and o ...
BSG 8ew 1.0 Solution Guide
... network and involve several components. The components involved in the architecture are the Communication Servers (CS2000), Media Gateways, Signaling Gateways, and CPE devices. They are interconnected through the Managed IP network that can be viewed as a core network that is managed by the service ...
... network and involve several components. The components involved in the architecture are the Communication Servers (CS2000), Media Gateways, Signaling Gateways, and CPE devices. They are interconnected through the Managed IP network that can be viewed as a core network that is managed by the service ...
Model FVL328 ProSafe High-Speed VPN Firewall Reference
... Equipment and Electronic Office Machines, aimed at preventing radio interference in such residential areas. When used near a radio or TV receiver, it may become the cause of radio interference. Read instructions for correct handling. ...
... Equipment and Electronic Office Machines, aimed at preventing radio interference in such residential areas. When used near a radio or TV receiver, it may become the cause of radio interference. Read instructions for correct handling. ...
Document
... possible addresses. IPv6 has been slow to arrive IPv4 revitalized by new features, making IPv6 a luxury, and not a desperately needed fix IPv6 requires new software; IT staffs must be retrained IPv6 will most likely coexist with IPv4 for years to come. Some experts believe IPv4 will remain for more ...
... possible addresses. IPv6 has been slow to arrive IPv4 revitalized by new features, making IPv6 a luxury, and not a desperately needed fix IPv6 requires new software; IT staffs must be retrained IPv6 will most likely coexist with IPv4 for years to come. Some experts believe IPv4 will remain for more ...
Advanced Routing - Fortinet Document Library
... Dynamic Routing Overview ........................................................................... 44 What is dynamic routing? ...................................................................................... Comparing static and dynamic routing................................................ ...
... Dynamic Routing Overview ........................................................................... 44 What is dynamic routing? ...................................................................................... Comparing static and dynamic routing................................................ ...
Xerox Secure Access EIP2 Manual
... To track the device usage the Xerox Network Accounting module must also be enabled (Network Accounting is also known as JBA accounting). The “Network Accounting” module is often included with the device, but for some devices it is necessary to have this enabled by your Xerox supplier. Please contact ...
... To track the device usage the Xerox Network Accounting module must also be enabled (Network Accounting is also known as JBA accounting). The “Network Accounting” module is often included with the device, but for some devices it is necessary to have this enabled by your Xerox supplier. Please contact ...
Cloud and Network Services
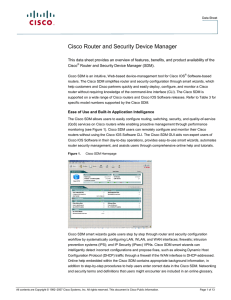
... SDM offers advanced configuration tools to quickly configure and fine-tune router security features, allowing network professionals to review the commands generated by the Cisco SDM before delivering the configuration changes to the router. The Cisco SDM helps administrators configure and monitor ro ...
... SDM offers advanced configuration tools to quickly configure and fine-tune router security features, allowing network professionals to review the commands generated by the Cisco SDM before delivering the configuration changes to the router. The Cisco SDM helps administrators configure and monitor ro ...
VPN Manager Guide
... components (whether installed separately on a computer workstation or on the WATCHGUARD hardware product) and may include associated media, printed materials, and on-line or electronic documentation, and any updates or modifications thereto, including those received through the WatchGuard LiveSecuri ...
... components (whether installed separately on a computer workstation or on the WATCHGUARD hardware product) and may include associated media, printed materials, and on-line or electronic documentation, and any updates or modifications thereto, including those received through the WatchGuard LiveSecuri ...
ATF_Best Practice Design for an Avaya Fabric Connect Campus
... network that is distributed across a city or even a larger geography Why? It will make your life easier It will free up your time and your staff’s time to work on more strategic projects It will allow you to support new initiatives improving your business – improve time to service It will ...
... network that is distributed across a city or even a larger geography Why? It will make your life easier It will free up your time and your staff’s time to work on more strategic projects It will allow you to support new initiatives improving your business – improve time to service It will ...